2025 E-Commerce Bot Threat Report

Insights on malicious bots that disrupt online retailers—and destroy holiday sales.
Podcasts, articles, and news delivering analyst-led perspectives to help leaders navigate AI, data, cybersecurity, and infrastructure decisions.
Discover expert led podcasts, articles, and news from enterprise technology leaders at EM360Tech, your source for B2B tech intelligence

Insights on malicious bots that disrupt online retailers—and destroy holiday sales.

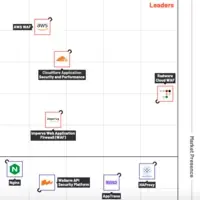
Customers lift Radware in G2’s Cloud WAF grid for Spring 2025
The Invisible Breach: Business Logic Manipulation and API Exploitation in Credential Stuffing Attacks
EM360Tech presents the definitive guide to the leading zero trust security vendors, helping enterprises shortlist the right partner with confidence.

With modern, identity-first security

Five key outcomes for your organization



Traditional security models fail because pipelines contain sensitive credentials, have administrative access to production, and process hundreds of third-party dependencies.




EM360Tech explores how security and privacy leaders can use synthetic data without falling foul of GDPR, with actionable guidance and red flag warnings.
Boost and protect your business in the digital age
Get the latest insights, analysis and tech news delivered straight to your inbox