2025 didn't introduce new cyber risk so much as it invalidated old assumptions about how cyber risk is managed. The year forced security leaders to confront an uncomfortable truth: several of the enterprise “defaults” that made modern security scalable started behaving like liabilities under pressure.
Trusted software updates propagated malicious change at speed. Regulatory frameworks turned incidents into disclosure events with governance consequences. Machine and autonomous identities stopped being background plumbing and became the fastest-growing attack surface.
Adversaries pushed incidents to machine tempo, collapsing response windows. And post-quantum cryptography stopped being a theoretical concern and became a migration programme with real timelines.

This is why enterprise security strategy in 2026 will look less like “add another tool” and more like redesigning foundations. The winning programmes will be built for trust that can fail, automation that must be governed, scrutiny that is inevitable, identities that are not human, and cryptography that must change on purpose, not by accident.
Trust in Automated Remediation Broke
Software supply chain security used to be described as a specialised problem. Something for engineering leaders, DevSecOps teams, and vendors selling scanning tools. 2025 dragged it back to the boardroom, because the failure mode was not “someone shipped a bug”. It was “the system that tells you what is safe is no longer reliable”.
Across open-source ecosystems and enterprise delivery pipelines, attackers targeted the trust anchors. Maintainer accounts. Build systems. Publishing workflows. Distribution channels. When that layer is compromised, security controls can still “work” and still spread risk. Signed artefacts, automated dependency updates, and continuous integration and continuous delivery (CI/CD) pipelines do not magically become safe because they are automated. They become faster.
The xz Utils incident in 2024 is still the most cited example because it demonstrated a slow-burn attempt to infiltrate a widely used component through upstream trust, not a smash-and-grab exploit. The lesson carried into 2025 as supply chain incidents kept reinforcing the same pattern: automation amplifies whatever it touches, including compromised provenance.
The most destabilising detail is that standard remediation advice stopped being universally safe. “Upgrade to the latest version” is only risk-reducing if the upstream source and release pipeline are trustworthy. Once that trust is uncertain, remediation becomes a decision, not a reflex.
How enterprises reacted in the moment
Enterprises didn't respond with philosophical debates about open source. They responded with friction.
Teams slowed down automated updates in critical systems. They introduced manual decision gates for dependency changes that would previously have been merged on autopilot. They forced visibility into what was being pulled into production, and from where. They also started treating build and release infrastructure as Tier 0, alongside identity and network control planes.
This is where dependency governance became more than a policy document. It turned into operational choices about what to allow by default, what requires review, and what gets blocked even if it's popular. Some organisations built allowlists for approved packages, registries, and maintainers. Others made upgrade paths conditional on additional verification steps, especially for libraries that sit deep in the stack and would be hard to unwind if compromised.
Rollback capability also moved up the priority list. Not as an engineering nice-to-have, but as a containment control. If automation can ship risk quickly, the enterprise needs the muscle memory to reverse change quickly, safely, and consistently.
Security strategies in 2026 prioritise provable safety over speed
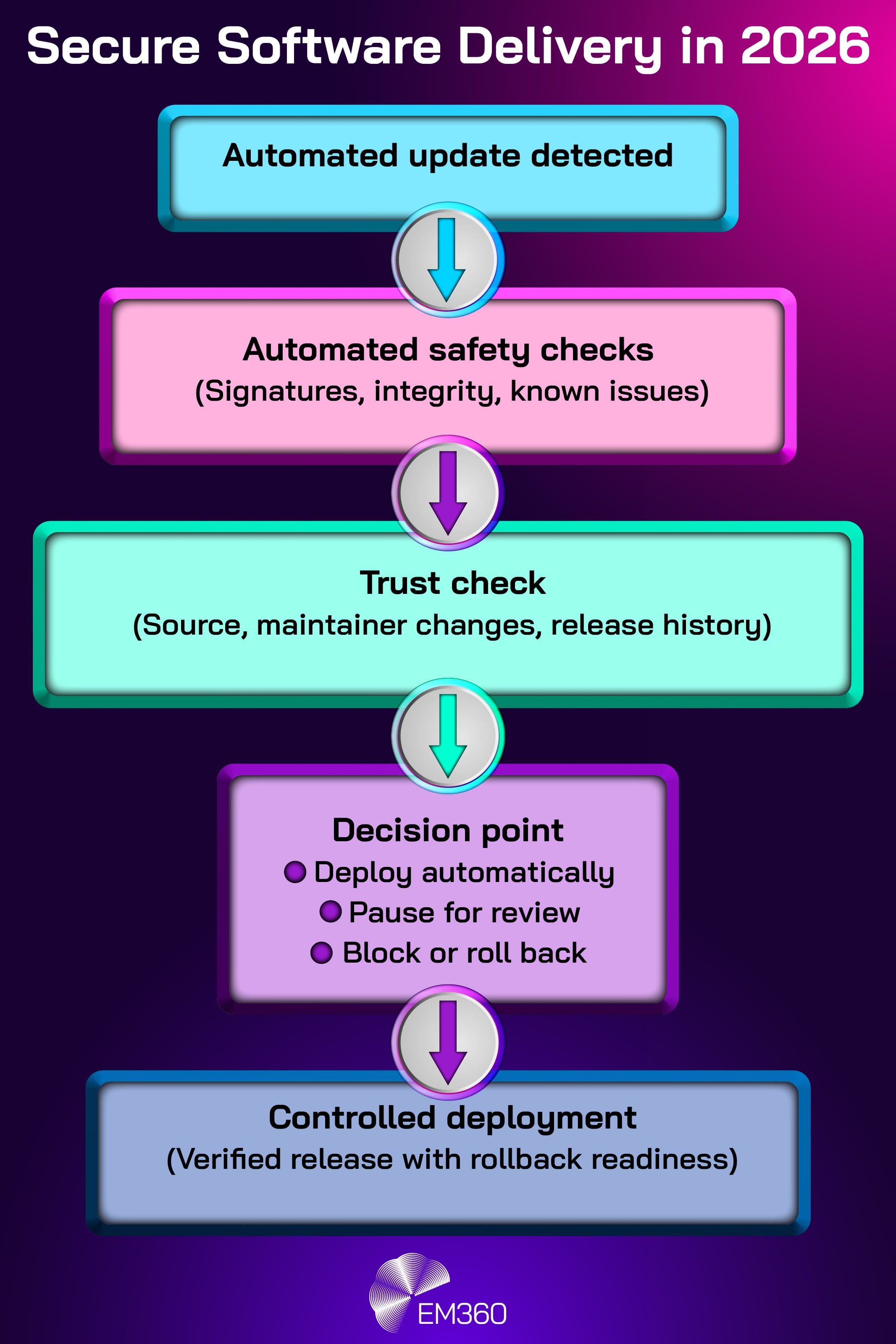
In 2026, the shift is not away from automation. It is away from blind trust in automation.
Security leaders will balance speed with evidence. “Fast patching” remains valuable, but only when it's paired with confidence that the patch itself is legitimate and safe. That pushes organisations toward secure software delivery that is continuously validated, not assumed.
From Audits to Continuous Trust
Shift compliance from annual snapshots to embedded, automated controls that keep hybrid estates aligned with fast-moving global regulations.

Practically, this means more investment in release integrity, dependency governance, and risk-based remediation. It also means building decision points that can pause automation when trust signals degrade. The goal is not to slow teams down for the sake of process. The goal is to prevent automated systems from becoming high-speed distribution channels for someone else’s compromise.
Cybersecurity Became a Disclosure and Governance Obligation
In 2025, cybersecurity regulation crossed a threshold where enforcement and disclosure moved from abstract risk to operational reality.
In the United States, the Securities and Exchange Commission (SEC) cyber disclosure rules require public companies to disclose material cybersecurity incidents on Form 8-K within four business days of determining materiality. In Europe, the NIS2 Directive expanded scope and tightened incident reporting expectations, pushing more organisations into formal accountability and structured response requirements.
These frameworks do not merely add paperwork. They change how enterprises must think about an incident. It is no longer just a technical event to contain. It is a regulated event that must be assessed, documented, and communicated under scrutiny.
That shift matters because it changes what “good security” looks like. Organisations are judged not only on whether they stop an attack, but on whether they can demonstrate governance, oversight, and decision-making that stands up to regulators, investors, customers, and the public.
How enterprises reacted in the moment
Most enterprises already had incident response plans. What changed in 2025 is that the plan could not live inside the security team anymore.
Legal, compliance, communications, and executive leadership became core participants earlier in the response timeline, not optional escalation paths. Organisations formalised materiality assessment processes, because in SEC terms, the disclosure clock starts after the company determines the incident is material, and that determination must be defensible.
This pushed many teams to tighten documentation and evidence discipline. Security teams were no longer writing notes purely for internal learning. They were creating records that could be scrutinised externally. That includes timelines, decision rationale, control posture, and the organisation’s governance model for cyber risk.
Inside the Politics of Tech Bans
See how bans on social platforms, devices and data tools expose the fault lines between innovation, public safety and state control.

It also raised a strategic question that is easy to overlook in technical post-mortems: who owns the judgement call when the facts are incomplete and the clock is running?
What security governance looks like in 2026
In 2026, security will be funded and evaluated with disclosure in mind. That does not mean security becomes a legal function. It means governance becomes a first-class design requirement.
The strongest programmes will have incident response governance that is structured, practiced, and documented. Board-level oversight will be visible and consistent, not reactive. And security reporting will be built to withstand the kinds of questions external stakeholders ask when something goes wrong.
This is where audit-ready security stops being a compliance slogan and becomes a competitive advantage. Enterprises that can respond decisively and explain credibly will recover faster and lose less trust, even when they cannot prevent every incident.

Non-Human Identities Became the Primary Attack Surface
For years, identity was treated as a human problem. People log in, people get phished, people abuse privileges. In 2025, that view became increasingly incomplete.
Enterprise environments now rely on APIs, service accounts, containers, CI/CD pipelines, SaaS integrations, and increasingly AI agents that authenticate and act independently. Many of the most important actions in modern systems are not initiated by humans. They are initiated by software, often at high frequency, across distributed environments, using credentials that are easy to create and hard to track.
That shift breaks a human-centric security model. Traditional identity and access management (IAM) was not designed for identity populations where the majority of identities are non-human, where ownership is unclear, and where accountability is hard to establish. It also exposes a governance gap: permissions and tokens often live longer than intended, are reused across systems, and are rarely rotated with the same discipline used for privileged human access.

When SIEM Becomes Core Security
Breaches, ransomware and compliance pressure are pushing SIEM from optional tooling to a mandatory layer in cyber defense.
The result is a growing class of actors that are authenticated, autonomous, and always on. When they are compromised, the blast radius can be immediate and difficult to attribute.
How enterprises reacted in the moment
Enterprise reaction in 2025 was pragmatic and slightly panicked: inventory first.
Teams started asking basic questions that turned out to be hard to answer. How many service accounts exist? Where are tokens stored? Which pipelines can deploy to production? Which integrations can write data, not just read it? What do AI agents have permission to do, and who approved it?
This drove greater investment in secrets management, credential lifecycle control, and privileged access disciplines applied to machine identities. It also triggered early governance moves for AI agent permissions, because granting broad access to autonomous systems is a new kind of risk. Not because agents are malicious by default, but because they can act quickly, chain actions, and make mistakes at scale.
How identity security architectures change in 2026
In 2026, identity security will extend beyond people as a formal architectural priority. Non-human principals will be treated as first-class identities with explicit owners, lifecycle management, and scoped permissions.
This shift also pushes enterprises toward behaviour-based monitoring. Access alone is not enough when identities can be authorised and still dangerous. Organisations will increasingly monitor what a machine identity is doing, how that behaviour changes, and how quickly it should be contained when it deviates from expected patterns.
The enterprises that get ahead here will treat machine identity governance as foundational, not as an add-on. That is the difference between managing risk and chasing it.
AI Pushed Cyber Incidents to Machine Speed
There is a lazy way to talk about AI and cybercrime, which is to say it makes attackers more capable. 2025 made a more important point: it makes everything faster.
When Shadow IT Becomes Strategy
Why boards must treat unsanctioned tools and shadow AI as enterprise exposure, demanding new governance, visibility and funding models.

Adversaries are increasingly operationalising automation for reconnaissance, phishing, credential abuse, lateral movement, and action chaining. Europol has been explicit about AI accelerating and scaling organised crime, including online fraud and cyber operations, and warns about increasingly autonomous capabilities.
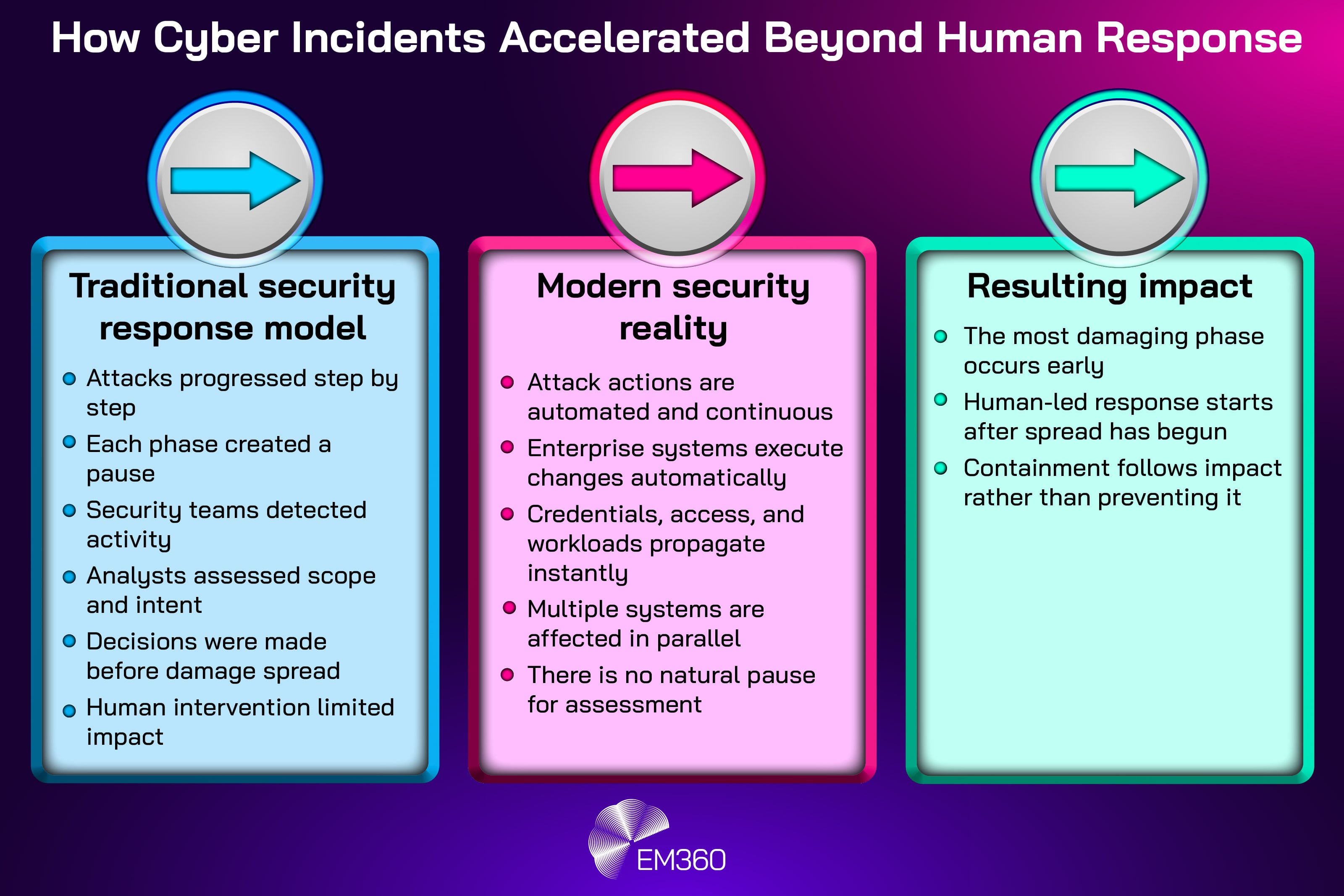
At the same time, enterprise environments are more automated than ever. Continuous deployment. Always-on integrations. Machine identities. Scheduled jobs. Autonomous workflows. When automation meets automation, incidents propagate at machine speed.
That changes the basic dynamics of a security event. The most damaging phase can occur before a human has enough context to make a confident decision.
How enterprises reacted in the moment
For a long time, security teams pursued faster detection as a primary goal. Better alerts, better telemetry, better correlation. In 2025, many organisations ran into the same wall: detection can be fast and still be too late.
When credentials are abused quickly, or when an attacker can chain actions through a series of automated systems, blast radius expands before human intervention is possible. Visibility becomes a lagging indicator. Analysts can see what happened, but the system has already moved.
This is not a reason to give up on detection. It is a reason to stop treating detection as the finish line. Security operations need the ability to interrupt cascading impact, not just describe it.
What machine-speed containment looks like in 2026
In 2026, the operational shift will be toward containment that can act as fast as the threat. That means pre-authorised response patterns, policy-driven enforcement, and automated containment that is designed to stop the spread of an incident while humans investigate.
This is where security orchestration becomes more than workflow automation. It becomes the mechanism for enforcing decisions at speed. When a signal crosses a threshold, the system must be allowed to isolate, revoke, block, or quarantine without waiting for a committee meeting.
The new question for security leaders is brutally simple: if the enterprise runs at machine speed, what parts of the security response are still allowed to move at human speed?
Post-Quantum Cryptography Became a Migration Requirement
Post-quantum cryptography is easy to treat as a future problem because the most dramatic scenario depends on a quantum computer capable of breaking widely used public-key cryptography. The real reason it became an enterprise planning requirement in 2025 is less cinematic and more operational.
Cryptography is deeply embedded. It sits inside applications, infrastructure, identity systems, devices, and third-party products. It is also often invisible until something forces it to the surface. That makes cryptographic change slow, complex, and risky.
At the same time, long-lived data changes the threat model. Sensitive data captured today may be decrypted later if cryptographic protections become obsolete. This “harvest now, decrypt later” risk pushes security teams to treat cryptographic agility as a current obligation, not a future curiosity.
The shift also has a clear standards and guidance backbone. NIST finalised its first three post-quantum cryptography standards in 2024, including ML-KEM and two digital signature standards. The UK National Cyber Security Centre (NCSC) published a migration timeline with milestones extending through 2035, which forces organisations to plan now if they want to avoid rushed, brittle upgrades later.
How enterprises reacted in the moment
Enterprise reaction in 2025 looked like the start of a multi-year programme, not a set of urgent patches.
Organisations began with cryptographic inventories and discovery, because you cannot migrate what you cannot see. They assessed where vulnerable algorithms live across applications and data stores, and they prioritised areas where data must remain confidential for many years.
They also began pushing requirements down the supply chain. Procurement questions started to include post-quantum readiness, algorithm agility, and upgrade paths. Product and platform teams were pulled in because cryptography is not something security can swap out from the side.
How security architecture changes for post-quantum readiness in 2026
In 2026, the most important change is architectural. Enterprises will invest in crypto agility as a capability, not a one-off project.
That means abstraction layers that reduce hard-coded cryptography, clearer inventory and ownership, and technical patterns that allow algorithm replacement without rewriting entire systems. It also means treating cryptographic change as routine. Not because quantum is guaranteed tomorrow, but because cryptography will continue to evolve, and the enterprise needs to evolve with it on purpose.
The programmes that succeed will be the ones that accept a quiet truth: the hardest part of cryptography is not the maths. It is the migration.

Final Thoughts: Security Strategy Starts With Broken Assumptions
2025 broke defaults, not just systems. The supply chain taught enterprises that trust cannot be automated without verification. Regulation taught them that incidents are governance events as much as technical events. Identity sprawl made it clear that the enterprise is now powered by non-human actors, and those actors need rules, ownership, and oversight. AI compressed incident timelines until containment, not detection, became the defining capability. Post-quantum planning proved that long-horizon risk still demands near-term action.
Taken together, these moments point to the same conclusion: the future of security is not a bigger toolkit. It is sharper judgement, better design, and security programmes that assume the environment will behave in ways that feel unreasonable until the day it does.
If 2026 is the year security leaders are judged on how well their organisations withstand scrutiny, contain impact at speed, and prove resilience when trust fails, then the smartest move is to keep building your thinking muscle alongside your technical stack. EM360Tech’s security coverage is designed to help teams do exactly that, with analysis that stays close to operational reality rather than hype.







Comments ( 0 )