Cybersecurity disclosure is no longer a back-office task. It is a test of executive judgement, investor communication, and operational control.
The United States Securities and Exchange Commission’s four-day incident disclosure requirement forces leadership to prove they can determine materiality quickly, coordinate across legal and technical teams, and communicate decision-useful information with precision.
The clock begins when materiality is concluded, not when the alert fires, which means decision quality and documentation matter as much as speed. Investors now read these filings as a signal of how well a company understands its own risk, how confidently it governs, and how transparently it reports.

Treat the rule as a forcing function to improve the playbook, not a form to be rushed at the end. That is why this rule is less about filings and more about governance.
Understanding the Rule and Its Scope
The rule requires public companies to disclose any material cybersecurity incident within four business days of determining that the incident is material, using Form 8-K Item 1.05. It sits alongside annual disclosure obligations that cover risk management, strategy, and governance under Regulation S-K Item 106.
The clock does not start at first detection. It starts when the company concludes the incident is material. That is a judgement call that must be documented, evidenced, and defended. Domestic registrants and foreign private issuers are in scope, and subsidiaries can be relevant depending on impact materiality at the parent level.
There is a narrow path to delay. If the Attorney General determines that immediate disclosure would pose a substantial risk to national security or public safety, an initial delay of up to 30 days may be granted, with limited extensions if risk persists. The practical message for leadership is clear.
Treat delay as an exception with high scrutiny, not a fallback.
Determining Materiality — The Hardest Day One Decision
Materiality is the hinge of the rule. Get it right and the four-day process is manageable. Get it wrong and you either mislead investors or over-signal uncertainty to the market.
What ‘material’ really means in practice
Materiality turns on when a reasonable investor would consider the information important to decision making. That demands a balanced assessment of qualitative and quantitative factors.
Direct costs matter, but so do operational disruption, service degradation, data sensitivity, regulatory exposure, third-party and customer impact, and reputational risk. Materiality is rarely a single metric. It is a documented conclusion anchored in investor relevance.
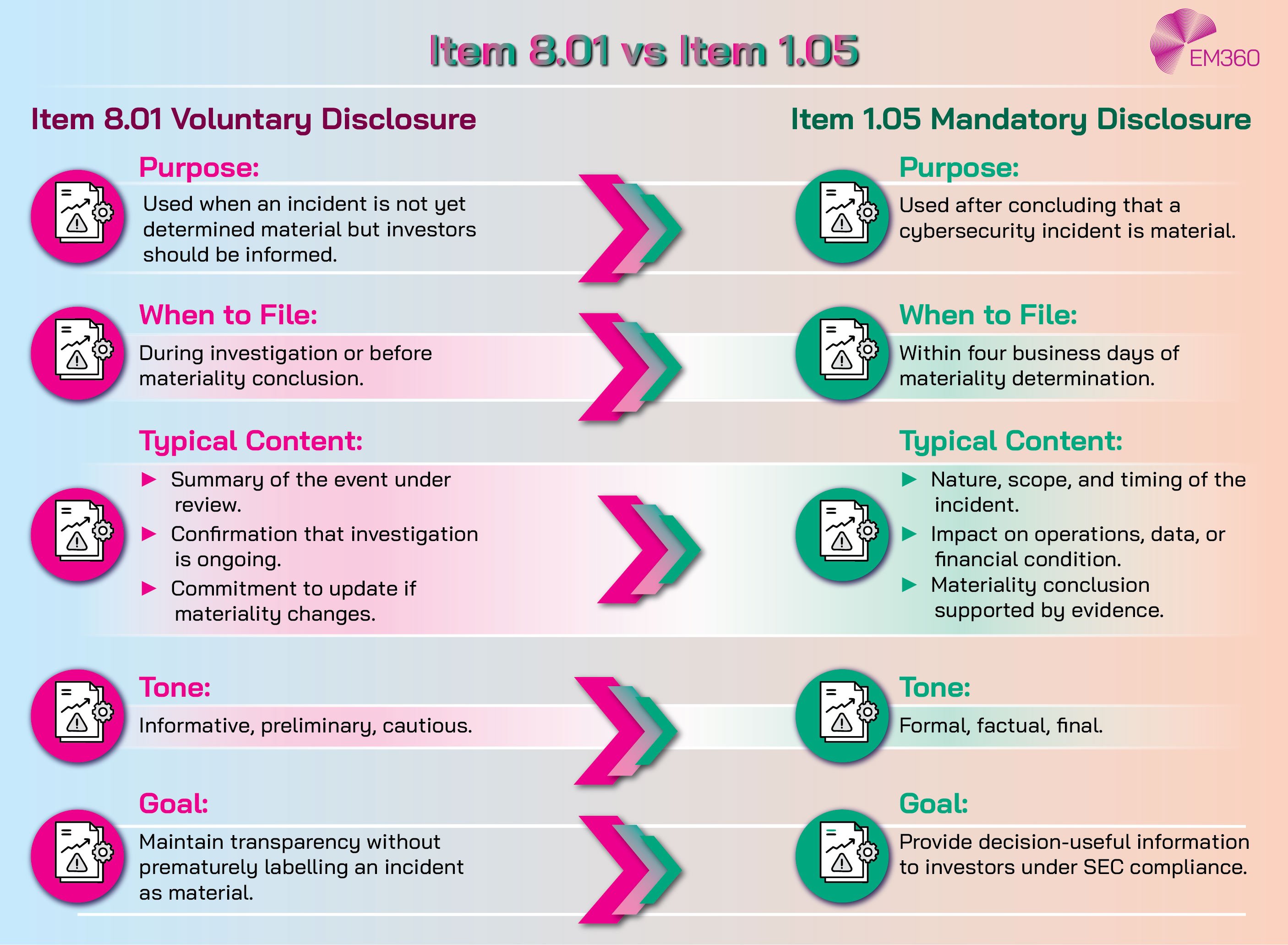
The 8.01 vs 1.05 dilemma
The market has adjusted to a practical rhythm. Use Item 8.01 for voluntary updates while facts are developing. Move to Item 1.05 once materiality is concluded. This avoids premature “material” labels that need later correction, preserves investor clarity, and shows discipline.
The pattern across recent filings confirms that cautious transparency is safer than rushing to a definitive call without an evidence trail.
From Breach to Disclosure — The Four-Day Countdown
Once materiality is determined, the four-day timeline compresses complex work into a short, auditable sequence.
Mapping the four-day process
Day zero is the decision. From that point, ownership must be clear. The CISO coordinates technical facts and scope. Legal leads materiality documentation and the narrative against the standard of investor relevance. Finance validates impact estimates and aligns with disclosure controls.
The board chair or delegated committee provides oversight and minutes. Investor relations and corporate communications prepare market-ready language consistent with the legal position. Draft, review, file.
As new facts emerge, file an amended 8-K to ensure accuracy. Brevity on day four is acceptable if the company amends promptly as evidence matures.
When the clock pauses
From Audits to Continuous Trust
Shift compliance from annual snapshots to embedded, automated controls that keep hybrid estates aligned with fast-moving global regulations.

If a credible national security or public safety risk exists, legal counsel should prepare a request through the Department of Justice process. Expect to document the risk basis, the specific harm posed by immediate disclosure, and the proposed delay period.
Keep a contemporaneous file. If a delay is denied or later lifted, the company returns to normal timing obligations and should be prepared to file quickly.
Inside the Disclosure — What Form 8-K Now Requires
The incident disclosure must be specific enough to inform investors without handing an attacker a playbook.
Incident disclosure content checklist
State what systems, data, or operations were affected. Describe the nature, scope, and timing of the incident. Explain the material impact or reasonably likely impact on the company’s financial condition and operations.
Avoid technical noise. Focus on clarity and investor relevance. If details would impede response or remediation, say so and commit to amending when appropriate.
Annual cyber risk and governance disclosure
Annual reporting must cover how the company identifies, assesses, and manages material cyber risks, the role of management, and the board’s oversight. This should align with existing enterprise risk management and be consistent with what the company says in other public reports.
Where applicable, ensure inline eXtensible Business Reporting Language (XBRL) tagging is handled correctly across the relevant items.
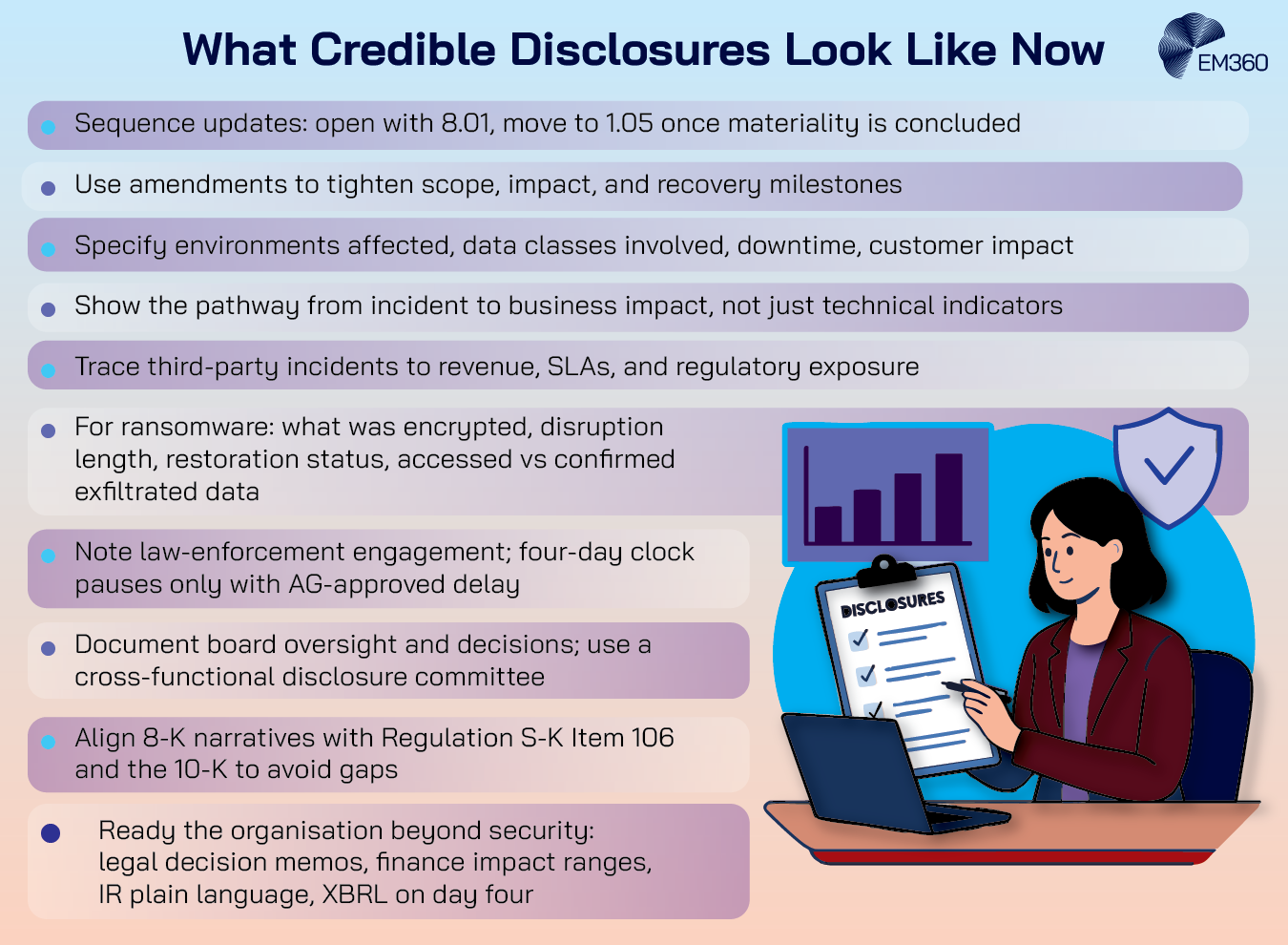
Lessons from Early Filings and Enforcement Trends
Early experience with the rule has already revealed how companies are adapting in practice, exposing both common missteps and emerging standards for what credible disclosure looks like. Many companies now open with Item 8.01 notices during the investigation phase and move to Item 1.05 once materiality is concluded.
This sequencing keeps investors informed without labelling an incident as material prematurely, then locks in the formal disclosure when the evidence supports it. Where facts evolve quickly, we see a pattern of an initial concise filing followed by one or more amendments that firm up scope, impact, and recovery milestones.
Disclosure quality is improving
Rethinking Trust in Automation
How supply chain trust, machine identities, PQ crypto and orchestration reshape security architecture and control planes.

Early filings often relied on generalities and defensive phrasing such as “no evidence of exfiltration at this time.” More recent filings describe which environments were affected, which data classes were involved, how long key systems were unavailable, and whether customer-facing services degraded.
The strongest examples explain the operational pathway from incident to impact, not just technical indicators, and state what has been restored versus what remains under containment or rebuild.
Third-party incidents feature heavily
Companies are documenting how a vendor compromise or a shared platform outage translated into their own risk, then walking through dependency mapping, compensating controls, and customer communication.
This matters for materiality because investor relevance often turns on whether a supplier’s issue caused revenue loss, missed service-level commitments, or regulatory exposure for the registrant itself.
Ransomware narratives are maturing
Rather than naming threat groups or negotiating stances, better filings identify what was encrypted, the duration of disruption, the progress of restoration, and any permanent loss of noncritical data.
Where theft occurred, some issuers now separate “data accessed” from “data confirmed exfiltrated,” committing to updates as forensics complete and notifications are issued.
Coordination with law enforcement appears more structured
Companies note engagement with agencies while making clear that such coordination does not pause the four-day timeline unless an Attorney General delay is granted. Where delays are approved, issuers reference the basis at a high level and prepare to file immediately when the delay lifts, often with a fuller set of verified facts.
Board oversight is moving from reactive briefings to pre-planned governance
Minutes reflect who attended, what evidence was reviewed, and the basis for the materiality conclusion. Several issuers have designated a standing cyber disclosure committee that brings Legal, Security, Finance, Audit, and Investor Relations into one decision room. This reduces rework and shortens time to a defensible narrative.
Consistency across reports is under closer scrutiny
Investors are comparing Item 1.05 filings, subsequent amendments, and the annual Regulation S-K Item 106 disclosure for alignment. Gaps between the incident narrative and the stated risk management approach invite questions.

How Tech Bans Reshape Markets
Assess how blanket restrictions on digital platforms can redirect investment, stall ecosystems and create new competitive moats.
Leading companies reconcile terminology, metrics, and control descriptions so the incident story fits the governance story in the 10-K.
Issuer readiness is broader than security
Legal teams have built decision memos for materiality. Finance has playbooks for estimating ranges of financial impact without overcommitting. Investor Relations prepares plain-language explanations that avoid technical ambiguity. Reporting teams are set up for inline eXtensible Business Reporting Language (XBRL) tagging on day four rather than retrofitting later.
The through-line is discipline. Where early filings were hurried and vague, the current benchmark is concise, specific, and consistent with how the company manages risk year round.
Building a Compliant and Defensible Disclosure Process
A resilient programme turns regulatory pressure into operational clarity. The goal is a playbook that works under stress and survives scrutiny.

Materiality workflow integration
Connect incident response with IRM, legal, finance, audit, investor relations, and communications. Define escalation paths, decision criteria, and quorum for materiality determination. Pre-agree thresholds and qualitative factors that trigger a formal review. Build a decision memo template so the analysis is consistent every time.
Documentation and evidence management
Record the facts considered, the alternatives weighed, and the final determination with timestamps. Capture drafts, approvals, and board touchpoints. Treat the file as if regulators and investors will read it later. The same applies to decisions about amendment timing and content.
Strengthening governance and preparedness
Schedule board and executive training on the standard for investor relevance. Run tabletop exercises that simulate hard choices, including third-party breaches and incomplete forensics.
Align your disclosure narrative with established frameworks such as NIST CSF 2.0 and ISO 27001 so that technical controls, governance, and reporting speak the same language. The outcome is not only faster filings. It is better decision making.
Strategic Implications — From Compliance to Investor Trust
Why SIEM Now Anchors Cyber Risk
Rising attacks are forcing leaders to treat SIEM as a strategic control point for detection, resilience and regulatory assurance.

Timely, plain-spoken disclosures build credibility with investors who understand that incidents are inevitable. What differentiates leaders is the quality of judgement, the speed of coordination, and the coherence between incident updates, governance disclosures, and enterprise risk reporting.
Cyber governance now sits alongside financial governance as a marker of management quality. Treat the four-day rule as a forcing function to strengthen both.
Final Thoughts: Compliance Is the Floor, Accountability Is the Standard
The four-day rule is not about racing the clock. It is about proving that leadership can recognise what matters, explain it clearly, and act in investors’ interests. The companies that document materiality well, file with precision, and follow through with consistent governance will earn trust faster than those who treat disclosure as damage control.
If your programme needs a sharper playbook and a stronger decision trail, explore EM360Tech’s latest analyses on regulation, resilience, and board-level cyber governance to turn obligation into advantage.






Comments ( 0 )