How do you build trust in a digital world where the perimeter has vanished? When breaches cost millions and attackers slip through overlooked cracks, security leaders can’t rely on static walls or blind faith.
Zero trust security vendors promise to verify every user, assess every device, and grant just enough access — no more, no less. The following guide demystifies the model, unpacks market trends, and profiles the zero trust solutions most capable of supporting enterprise growth and resilience.

Understanding Zero Trust Security
For all the hype, zero trust is not a product you plug in but a mindset. It’s about removing implicit trust from your network architecture and constantly questioning who or what is asking for access.
What zero trust security means for enterprises
Zero trust starts with identity: don’t assume a device or user is safe simply because they passed a single check or sit behind the firewall. Instead, you authenticate every request with multiple factors, ensure the device is healthy, and grant only the minimum permissions necessary for the task.
Microsegmentation confines users and workloads to their own digital rooms, while continuous verification watches for abnormal behaviour and responds quickly. Taken together, these controls form a zero trust architecture aligned with standards such as NIST SP 800‑207 and CISA’s maturity model.
They allow enterprises to manage risk dynamically, rather than trusting and forgetting.
Why data and security leaders are investing now
Security is no longer just a technical problem; it’s a board‑level issue. The average data breach now carries a seven‑figure price tag, and response times are shrinking thanks to automation and AI. Regulators around the world are mandating stricter controls and greater accountability, while customers expect companies to safeguard their data.
Against this backdrop, zero trust isn’t just a buzzword: it’s a strategy for reducing attack surfaces, meeting compliance requirements, and building resilience in hybrid and multi‑cloud environments. For decision‑makers, the question is no longer “Do we need zero trust?” but “Which solution will take us there?”
Key Trends Shaping the Zero Trust Vendor Landscape
The market for zero trust is maturing quickly. Enterprises must look beyond marketing hype to understand where the industry is heading.
Convergence of identity and network security
Identity and network controls are merging. Leading vendors now integrate user signals — who you are, what device you’re using, where you’re coming from — directly into network enforcement.
Partnerships such as Okta with Palo Alto Networks illustrate this shift: identity platforms feed risk data to network gateways, allowing policies that change in real time. This convergence reduces blind spots and simplifies management, aligning security with how people actually work.
Zero Trust delivered via SSE and SASE
Zero Trust Network Access began as a niche tool to replace VPNs. Today, it’s delivered as part of broader Security Service Edge (SSE) and Secure Access Service Edge (SASE) platforms.
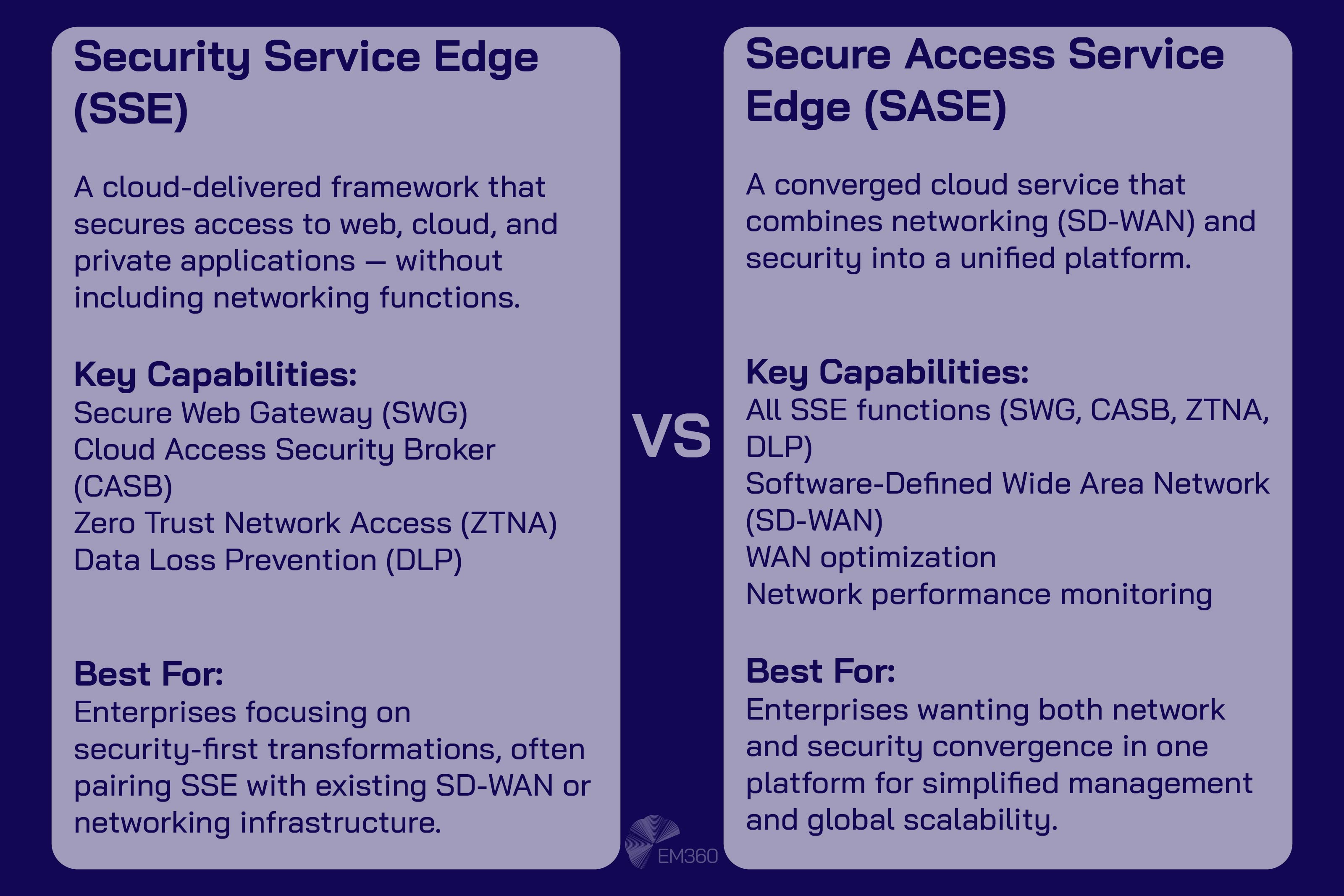
By combining ZTNA with secure web gateways, CASB and data‑loss prevention into a single cloud‑native stack, SSE and SASE provide consistent policies and lower latency for a dispersed workforce. For enterprises, this means less integration pain and fewer chances for configuration drift.
Adoption maturity and capability gaps
Interest in zero trust is high, but capability gaps remain. Surveys show that many organisations still grant broad network access or rely on VPNs, and only a small percentage have implemented just‑in‑time access or strict least‑privilege controls.
This leaves room for lateral movement and insider abuse. When evaluating vendors, look for those that support advanced policy engines, robust device posture assessment and continuous monitoring — the building blocks of mature adoption.
How to Evaluate Zero Trust Security Vendors
Choosing a vendor is not a game of buzzword bingo. Use a structured approach to find the right fit.
Core capabilities to require

Why UEM Now Anchors Security
See how unified endpoint platforms secure a dispersed workforce and centralize control across laptops, mobiles and IoT devices.
Start with integration. The platform should work seamlessly with your existing identity provider, enforce adaptive multi‑factor authentication and check device posture on every request. Look for built‑in data‑loss prevention, real‑time threat analytics and policy engines capable of microsegmentation and automated remediation. The solution should integrate with your SIEM and SOAR to streamline incident response and provide context.
Performance and scale considerations
User experience matters. Ask about global points of presence and latency guarantees. A multitenant cloud may deliver consistent performance, while hybrid deployments might better suit industries with strict data locality requirements. Ensure the platform can scale with your organisation, whether you’re adding new users, devices or applications.
Compliance, reporting and governance
Auditability is essential. Vendors should provide granular logs, policy versioning and compliance artefacts for standards like ISO 27001 and SOC 2. Clear reporting makes it easier to demonstrate due diligence to regulators and customers and helps your team spot gaps before they become issues.
The Top 10 Zero Trust Security Vendors in 2025
The zero trust landscape is crowded, but these ten top zero trust companies stand out for enterprise readiness. Presented alphabetically, each profile details who they are, why their features matter, what they do well, where they fall short and who they serve best.
Check Point – Infinity / Harmony
Check Point is best known for its firewalls, but the Infinity platform shows how far the company has evolved. Infinity unifies network, cloud and endpoint protection under one management layer, while Harmony secures remote workers and SaaS applications.
Enterprise-ready features
Infinity delivers consistent security across data centres, cloud workloads and remote devices by centralising policy creation and distribution. Automated updates push threat intelligence and configuration changes through your pipelines, keeping controls in sync.
AI‑driven detection analyses network traffic and endpoint behaviour to stop known malware and unknown threats alike. Harmony adds web filtering, email security and identity‑based access, extending zero trust to remote workers without requiring multiple agents.
For regulated industries, Infinity provides compliance dashboards and reporting that map to frameworks such as NIST and GDPR.
Pros
Inside Phishing-Resistant MFA
Explore device-bound passkeys, security keys and the integration pitfalls that can derail an enterprise move to resilient authentication.
- Unified coverage for network, cloud and endpoints.
- Industry-leading threat intelligence with behavioural analytics.
- Single console simplifies operations and reduces misconfigurations.
- Automation propagates policy changes quickly.
- Strong option for organisations already invested in Check Point.
Cons
- Perception as a legacy vendor may deter start‑ups and cloud‑native teams.
- Broad feature set can introduce complexity.
- Innovation cadence slower than some cloud‑only competitors.
Best fit
Enterprises with hybrid infrastructures looking to consolidate multiple security tools into one platform. Particularly well-suited if you already run Check Point firewalls and want to extend protection to remote users and SaaS applications.
Forescout – Continuum Platform
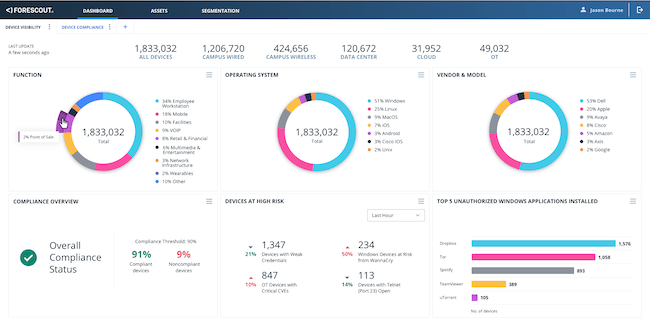
Forescout focuses on what many overlook: unmanaged and unagentable devices. The Continuum Platform discovers, classifies and secures everything from laptops to factory sensors.
Enterprise-ready features
Forescout’s agentless technology discovers devices across IT, OT and IoT networks, even in rugged environments where deploying agents isn’t an option. It assigns risk scores based on device type, configuration and behaviour, then enforces segmentation policies automatically.
This stops attackers from moving laterally and allows you to quarantine non-compliant devices without interrupting operations. Continuum integrates with SIEM, NAC and EDR tools to provide context and coordinate responses.
For large enterprises juggling compliance, its continuous monitoring and policy automation help meet regulatory requirements without manual intervention.
Pros
- Agentless discovery provides full visibility across diverse devices.
- Real-time risk scoring prioritises fixes.
- Automated segmentation limits lateral movement.
- Continuous compliance supports zero trust maturity.
- Strong interoperability with existing NAC and SIEM tools.
Cons
- User-level context may require a separate identity solution.
- Policy tuning can be challenging in dynamic OT environments.
- Some deployments need hardware appliances.
Best fit
Organisations in energy, healthcare and manufacturing that manage a mix of IT and OT systems. Also useful for enterprises looking to automate compliance and segmentation without deploying agents.
Fortinet – Security Fabric + SASE
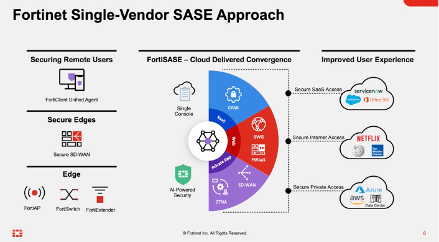
Fortinet brings networking and security together. Security Fabric stitches together firewalls, SD‑WAN, endpoint protection and cloud security, while its SASE service extends these capabilities to remote workers.
Enterprise-ready features

Mitigating Breach Risk with MFA
Quantify how layered verification reduces account takeover exposure, and what to demand from vendors to address SMS, token and biometric weaknesses.
Fortinet’s custom processors and hardware acceleration deliver low-latency performance for branch offices and data centres. Universal ZTNA ensures consistent, least‑privilege access whether users connect from the headquarters or home.
Built-in network access control discovers and isolates IoT devices, while FortiManager provides a single console for deploying policies and monitoring compliance. Fortinet’s broad partner ecosystem means you can integrate identity, analytics and automation solutions without bespoke development, simplifying deployment for large organisations.
Pros
- Converged networking and security reduce operational complexity.
- Hardware acceleration supports high throughput and low latency.
- Unified console eases policy management.
- Flexible deployment across on‑premises and cloud.
- Extensive ecosystem enables custom integrations.
Cons
- Licensing can be confusing across multiple modules.
- Some identity features require third‑party tools.
- Large feature set may overwhelm smaller teams.
Best fit
Enterprises already invested in Fortinet hardware or looking a high‑performance SD‑WAN with integrated security. Particularly strong for large branch networks and organisations requiring consistent policy enforcement across on‑premises and cloud resources.
Google BeyondCorp Enterprise
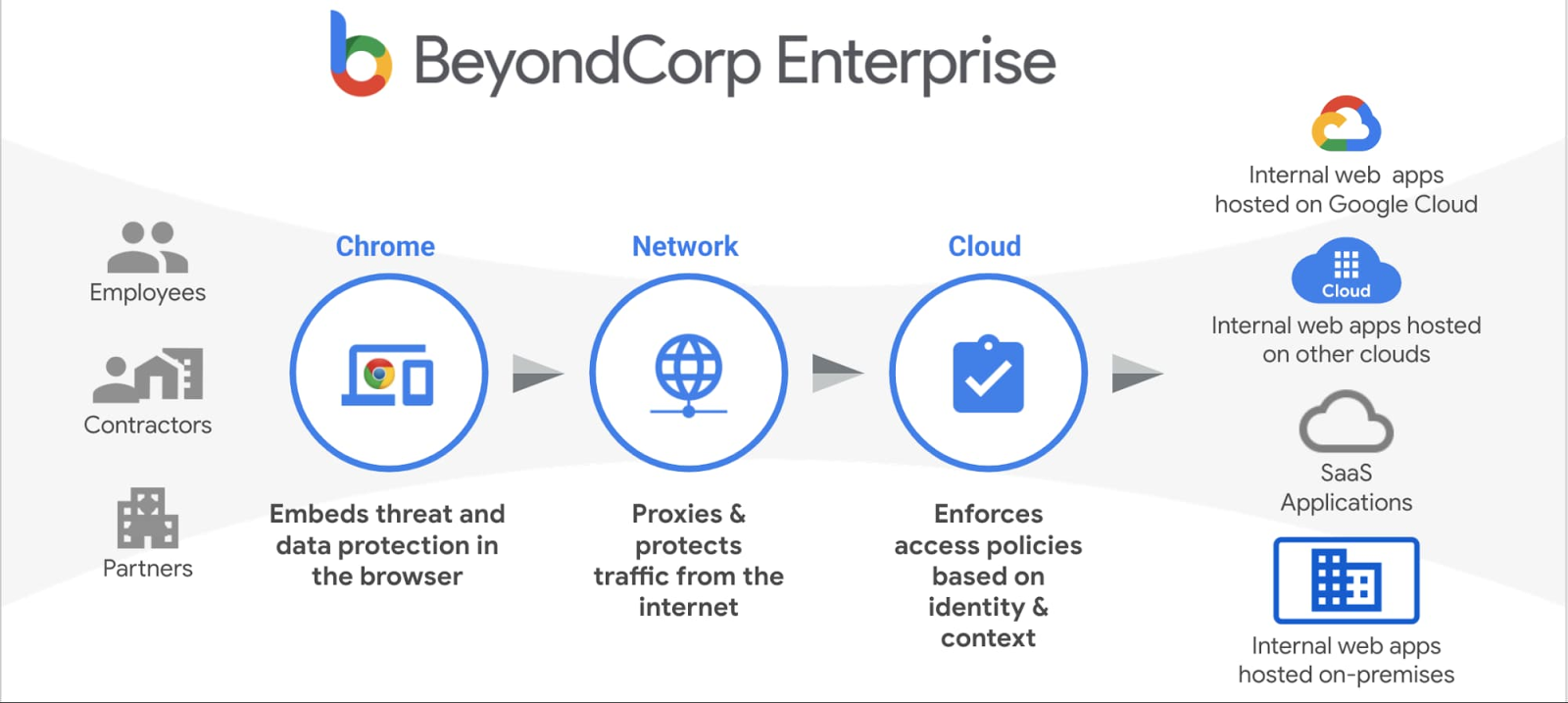
Born from Google’s internal security model, BeyondCorp Enterprise offers browser‑based zero trust access on a global scale without agents or VPNs.
Enterprise-ready features
BeyondCorp continuously evaluates user and device context, using the Chrome browser as the enforcement point. It supports phishing-resistant authentication methods, such as FIDO2 security keys, and uses malware sandboxing to scan downloads before they reach endpoints.
Device-based rules restrict API and console access to approved hardware, and built-in DLP detects and blocks sensitive data exfiltration. Integration with Google Cloud services offers consistent controls across GCP workloads, while connectors allow access to on-premises and multi-cloud environments.
Detailed audit logs support compliance with FedRAMP and other standards.
Pros
- Agentless, browser-based deployment speeds adoption.
- Advanced threat and data protection baked into the access layer.
- Leverages Google’s global network for reliable performance.
- Context-aware policies that adapt to device and user risk.
- Tight integration with Google Cloud and Workspace services.
Cons
When Remote Work Breaks Trust
How rushed pandemic-era tools reshaped workplace communication risk and why zero trust, not policy alone, must anchor security strategy.

- Non-web apps need additional connectors.
- Works best with Chrome; experience on other browsers may be limited.
- Less appeal for organisations with no Google footprint.
Best fit
Companies running workloads on Google Cloud or using Google Workspace for collaboration. Also attractive for enterprises looking to phase out VPNs while securing a mobile workforce with strong phishing-resistant authentication.
Microsoft – Entra ID + Defender Stack
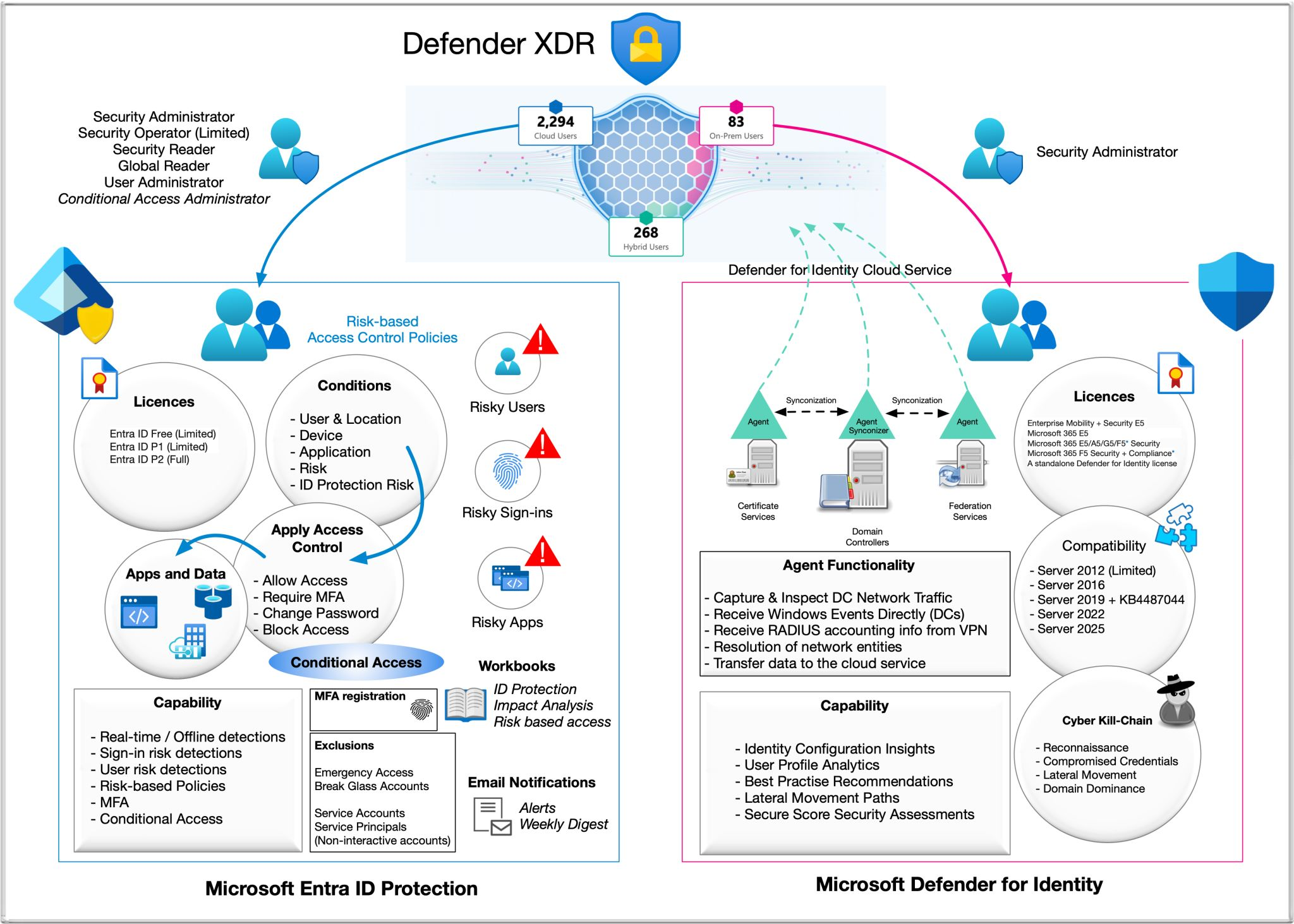
Microsoft’s zero trust approach combines Entra ID (formerly Azure AD) for identity management with the Defender suite for threat protection, SaaS security and compliance.
Enterprise-ready features
Conditional Access policies evaluate identity, device health, location and user risk to determine how and when to enforce multi-factor authentication or block access. Defender for Cloud Apps discovers shadow IT, assesses SaaS configuration and enforces policies across multiple cloud services.
Integration with Microsoft Purview brings unified data classification and retention policies across Office 365, Teams and SharePoint. The platform’s threat intelligence surfaces suspicious patterns, while extensive compliance certifications simplify audits.
For hybrid and on-premises workloads, Microsoft’s integration with Windows Server and Active Directory eases migration.
Pros
- End-to-end integration with Microsoft productivity and cloud platforms.
- Dynamic, context-aware access policies.
- Deep SaaS visibility and data protection.
- Strong compliance and reporting capabilities.
- Modular licensing for different organisation sizes.
Cons
- Advanced features are often locked behind premium tiers.
- Non-Microsoft environments require more integration effort.
- Complexity rises when linking legacy on-premises applications.
Best fit
Enterprises deeply invested in Microsoft 365, Azure and Windows. Ideal for organisations looking unified identity, productivity and security with built-in compliance and threat analytics.
Okta Identity Cloud
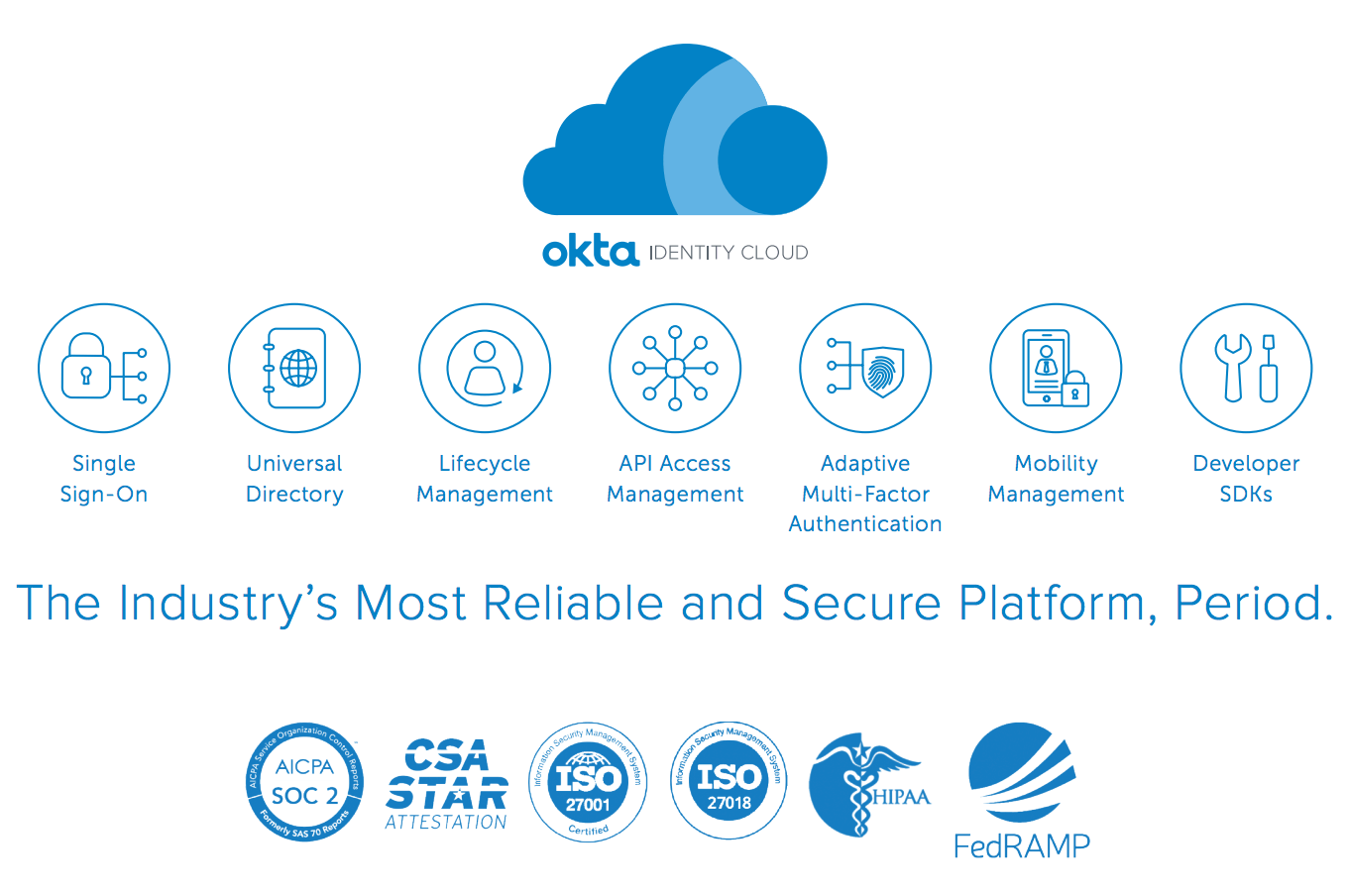
Okta is an identity-first platform that delivers multi-factor authentication, single sign-on and lifecycle management across thousands of cloud and on-premises applications.
Enterprise-ready features
Okta’s adaptive MFA uses signals such as location, device posture and user behaviour to determine the right level of challenge. Its Integration Network of more than 7,000 connectors makes onboarding new applications easy and supports standard protocols like SAML, OIDC and SCIM.
Lifecycle management automates provisioning and deprovisioning, ensuring users only have access when they need it. A privileged access module adds just-in-time controls for admin accounts, and partnerships with vendors like Zscaler allow context from Okta to inform network policies.
Detailed logs and policy controls help meet compliance requirements.
Pros
- Identity-focused architecture simplifies governance.
- Contextual MFA balances security and user convenience.
- Massive integration catalogue reduces custom work.
- Automated provisioning minimises manual errors.
- Privileged access module protects high-risk assets.
Cons
- Needs complementary tools for network and endpoint security.
- Costs can add up with multiple modules.
- Legacy or bespoke applications may need custom connectors.
Best fit
Organisations prioritising user experience and centralised identity governance. Perfect for enterprises with large SaaS portfolios or those adopting a best‑of‑breed security stack where identity is the linchpin.
Palo Alto Networks – Prisma Access
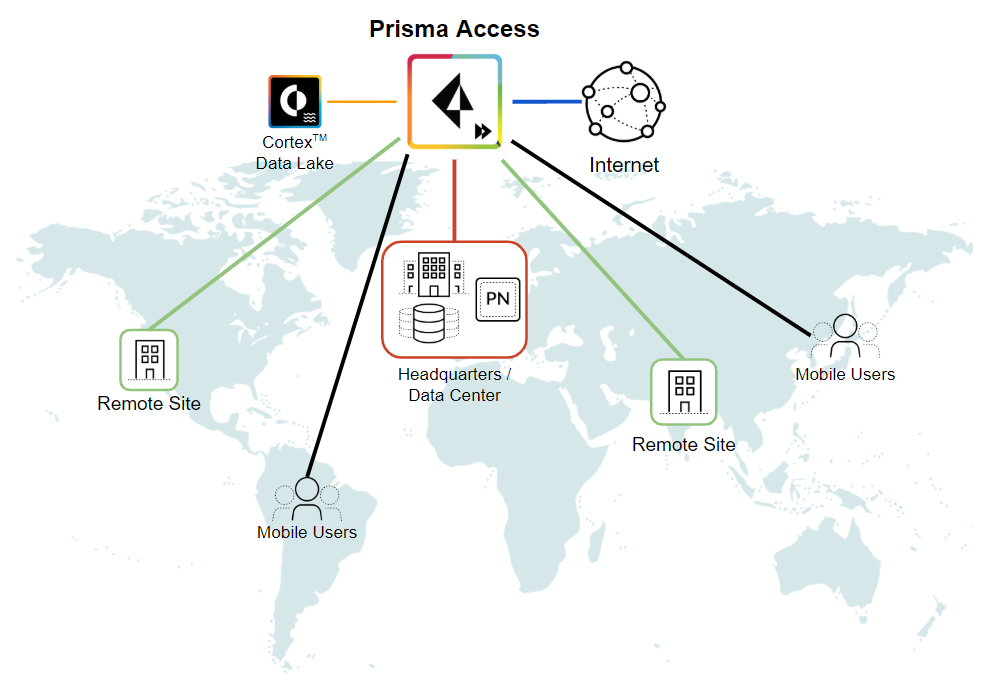
Prisma Access is Palo Alto Networks’ flagship SASE platform, combining ZTNA, secure web gateway, CASB and firewall-as-a-service to deliver consistent policies without VPNs.
Enterprise-ready features
Powered by machine learning, Prisma Access inspects all traffic—including encrypted sessions—to block phishing, malware and ransomware. Remote browser isolation enables risky websites to be run in a sandbox so that malicious code never touches the user’s device.
SaaS security posture management assesses the configuration of cloud applications and applies policies that prevent data leaks. The firewall-as-a-service component maintains centralised control and signature updates without on-premises appliances. Identity integrations allow policies to adapt based on user role and risk.
For multinational organisations, global points of presence and strict SLAs ensure users experience low latency wherever they are.
Pros
- All-in-one SASE service with comprehensive coverage.
- AI-driven threat detection keeps pace with evolving tactics.
- Eliminates VPN complexity by delivering true least-privilege access.
- Remote browser isolation protects endpoints from malicious sites.
- Seamless identity integration supports context-based policies.
Cons
- Premium pricing compared to some rivals.
- Requires careful tuning to minimise false positives.
- Migration from traditional networks can be time-consuming.
Best fit
Large enterprises with dispersed users and a complex mix of applications. Ideal for those looking to replace VPNs and unify security across web, SaaS and private applications in a single cloud-based platform.
Prophaze
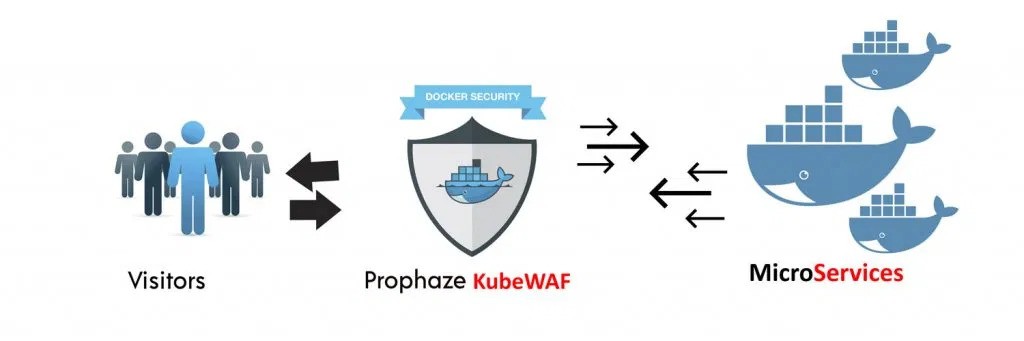
Prophaze is a Kubernetes-native web application firewall and API security platform that uses machine learning to defend modern, microservice environments.
Enterprise-ready features
Prophaze learns baseline behaviour for each microservice and detects anomalies that signal attacks, including injection attempts and business logic abuse. Its virtual patching capability blocks exploit paths before official fixes are released, buying time for developers to remediate vulnerabilities.
DDoS mitigation and rate limiting keep applications running under stress, while API security functions inspect request and response payloads to prevent data leaks and sensitive information exposure.
Policies are generated automatically and adapt as workloads evolve, with dashboards providing insights into attack patterns and compliance status.
Pros
- Tailored for Kubernetes and microservice architectures.
- Machine learning adapts to emerging threats.
- Virtual patching reduces exposure to zero-day exploits.
- Automated policies lower operational burden.
- Detailed analytics enable continuous improvement.
Cons
- Focuses solely on application and API security.
- Smaller ecosystem and community than more established vendors.
- False positives may require tuning during initial deployment.
Best fit
DevOps-driven organisations running containerised workloads that need hands-off protection for APIs and web applications. Particularly valuable for teams wanting to automate security without slowing down rapid release cycles.
StrongDM
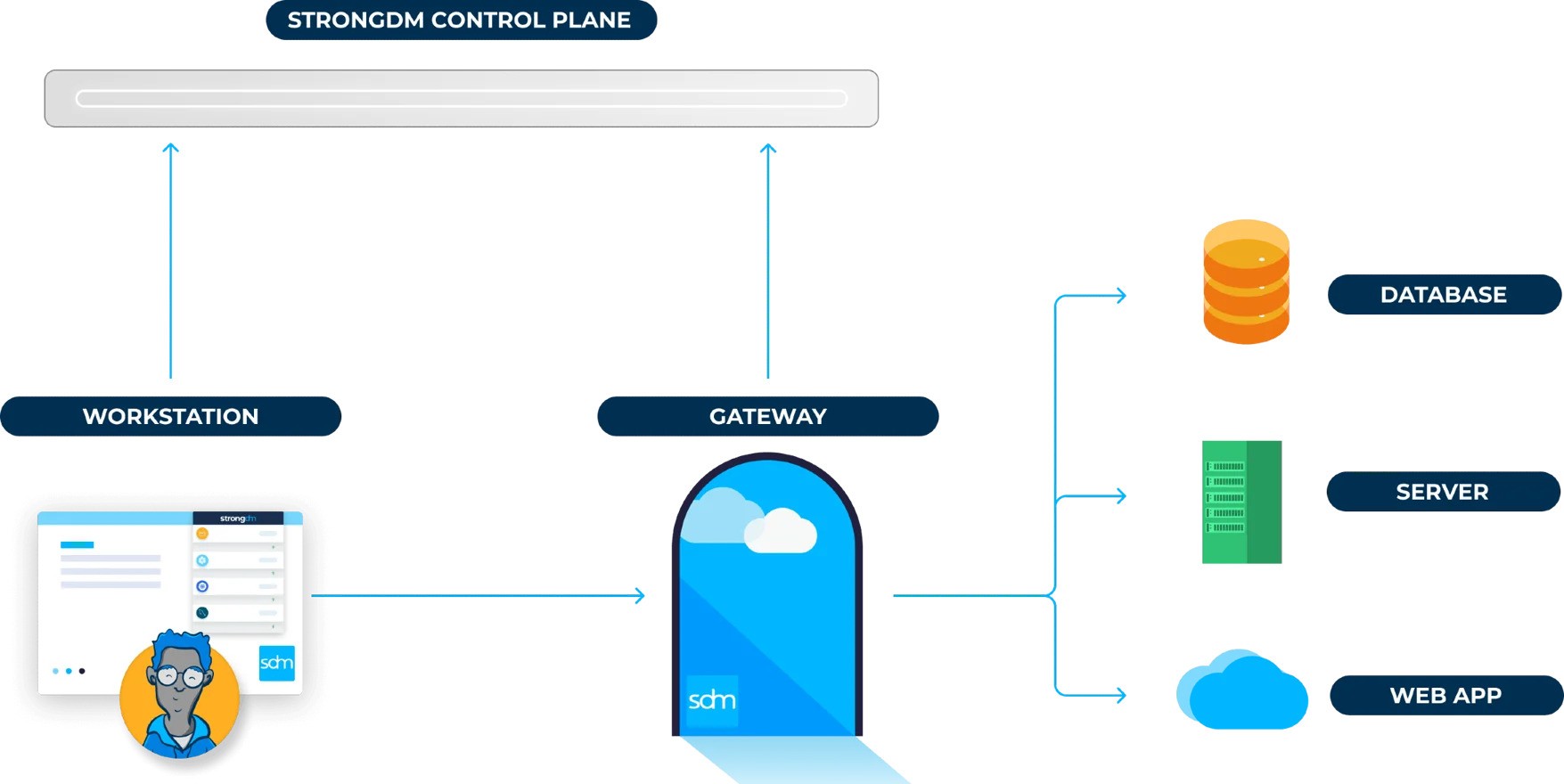
StrongDM delivers zero trust privileged access management for servers, databases and Kubernetes clusters, providing just-in-time access and complete audit trails.
Enterprise-ready features
StrongDM grants access only when needed, then automatically revokes permissions once a session ends. It integrates with existing secret stores and vaults, allowing teams to avoid moving or duplicating credentials. Fine-grained policies define exactly what actions a user can take, and role-based access controls align permissions with job functions.
Continuous authorization monitors user actions in real time and modifies access if risk increases. A frustration-free interface encourages adoption, while audit logs capture every session for compliance and forensic investigations. The platform’s context-aware policies adapt dynamically based on user, device and location.
Pros
- Just-in-time workflows reduce standing privileges and risk.
- Integrates seamlessly with existing vaults and secrets.
- Fine-grained permissions and thorough audit trails support compliance.
- Continuous authorization adjusts access in real time.
- User-friendly interface encourages adoption among technical teams.
Cons
- Focus is on infrastructure; network and endpoint controls require other tools.
- Requires careful policy design and planning.
- Smaller market footprint than some mainstream vendors.
Best fit
DevOps, SRE and infrastructure teams needing to control privileged access without refactoring applications. Excellent for organisations that want to integrate zero trust PAM into existing secret management workflows.
Zscaler – Zero Trust Exchange
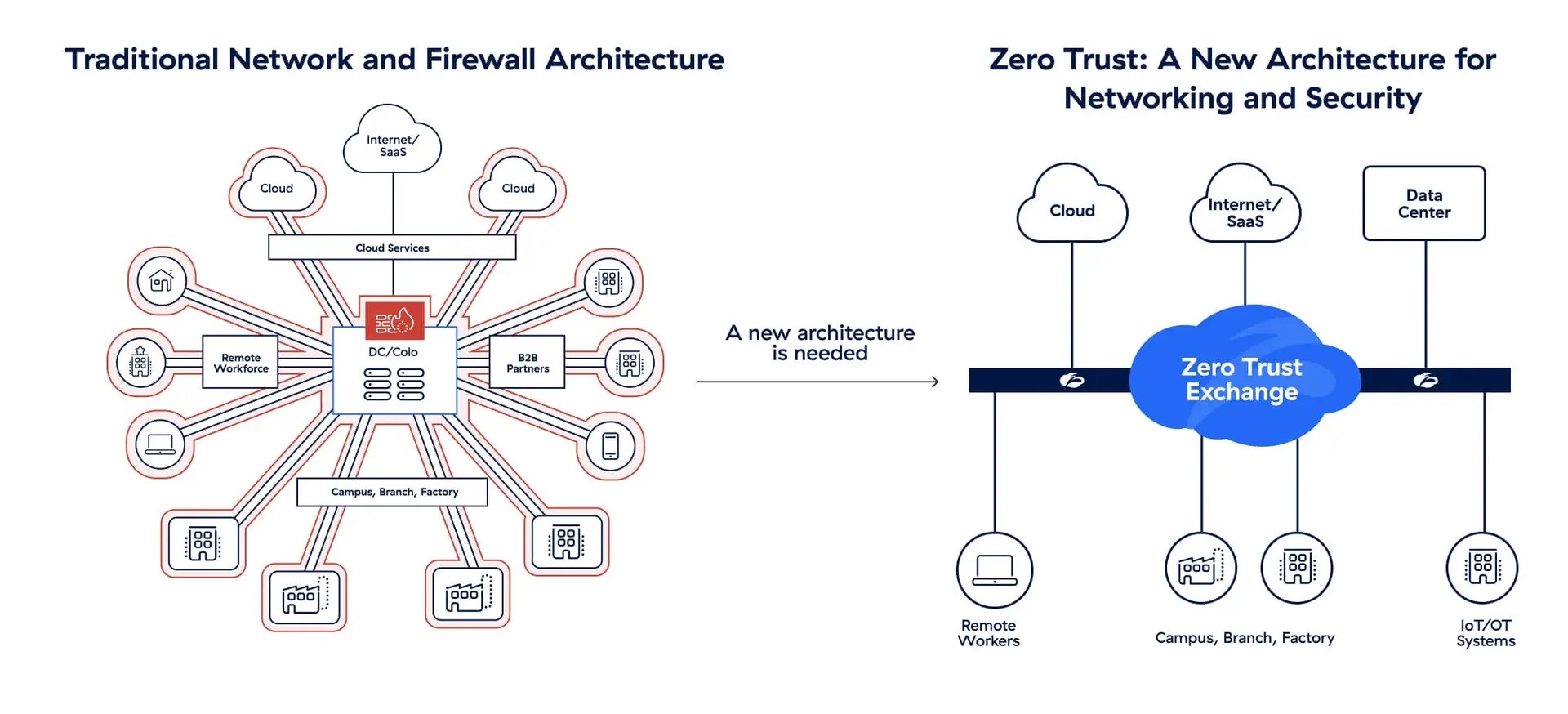
Zscaler’s Zero Trust Exchange is a cloud-native platform that directly connects users to applications instead of networks, eliminating VPNs and hiding internal resources from prying eyes.
Enterprise-ready features
Zscaler enforces least-privilege access based on identity and context. Its proxy architecture decrypts and inspects traffic—including TLS sessions—to block threats and prevent data exfiltration.
Integrated SSE platforms provide secure web gateways, CASB, cloud security posture management and data loss prevention, reducing the need for disparate tools. Applications are segmented without network changes, preventing lateral movement if credentials are compromised.
A global, multitenant architecture delivers consistent low-latency performance, and integrations with identity providers enable single sign-on and adaptive MFA. Centralised management offers visibility and policy controls, while logs facilitate compliance.
Pros
- Replaces VPNs and simplifies network architecture.
- Deep inspection and DLP improve security.
- Unified stack reduces tool sprawl.
- Multitenant cloud architecture scales globally.
- Wide range of integrations with identity and security partners.
Cons
- Proxy model may require network redesign.
- Pricing and licensing can be complex.
- Latency can be a concern for extremely sensitive workloads.
Best fit
Global enterprises looking to standardise zero trust across users, devices and applications. Especially suitable for organisations moving away from traditional VPNs and looking for a comprehensive, cloud-based platform.
Common Pitfalls to Avoid When Selecting a Vendor
Even the best technology won’t succeed without a thoughtful implementation. Be aware of these traps.
Over-relying on vendor marketing claims
Slick presentations don’t equal real-world performance. Don’t take claims at face value. Ask for references from similar organisations, run proof-of-concept trials and request clear evidence of how a feature improves security or user experience in practice.
Ignoring integration and migration complexity
Zero trust touches identity, network, endpoint and cloud systems. Assuming it will “just work” can lead to delays, unexpected costs and frustrated users. Map out dependencies, verify API compatibility and plan phased rollouts with enough time for testing and training.
Underestimating policy management and change control
Granular policies are the heart of zero trust, but poorly designed rules can block legitimate work or leave gaps for attackers. Use simulation tools and pilot groups to test new policies before enforcement. Establish a governance process that includes security, IT and business stakeholders, and schedule regular reviews.
FAQs on Zero Trust Security Vendors
Which Zero Trust network access provider is most reliable?
Reliability depends on your specific needs. Consider factors such as global presence, uptime guarantees, integration with your identity systems and support quality. Zscaler and Palo Alto Networks offer robust, cloud-native platforms; Fortinet pairs strong on-premises hardware with cloud services; Forescout and Microsoft excel at compliance and visibility for regulated industries.
Why is ZTNA better than VPN?
VPNs create a tunnel into your network, granting broad access once inside. Zero Trust Network Access connects users directly to applications based on identity and context, limiting lateral movement and removing the need to backhaul traffic. This improves security and user experience, especially for remote and hybrid work.
What are the five pillars of Zero Trust?
While frameworks differ, most include: verifying every user; validating every device; enforcing least‑privilege access; segmenting networks and workloads to contain breaches; and continuously monitoring and responding to anomalies. Together, these pillars build an adaptive, resilient security posture.
Final Thoughts: Zero Trust Success Starts With the Right Vendor Fit
Zero trust isn’t a product you install but a strategy you adopt. To succeed, define what you need to protect, the regulations you must meet and the experience you want for users. Evaluate vendors using clear criteria: integration with your identity stack, device posture checks, policy automation, performance and compliance support.
Run pilots, involve stakeholders and plan for incremental rollout. The vendors profiled here offer strong foundations, but the right choice depends on your architecture and culture. For further insights and case studies to guide your zero trust strategy, explore the resources at EM360Tech — they’ll help you turn vision into practice with confidence.







Comments ( 0 )