Blockchain is slowly weaving itself into everyday business. It now moves money across borders, tracks goods through supply chains, and anchors how people prove who they're online. But the real risks aren’t buried deep in the code.
They’re in the places where people connect to it — where someone signs a transaction, where one system talks to another, and where attackers wait for the smallest mistake. Over the past year, investigations have shown a clear shift. Attackers aren’t trying to break the blockchain itself.
Instead, they’re tricking the people and tools that use it.
Phishing sites, fake wallet pop-ups, and “drainer” kits that empty accounts in seconds have become common. Research from Chainalysis, TRM Labs, and other industry trackers all point to the same reality: what fails most often isn’t the technology, but the way it’s used.

That’s where modern blockchain cybersecurity comes in. The focus now is on protecting the systems, applications, and people who rely on blockchain — not the ledger that records their actions.
Real-time visibility across wallets and contracts, strong key management, and analytics that turn data into early warnings are becoming the backbone of digital trust. The next wave of resilience will come from controls that stop fraud before it spreads, contain incidents quickly, and make governance something you can prove, not just promise
Understanding Blockchain Cybersecurity
Securing blockchain is only half the story. To keep real people and real businesses safe, we also need to secure everything that touches it.
What blockchain cybersecurity really means
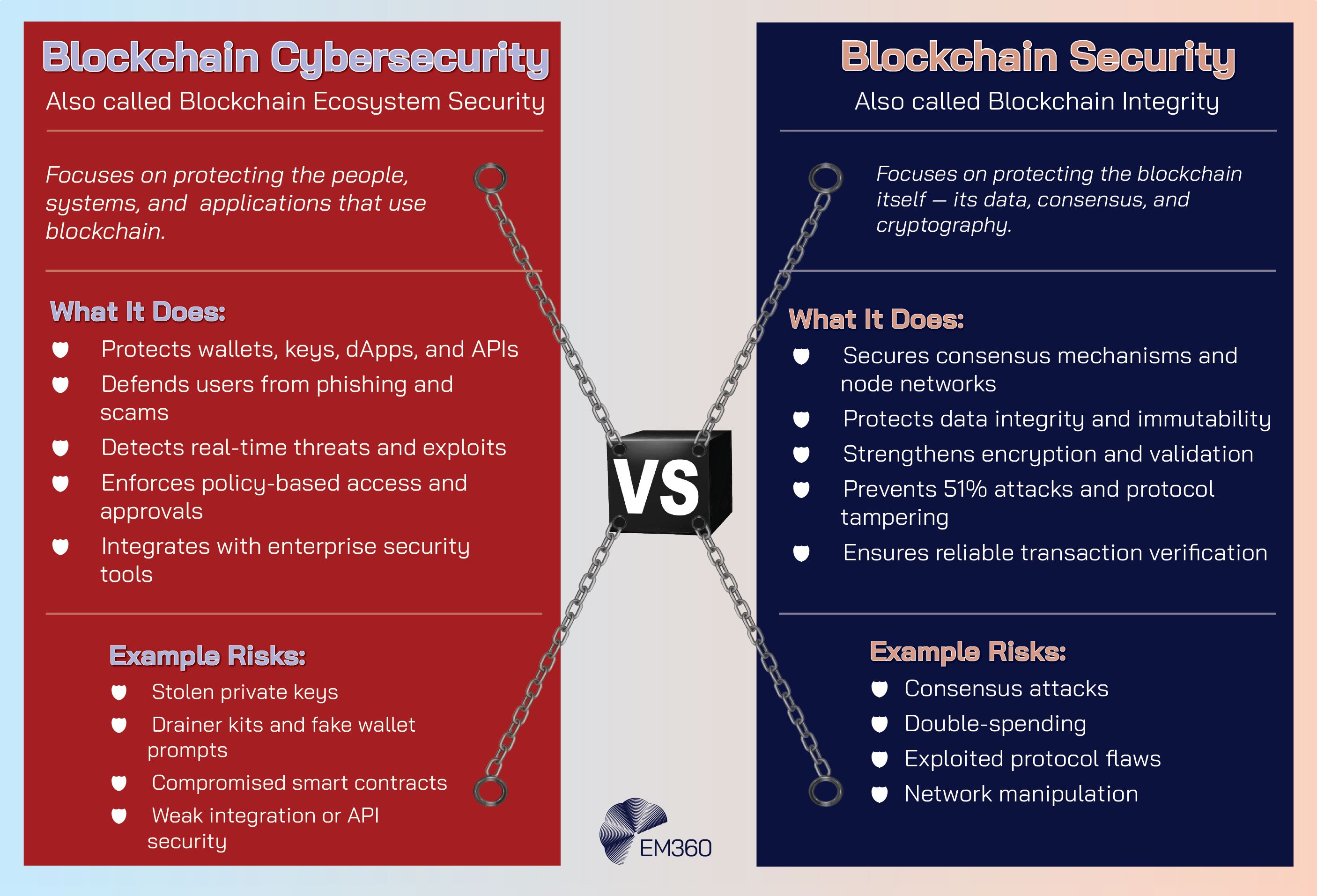
You will hear people use “blockchain security” and “blockchain cybersecurity” as if they're the same thing. They're not. Think of a motorway. One concern is whether the road itself is sound. The other is whether the cars are safe to drive, the signs are clear, and the people using the road know what they're doing.
Blockchain security is the health of the road. It's about the ledger’s core machinery: how new entries are agreed by the network, how records are locked so they cannot be altered, and how the system resists tampering. If the protocol is well designed and correctly run, the road stays intact.
Blockchain cybersecurity is everything that happens on and around that road.
In other words, it's the protection of people, applications, and business processes that rely on the chain. That includes how keys are stored and approved, how wallets are configured, how smart contracts behave once deployed, how decentralised applications connect to traditional web services, and how teams prove they're following policy.
The risks tell the story. A smart contract can contain a logic mistake that only appears when a rare set of actions align. A pop-up can trick a user into signing a transaction that grants an attacker control. A poorly guarded API can let someone bypass a check that was assumed to be enforced elsewhere.
A single leaked recovery phrase can undo otherwise careful controls. These aren't problems with the road. They're the everyday failures that happen when people, software, and process meet real-world pressure.
Attackers have learned to exploit those same weak spots — the people, the integrations, and the gaps between systems — because it’s far easier than breaking the cryptography itself. The lesson is clear: security has to extend beyond the protocol to protect users and every point where blockchain meets the real world.
Why it matters to enterprises

Inside Modern Phishing Tactics
How social engineering exploits trusted channels to trigger breaches, and what controls leaders need to harden users as the new security perimeter.
Enterprises now use blockchain for far more than digital coins or speculative assets. Payment networks, loyalty programmes, trade documents, provenance tracking, and digital credentials all depend on it. That brings familiar expectations for governance and audit, but with a few sharp twists. In decentralised models, accountability shifts.
Where a central intermediary once carried the risk, each team now holds the keys, sets the policy, and approves the transactions. Board oversight must therefore extend to key management, transaction controls, incident reporting, and the evidence that those controls are working.
For practical risk reduction, leaders need security tools that fit into their existing operations.
They need real-time on-chain monitoring that connects with SIEM and SOAR pipelines, custody and wallet platforms that enforce policy before a signature is made, analytics that surface fraud and anomalies early, and runtime protection capable of blocking a malicious transaction before it completes.
The Leading Blockchain Cybersecurity Platforms Protecting Systems, Apps, and Users
Security teams need tools that reduce risk where it actually appears: at the point of signature, inside the runtime of smart contracts, and in the analytics that turn on-chain data into a timely decision.
The platforms below are selected for their fit with enterprise controls, the maturity of their features, and a proven focus on protecting people and applications as much as infrastructure.
BitGo
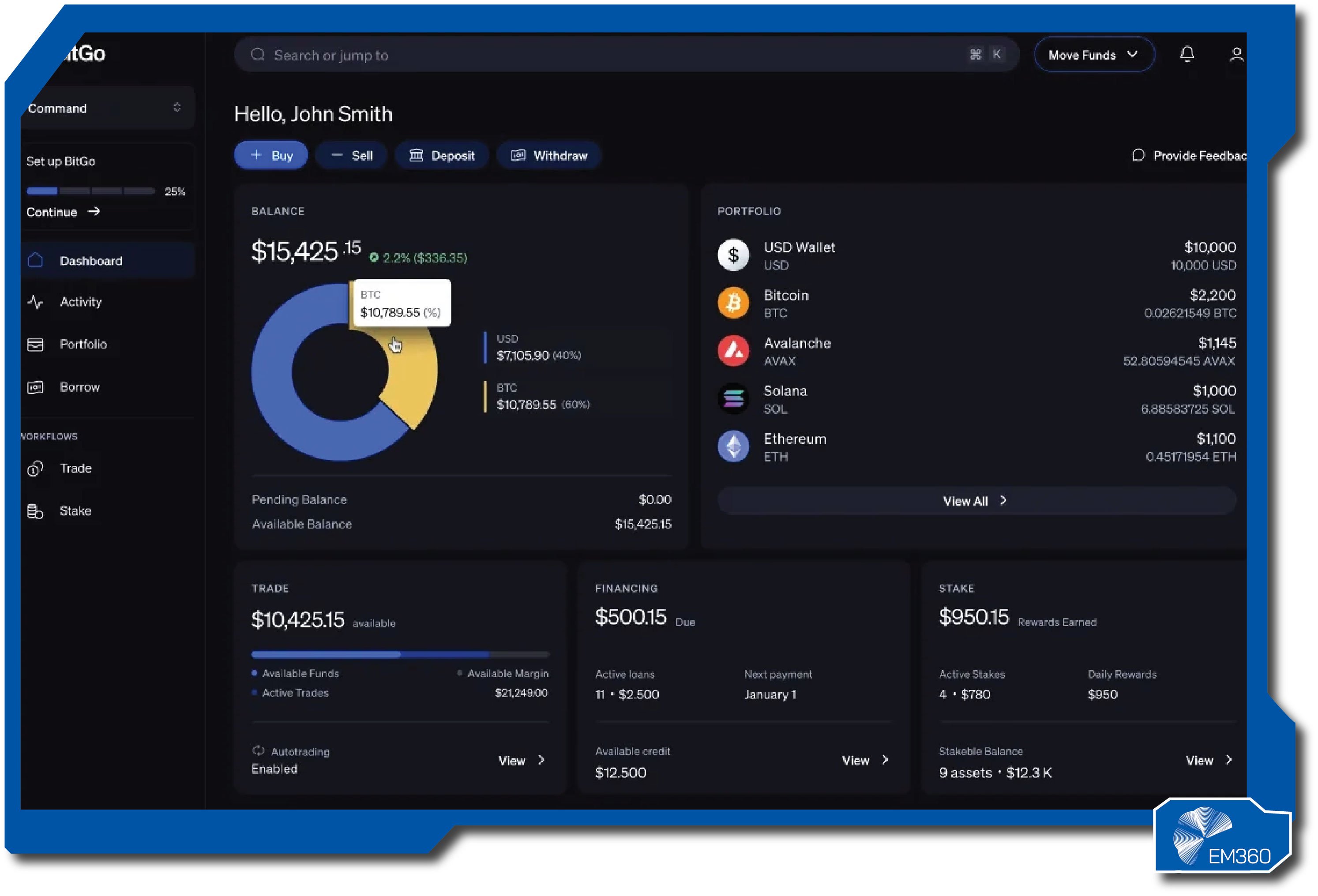
BitGo is one of the earliest names in institutional digital asset security. It began by solving custody for exchanges and funds, then broadened into policy controls, insurance wrappers, and integrations that suit regulated firms. Its reputation rests on careful key handling and operational hygiene rather than marketing promises.
BitGo’s platform centres on secure wallet infrastructure with strong approval workflows. Keys can be split using multi-party techniques so no single person holds full control, and policy rules can gate who signs, how much, and for what purpose. Reporting, segregation of assets, and tamper-evident logs help teams meet audit needs without slowing operations.
Pros
Inside Breach Recovery Costs
Breaks down how outages, remediation, compliance work, and security uplift turn a single breach into a multi-year infrastructure expense.

- Mature custody workflows that fit how larger teams actually operate.
- Strong policy controls before any transaction is signed.
- Widely supported by exchanges, brokers, and service partners.
- Clear separation of duties to reduce insider risk.
- Evidence and reporting features that support audit and assurance.
Cons
- Feature velocity can feel slower than newer entrants.
- Pricing and contracts can be less flexible for smaller teams.
- Some advanced automations may require custom work.
Best for
Enterprises that prioritise proven custody, strong policy enforcement, and clear audit trails across multiple business units.
BlockSec
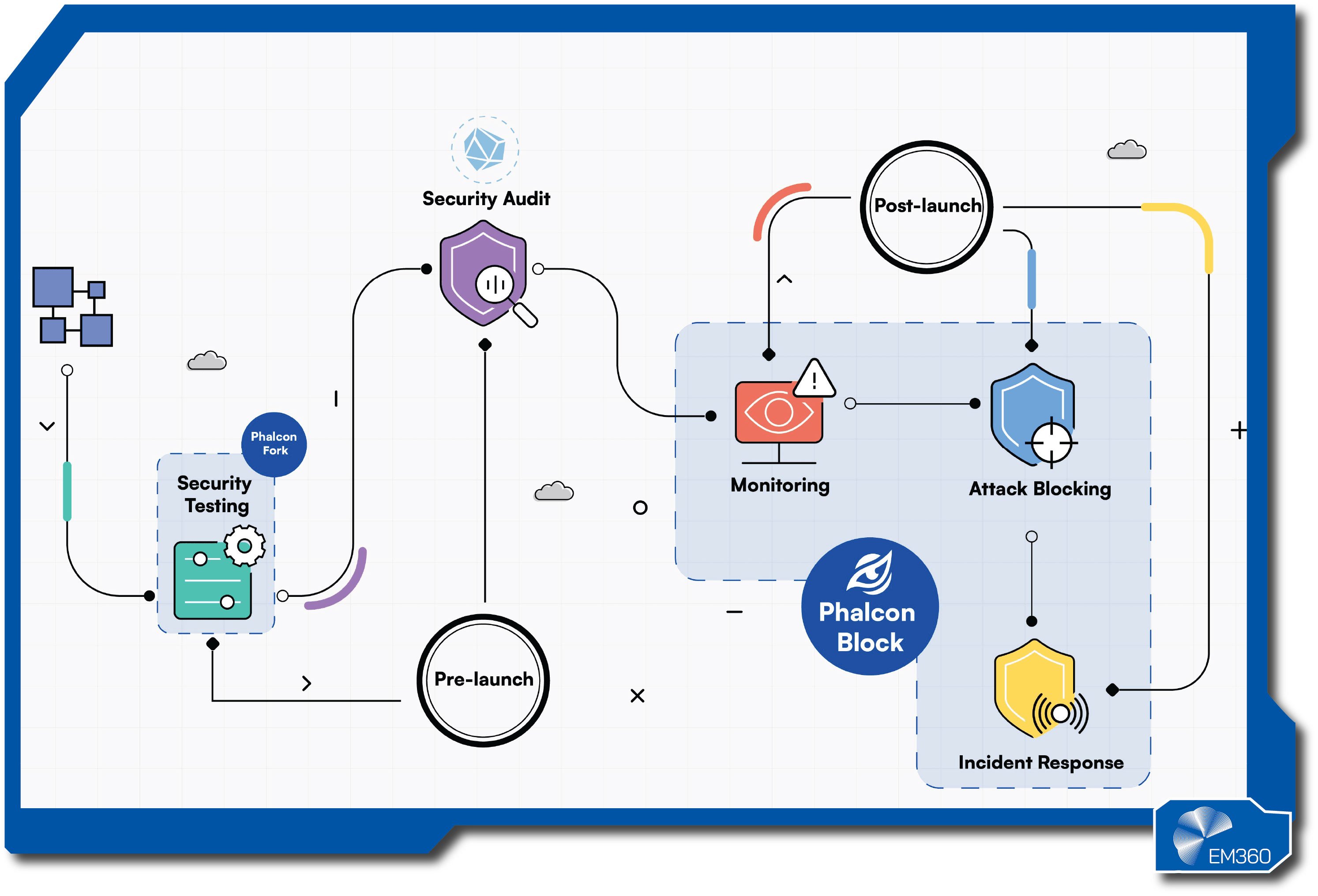
BlockSec was founded by security researchers focused on how attacks unfold in real time. The team built Phalcon to watch transactions as they're proposed, spot malicious patterns, and intervene before they settle. The company is widely known in developer circles for detailed post-mortems and for tooling that supports both prevention and learning.
Phalcon monitors contracts and transactions continuously. It analyses intent, context, and call paths to catch exploits such as re-entrancy, price manipulation, or permission misuse. When a threat is detected, it can block or pause risky flows, alert responders, and provide the context engineers need to fix the root cause. Integrations help feed signals into existing alerting and ticketing.
Pros
- Strong at catching live exploit behaviour before finality.
- Useful forensic context to speed up triage and fixes.
- Good fit for teams running active dApps and protocols.
- Developer-friendly approach with clear technical insight.
- Integrates with common engineering and incident tools.
Cons
- Works best when engineering teams wire it deeply into their pipelines.
- Coverage and models need tuning for niche protocols.
- Costs can scale with breadth of monitoring.
Best for
Product and security teams that run smart contracts in production and need runtime protection aligned to how attacks actually happen.
CertiK
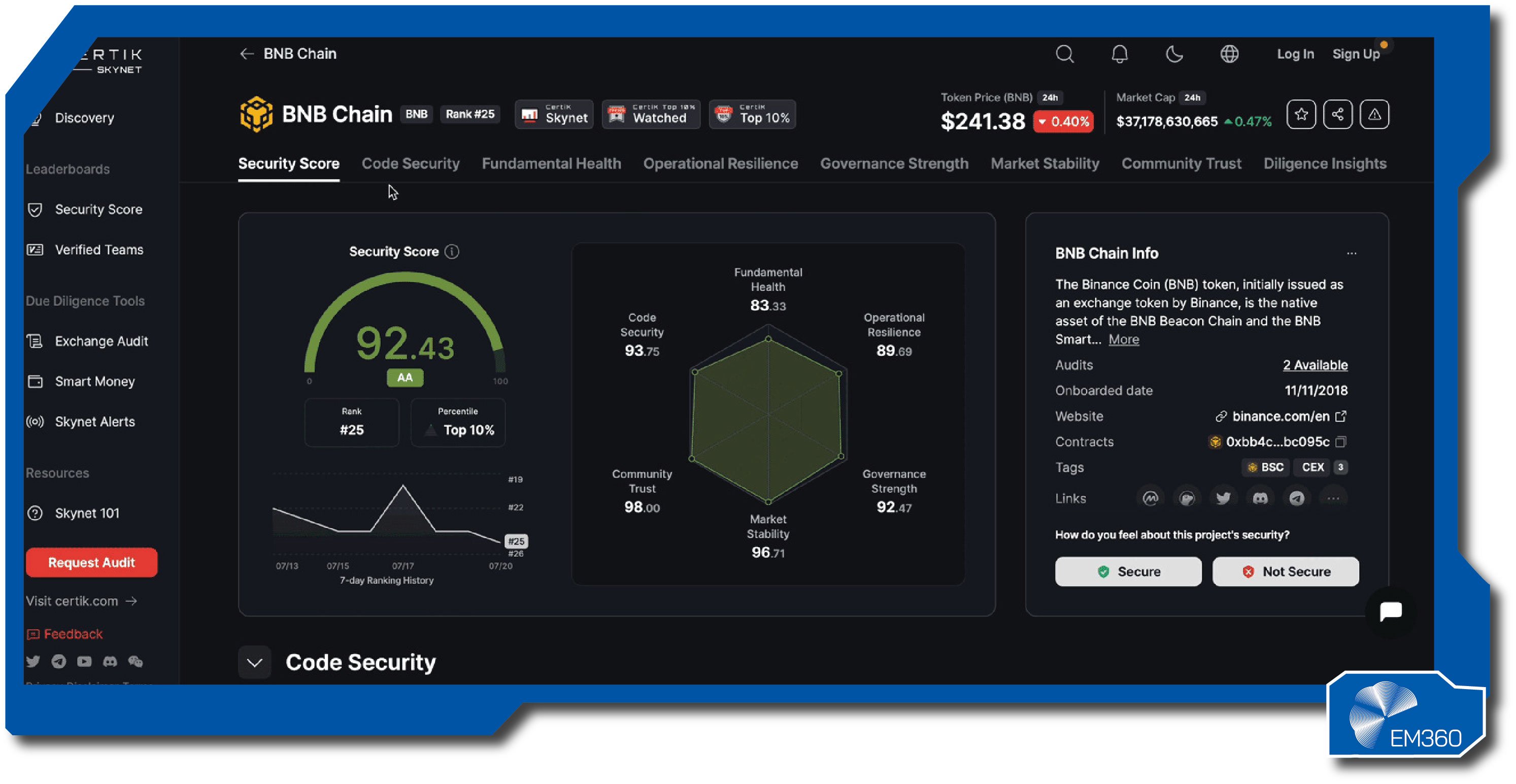
CertiK built its name on smart contract audits, then expanded into continuous monitoring and project risk analytics. The firm publishes frequent incident summaries and maintains a large view of on-chain threats, which informs its ratings and alerts.

DNS Security, Privacy, Control
Examines DNSSEC, filtering and logging policies so leaders can balance threat protection with user trust and compliance.
Skynet, CertiK’s monitoring layer, tracks deployed contracts and associated assets, looking for abnormal behaviour and known risk patterns. Dashboards surface security posture across projects, while alerts help teams respond quickly to suspicious activity. Audit services and best-practice libraries can support development before launch.
Pros
- Broad market visibility through ongoing incident tracking.
- Continuous monitoring that complements pre-launch audits.
- Clear dashboards that communicate risk to non-engineers.
- Large library of common weaknesses and patterns.
- Option to bundle audits with monitoring for end-to-end coverage.
Cons
- Dashboard breadth can be overwhelming without clear ownership.
- Depth of findings varies with project complexity.
- Response playbooks may need in-house refinement.
Best for
Organisations that want a combined audit and monitoring partner to raise baseline quality and maintain visibility after deployment.
Chainalysis
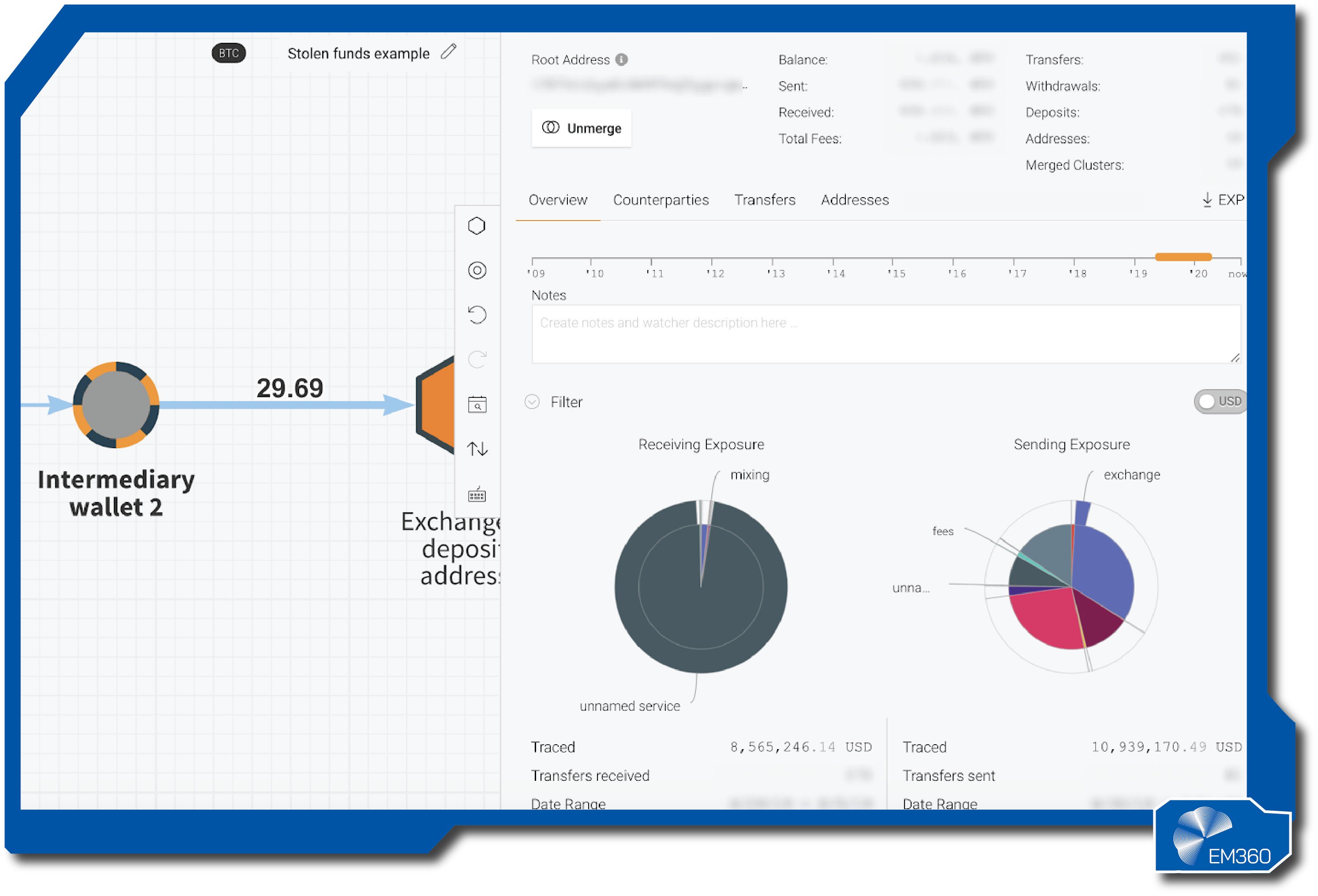
Chainalysis is a pioneer in blockchain analytics. Law enforcement, exchanges, and financial institutions use its tools to trace flows, identify counterparties, and assess risk. The platform’s strength is the breadth of labelled entities across multiple chains and the ability to turn that data into practical screening and investigation outcomes.
The product suite provides real-time risk scoring for addresses and transactions, screening against known scams and sanctioned entities, and deep investigation workspaces. These capabilities help compliance teams reduce fraud exposure, block illicit flows, and document the reasoning behind decisions for regulators and auditors.
Pros
- Extensive entity attribution that improves screening accuracy.
- Investigation tooling that shortens complex tracing work.
- Widely recognised by regulators and investigators.
- Multi-chain coverage suited to modern asset mixes.
- Strong training and enablement materials for compliance teams.
Cons
- Licensing can be expensive for broad team access.
- Data coverage for emerging chains may lag initially.
- Best results depend on clear internal processes.
Best for
Compliance, fraud, and security teams that need reliable screening and investigation capabilities to manage enterprise and regulatory risk.
Copper
When Open Source Runs Defense
Assess how open-source firewalls reshape security strategy by trading license spend for transparency, control and in-house expertise.

Copper focuses on secure settlement infrastructure for institutional trading. Its custody uses multi-party techniques to protect keys, and its ClearLoop model lets institutions settle with exchanges without holding assets on those venues. The aim is to cut counterparty risk while keeping operations smooth for trading and treasury teams.
The platform provides policy-based approvals, network segregation, and detailed logging. Off-exchange settlement reduces hot-wallet exposure on external platforms, while controls help ensure that only approved transactions move through. Reporting supports oversight across desks and entities.
Pros
- Off-exchange settlement that reduces venue risk.
- Policy controls that prevent unwanted movements before they occur.
- Clear operational workflows for trading and treasury.
- Strong focus on segregation and evidence for audit.
- Partner network that supports institutional use cases.
Cons
- Works best for firms that interact with supported venues.
- Advanced configurations may require onboarding effort.
- Pricing tiers can limit experimentation for smaller teams.
Best for
Institutions that trade or manage larger balances and want custody with policy safeguards plus settlement that lowers counterparty exposure.
Elliptic
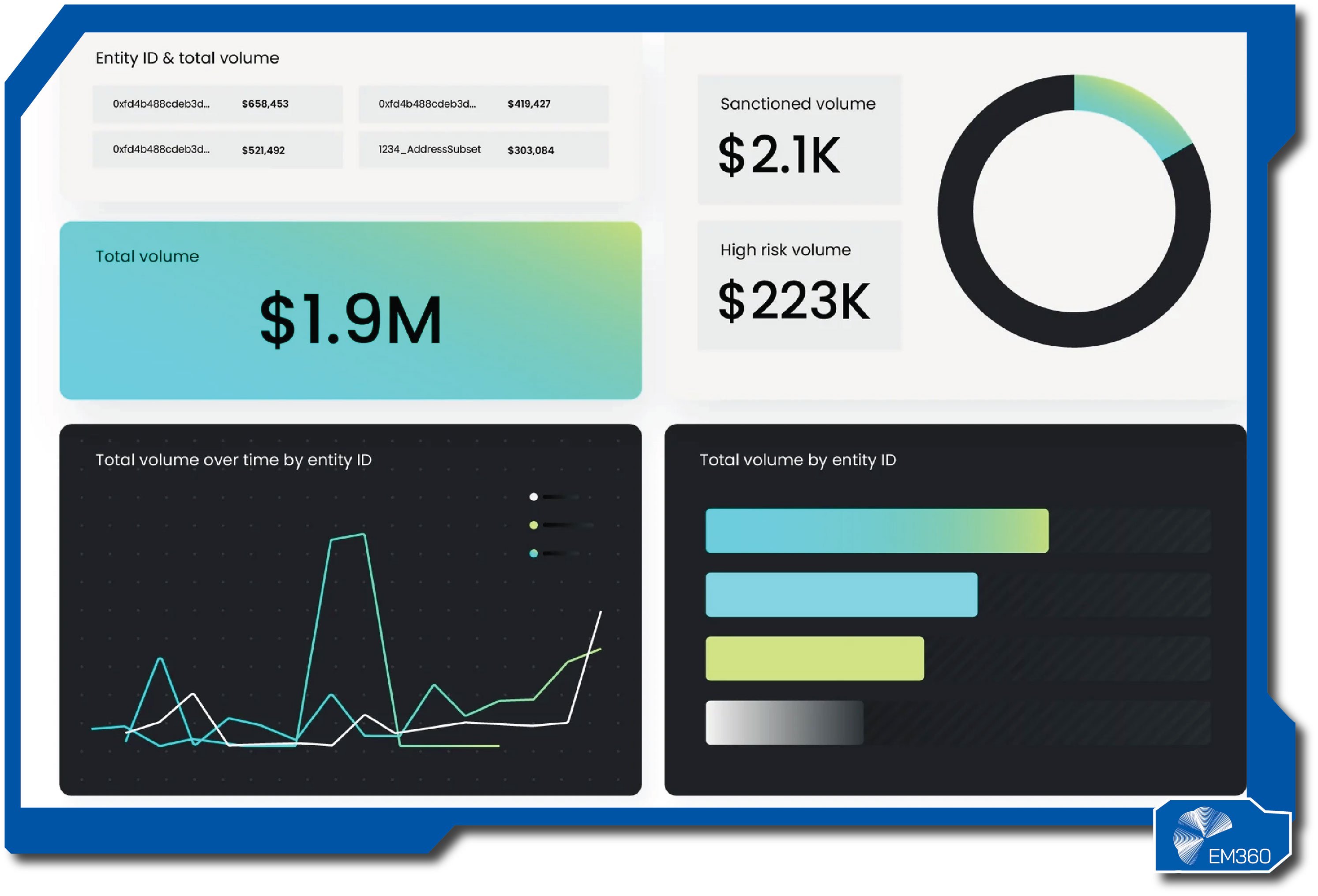
Elliptic is a long-standing provider of blockchain analytics. It grew alongside the first wave of digital asset businesses, building tools that help teams see who they're dealing with on chain and whether a transaction carries hidden risk. Its customers include financial institutions, exchanges, and investigators who need clear answers they can stand behind.
The platform maps wallets and entities across major chains, then uses that data to score risk, flag exposure to scams or sanctions, and trace the flow of funds during an investigation.
Screening can be applied before funds move, while investigation workspaces let analysts follow complex paths across assets and bridges. Reporting features help teams document decisions for audit and regulators without slowing operations.
Pros
- Broad entity coverage that improves the quality of risk screening.
- Clear visual tracing that shortens complex investigations.
- Widely recognised by compliance teams and investigators.
- Multi-chain support that matches real asset mixes.
- Reporting that helps evidence why a decision was made.
Cons
- Licensing can be costly for wider team access.
- Coverage for very new chains may take time to mature.
- Best results rely on strong internal processes and playbooks.
Best for
Compliance, fraud, and investigations teams that need reliable screening and tracing to reduce exposure and prove controls work.
Fireblocks
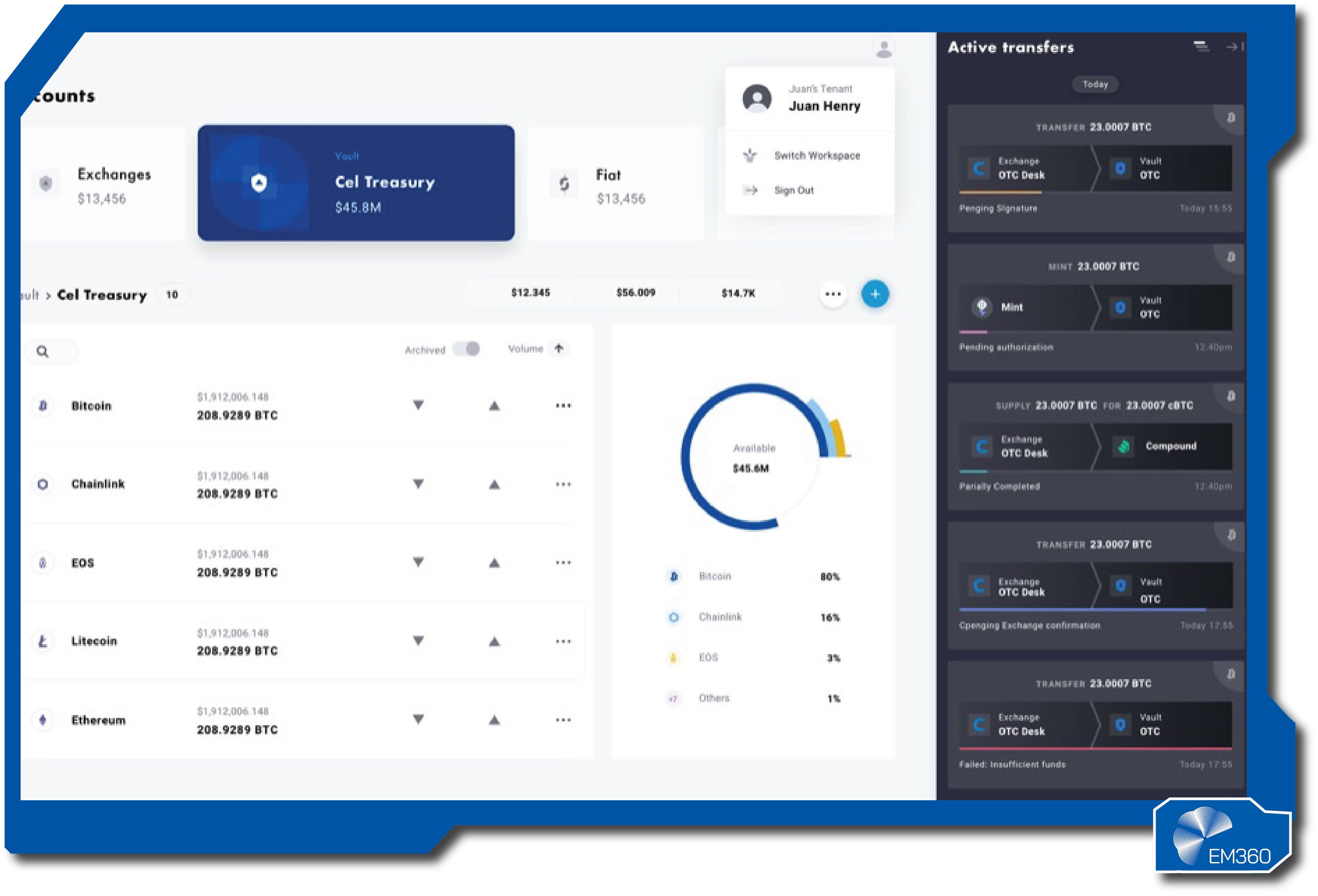
Fireblocks is known for secure wallet infrastructure built for institutions. It started by making key storage safer, then expanded into policy workflows that control who can sign, how much can move, and under what conditions.
The aim is simple: stop risky transactions before they're signed, and keep operations smooth for teams that move value every day. The platform uses multi-party computation to split signing authority so no single person holds a full key. A policy engine lets organisations enforce approvals, limits, and whitelists.
Connections to exchanges and services are segmented, and every action is logged for later proof. APIs support automation, while controls keep automation within guardrails that leadership can trust.
Pros
- Policy controls that prevent unwanted transactions at source.
- Key handling that reduces single points of failure.
- Strong ecosystem of integrations for real-world operations.
- Detailed logging that supports audit and assurance.
- API support that enables secure automation.
Cons
- Pricing and tiers can be a hurdle for smaller teams.
- Advanced configurations may need careful onboarding.
- Feature depth is strongest for commonly used chains and venues.
Best for
Enterprises that move assets at scale and need custody with policy enforcement, segregation, and clear evidence of control.
Forta
Forta emerged to answer a pressing need: detect threats on chain as they happen. It operates as a decentralised network of detectors that analyse transactions and contract activity in near real time. The idea is to raise the alarm early, so teams can act before an exploit's final.
Security and operations teams can subscribe to detectors for known attack patterns, deploy custom detectors for their own contracts, and route findings into existing alerting tools. Forta’s newer offerings extend this into firewall-style protections and compliance signals for supported chains.
The focus is live visibility, actionable alerts, and the ability to evolve as attackers change tactics.
Pros
- Real-time alerts that surface threats before losses mount.
- Flexible detector model for both common and custom risks.
- Easy to connect with existing monitoring and incident tooling.
- Community-driven approach that adapts quickly to new patterns.
- Options that move beyond alerting into protective controls.
Cons
- Signal quality depends on tuning and detector choice.
- Best value comes when teams dedicate owners to triage.
- Coverage varies by chain and project maturity.
Best for
Teams running active contracts or platforms that need live detection, quick triage, and a path to automated protection.
Tenderly
Tenderly is a developer-focused platform that helps teams understand and control what their smart contracts are doing in production. It became popular for accurate transaction simulation and debugging, then added monitoring and alerting so engineers can catch problems before users feel them.
With Tenderly, teams can simulate a transaction to see exactly what will happen, which helps prevent harmful signatures and failed user experiences. Observability features track contract health, event flows, and unusual behaviour across environments. Alerts feed into chat and ticketing, while integrations let engineering and security work from a shared view of what went wrong and why.
Pros
- High-fidelity simulation that prevents costly mistakes.
- Clear observability that shortens time to understand incidents.
- Helpful alerts for both engineers and security staff.
- Smooth developer experience that encourages adoption.
- Works well alongside runtime protection and monitoring tools.
Cons
- Strongest on EVM-compatible chains; others may be limited.
- Requires disciplined use in CI/CD to realise full value.
- Some teams will still need separate tools for formal audits.
Best for
Product and platform teams that want to prevent bad signings, spot abnormal contract behaviour early, and reduce user-impacting errors.
TRM Labs
TRM Labs provides blockchain intelligence for risk management, compliance, and investigations. It's used by banks, payment firms, exchanges, and public sector teams that need a trusted view of illicit activity and exposure across fast-moving assets and networks.
The platform offers risk scoring for addresses and transactions, screening against scam and sanctions data, and a full investigation environment for tracing across chains and assets. Visual graphs make complex flows easier to explain, while reporting features help teams show why they blocked, allowed, or escalated a case.
Coverage includes major chains and stablecoins, reflecting how modern flows actually move.
Pros
- Strong cross-asset tracing that mirrors real transaction paths.
- Useful screening that reduces false comfort and false alarms.
- Investigation workspaces that speed up complex cases.
- Clear outputs that support regulatory and audit needs.
- Frequent dataset updates aligned to current threats.
Cons
- Enterprise licensing can be significant for large user bases.
- New or niche chains may have lighter attribution at first.
- Effective use depends on defined roles and case workflows.
Best for
Risk, compliance, and investigations teams that need accurate screening and deep tracing to manage fraud, sanctions exposure, and incident response.
Key Trends Shaping Blockchain Cybersecurity in 2025
The threat picture is changing quickly, and the best tools are changing with it.
AI-driven scams and drainer kits
Well-crafted phishing pages and “drainer-as-a-service” kits are lowering the barrier to theft. Attackers copy trusted wallet flows and push users toward a single careless click. This is why user-focused controls, warning signals at the point of signing, and transaction simulation now matter as much as code quality.
Real-time on-chain detection and automated blocking
Visibility after an incident is not enough. Security teams are building detection that watches transactions as they form, flags malicious intent, and blocks or pauses risky flows before finality. The winning pattern links on-chain signals to the tools teams already use for alerting and response.
MPC as the default for key management
Multi-party computation splits signing authority across separate parties or devices so no one holds a full key. This reduces single points of failure and brings policy into the moment of approval, rather than after the fact.
Off-exchange settlement to cut venue risk
Trading and treasury teams are moving assets without leaving large balances on external venues. Off-exchange settlement lets firms keep custody while still gaining speed and liquidity, which limits exposure if a venue is compromised.
Post-quantum planning moves from theory to timelines
Quantum-resistant algorithms and migration plans are entering procurement checklists. Long-lived keys, HSM choices, and custody platforms are being assessed for how they will handle upgrades without breaking operations.
Taken together, these shifts point to a combined strategy. Enterprises need fraud analytics that catch social engineering early, runtime monitoring that can act before money moves, and custody platforms that enforce policy at the moment of signature. Strength comes from using these layers together, not as isolated projects.
How Enterprises Can Strengthen Blockchain Defences
Security leaders already have foundations they can build on. The aim is to connect blockchain-specific risks to existing controls and evidence.
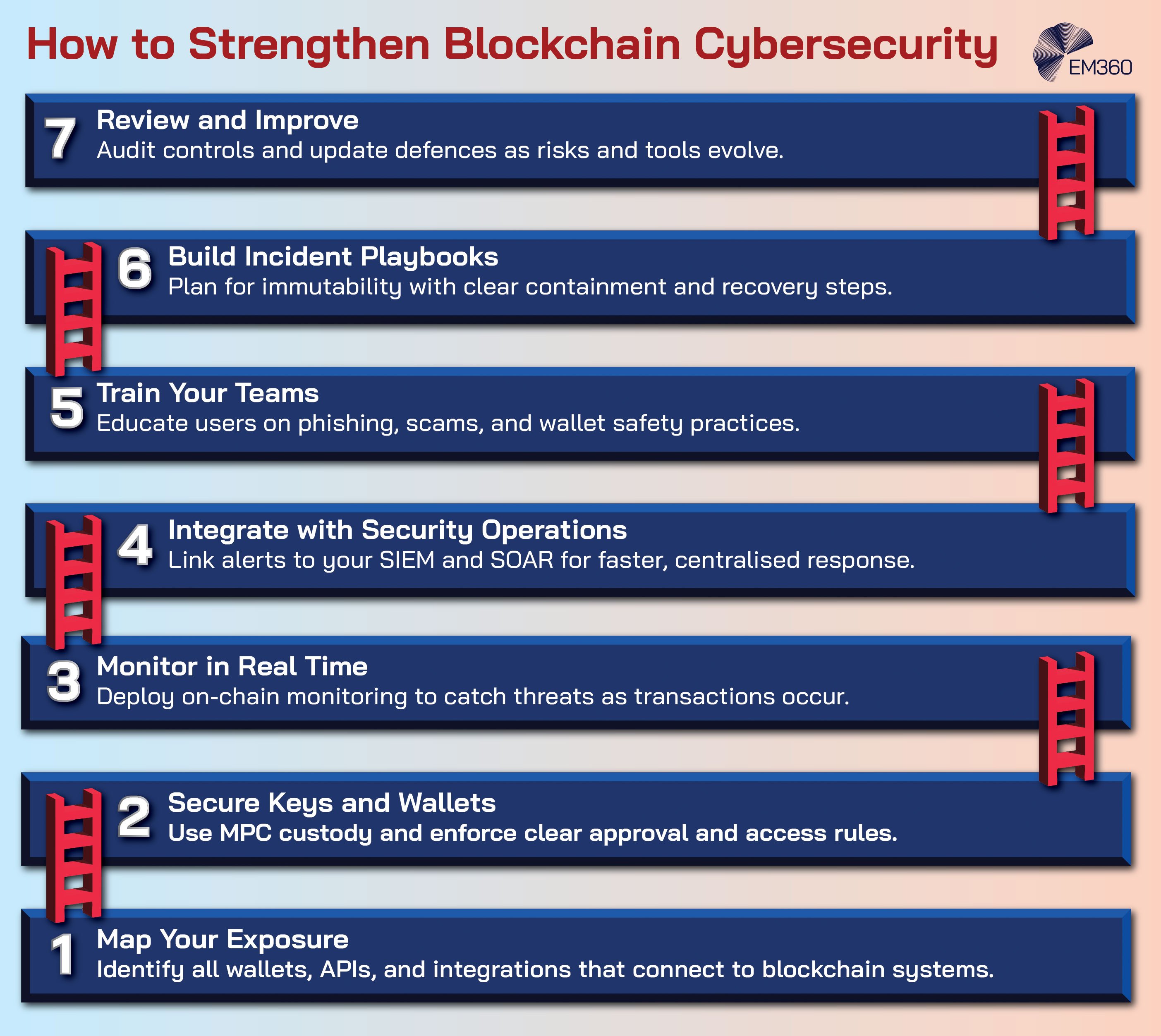
- Integrate on-chain monitoring with your SIEM and SOAR: Send high-signal alerts into the systems that already handle triage, enrichment, and response. SIEM is your central log and alert platform. SOAR is the playbook engine that automates the steps your analysts take. Together they turn on-chain signals into action.
- Set clear key and wallet policies with MPC custody: Define who can propose, approve, and sign. Use spend limits, whitelists, and separation of duties. MPC ensures no single person can move funds alone, while policy rules prevent risky transactions from starting.
- Use threat-intelligence-integrated screening to reduce fraud: Screen addresses and transactions against high-quality datasets for scams, sanctions, and mule activity. Apply screening before funds move and record the reasoning for audit and regulators.
- Write incident paths that reflect immutability: Once a transaction is confirmed, it cannot be reversed. Design playbooks that act earlier in the flow: pause, block, or quarantine before finality. Include recovery steps for leaked keys, malicious approvals, and compromised dApp components.
These actions connect new risks to the same operational muscle that already runs your security programme. They also generate evidence that controls exist, are followed, and can be improved over time.
Final Thoughts: Trust in Blockchain Depends on Securing Its Users
The value of blockchain does not come from cryptography alone. It comes from people being able to move value and prove truth without fear that a trick, a bug, or a rushed click will undo the promise. The constant across this landscape is simple.
Real trust grows when enterprises combine real-time visibility, strong policy at the moment of signing, and clear governance that stands up to scrutiny. Leaders who make that combination work will set the pace. They will cut fraud, shorten incidents, and show the evidence that boards and regulators expect.
If you are building that roadmap now, stay close to the tools and patterns that surfaced here, and keep learning with EM360Tech’s expert coverage of security, resilience, and the controls that make digital trust real.







Comments ( 0 )