Kubernetes is fast becoming the industry standard for container lifecycle management, powering modern applications across enterprises worldwide. Its flexibility, scalability, and automation make it essential for driving digital transformation and building cloud-native applications. However, this innovation also brings new layers of complexity and risk. Kubernetes environments are highly fluid, with workloads frequently starting and stopping across APIs, service meshes, and distributed clusters. This creates both opportunity and risk for the executives responsible for safeguarding business systems.
What is Kubernetes?
Kubernetes, often called K8s, an abbreviation that comes from counting the eight letters between the 'K' and the 's', is an open-source system for automating the deployment, scaling, and management of containerised applications. The name itself originates from the Greek word for "helmsman" or "pilot," reflecting its role in guiding and managing complex workloads. It groups containers into logical units for easier management and discovery, building on more than 15 years of Google’s experience running production workloads, alongside best practices from the open-source community. By design, Kubernetes makes distributed systems more resilient, handling scaling and failover, managing deployments, balancing network traffic, and even self-healing by restarting or replacing failing containers. From service discovery and storage orchestration to automated rollouts, secret management, and horizontal scaling, Kubernetes has become the backbone of modern enterprise IT.
For Chief Information Security Officers (CISOs), however, this strength is a double-edged sword. The same agility that makes Kubernetes so valuable also expands the attack surface. Misconfigurations, exposed dashboards, and supply chain compromises can quickly lead to unauthorised access, privilege escalation, data breaches, or operational disruption. Securing Kubernetes is no longer an optional afterthought; it is critical to protecting both applications and the business itself.
EM360Tech wants to provide CISOs with actionable guidance for reducing Kubernetes-related risks. Security must be embedded across every layer, spanning infrastructure, the control plane, workloads, and developer pipelines without undermining the agility that makes Kubernetes indispensable. For security leaders, the challenge is to strike the right balance between resilience and risk.
Why Kubernetes Security Matters
Kubernetes has become the backbone of modern cloud-native infrastructures. It powers scaling, automated recovery systems, and seamless rollouts across hybrid and multi-cloud environments. With this power comes a price: security becomes exponentially more complex. Neglecting Kubernetes security can lead to catastrophic breaches, data loss, or compliance violations. In 2025, attackers are faster, more sophisticated, and increasingly targeting misconfigured clusters, supply chain weaknesses, and exposed APIs. Securing Kubernetes is therefore essential for any enterprise.
Let's have a look at why it matters:
Expanded Attack Surface in Kubernetes Security
By design, Kubernetes distributes workloads across pods, nodes, and clusters, which inherently expands the attack surface. Every API, controller, and service can serve as a potential entry point for attackers.
API Server Vulnerabilities
The Kubernetes API server is the heart of cluster control, managing workloads, configurations, and communications across the cluster. Its critical role makes it a prime target for attackers. Recent vulnerabilities, such as CVE-2025-5187, have allowed unauthorised users to manipulate cluster resources by exploiting weak Role-Based Access Control (RBAC) policies, potentially giving attackers the ability to create, modify, or delete pods, secrets, and other critical objects. Meanwhile, improper certificate validation in Kubernetes clients has introduced the risk of man-in-the-middle attacks, where attackers could intercept or alter API server communications. These vulnerabilities highlight that even small misconfigurations in the API server can have far-reaching implications for cluster integrity, data security, and overall operational stability.
Pod and Node Exploits
Compromised containers can facilitate lateral movement within the cluster. Exploits like CVE-2025-1974 in the Ingress NGINX Controller have demonstrated how attackers can gain unauthorised access to secrets across namespaces, leading to cluster-wide compromises. This demonstrates that a single vulnerable container or misconfigured component can have far-reaching consequences in a distributed Kubernetes environment.
Service Mesh Misconfigurations

Inside 2025 Blockchain Defences
Boards are shifting focus from protocol safety to tools that secure keys, wallets, contracts and users across decentralised operations.
Service meshes, such as Istio and Linkerd, play a critical role in managing microservices communication by providing traffic routing, observability, policy enforcement, and encryption. However, the complexity they introduce can create security gaps if not properly configured. Misconfigured TLS settings, overly permissive sidecar permissions, or incorrect policy definitions can all be exploited by attackers, potentially allowing unauthorised access or data interception. While a service mesh enhances security and operational insight, it also introduces resource overhead, additional operational complexity, and new potential points of failure. Organisations must carefully balance the benefits of encryption, observability, and fine-grained control against the increased attack surface and maintenance burden that comes with these systems.
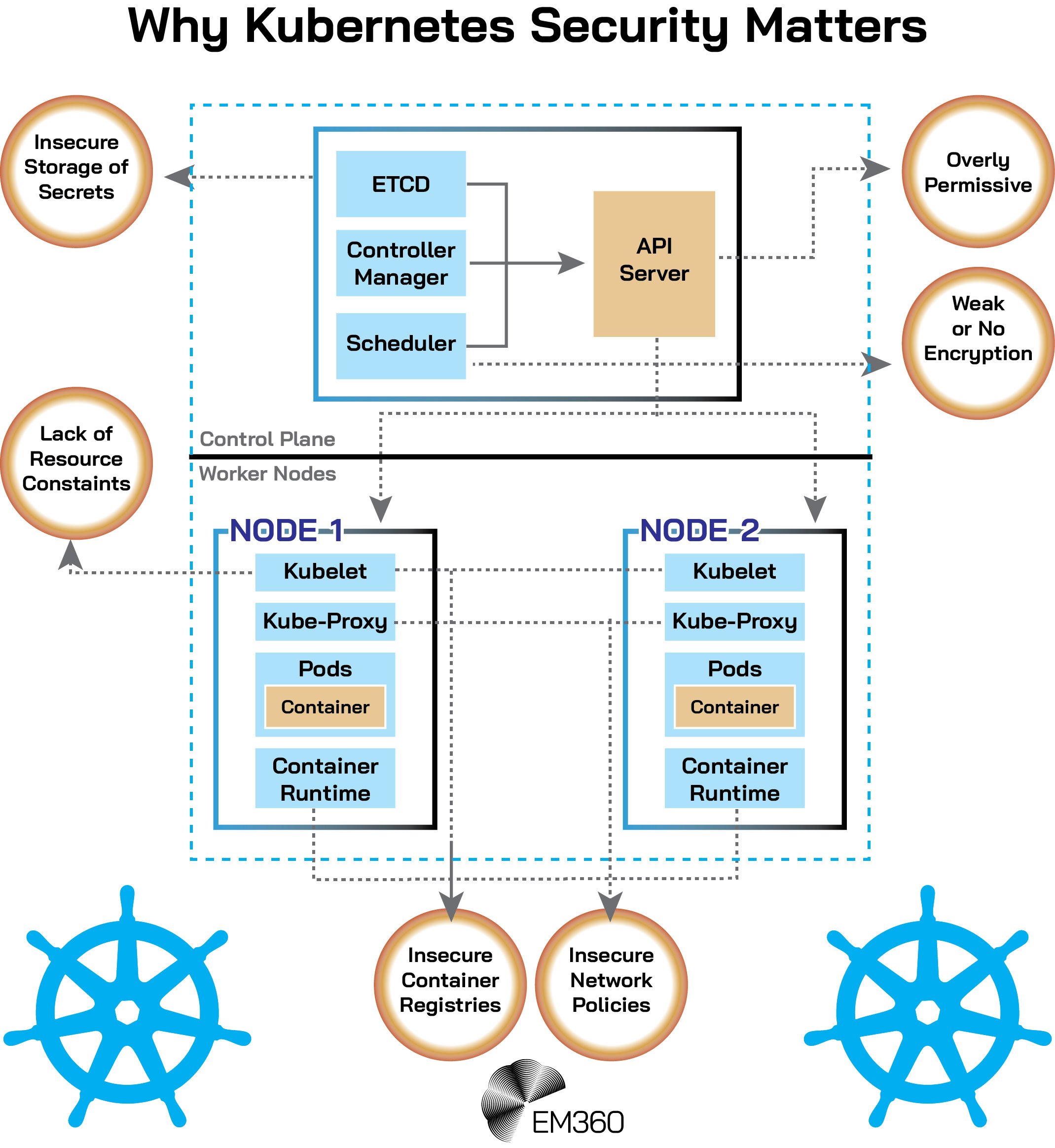
Securing the Kubernetes Ecosystem
Given the modular and distributed system of Kubernetes, securing a cluster requires a multi-layered and systematic approach.
Let's take a look at what is needed:
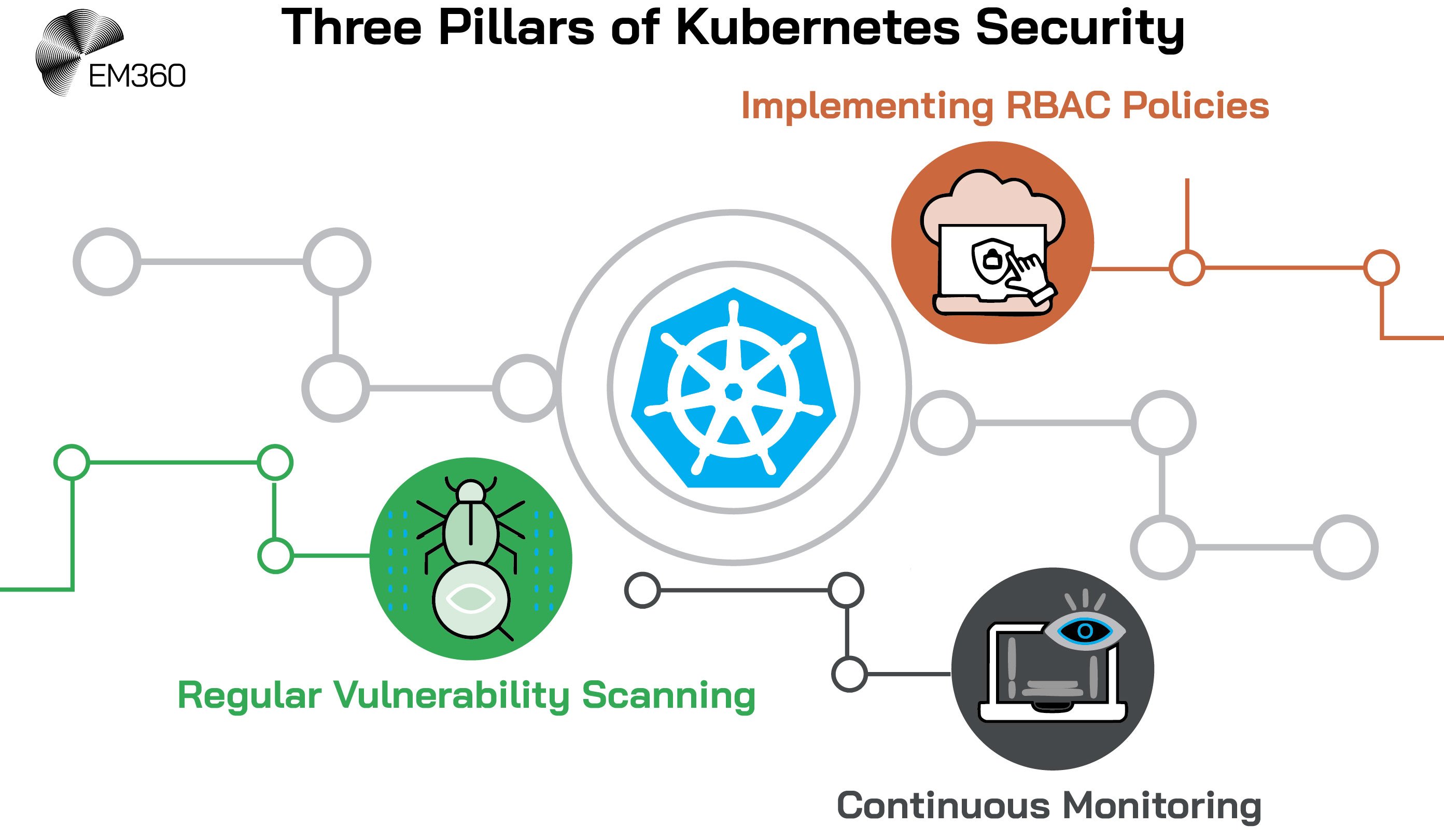
Implementing RBAC Policies
Role-Based Access Control (RBAC) is imperative to limiting what users, service accounts, and workloads can access within a cluster. Applying the principle of least privilege helps reduce the risk of a compromised account or pod being used to escalate privileges or access sensitive resources.
Regular Vulnerability Scanning
Continuous scanning of container images, configurations, and cluster components is critical. Tools such as ARMO and other Kubernetes security scanners can identify misconfigurations, known vulnerabilities, and outdated packages in real time, allowing teams to remediate issues before they are exploited.
Continuous Monitoring
Runtime security tools provide real-time visibility into cluster activity, detecting anomalies, suspicious API calls, or unauthorised changes. These tools establish a baseline of normal behaviour and flag deviations such as unexpected network calls or unauthorised file access as potential security risks. Beyond passive monitoring, runtime security solutions actively enforce policies to prevent malicious actions. They analyse three primary areas: application behaviour, network traffic, and system calls.
- Application Behaviour Analysis: Tracks all actions performed by an application, including file access, data processing, and network connections. Understanding typical patterns allows the tool to identify anomalies and potential vulnerabilities.
- Network Traffic Monitoring: Observes communication between pods, services, and external endpoints. Unusual traffic patterns can indicate data exfiltration attempts, lateral movement, or misconfigured network policies.
- System Call Monitoring: Examines low-level system calls to detect unauthorised access to the host or container environment, such as attempts to escalate privileges or execute unexpected processes.
Inside Breach Recovery Costs
Breaks down how outages, remediation, compliance work, and security uplift turn a single breach into a multi-year infrastructure expense.

Integrating these runtime monitoring capabilities into operational workflows enables teams to respond quickly to threats, minimise the damage from attacks, and maintain the integrity of the cluster. Together with RBAC and vulnerability scanning, continuous monitoring forms the foundation of a great Kubernetes security strategy. These practices ensure that clusters remain resilient and secure, even as workloads scale and environments grow more complex.
Common Threats and Vulnerabilities
As Kubernetes adoption grows across enterprises, attackers have adapted their methods to exploit the unique aspects of containerised and cloud-native environments. Understanding the most prevalent threats and vulnerabilities is essential for CISOs and security teams seeking to protect clusters effectively.
In 2025, organisations face a range of challenges from misconfigurations and exposed dashboards to supply chain risks and vulnerabilities in main components such as controllers and ingress. Even minor lapses in configuration or oversight can provide attackers with a foothold, allowing them to move laterally across the cluster or access sensitive data.
This section explores the key threats and vulnerabilities that organisations need to address to maintain secure and resilient Kubernetes environments.
1. Misconfigurations
The first is that misconfigurations remain a leading cause of security incidents in Kubernetes environments. Default settings, disabled encryption, open ports, and overly permissive RBAC policies create exploitable gaps. A survey by Red Hat found that 40 per cent of organisations detected misconfigurations in their container or Kubernetes environments, highlighting why careful configuration management is essential.
Main Misconfiguration Risks:
- Overly Permissive RBAC Policies: Granting broad permissions can allow attackers to escalate privileges within the cluster. For instance, binding the default service account in the default namespace to the cluster-admin ClusterRole can result in full control of the entire cluster.
- Disabled Encryption: Failing to enable encryption for secrets or etcd data can expose sensitive information to unauthorised access.
- Open Ports: Exposing unnecessary ports, especially the insecure API server port, can provide attackers with entry points into the cluster.
- Insecure Network Policies: Lack of proper network segmentation can allow lateral movement within the cluster, enabling attackers to access other services and data.
Mitigation Strategies:

When SIEM Becomes Core Security
Breaches, ransomware and compliance pressure are pushing SIEM from optional tooling to a mandatory layer in cyber defense.
- Implement Least Privilege Access: Ensure that users and service accounts have only the permissions necessary to perform their tasks.
- Enable Encryption: Configure encryption for secrets and etcd data to protect sensitive information.
- Restrict Open Ports: Only expose necessary ports and use firewalls to limit access.
- Define Network Policies: Use network policies to control the communication between pods and services, reducing the risk of lateral movement.
2. Exposed Dashboards or Control Planes
Unsecured web dashboards or APIs accessible from the internet are high-risk targets. Attackers often scan for exposed clusters immediately after deployment.. Research indicates that new Kubernetes clusters frequently attract attack attempts within minutes of going live. Ensuring that dashboards, APIs, and control planes are properly restricted is therefore essential.
Risks of Exposed Dashboards:
- Unauthorised Access: Exposed dashboards can allow attackers to gain administrative access to the cluster.
- Sensitive Information Disclosure: Dashboards may display sensitive information, such as pod configurations and secrets, which can be exploited by attackers.
Mitigation Strategies:
- Restrict Access: Use authentication mechanisms and firewalls to limit access to dashboards and control planes.
- Use Secure Connections: Ensure that all communications with dashboards and APIs are encrypted using TLS.
- Regular Audits: Periodically review access logs and configurations to detect and remediate any potential exposure.
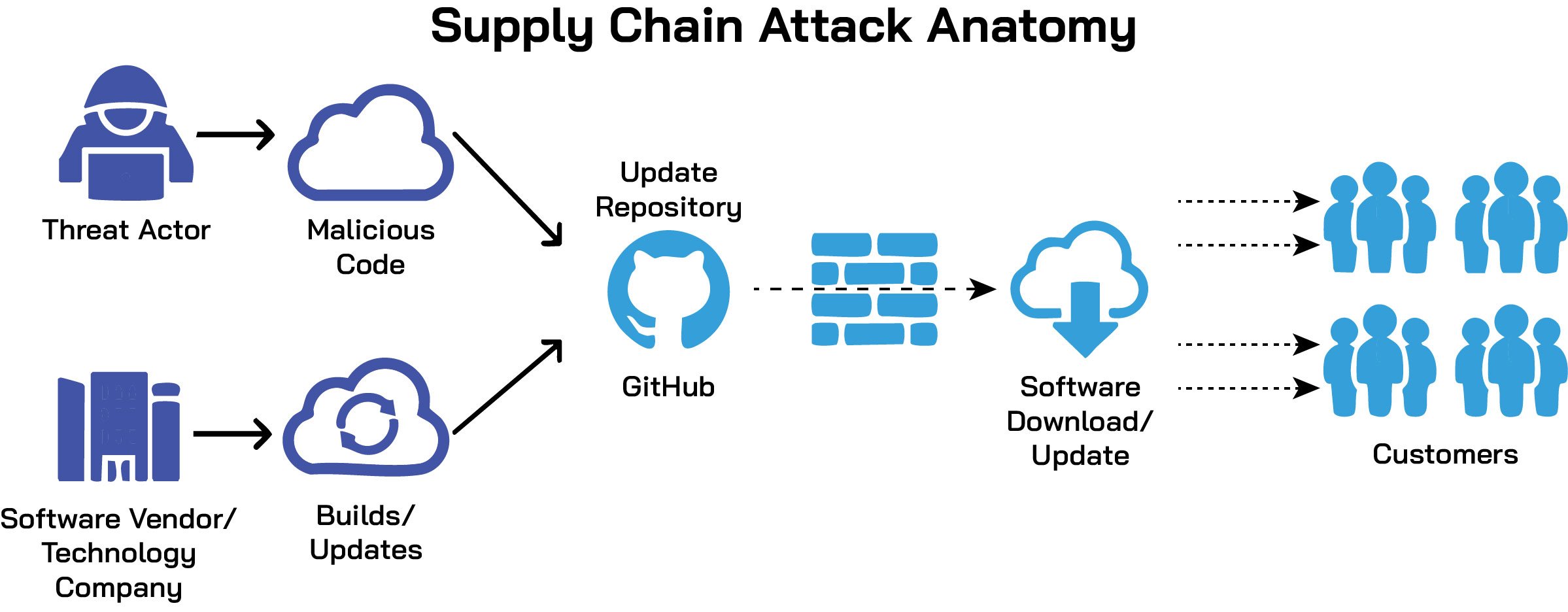
3. Supply Chain Attacks
Threats can also enter the environment before deployment. Malicious or vulnerable third-party container images, compromised Continuous Integration/Continuous Deployment (CI/CD) pipelines, or tampered Helm charts can introduce backdoors or known vulnerabilities (CVEs) into otherwise trusted workloads. Supply chain attacks remain a key vector for introducing threats in production environments.
Common Supply Chain Risks:
- Compromised Container Images: Using unverified or outdated images can introduce vulnerabilities into the cluster.
- Tampered Helm Charts: Modifying Helm charts can alter the deployment configurations, leading to potential security issues.
- Insecure CI/CD Pipelines: Weaknesses in the CI/CD pipeline can be exploited to inject malicious code during the build or deployment process.
Mitigation Strategies:
When DNS Becomes Strategy
How selecting public DNS now affects speed, resilience, privacy and governance in increasingly distributed digital estates.

- Use Trusted Sources: Only use container images and Helm charts from trusted and verified sources.
- Implement Image Scanning: Regularly scan container images for known vulnerabilities and malware.
- Secure CI/CD Pipelines: Implement security measures, such as code signing and access controls, to protect the CI/CD pipeline from tampering.
4. Vulnerabilities in Controllers and Ingress
Critical vulnerabilities in widely used components continue to pose significant risks. In March 2025, researchers identified multiple flaws in the Ingress NGINX Controller (e.g., CVE-2025-1097, CVE-2025-1098, CVE-2025-24514, CVE-2025-1974), allowing remote code execution. Dubbed “Ingress Nightmare” by the security community, these vulnerabilities affected organisations that exposed ingress controllers to the public internet, leaving clusters immediately at risk.
Risks of Vulnerable Controllers and Ingress:
- Remote Code Execution: Exploiting vulnerabilities can allow attackers to execute arbitrary code within the cluster.
- Unauthorised Access: Misconfigurations can allow attackers to bypass access controls and gain unauthorised access to services.
Mitigation Strategies:
- Regular Updates: Keep controllers and ingress components up to date with the latest security patches.
- Secure Configurations: Follow security best practices when configuring controllers and ingress resources.
- Limit Exposure: Avoid exposing controllers and ingress components to the public internet unless absolutely necessary.
5. Drift and Configuration Sprawl
As clusters scale, configurations and policies can drift from their intended state. Without continuous auditing and policy enforcement, inconsistencies accumulate, creating opportunities for privilege escalation or container escape. Managing configuration drift is therefore essential for maintaining a secure and stable Kubernetes environment.
Risks of Configuration Drift:
- Privilege Escalation: Changes in configurations can inadvertently grant elevated privileges to users or services.
- Inconsistent Policies: Divergent configurations can lead to inconsistent security policies, increasing the attack surface.
Mitigation Strategies:
- Continuous Monitoring: Implement tools to continuously monitor and detect configuration drift.
- Automated Remediation: Use automation to correct deviations from the desired configuration state.
- Version Control: Maintain version-controlled configuration files to track changes and facilitate rollbacks.
Shared Responsibility in Kubernetes Security
In cloud-native environments, security is a shared responsibility. Cloud providers manage the security of the underlying infrastructure, including physical hardware, networking, and the hypervisor layer. However, customers are responsible for securing their workloads, configurations, and policies within the cloud environment.
Kubernetes introduces an extra abstraction layer between the infrastructure and workloads, creating new responsibilities for organisations. While Kubernetes provides a powerful platform for orchestrating containerised applications, it also requires a heightened focus on security practices to mitigate potential risks.
Kubernetes Best Practices
1. Control Plane Protection
The control plane is the brain of a Kubernetes cluster, managing the overall state and configuration. Securing the control plane is paramount:
- Use TLS for Encryption: Ensure that all communication within the control plane is encrypted using Transport Layer Security (TLS). This protects data in transit between components like the API server, etcd, and kubelets.
- Encrypt Data at Rest: Enable encryption at rest for sensitive data stored in etcd, such as secrets and configuration data, to prevent unauthorised access.
- Implement Strict Authentication and Authorisation: Use strong authentication methods, such as certificate-based access and token mechanisms, to control who can access the API server. Implement Role-Based Access Control (RBAC) to enforce the principle of least privilege.
- Limit API Server Exposure: Restrict access to the API server by using network policies and isolating management traffic. The control plane should not be exposed to the public internet.
2. Secrets Management
Improper management of secrets, credentials, or configuration data can lead to unauthorised access, data leaks, or compliance breaches. Handling sensitive information securely is also very important:
- Encrypt Secrets at Rest: Use Kubernetes' built-in mechanisms to encrypt secrets stored in etcd.
- Utilise External Secret Management Tools: Integrate with external secret management solutions like HashiCorp Vault or AWS Secrets Manager for better lifecycle management and rotation of secrets.
- Avoid Embedding Secrets in Code: Do not hard-code secrets in application code or configuration files. Use environment variables or mounted volumes to inject secrets securely.
3. Workload Protection
Each pod and container represents a potential entry point for attackers, so organisations must enforce strict security controls at the workload level. Combining these measures ensures that workloads remain resilient against both internal and external threats. Securing the workloads running within the cluster is essential:
- Enforce Pod Security Standards: Implement Pod Security Admission (PSA) to enforce security standards at the pod level across Kubernetes clusters.
- Use Runtime Security Tools: Employ tools like Falco or eBPF-based detectors to monitor and detect anomalous behaviour in containers.
- Implement Network Policies: Define network policies to control traffic between pods and restrict external ingress or egress by default.
- Scan Container Images: Use image scanning tools like Trivy or Clair integrated into CI/CD pipelines to identify vulnerabilities before deployment.
4. Admission Control
Admission controllers are critical for enforcing policies: they act as gatekeepers for the Kubernetes API server, intercepting requests to create or modify resources and ensuring that all actions comply with organisational security and operational policies. Regularly reviewing and updating these controllers is essential, as outdated rules may fail to prevent new threats.
- Use Validating and Mutating Webhooks: Implement webhooks to validate and mutate API requests as they enter the cluster, ensuring compliance with security policies.
- Keep Webhook Logic Updated: Regularly update webhook logic to align with evolving security requirements and Kubernetes updates.
- Ensure Webhook Performance: Design webhooks to be efficient and fail-safe to prevent potential disruptions in the cluster.
5. Auditing and Logging
Continuous monitoring and auditing are vital; they provide visibility into all activity within the cluster, allowing organisations to detect anomalies, misconfigurations, or unauthorised actions before they escalate into security incidents. Regular audits also help verify that security policies are enforced consistently, configuration drift is detected, and lessons from incidents are fed back into operational improvements.
- Enable Audit Logs: Activate Kubernetes audit logs to record every action in the cluster, from API calls to control plane changes.
- Centralise Log Storage: Ship logs to a secure, centralised log store (e.g., SIEM, ELK, Splunk) for correlation and retention.
- Define Alerting Mechanisms: Set up alerts for anomalous activities, such as escalated privileges or unexpected role assignments.
- Regularly Review Audit Trails: Perform regular reviews of audit logs to identify and respond to potential security incidents.
Emerging Trends in 2025
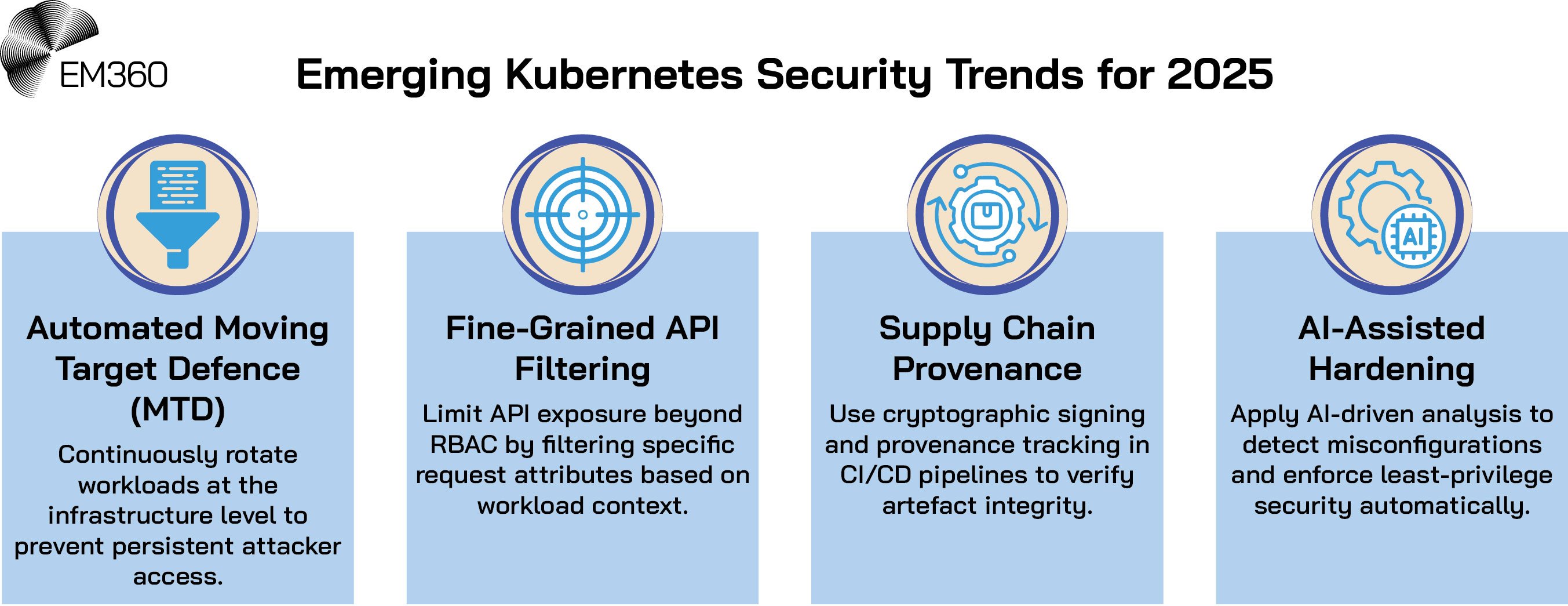
The threat landscape for Kubernetes is continually evolving, and traditional security controls may not be sufficient to address advanced attack vectors. Leveraging new technologies can enhance detection, enforcement, and resilience across clusters. To stay ahead of potential threats, organisations should consider adopting emerging security technologies:
- Automated Moving Target Defence (MTD): Implement systems like ADA that continuously rotate workloads at the infrastructure level within Kubernetes, making it harder for attackers to maintain persistent access.
- Fine-Grained API Filtering: Explore solutions like KubeFence that restrict API surface beyond RBAC, filtering specific request attributes based on workload context.
- Supply Chain Provenance: Adopt models like ARGO-SLSA that integrate cryptographic signing, attestation, and provenance tracking into Argo Workflows, enhancing trust in artefacts generated through Kubernetes-native automation.
- AI-Assisted Hardening: Investigate tools like KubeGuard that use large language models to analyse runtime logs and configuration manifests, recommending least-privilege configurations to continuously harden clusters.
Recommendations for CISOs & Tech Leaders in 2025
As Kubernetes adoption grows, securing clusters requires a proactive, multi-layered approach. The following strategies provide practical guidance for CISOs and tech leaders to reduce risk, maintain compliance, and safeguard workloads across complex cloud-native environments.
To IMPROVE Kubernetes security, consider the following strategies:
- Start from Day Zero: Treat every cluster as if it's under threat. Implement hardened templates, enforce policies before the first pod starts, and restrict API exposure from the outset.
- Adopt a "Policy + Enforcement" Model: Leverage policy engines like Open Policy Agent (OPA), Gatekeeper, or Kyverno to impose guardrails, not just best-effort guidance.
- Shift Security Left: Integrate image scanning, policy checks, vulnerability assessments, and compliance validation into CI/CD pipelines to prevent insecure artefacts from entering runtime.
- Continuous Audit and Drift Detection: Use tools that monitor configuration drift, detect changes outside pipelines, and flag policy violations in real time.
- Leverage Runtime Observability and Anomaly Detection: Employ eBPF-based tracing tools like Cilium's Tetragon or Falco to detect suspicious behaviour, lateral movement, or privilege escalations.
- Implement a Zero Trust Mindset: Apply the principle of least privilege, microsegmentation, and just-enough-access everywhere—between namespaces, services, and external integrations.
- Stay on Top of Patching and Versioning: Ensure clusters run supported Kubernetes versions and promptly apply security patches.
- Monitor Supply Chains and Provenance: Use image signing, provenance attestation, and provenance-aware paths for CI/CD artefacts (e.g., via ARGO-SLSA).
- Invest in Advanced Tooling and Research: Consider emerging techniques such as automated MTD, AI-supported security hardening (e.g., KubeGuard), or fine-grained API filtering (e.g., KubeFence).
- Educate Teams and Establish Governance: Security is not a single team's job. Establish proper governance, cross-team responsibility, and security training for developers and operations alike.
Securing Kubernetes
Kubernetes has changed the way enterprises use and manage applications, allowing systems to grow easily, adapt to changes, and work quickly and smoothly. However, its complexity and distributed architecture also make it a prime target for cyber threats. For CISOs, securing Kubernetes environments is no longer optional; it is a strategic necessity that directly impacts business continuity, compliance, and risk management. Recent 2025 data highlights the urgency of addressing Kubernetes security. Check Point reports that over 58 per cent of organisations experienced Kubernetes-related security incidents in the past year, 62 per cent identified vulnerabilities in deployed container images, and nearly half of workloads continue to run with high privileges.
The stakes are clear with a single misconfigured API, exposed dashboard, or compromised third-party image can cascade into widespread breaches and operational disruption. CISOs must therefore adopt a layered, defence-in-depth approach, combining strict access control, encrypted secrets management, workload isolation, continuous monitoring, and proactive supply chain verification. Integrating these measures with DevSecOps practices ensures that security is embedded from development through deployment and into runtime operations.
Ultimately, Kubernetes security is not just about protecting containers; it is about safeguarding the enterprise itself. By anticipating threats, enforcing policies religiously, and continuously monitoring for anomalies, CISOs can use Kubernetes to transform a potential vulnerability into a resilient, secure foundation that supports business growth and innovation in 2025 and beyond.







Comments ( 0 )