In one of the most major cybersecurity incidents of the year, Microsoft SharePoint servers have become the target of an aggressive global hacking campaign taking advantage of an unpatched zero-day flaw in the software. The recent attacks have breached U.S. federal and state agencies, universities, energy companies, and an Asian telecommunications provider.
The vulnerability, called CVE‑2025‑53770, has been actively exploited since mid‑July, enabling remote code execution and allowing hackers to harvest cryptographic keys that persist even after patching.
The Washington Post reported that these breaches exploited a vulnerability impacting on-premises SharePoint servers, a widely used platform for document management and collaboration within organisations. The cyberattack has prompted urgent investigations by the U.S., Canadian, and Australian governments and forced thousands of organisations worldwide to scramble for a fix amid fears of lasting compromise.


Analysts warn many remain exposed as Microsoft has yet to release comprehensive security patches to fully address the threat. The incident highlights ongoing challenges in enterprise risk management related to legacy system reliance.
Despite previous high-profile attacks such as SolarWinds, Exchange, and MOVEit, many organisations continue to operate important systems on older platforms like SharePoint without contingency plans. They have been slow to migrate due to integration complexities, costs, or regulatory concerns. However, this recent attack may change that calculus.
Watch this video
Microsoft Responds
This latest breach affects only SharePoint servers managed on-premises by organisations, sparing cloud-based services like Microsoft 365. In a blog post on their website, Microsoft acknowledged the ongoing attacks targeting on-premises SharePoint Server customers by exploiting vulnerabilities only partially addressed by their July Security Update. The company emphasised that these vulnerabilities affect on-premises SharePoint Servers only, and that SharePoint Online within Microsoft 365 remains unaffected.
Microsoft confirmed that it has released security updates that fully protect users of SharePoint Subscription Edition and SharePoint 2019 against the risks associated with vulnerabilities CVE-2025-53770 and CVE-2025-53771. The company urged customers to apply these updates immediately to safeguard their systems.

Microsoft Issues Incomplete Fix
While Microsoft released a partial security update late Sunday for SharePoint Server 2019 and the Subscription Edition, earlier versions such as SharePoint 2016 remain vulnerable. In the absence of a complete fix, the company has advised organisations to disable external access or isolate their SharePoint servers until additional patches are available.
For these other supported versions, including SharePoint 2016 and some editions of SharePoint 2019, Microsoft is actively working on further security updates. Customers have been encouraged to monitor Microsoft’s official communications closely for any new information or releases.

Inside Modern Phishing Tactics
How social engineering exploits trusted channels to trigger breaches, and what controls leaders need to harden users as the new security perimeter.
Microsoft’s Ongoing Security Challenges
This breach is not an isolated event. It follows a series of damaging Microsoft-related cyber incidents, including the 2023 Chinese espionage campaign that compromised U.S. government email accounts, including those of then-Commerce Secretary Gina Raimondo. A U.S. cyber review board later attributed part of that breach to Microsoft’s operational security failures.
Meanwhile, in 2024, the National Public Data, a background check and fraud prevention service, suffered a major data breach that has raised serious privacy concerns. Its believed a malicious actor initially gained unauthorised access to their systems in December 2023. Over the following months from April through the summer of 2024, the stolen data was gradually leaked on the dark web.
The breach is believed to have exposed up to 2.9 billion records containing highly sensitive personal information. These records reportedly involve data from approximately 170 million individuals across the United States, the United Kingdom, and Canada, making it one of the largest data compromises in recent history.
Security experts say the SharePoint vulnerability, which allows remote code execution, is now being weaponised by multiple threat actors to access sensitive files, harvest credentials, and implant backdoors into enterprise systems.
Dutch cybersecurity firm Eye Security further reported that attackers had obtained encryption keys and tokens, enabling them to maintain covert access even after organisations apply patches, a growing tactic seen in modern state-aligned espionage.

Inside Public DNS Performance
Breaks down how leading DNS networks route queries, cut latency and offload fragile ISP infrastructure at global scale.

Impact of the SharePoint Zero-Day
The recent SharePoint zero-day vulnerability reveals more than a technical flaw; it highlights difficult challenges in how enterprises manage risk and respond to evolving cyber threats. As investigations unfold globally, the implications extend beyond IT, touching national security and international policy.
Let's have a look:
- No quick fix
With a sky-high CVSS score of 9.8, this zero-day vulnerability provides attackers a critical window to exploit systems. Even after patches are released, persistent cryptographic keys can allow continued access, complicating remediation efforts. - An evolving threat landscape
This breach is part of a broader pattern, echoing previous high-profile Microsoft incidents such as the 2023 state-sponsored email hack attributed to China. It highlights ongoing risks posed by legacy systems that affect both national security and enterprise operations. - Wider implications for enterprises
Legacy on-premises systems represent more than just IT risks; they can become national security liabilities. Even a forgotten or poorly managed server can serve as a critical vulnerability. Patching alone is no longer enough; persistent threats emphasise the importance of proactive measures such as threat hunting and regular cryptographic key rotation. - A geopolitical challenge
With investigations underway across the U.S., Canada, and Australia, the fallout from these breaches is rapidly evolving into a global policy concern. The SharePoint zero-day exposes systemic weaknesses in enterprise risk management and cybersecurity. Without proactive defence strategies and stronger vendor accountability, similar exploits will continue to threaten important systems worldwide.

When Blockchain Security Breaks
Human error, drainer kits and weak integrations now drive losses. Map the tools that contain fraud before immutable transactions settle.
A Global Wake-Up Call
Researchers warn that the breach poses a serious risk beyond initial access. Hackers have reportedly obtained information that could allow them to maintain access even after affected systems are patched.
One challenge is that releasing a patch days after an attack does little to help organisations already compromised during that period. This timing gap means many affected entities remain vulnerable even as fixes are rolled out, complicating efforts to contain the breach.
The attackers’ identity and motives remain unclear. However, private security firms have observed the campaign targeting a diverse range of victims including servers in China, a state legislature in the eastern U.S., and over 50 other breaches involving major energy companies and several European government bodies, according to Netherlands-based firm Eye Security.
The FBI issued a statement saying it is “working closely with federal government and private sector partners.” The Cybersecurity and Infrastructure Security Agency (CISA) is coordinating with Microsoft and affected sectors to contain the fallout.
The recent attack highlights how vulnerable many enterprise IT systems still are, especially those relying on software on their premises.

When Open Source Runs Defense
Assess how open-source firewalls reshape security strategy by trading license spend for transparency, control and in-house expertise.

Microsoft’s Zero Trust Strategy
Although it looks like the tech giant is trying to correct its wrongs from the past. In a March 2025 report, Forrester highlights Microsoft’s continued leadership in promoting Zero Trust security, a model focused on verifying every user and device before granting access. Since 2020, Microsoft has been a vocal advocate of this approach and is now expanding its strengths in identity management by tightly integrating its core security tools.
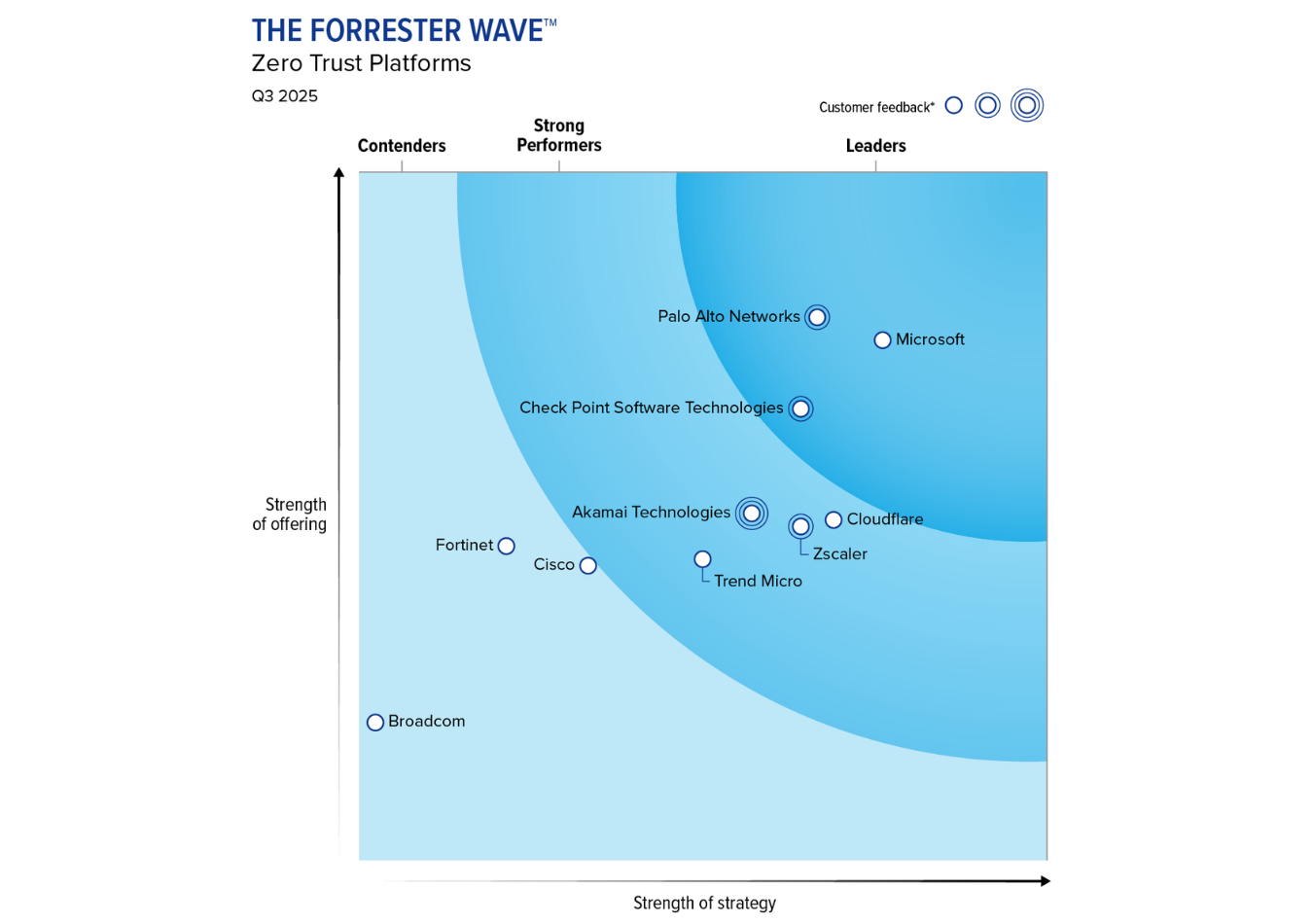
One standout offering is Microsoft Security Copilot, which leverages AI to help organisations, regardless of where they are on their cybersecurity journey, improve protection and streamline operations. This aligns with Microsoft’s broader vision of building proactive, AI-driven security architectures.
The report also points to Microsoft’s wide partner network and community resources, which provide support for enterprises looking to adopt Zero Trust frameworks. However, the report notes some downsides: Microsoft’s pricing can be complicated, and its long-term product roadmap lacks transparency, leaving some customers uncertain about future developments.
From a capabilities standpoint, Microsoft excels at enforcing strict identity controls and providing centralised management and visibility. While it supports both cloud and on-premises use, there is a clear emphasis on cloud readiness reflecting a wider industry shift.
Customers appreciate the simplicity and integration across Microsoft’s platform, though some have called for clearer support and more predictable end-of-life plans for certain features. Given these factors, Forrester recommends Microsoft for organisations prioritising cloud environments and aiming to minimise reliance on on-premises infrastructure.

Microsoft SharePoint Breach
With this in mind, the recent SharePoint attacks highlight the risks that come with relying on older, on-premises systems alongside cloud services. As organisations juggle this mix, attackers find more opportunities to exploit weaknesses, making timely updates and migrations critical.
Microsoft’s push toward Zero Trust security and AI-driven tools shows progress, but companies need to actively modernise their defences and improve threat detection. Simply patching vulnerabilities isn’t enough anymore.
Until businesses fully embrace these new approaches, breaches like this will continue to pose serious risks to essential systems in both the public and private sectors.
Watch this video below by EM360Tech’s Ben King for a breakdown of the incident and its implications:







Comments ( 0 )