Infrastructure today doesn’t live in a single rack or region. Instead, it stretches across clouds, geographies, and deployment models. And as that complexity grows, so does the cost of inconsistency — which ranges from configuration drift to delayed deployments and misaligned environments, and beyond. For enterprise infrastructure leaders, the challenge is no longer just scale. It’s stability at scale.
Infrastructure as Code (IaC) has emerged as a response to this problem, but it isn't just a way to automate infrastructure. With IaC, your team treats your infrastructure the exact same way they would software. Meaning manual provisioning and static templates are replaced by version-controlled code.

So automations replace repetition, configurations become repeatable, and you get more than just faster deployments in the end. Now you also have fewer errors overall, consistent environments, and the ability to quickly and easily scale your infrastructure — without sacrificing control.
But IaC is not just a DevOps tool or a cloud efficiency play. It’s a foundational capability for any organisation that needs to move fast without breaking things — especially when hybrid architectures and multi-cloud sprawl come into play.
Defining Infrastructure as Code in the Enterprise Context
Most infrastructure leaders wouldn’t dream of deploying an application without source control, testing, or rollback capabilities. But until recently, those same expectations rarely extended to infrastructure itself.
Infrastructure as Code (IaC) changes that. It uses the same rules that make guide software development best practices — versioning, modularity, and repeatability — to the infrastructure that runs it. Teams write and keep infrastructure definitions as code instead of using static templates or manual provisioning.
These scripts set the desired state for every part of your infrastructure, including virtual machines, networks, and IAM policies. And you can store, version, and reuse them just like any other part of your codebase.
The result is a shift from infrastructure-as-labour to infrastructure-as-product. You get faster environments, more predictable outcomes, and infrastructure that can actually scale with the systems it supports. But that shift also requires a new understanding of how different IaC models behave — and what they enable.
What does IaC actually do?
Infrastructure as Code replaces point-and-click provisioning with something far more scalable: code that defines the exact state your environment should be in. That includes every resource, dependency, permission, and setting — written out and versioned like any other software asset.
This isn’t just about faster builds. When your infrastructure lives in source code, it can be reviewed, tested, reused, and rolled back on demand. You get environments that are defined by logic, not by memory or manual effort. And because that logic is stored in code, it stays consistent across dev, test, and production.
Instead of writing up a checklist for provisioning infrastructure, you write a script that provisions it the same way, every time.
Declarative vs. imperative approaches to code-driven infrastructure
There’s more than one way to write infrastructure as code — and the approach you choose shapes how that code behaves.
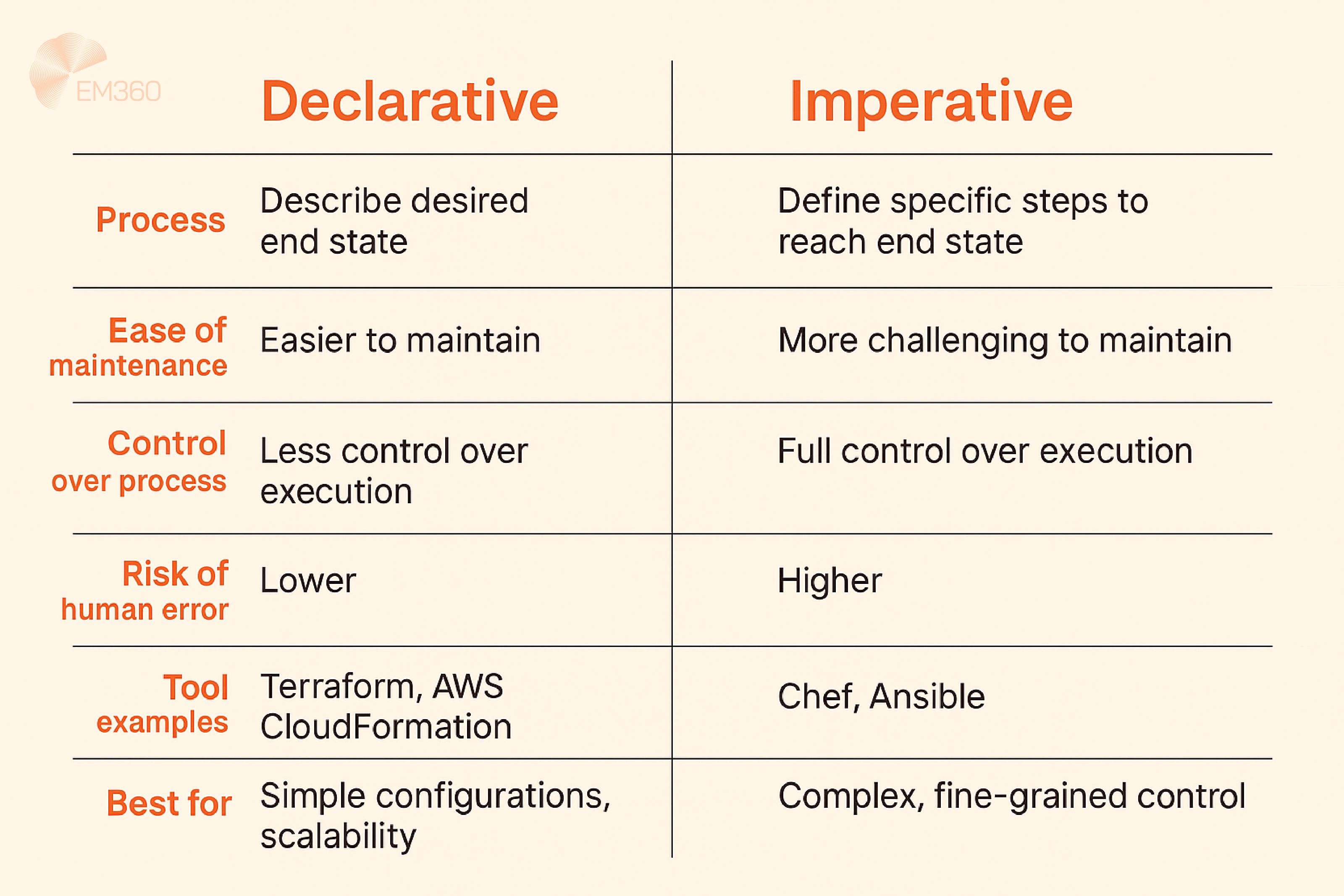
A declarative model describes what you want your infrastructure to look like. You define the outcome — a virtual machine with X specs, a database with Y permissions — and the tool figures out how to make it happen. Think of it like setting a destination on a map and letting your navigation system choose the best route.
From Audits to Continuous Trust
Shift compliance from annual snapshots to embedded, automated controls that keep hybrid estates aligned with fast-moving global regulations.

An imperative model, on the other hand, is about figuring out how to get your infrastructure to the state you want it to be in. In other words, you write down every single step that needs to be taken, in the exact order they must be taken, in order to build or change your environment.
This translates into more control over the whole process, but at the same time you’re responsible for things like sequencing, error handling, and state tracking.
Most modern IaC tools favour the declarative approach because it’s easier to maintain and less prone to configuration drift. It also pairs well with automation tools, which are designed to identify mismatches between current and desired states — then correct them automatically.
At the end of the day, choosing the right model isn’t about which one is better overall. Instead it’s about considering your infrastructure goals, the maturity of your team, and your risk tolerance — and understanding which of the two suits them best. Both can work, depending on your circumstances.
And the trick to deciding which one you’ll use is to treat your infrastructure not as something that just needs to be deployed, but rather as something worth designing.
Why IaC Is a Strategic Priority, Not Just a DevOps Tactic
Most DevOps teams already use some form of automation to speed up deployment. But Infrastructure as Code is not just another DevOps tool. When implemented properly, it becomes a lever for cost control, risk reduction, and operational consistency — and that’s exactly what elevates it from tactic to enterprise strategy.
With IaC, infrastructure provisioning stops being a one-off event and becomes a predictable, versioned capability. This brings consistency to how environments are built, no matter how often they’re deployed or where they’re running. It also means manual processes are replaced with code, and human error is significantly reduced as a result.
Inside Enterprise CI/CD Stacks
A comparative look at CI/CD platforms underpinning hybrid, Kubernetes and GitOps strategies for large, distributed engineering teams.

That shift has implications far beyond engineering. It allows teams to move faster without increasing risk. It improves the security posture of every environment. And it gives decision-makers the confidence that infrastructure won’t break under pressure — or at scale.
The business value of codifying infrastructure
When infrastructure becomes code, it becomes visible. That visibility translates into speed, control, and resilience — not just for software developers, but for any team responsible for maintaining infrastructure uptime or service availability.
Automated builds eliminate bottlenecks. Version control creates audit trails and rollback options. And consistent environments reduce the risk of issues in deployment, testing, or compliance reviews.
More importantly, teams spend less time troubleshooting infrastructure and more time improving it. That means shorter lead times, fewer incidents, and better collaboration between developers and operations.
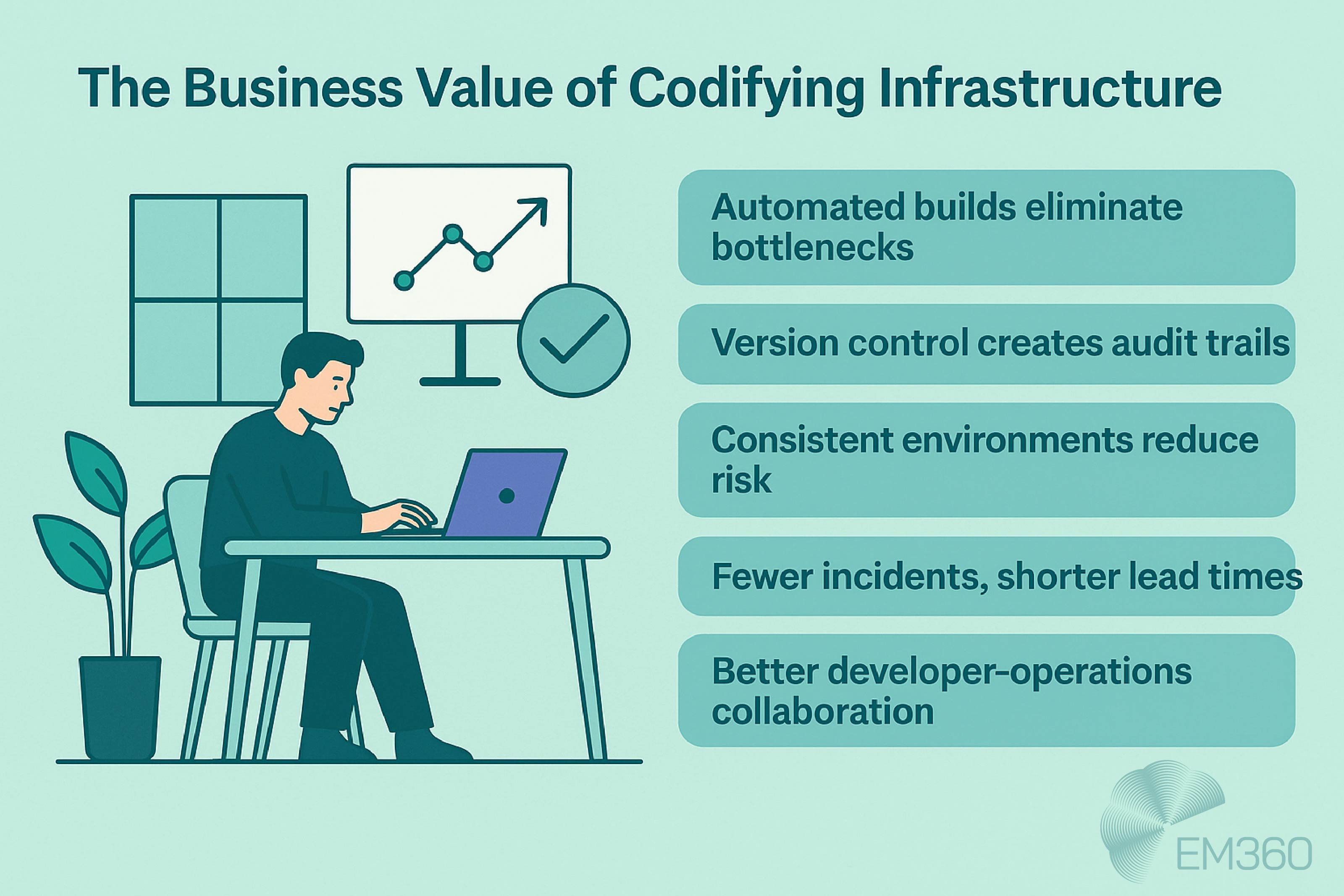
When viewed through a strategic lens, the benefits of Infrastructure as Code go well beyond automation. You’re codifying institutional knowledge, enforcing policy through logic, and creating infrastructure that scales with your organisation — without introducing more complexity.
Configuration drift and repeatability: IaC as risk mitigation
One of the most common causes of infrastructure instability is drift — when the production environment starts to diverge from dev, test, or staging. These mismatches leave holes in coverage, make systems more vulnerable, and slow down important fixes or updates.
By defining every environment in code, Infrastructure as Code gets rid of that risk. You don't depend on documentation or memory anymore; you depend on your version control system. That system becomes the only place to find out how infrastructure should look, work, and grow.
You don't have to worry about hidden config changes or silent failures anymore if you keep track of every change, make sure it's repeatable, and test it before you use it.
And if something does go wrong, you can roll back to a known good state — fast.
For enterprise teams managing hundreds of environments across hybrid or multi-cloud architectures, this is no longer a nice-to-have. It’s a baseline for stability, resilience, and trust.

DevOps Automation as Advantage
Turn routine workflows into a competitive edge by standardizing tooling, cutting release friction and amplifying scarce engineering talent.
Tools That Power Infrastructure as Code
Infrastructure as Code isn’t a single tool or platform. It’s a practice — one supported by a growing number of frameworks built to define, deploy, and manage infrastructure across hybrid and multi-cloud environments.
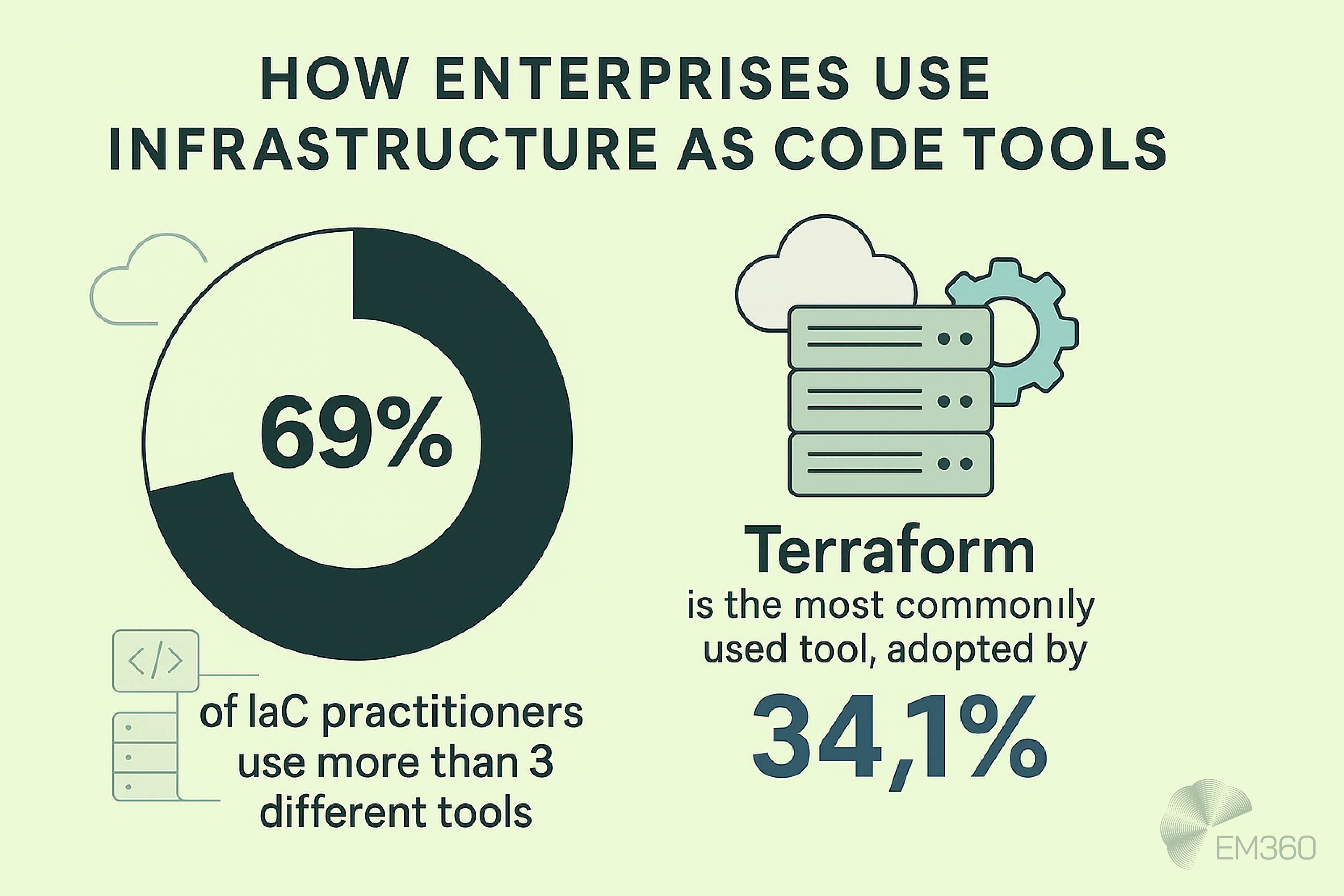
Cloud-agnostic tools like Terraform, Pulumi, and Ansible allow you to define infrastructure across AWS, Azure, Google Cloud, and on-prem environments using a single configuration language. These are especially useful for organisations managing hybrid architectures or working toward vendor diversity, since they offer flexibility without locking teams into one specific ecosystem.
Cloud-native tools such as AWS CloudFormation and Azure Bicep, on the other hand, are built to work within a specific provider’s environment. They offer tighter integration with native services, better compatibility out of the box, and in some cases, faster support for newly released features.
Most enterprises use a combination of both. Teams might rely on Terraform or Pulumi to provision cloud-agnostic workloads across environments, while using CloudFormation for more provider-specific templates and deployments already in place. The key is to choose tooling that fits your current infrastructure while also supporting the way you want your environments to evolve.
Beyond provisioning, these tools also play a critical role in CI/CD pipelines. They automate the creation of clean, consistent environments during the build and deployment process. They make application deployment repeatable by design. And when integrated with policy enforcement frameworks, they let teams codify access controls, encryption rules, and compliance logic — directly into the infrastructure layer.
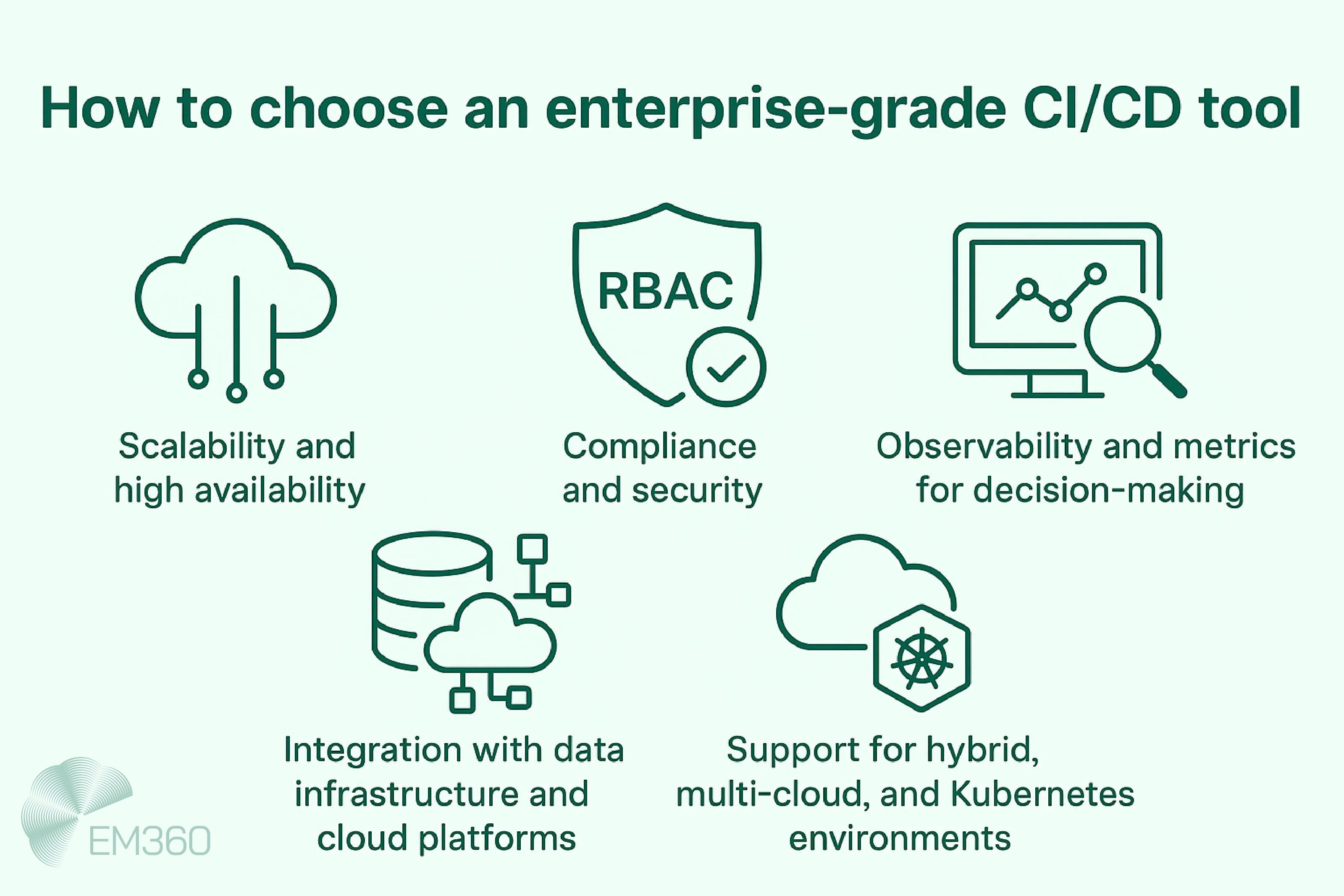
When it comes down to it, selecting a tool isn’t just about language preference or popularity. It’s about how well that tool supports your environment, your risk posture, and the way your teams actually work.
The Role of IaC in DevOps, Security, and Compliance
Why AI Needs Tool Consolidation
Tricentis shares how consolidating testing and AI tooling is becoming a board-level mandate for speed, quality and cost control in digital programmes.

Infrastructure as Code doesn’t just make environments faster to deploy. It also makes them easier to secure, easier to manage, and easier to audit. That’s because IaC integrates directly into the CI/CD process — allowing infrastructure to evolve alongside code without compromising stability or control.
By codifying infrastructure, teams can apply the same versioning, peer review, and testing processes they already use for application development. Changes are tracked. Rollbacks are built in. And every update to an environment can be tied directly to a commit, pipeline, or pull request.
This also makes it easier to shift from basic CI/CD to more mature models like GitOps or Policy as Code. Teams can manage infrastructure through , enforce environment rules through logic, and ensure that what gets deployed is not just functional — but also compliant.
From DevOps to DevSecOps: Security in IaC workflows
When infrastructure changes are handled manually, misconfigurations are almost guaranteed. And in modern environments, that risk adds up quickly. In fact, 59% of the respondents to a Checkpoint survey rank misconfigurations as their top cloud security concern.
Infrastructure as Code reduces that risk by enforcing consistency and visibility at every stage of the delivery pipeline. You know what’s being deployed, how it’s configured, and who made the change — because it’s all stored in code.
More importantly, you can automate validation before anything hits production. That means faster audits, simpler compliance reviews, and fewer opportunities for manual error to creep into critical systems. Tools like Checkov, Open Policy Agent (OPA), and HashiCorp Sentinel can scan code before it’s applied, checking for violations in access controls, encryption standards, or network policies.
This shift isn’t just about moving faster. It’s about building security into the way infrastructure is defined — not adding it on after the fact.
Policy as Code and enterprise guardrails
Policy as Code takes that idea a step further. It allows teams to encode governance rules directly into infrastructure definitions, so that enforcement becomes part of the provisioning process.
That might include access controls, encryption requirements, logging mandates, or resource limits. But instead of living in a spreadsheet or external policy doc, these rules are codified alongside the infrastructure itself — and evaluated every time a change is made.
Because these policies reflect the desired state of your infrastructure, they can be tested, versioned, and enforced automatically. If someone tries to deploy a resource without the required encryption or outside the allowed region, the tool can flag it or block it before anything changes.
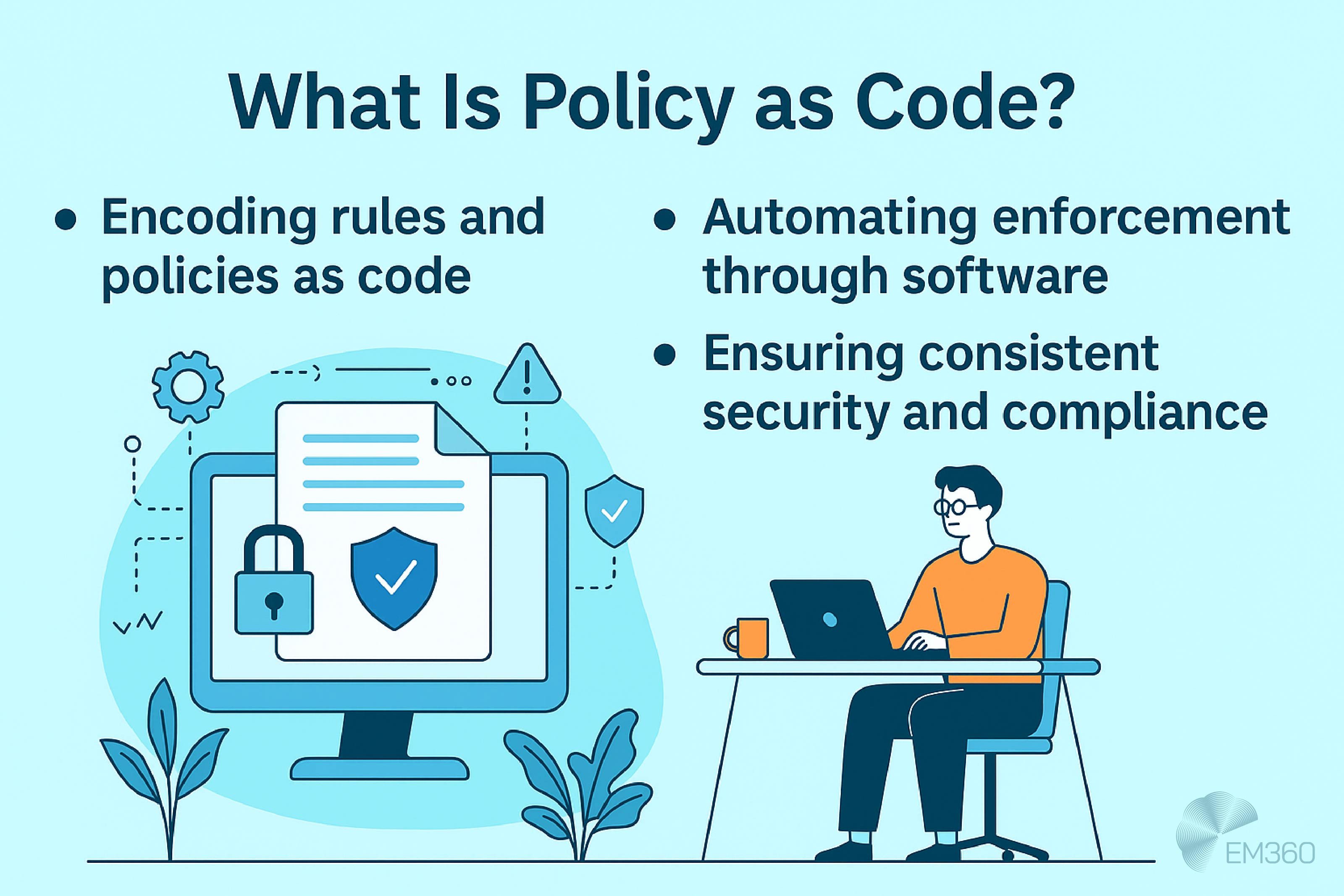
This turns governance from a reactive checkpoint into a real-time control. It also means security and compliance aren’t dependent on tribal knowledge or manual review. They’re enforced by automation tools, and they scale with your infrastructure.
For enterprises managing dozens of teams and hundreds of environments, that’s not just a benefit. It’s a baseline for control.
Challenges and Maturity Considerations
Infrastructure as Code can simplify complexity. But getting it right at scale still takes work. Many of the biggest challenges aren’t technical at all — they’re cultural, architectural, or rooted in decisions made early on without a long-term plan in place.
For some organisations, the biggest barrier is the learning curve. Writing good infrastructure code depends on a blend of software engineering principles and operational awareness. And for teams used to manual processes or point-and-click tools, that shift needs more than training.
It means changing how infrastructure is designed, reviewed, and maintained — and that can expose skills gaps, resistance to change, or outdated assumptions about who “owns” the environment. In other words, this sin’t an overnight sort of implementation.
Then there’s the question of legacy scripts and early-stage tooling. Many teams start with quick fixes — hardcoded values, siloed templates, minimal reuse — and wind up with technical debt that’s difficult to unwind later. Others underestimate what it takes to manage IaC at scale, from coordinating state files to enforcing consistent practices across teams.
Even the most advanced teams still face emerging challenges. As infrastructure grows more automated, questions around sustainability and governance become harder to ignore. And without the right maturity practices in place, even the best-intentioned IaC strategy can become difficult to sustain.
Avoiding script sprawl and governance debt
The more environments you manage, the more pressure there is to keep your infrastructure code clean, modular, and well governed. That’s where many early IaC efforts start to show cracks — not because the tools fail, but because the surrounding practices never evolve.
When every team builds from scratch, scripts pile up. Versions drift. Shared modules get overwritten. And the very benefits IaC was meant to unlock — repeatability, consistency, control — start to slip away.
The solution isn’t to write less code. It’s to write it better. That means structuring your source code in a way that reflects your architecture. It means using your version control system not just to store files, but to track decisions and enforce change control. And it means treating infrastructure code with the same standards of testing, review, and documentation you’d apply to any critical software system.
Without that maturity, IaC doesn’t scale. It fragments.
The emerging challenge of IaC sustainability
As automation becomes standard, a new question is starting to take shape: how efficient is the infrastructure we’re defining?
A 2025 study analysed almost 30,000 Terraform scripts and found widespread evidence of “sustainability smells” — inefficient code patterns that lead to unnecessary resource consumption. These included redundant provisioning, hardcoded configurations, and overly complex logic for routine tasks.
Left unaddressed, these inefficiencies add up. They consume more compute. They increase cloud spend. And they undermine the performance and sustainability gains that automation was supposed to deliver.
This isn’t just a tooling issue. It’s a design issue. The infrastructure you define is the infrastructure you run — and over time, poor code habits lead to higher environmental and financial costs.
That’s why maturity in IaC now includes sustainability. It’s not just about achieving the desired state. It’s about doing so in a way that reflects your values, your budget, and your long-term goals.
Where IaC Is Going: Trends to Watch
Infrastructure as Code has already transformed how environments are built, deployed, and secured. But its most significant evolution may still be ahead. As complexity grows and pressure on infrastructure teams increases, the next wave of IaC tools and practices is focused on automation, intelligence, and control at scale.
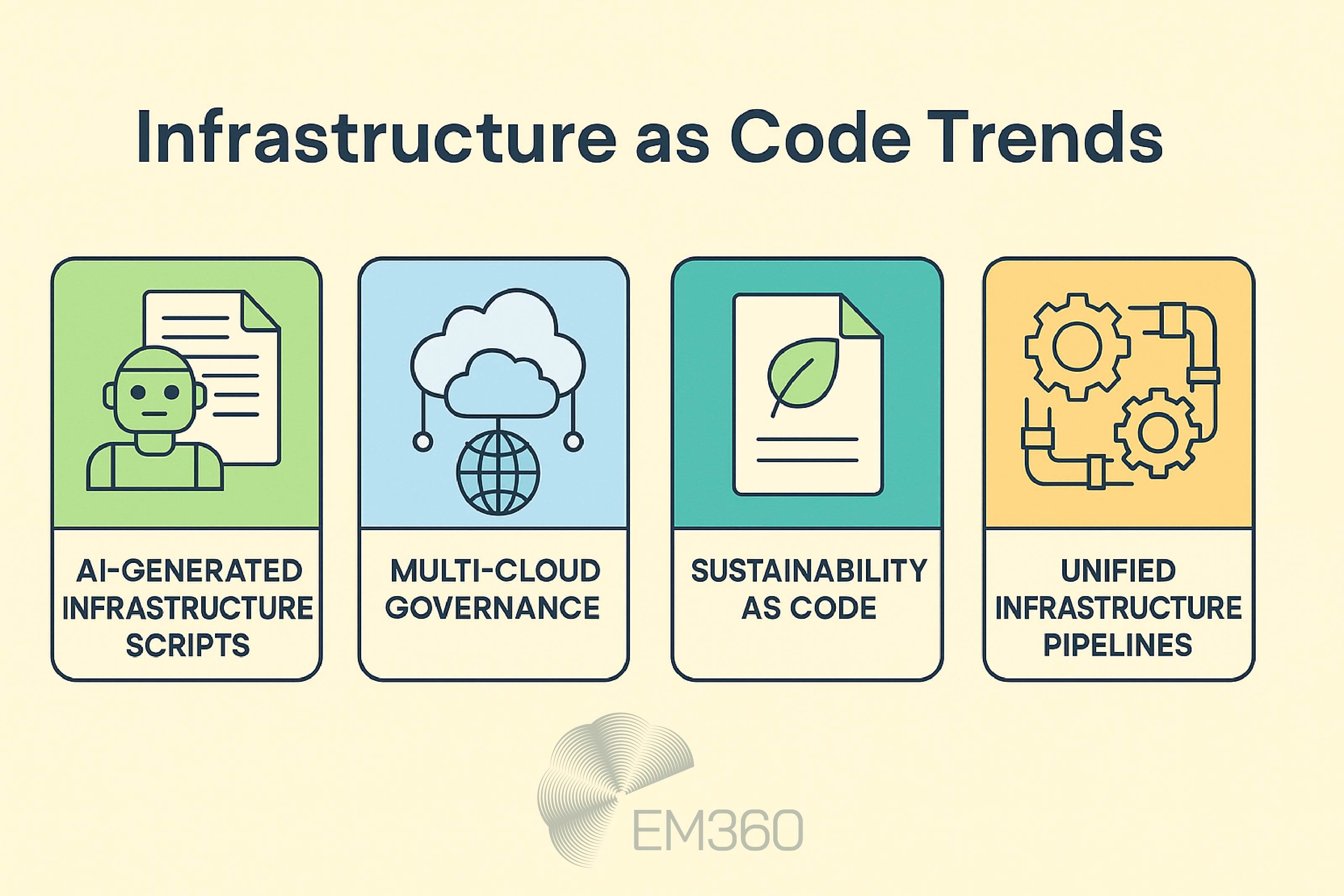
One of the most visible shifts is the rise of AI-assisted provisioning. Tools like IaCGen and emerging GitHub Copilot integrations are beginning to generate infrastructure scripts based on natural language prompts. That doesn’t mean replacing your engineers — it means giving them faster ways to scaffold configurations, enforce standards, and reduce repetitive tasks. Early results are promising, especially when paired with defined modules and guardrails.
Meanwhile, enterprises are doubling down on multi-cloud governance. IaC is being used not just to provision infrastructure, but to enforce architecture strategy across providers. That includes automating compliance checks, embedding policy controls, and ensuring consistent environments — even when the underlying cloud platforms differ.
We're also seeing more conversations around sustainability-as-code. As organisations become more conscious of their environmental footprint, IaC offers a way to enforce green defaults, eliminate redundant resources, and optimise consumption by design. That could mean tagging resources for lifecycle automation, or using configuration rules to restrict high-impact services by default.
Finally, there's the convergence of IaC with adjacent disciplines like CloudOps, GitOps, and unified infrastructure pipelines. These are different models, but the goal is the same: reduce friction between infrastructure and application delivery. In practice, that means tighter integrations between code repos, orchestration tools, CI/CD platforms, and provisioning infrastructure — all managed as a single, automated pipeline.
As these trends mature, the role of Infrastructure as Code will only grow. Not as a set of scripts, but as a strategic layer of control across everything the business builds, secures, and scales.
Final Thoughts: The Value of IaC Is How It Changes What Infrastructure Can Do
Infrastructure as Code isn’t just a better way to provision environments. It’s a smarter way to manage infrastructure as a whole — from the way it’s built, to how it’s governed, to how it scales alongside the business.
It brings consistency to complex architectures, codifies best practices across teams, and creates a foundation for security and compliance that doesn’t slow delivery down. And when applied with care, it reduces waste, mitigates risk, and turns infrastructure into a strategic advantage — not a source of friction.
For enterprise teams navigating hybrid complexity, multi-cloud sprawl, and rising demand for speed without compromise, IaC has become more than an automation tool. It’s become the connective tissue between infrastructure, operations, and innovation.
To go deeper into how today’s teams are building and scaling smarter, explore more of EM360Tech’s insights on infrastructure strategy and DevOps maturity — and see how other enterprise leaders are moving from patchwork provisioning to infrastructure that’s ready for what’s next.





Comments ( 0 )