Shadow IT risks are a growing concern for modern organisations as employees increasingly use unauthorised hardware, software, or cloud services without IT approval. With the rise of remote and hybrid work and the easy availability of cloud-based tools, shadow IT has become more widespread than ever.
But what is shadow IT? Simply put, shadow IT refers to any technology, whether hardware, software, or cloud services, that employees use for work without the knowledge or authorisation of the organisation’s IT department.
Employees often adopt unsanctioned apps or personal devices to work more efficiently, collaborate faster, or bridge gaps in the standardised tools the company offers, but this practice brings significant risks.

When employees bypass IT controls and governance to deploy personal laptops, messaging platforms, file-sharing services, or SaaS applications, they create dangerous blind spots for security and compliance teams.
These unauthorised tools can easily become entry points for cyberattacks, cause data leaks, or expose sensitive business information to external threats. The increase in consumer-driven technologies like smartphones, personal apps, or cloud services, which are increasingly used in workplace settings, has only accelerated these shadow IT risks, as users grow more comfortable downloading and integrating apps directly from the cloud without consulting their IT departments.
Shadow IT risks go beyond simple applications; they can also include personal smartphones, unmanaged hardware, and even entire infrastructure purchases that slip past IT’s oversight. This unchecked growth results in “app sprawl,” wasted budgets, duplicate systems, and poor collaboration.
More seriously, shadow IT assets left off the security team’s radar make it impossible to properly manage vulnerabilities, leaving the organisation wide open to attacks.
Technology leaders must gain a clear view of shadow IT, understand its risks, and establish balanced strategies that enable innovation while safeguarding security, compliance, and cost efficiency.
Understanding Shadow IT in 2025
Shadow IT risks in 2025 have evolved beyond unauthorised applications alone. The phenomenon now includes “shadow AI,” where employees use unapproved artificial intelligence tools that may expose sensitive data or create new security vulnerabilities.
As remote and hybrid work models continue to expand, employees are more empowered and sometimes more impatient to adopt technology that helps them work faster and smarter, whether or not IT teams have approved it.
Recent statistics highlight just how widespread shadow IT has become:
- 64 per cent of employees admit to using unsanctioned SaaS applications for work, with 26 per cent doing so every day.
- 50 per cent of organisations have already suffered a security breach tied to shadow IT.
- 67 per cent of employees in large enterprises use unapproved SaaS apps, and 42 per cent of company applications are considered shadow IT.
These numbers confirm that the risks are significant and growing, especially as the consumerisation of technology makes it easier than ever for staff to adopt tools independently.
Shadow IT now extends into artificial intelligence, where generative AI platforms are being leveraged without proper vetting, raising concerns about data privacy, compliance, and the security of proprietary information.
Common Types of Shadow IT Applications
- Cloud storage services: Unapproved use of platforms like Dropbox or Google Drive to store or share business data outside of managed environments.
- Communication tools: Employees relying on consumer-grade messaging apps such as WhatsApp or Slack without IT oversight, risking insecure data exchanges.
- Productivity applications: Tools like ClickUp, Trello, or TickTick used outside official channels, creating inconsistencies and potential data silos.
- AI tools: Generative AI systems adopted without IT approval, which may lead to uncontrolled data exposure, intellectual property risks, or compliance failures.

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
As these shadow IT risks grow more complex, technology leaders must take proactive steps to identify and manage them before they undermine business security, compliance, and operational stability.
7 Risks of Shadow IT
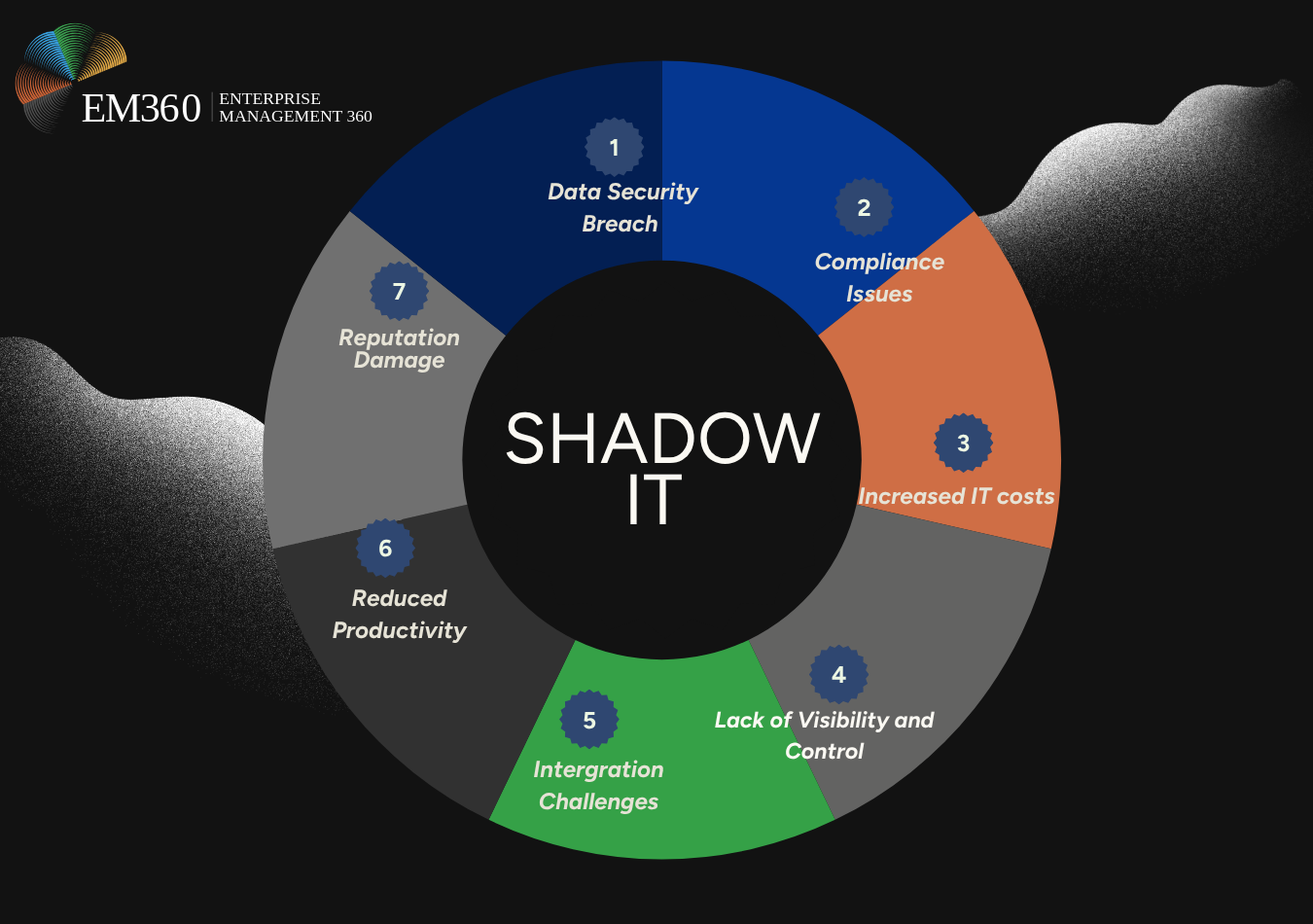
To build these balanced strategies, it’s important to first understand exactly where shadow IT can go wrong. By identifying the specific risks associated with shadow IT, technology leaders can prioritise their efforts and address the most critical threats.
Here are seven key shadow IT risks every organisation should be aware of:
1. Data security breaches
Shadow IT significantly heightens the risk of data security breaches. Employees may store sensitive corporate data in unauthorised cloud applications and other unsecured shadow IT solutions, putting that data at serious risk. Without the benefit of IT-approved safeguards such as encryption, data backups, or strong access controls, this information can be easily leaked, stolen, or permanently lost.
A data breach occurs whenever unauthorised parties gain access to confidential information, whether that includes personal data like bank account details, healthcare records, or Social Security numbers, or corporate data such as intellectual property, customer records, or financial reports.
Many of the controls organisations apply to sanctioned devices and services, including encryption and allow/deny listing, are unlikely to be properly enforced on shadow IT assets. Protecting data becomes an even greater challenge because if you don’t have control of the services processing data, or the devices that hold data, you can’t be sure appropriate backups are being made.
As a result, organisations cannot reliably track where their data is stored, how it is processed, or where it might ultimately end up. Around 30–40 per cent of organisations have suffered data breaches or leaks linked to shadow IT in 2025 so far. This lack of oversight exposes businesses to threats such as ransomware, legal repercussions over data privacy violations, reputational damage, and costly recovery efforts.
2. Compliance issues
Inside a Social Graph Collapse
A case study in weak mobile-era adaptation, algorithm shifts, and feature deprecation eroding network effects in visual platforms.

Shadow IT introduces significant compliance and regulatory risks for organisations. When employees use unauthorised hardware, software, or cloud services, they may inadvertently violate strict industry standards and company policies designed to protect sensitive data.
Regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) all place rigorous requirements on how personal and corporate data is collected, processed, and stored.
Shadow IT solutions, lacking formal oversight, often fail to meet these compliance standards, increasing the likelihood of a data breach and exposing organisations to serious legal and financial consequences. In 2025, so far, at least 53 per cent of organisations have experienced compliance violations due to shadow IT.
Non-compliance stemming from shadow IT can result in substantial fines, mandatory audits, and even criminal charges for executives in severe cases. Regulatory authorities may impose penalties reaching into the millions, while affected customers or partners could pursue costly legal action. Repeated compliance failures risk damaging a company’s reputation and may lead to the loss of business licences or stricter government oversight.
One key challenge is that unauthorised cloud services and personal devices, especially in BYOD (bring your device) environments, can blur the lines between personal and corporate data, making it difficult to enforce policies consistently. Employees may store or transmit sensitive data through unapproved platforms that lack essential security measures, or through cloud services operating in unapproved jurisdictions, breaching data residency laws.
Similarly, using personal email accounts or non-compliant messaging apps can expose confidential business communications to unintended recipients. More than 75 per cent of IT leaders say shadow IT complicates compliance and security efforts
The consequences of compliance failures extend beyond fines and legal action. Organisations often face reputational harm, operational disruption, and costly recovery processes.

Closing the Distributed Device Gap
Contrast top UEM choices to cut attack surface, enforce data protections and sustain a consistent user experience at scale.
In many cases, the cost of correcting compliance failures after the fact far exceeds the investment required for proactive shadow IT management. As a result, implementing clear policies and oversight to identify and control shadow IT is critical to maintaining compliance and safeguarding sensitive business data.
3. Increased IT costs
Shadow IT can drive unexpected costs and budget overruns that organisations may not fully recognise until the financial impact becomes substantial. These hidden expenses can strain budgets, disrupt financial planning, and drain resources away from strategic priorities.
When employees in remote teams independently adopt unauthorised tools and services, they often create duplicate licensing costs and wasted investments. For example, a remote team using unapproved collaboration software might inadvertently pay for duplicate licences, incur training costs for non-standard platforms, or experience integration challenges when those tools conflict with officially supported systems.
Similarly, remote workers adopting unsanctioned file-sharing services can create data silos, reduce team coordination, and introduce data loss risks that lead to expensive recovery efforts.
Beyond duplicate software costs, shadow IT can lead to broader financial exposure. Security incidents involving unsecured, unmonitored tools may require costly legal support, regulatory fines, and brand damage repairs. Without centralised visibility and control over Software as a Service (SaaS), organisations risk overspending on cloud subscriptions, especially when remote teams use similar tools independently. Incompatible systems can also reduce productivity, leading to hidden operational costs over time.
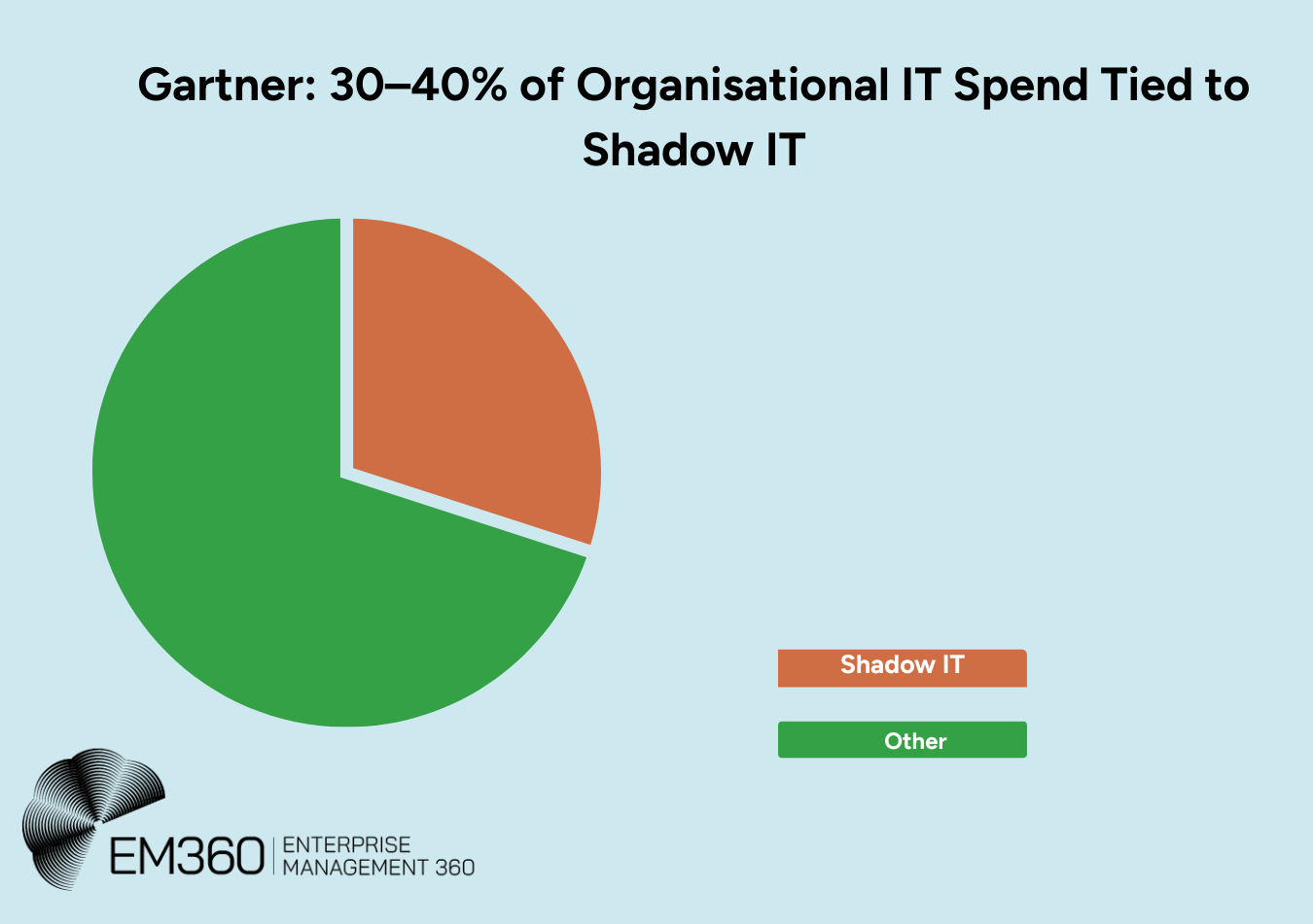
According to Gartner, as of 2025, up to 30 - 40 per cent of IT spending within organisations is linked to shadow IT—technology and services operating beyond official approval. Meanwhile, 60 per cent of IT leaders report being unaware of which cloud applications their employees use, suggesting that a significant share of IT budgets is consumed without proper oversight. These unplanned costs not only undermine budgets but also introduce security gaps and operational inefficiencies that can quickly spiral out of control.
4. Lack of data visibility and control
When File Sharing Becomes Risk
How SMB signing turns routine file sharing into a strategic control point, and what misconfigurations silently erode that protection.
Shadow IT poses a significant challenge to data visibility and control. This is due to unauthorised tools often operating outside the organisation’s approved systems, which remain largely invisible to IT teams.
Estimates suggest that between two-thirds and four-fifths of shadow IT applications go completely untracked, creating opaque data environments where sensitive information can be accessed, stored, or shared without oversight.
Alarmingly, nearly 75 per cent of shadow IT tools are only discovered during investigations or audits, often too late to prevent damage. This lack of visibility can lead to increased workload and stress on IT personnel as they scramble to address issues arising from unsupported applications.
Proactive detection is further hampered by insufficient governance practices, as many organisations do not maintain adequate inventories, policies, or monitoring systems to identify and manage unsanctioned tools. As a result, around 65 per cent of organisations report lacking visibility into shadow IT activity, leaving most of these tools to operate under the radar. When employees use unauthorised software or cloud-based services, IT teams lose the ability to track how data is handled, apply software updates, or enforce security measures. This weakens the organisation’s overall security posture and exposes it to considerable risk, including data breaches, compliance violations, and operational disruptions.
5. Integration challenges
Shadow IT creates huge obstacles to the seamless integration of software and applications within organisations. Over half of companies (55 per cent) report lacking a centralised inventory of all IT assets, including shadow IT tools, making it difficult to effectively manage and integrate these unauthorised applications. If that is not scary enough, 59 per cent of IT departments struggle to incorporate shadow IT into the official infrastructure, resulting in fragmented systems and disrupted workflows.
This fragmentation often leads to data silos, where different teams rely on separate tools that don’t communicate, causing duplication of effort, miscommunication, and lost time. In the absence of proper integration, employees may resort to manual data entry or frequent exports to bridge gaps between platforms, which increases the likelihood of errors and inconsistencies. The need to support and troubleshoot shadow IT diverts valuable IT resources away from strategic projects, slowing down digital transformation efforts and negatively impacting overall organisational productivity.
6. Reduced productivity
Shadow IT can significantly hinder employee productivity and collaboration. When teams rely on incompatible or redundant software, they often face workflow disruptions, manual workarounds, and increased frustration. These unsupported tools may cause compatibility issues or leave employees without proper training, leading to inefficiencies and duplicated efforts. Studies show businesses can lose up to 20–30 per cent of productivity due to these challenges.
Data breaches linked to shadow IT are often harder and slower to detect and resolve compared to those involving approved systems. The lack of visibility and control over unauthorised tools means that security teams may not become aware of incidents right away, allowing threats to persist longer.
This delay in detection and containment can extend the time an organisation is exposed to risk, potentially causing serious disruptions to operations and increasing the overall damage caused by the breach. The fragmented work environments created by shadow IT force employees to juggle multiple, disconnected platforms, spending excessive time troubleshooting and coordinating across siloed systems.
7. Reputation Damage
Shadow IT doesn’t just pose technical or compliance risks; its impact can extend deeply into a company’s reputation and credibility. A single publicised data breach linked to unauthorised tools can instantly erode customer trust, damaging the brand in ways that take years and significant effort to repair.
In an age where data privacy and security are paramount, consumers expect organisations to safeguard their information rigorously. When shadow IT leads to a security incident, the resulting negative publicity can cause irreparable harm to a company’s image.
According to IBM’s Cost of a Data Breach Report, breaches involving shadow data are especially costly, with organisations incurring expenses around 16 per cent higher on average compared to other breaches. This increase stems not only from prolonged investigations but also from managing public relations crises and rebuilding damaged relationships with customers and partners.
Nearly half of organisations (48 per cent) have reported that incidents related to shadow IT have directly caused measurable reputational harm. This includes loss of customer trust, reduced brand loyalty, and negative perceptions in the marketplace. The ripple effects can be severe, beyond immediate financial loss, organisations risk losing long-term business opportunities and suffering decreased market value.
Ultimately, shadow IT incidents highlight a broader issue: poor control over unauthorised tools weakens an organisation’s ability to respond swiftly and effectively to breaches. Longer investigation times and higher remediation costs amplify the fallout. This highlights the importance of comprehensive shadow IT management — not only to protect data and ensure compliance but also to safeguard a company’s reputation, which is often its most valuable asset.

Understanding the Root Causes of Shadow IT
It’s important to recognise that shadow IT is rarely the result of malicious intent. More often, it emerges because employees perceive official tools or processes as insufficient for meeting their work needs. Faced with productivity challenges or workflow bottlenecks, they turn to unofficial solutions to get their jobs done efficiently.
Common factors driving the adoption of shadow IT include:
- Limited storage capacity on sanctioned platforms
- Inability to share data easily with external partners or third parties
- Lack of access to essential services, such as specific development or testing tools
- Absence of approved video conferencing or instant messaging applications
- Cumbersome, slow, or ineffective procedures for requesting new IT assets or services
- Official tools or SaaS offerings that lack required features or flexibility
- Employees’ unawareness that using personal devices or unmanaged SaaS solutions can introduce significant security and compliance risks
By understanding these underlying reasons, organisations can better address the root causes of shadow IT and develop solutions that meet employees’ needs while maintaining security and governance.
Common Examples of Shadow IT Applications
Shadow IT covers a wide range of unauthorised tools and platforms that employees adopt without formal IT approval.
Here are some common examples:
- Cloud storage platforms: Employees may store sensitive data on unauthorised services such as Dropbox or Google Drive, bypassing corporate data protection measures.
- Communication applications: Tools like WhatsApp or Slack are sometimes used without IT approval, creating gaps in compliance and security oversight.
- Productivity and task management tools: Platforms such as ClickUp or TickTick can be adopted outside official procurement processes, introducing compatibility and integration challenges.
- Artificial intelligence solutions: Generative AI tools, if deployed without proper review and governance, can increase the risk of data exposure and compliance violations.
How to Mitigate the Risks of Shadow IT
Effectively managing shadow IT requires a proactive, multi-layered approach that balances security with employee productivity. Here are key strategies organisations can implement to reduce shadow IT risks while supporting their workflow:
1. Implement a strong IT governance framework
Establish clear oversight of technology usage across the organisation. A governance framework defines roles, responsibilities, and processes to manage software procurement, deployment, and monitoring systematically.
2. Educate employees and promote transparency
Awareness is critical. Train employees on the risks associated with shadow IT and encourage them to be transparent about the tools they use. When staff understand the potential consequences, they’re more likely to follow established procedures and seek approval for new applications.
3. Create clear policies and guidelines
Develop and communicate straightforward policies that specify what software and hardware are permitted, how purchases should be approved, and the consequences of circumventing these rules. Well-defined guidelines reduce ambiguity and reinforce compliance among your employees.
4. Conduct regular audits and usage reviews
Schedule frequent audits comparing actual application usage with license invoices to detect duplicate subscriptions, redundant software, or unauthorised tools. Proactive audits help uncover shadow IT early and prevent unnecessary spending.
5. Invest in Secure, User-Friendly Technology Solutions
Provide employees with approved, easy-to-use tools that meet their needs. When official platforms offer the required functionality and usability, employees are less likely to seek alternatives outside IT’s control.
6. Adopt Shadow IT Detection Tools
Leverage specialised solutions to monitor application usage in real time, manage software licences, and reduce security risks. These tools help organisations identify and respond swiftly to unauthorised app deployments.
7. Simplify IT approval processes
Streamline and accelerate the process for approving new software and services. Removing bureaucratic bottlenecks reduces the temptation for employees to find unofficial workarounds and encourages compliance with IT policies.
By combining these strategies, organisations can minimise the risks of shadow IT while empowering employees with the tools they need to perform effectively and securely.
Bringing Shadow IT Under Control
Shadow IT continues to present significant challenges for organisations, particularly as employees turn to unapproved tools in search of faster, more flexible ways to work. While these tools may seem to offer immediate benefits, they introduce long-term risks ranging from security breaches and compliance failures to operational inefficiencies and wasted budgets.
In an era of increasingly blended teams — with both insourced and outsourced software engineering talent — managing technology governance has never been more crucial. According to Gartner, by 2026, 80 per cent of organisations that effectively combine insourced and outsourced software engineering teams through clear roles and responsibilities will see a 30 per cent improvement in team productivity. This underscores the importance of strong collaboration, oversight, and defined processes.
To address the risks posed by shadow IT, organisations must proactively invest in solutions that offer visibility, security, and ease of use. SaaS management platforms are available to provide the tools needed to regain control of the IT environment, eliminate hidden software deployments, and improve costs. If this is coupled with employee education, simplified approval processes, and ongoing audits, these measures form a secure defence against the dangers of shadow IT.
Ultimately, striking the right balance between enabling innovation and maintaining secure, governed systems will help organisations succeed in a complex delivery ecosystem and build a foundation for greater productivity and business success.







Comments ( 0 )