While originally created to support Bitcoin, blockchain technology is set to revolutionise how businesses and financial institutions across the globe store and verify data.
According to Statista, spending on blockchain solutions will grow exponentially over the next few years, reaching almost $19 billion in the US alone by the end of 2024 as organisations across different industries adopt the powerful technology.
One of the key reasons Blockchain is gaining popularity is its security. The technology is helping finance corporations and large organisations prevent fraud and unauthorised activity while also reducing costs and increasing efficiency.
But, as blockchains become more and more common in the enterprise world, it’s important to note that the technology is not unhackable. That’s why blockchain security is crucial.
In this article, we’ll explore the key components of blockchain security, what makes blockchain secure, and the challenges organisations face when securing the technology.
What is Blockchain Security?
Blockchain security refers to the combination of techniques, tools, and practices that protect blockchain networks from cyber attacks and fraud. It is based on the principles of cryptography, decentralization and consensus, which each ensure trust in every transaction.
Securing a blockchain is a multi-layered approach that uses various components to ensure the integrity, confidentiality, and availability of data stored on the blockchain.
Here's a breakdown of some key aspects of blockchain security:
1. Cryptography
One of the key components of blockchain security is its cryptographic principles. Each block contains a unique hash value generated based on the data it contains, making any unauthorised changes to the block immediately detectable.
Digital signatures add to this protection, providing a mechanism for verifying the authenticity of transactions. The combination of these cryptographic elements creates a robust foundation for securing the data stored on the blockchain.
2. Decentralisation
The decentralized structure of blockchains is also a key factor in their security. Unlike traditional centralized systems, where a single point of failure can jeopardize the entire network, blockchains distribute data across a network of nodes. This reduces vulnerability to attacks and enhances the overall security of the system by eliminating a central target for malicious activities.
3. Consensus
Another crucial element of blockchain security is consensus mechanisms. Every transaction on a blockchain is also encrypted using complex consensus algorithms that ensure data integrity and authenticity. These algorithms ensure agreement among nodes on the state of the blockchain, requiring participants to solve complex mathematical problems or give proof of their stake in the system to gain access.
What makes blockchain so secure?
Unlike traditional centralized systems, the data in blockchains is structured into blocks and each block contains a transaction or bundle of transactions. This makes them incredibly secure, since compromising a single block or even a group will not impact the entire network.
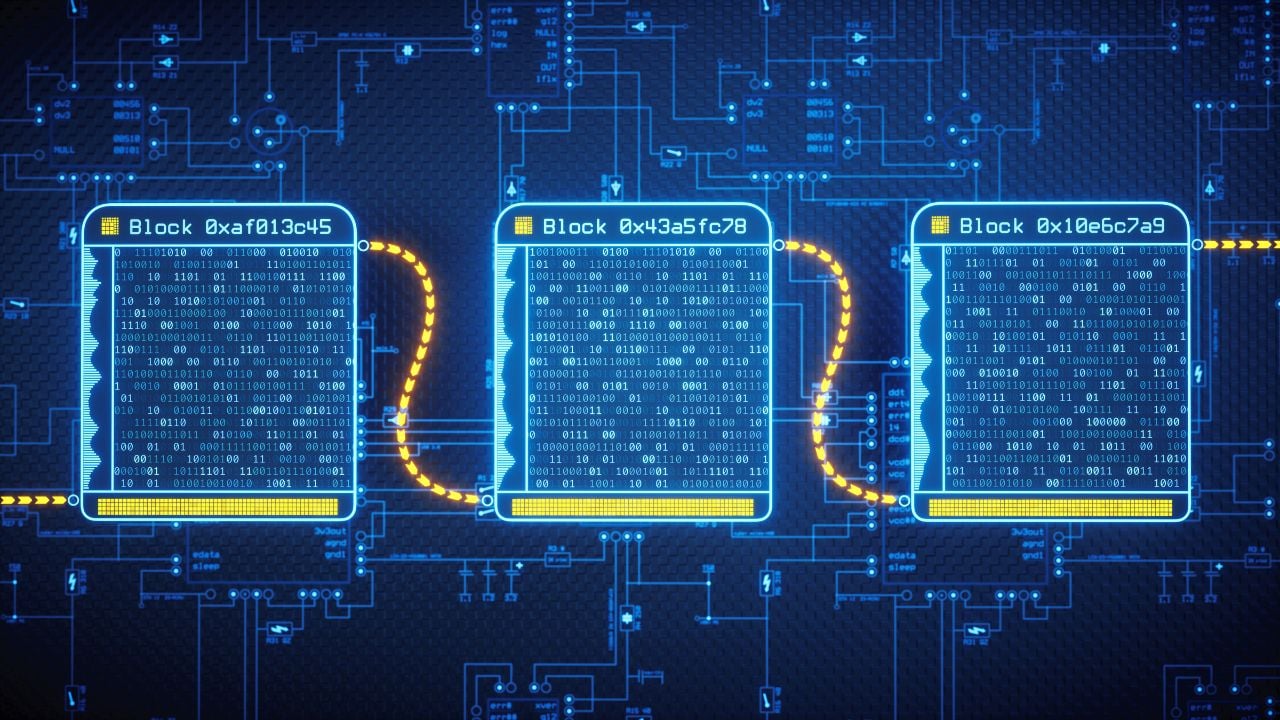
Each new blockchain block also connects to all the blocks before it in a cryptographic chain in such a way that it's nearly impossible to tamper with. All transactions within the blocks are validated and agreed upon by a consensus mechanism, ensuring that each transaction is authorised.
Nobody can change or delete existing data either. Any attempt to tamper with the ledger is easily traced back to the prospective hacker, who then typically loses access to the network.
Securing the four types of blockchain
While the design of blockchains makes them easy to secure, there are several types of blockchains that each serve different purposes. Securing these different types of blockchains involves implementing specific measures tailored to the characteristics and use cases of each blockchain.
1. Public Blockchains:
Public blockchains are open and decentralized networks where anyone can participate, validate transactions, and become a part of the consensus process. Security in public blockchains primarily focuses on ensuring the integrity of transactions while preventing double-spending and maintaining the overall health of the network.
Public blockchains rely on robust consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to achieve a high degree of security. PoW, for example, uses computational power to validate transactions, making it difficult for malicious actors to disrupt the network.
Measures like firewalls, intrusion detection systems, and secure coding practices are also crucial for individual nodes to resist cyberattacks and vulnerabilities. In blockchains like Ethereum, for instance, smart contract audits and secure coding practices are vital to prevent exploits and ensure code integrity.
2. Private Blockchains:
Private blockchains are centralized and restricted to a specific group of participants. They are often used within organizations for internal processes. Security in private blockchains focuses on controlling access, ensuring data privacy, and maintaining the reliability of transactions.
In private blockchains, only authorized participants can join the network, reducing the attack surface and simplifying security measures. The governing organization can implement stricter security policies and controls, such as transaction restrictions and user authentication protocols.
Some private blockchains use consensus mechanisms like Byzantine Fault Tolerance (BFT) which prioritizes fast transaction finality without requiring high mining power like PoW. Sensitive data is also often encrypted at rest and in transit to further improve security.
3. Consortium blockchains
Consortium blockchains are semi-decentralized and involve a group of organizations working together. Security measures focus on balancing the benefits of decentralization with the need for controlled access and governance.
In consortium blockchains, security measures are often shared among consortium members, leveraging their expertise and resources for a robust defence. Consortiums can tailor consensus mechanisms to their specific needs, balancing security with efficiency and performance.
Strong identity verification and access control systems are crucial to ensure only authorized parties participate in the network. Effective communication and collaboration among consortium members are also key so that they can identify and address potential security threats quickly.
4. Hybrid blockchains
Hybrid Blockchains combine elements of both public and private blockchains. They are designed to leverage the benefits of public networks while maintaining control over certain aspects. Security measures in hybrid blockchains address the unique challenges this combination can cause.
To do this, Hybrid blockchains leverage the strengths of both public and private chains, often combining strong cryptography and consensus mechanisms from public chains with the permission access and centralized control of private chains.
Examples of Blockchain Security
While blockchain is still under development, its security features are already being used in innovative ways across various industries. Here are some examples of blockchain security in action:
- MediLedger – MediLedger, a consortium of leading pharma companies, uses blockchain to track the movement of drugs and authenticate their legitimacy. This helps combat counterfeit drugs and improve patient safety. Unlike public blockchains like Bitcoin, MediLedger is private, meaning only authorized participants (pharmaceutical companies, distributors, pharmacies, etc.) can access the network. It also prioritizes verifying and aligning transaction-related data between trading partners. This ensures everyone has a single, consistent view of the data, reducing errors and security issues.
- J.P Morgan – The US financial giant J.P. Morgan actively uses blockchain technology to keep transactions secure and protect data from unauthorized access. The company has developed its blockchain platform called Quorum, which is an enterprise-focused distributed ledger technology. Quorum is designed to address the specific needs of financial institutions, providing features like privacy and permissioning. It’s an Ethereum-based platform and has been used for various applications within the financial industry
- Walmart – Walmart partnered with IBM Food Trust to track the journey of various food products from farm to store using blockchain technology. This allows them to quickly identify the source of potential contamination outbreaks and improve overall food safety. Blockchain solutions have also streamlined communication and data sharing between Walmart and its suppliers and logistics partners. This results in faster, more efficient deliveries and reduced discrepancies in invoices and payments.
- Coinbase – Coinbase is an exchange for selling and purchasing cryptocurrency. Running entirely on encryption, it uses blockchain technology to store wallets and passwords in a secure database. Limited Coinbase employees are the only users who can access these blockchains, and they must undergo a rigorous background check to keep people’s wallets secure.
- DL Freight – DL Freight is a prime example of how blockchain technology is revolutionizing the logistics industry. It operates on a private, permissioned blockchain network based on Hyperledger Fabric, ensuring security and privacy for participating organizations. In this blockchain, automated and tamper-proof smart contracts handle key aspects of the freight process, including generating invoices, verifying data, and triggering payments.
Challenges of blockchain security

Despite its impressive security features, blockchain technology is not unhackable. It faces several technological challenges that could provide entry points for hackers and cyber threats.
Here are some of the major challenges of blockchain security:
- Quantum Computing - The emergence of quantum computers could potentially break the cryptography used in blockchain, jeopardizing the security of the entire system. Research on quantum-resistant cryptography is ongoing, but vulnerabilities remain.
- Smart Contract Security - Bugs and vulnerabilities in smart contracts can be exploited by hackers, leading to financial losses and potential manipulation of the network. Rigorous auditing and secure coding practices are crucial to mitigate these risks.
- Forkability - Some blockchains are susceptible to hard forks, where the chain splits into two separate versions due to disagreements or technical issues. This can create uncertainty and confusion for users, and potentially weaken the security of the network.
- Private Key Management - Losing or having your private key stolen can permanently lock you out of your funds or assets stored on the blockchain. Secure storage and backup solutions are essential, but user error remains a risk.
- Social Engineering - Phishing scams and other social engineering tactics can trick users into revealing their private keys or falling victim to other fraudulent activities. User education and awareness are crucial to combat these threats.
Despite these challenges, significant efforts are being made to address them and enhance blockchain security. Continuous research and development, paired with best practices in coding, user education, and regulations, are crucial to ensure the secure future of blockchain technology.







Comments ( 1 )
David Argent
05/01/2024