Think your firewalls are protecting your business? Think again. While traditional cyber threats aim for your networks, a new, insidious adversary is already inside your perimeter: your mind.
Cognitive hacking is a growing cyber threat that has to be on your radar. This sophisticated cyber attack uses digital tools to influence human perspective and behaviours, rather than directly targeting computer systems.
We’ve got you covered with this comprehensive guide to cognitive hacking, how the cyber threat is being superpowered by agentic AI and how it’s different to social engineering scams.

What is Cognitive Hacking?
Cognitive hacking is a form of cyber attack. You might expect that this means it directly targets computers or networks. But this attack prioritises manipulating human behaviour, perception and decision making processes.
Whilst cognitive hacking uses digital tools, the goal is to influence human minds. Cognitive hackers exploit cognitive biases, psychological vulnerabilities, and existing prejudices.
This can be done by deliberately spreading false information through the creation of fake news articles and deepfake images or videos.
Cognitive hacking also impacts what you might be seeing on your social feeds. By using fake accounts, bot networks, and engagement farming to amplify specific messages a false sense of consensus is created.
Recommendation algorithms on platforms like Facebook, YouTube, TikTok are designed to keep users engaged by showing them content they are likely to interact with. Attackers will exploit these systems to amplify specific push biased content, or even radicalize users.
Search engine and algorithm manipulation are a critical component of cognitive hacking. This directly impacts what information people see. Search result pages are one of the primary information sources for billions of users. Subtle changes can significantly shape public perceptions and influence behavior.
Tactics for algorithm manipulation include Black Hat SEO methods such as:
- Keyword stuffing
- Cloaking
- Spammy backlinks
- Content scraping or spinning
- The use of hidden text or links to deceptively influence search rankings.
Cognitive hacking is done for a variety of reasons. Reputational damage is perhaps the most critical concern for AI leaders.
A company's reputation is an intangible asset that directly impacts its financial health, investor confidence, and ability to attract talent. Cognitive hacking understands this and aims to systematically dismantle it.
For IT leaders, cognitive hacking represents a unique challenge. Traditional cybersecurity defenses focused on network perimeters and data integrity offer limited protection against attacks that manipulate public perception and psychological vulnerabilities.
While a system can be restored after a technical attack, a damaged reputation can linger for years, making recovery much more challenging and costly.
Effectively combating cognitive hacking requires a shift towards 'cognitive security,' demanding collaboration across IT, PR and legal teams.
Cognitive hacking and AI
The rapidly growing prevalence of AI has dramatically amplified the scale and impact of cognitive hacking.
Generative AI, including image and video generators can create massive amounts of highly convincing and contextually relevant fake news articles, social media posts, comments, reviews.
This allows cognitive hackers to flood the information ecosystem, making it incredibly difficult for individuals to be able tell what is true.
Agentic, autonomous AI are able to carry out adaptable disinformation campaigns with very limited human oversight. Through fake accounts they can interact with real users, spread narratives, and adapt their behavior based on real-time feedback.
Unlike static, human-managed campaigns, agentic AI systems can monitor real-time user reactions, engagement metrics, and counter-narratives. They can then dynamically adapt their messaging, tone, and distribution strategies to maximize influence and avoid detection.
Agentic AI can also hyper-personalize disinformation. This means it can craft messages that specifically target individual cognitive biases and interests. Cognitive hackers can manage entire networks of interconnected fake accounts, each with a consistent backstory, posting history, and personality.

From Tools to AI Agents
Map the seven-stage evolution from reactive systems to superintelligence and align enterprise strategy to each step of agentic maturity.
They can even learn to evade detection mechanisms by changing their posting patterns, using different language styles, or mimicking human-like errors. This makes the manipulation far more effective and harder to identify as malicious.
Cognitive hacking enhanced by the power of agentic, autonomous AI feeds into the ‘dead internet theory, the idea that the content on the internet is mostly machine-generated or automated by artificial means.
Cognitive Hacking vs Social Engineering
Cognitive hacking is similar to social engineering scams you may have heard of. However, cognitive hacking typically operates on a much broader and often more strategic level.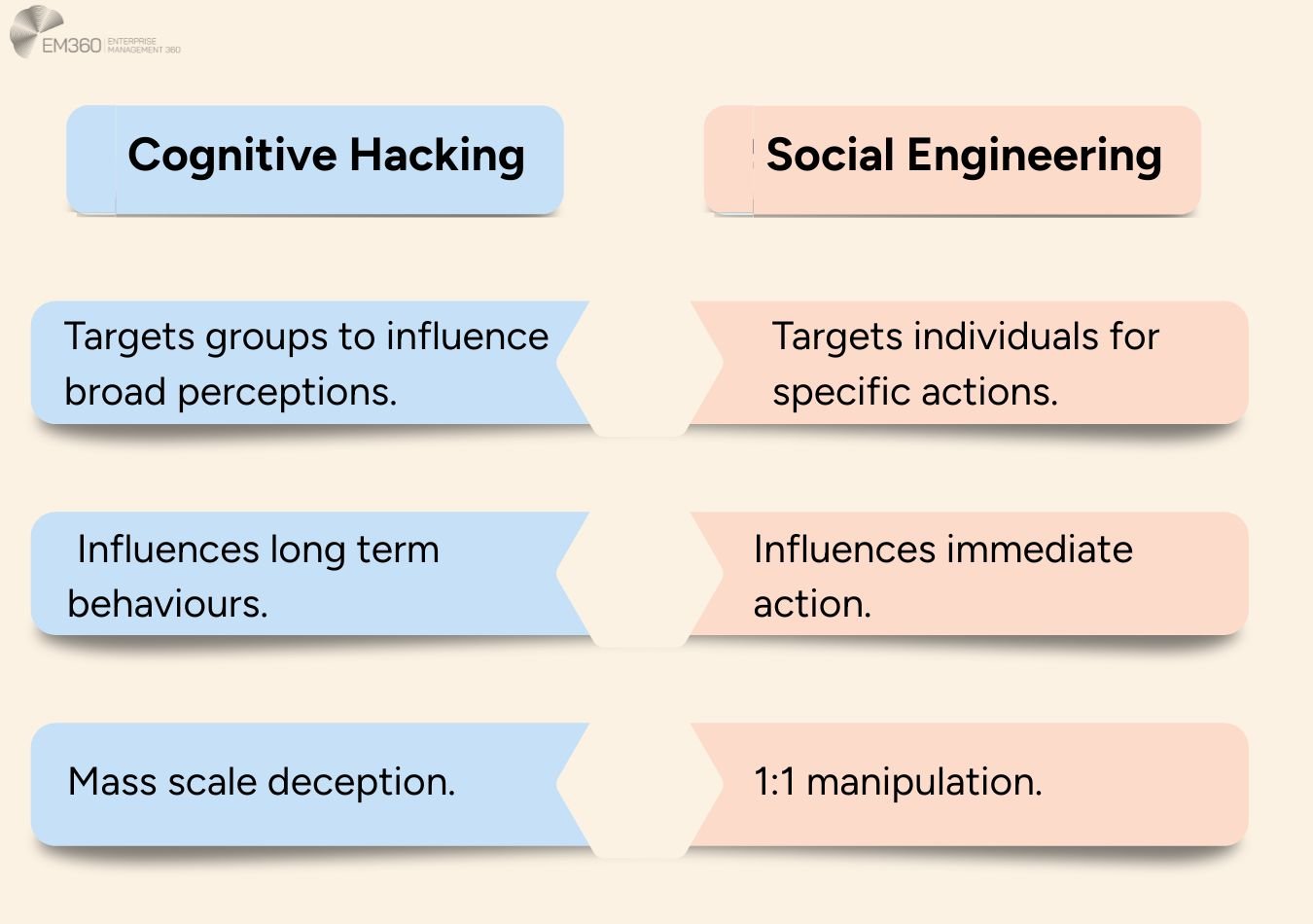
Social engineering attempts to trick an individual into performing a specific action like clicking a malicious link or revealing passwords through techniques like phishing, vishing and smishing.
Cognitive hacking instead aims to influence groups of people over time. It does this in order to influence public opinion with the goal of manipulating behaviour in the long term.
The rise of cognitive hacking, particularly with the acceleration brought by agentic AI, erodes trust in institutions and companies.
As AI continues to evolve, the challenge of distinguishing between genuine humans online and AI-driven manipulation will only intensify, making digital literacy and a collective commitment to verifying information more critical than ever.
For IT and security leaders, this means proactively integrating digital literacy training, implementing advanced content verification tools, and fostering cross-team strategies to build an organisation-wide defense against cognitive threats.







Comments ( 0 )