Large organizations often juggle dozens of cloud services and DevOps tools across AWS, Azure, on-premises data centres and more – all while trying to enforce security standards and meet tight delivery deadlines. If you’re an infrastructure lead drowning in complexity, you’re not alone.
Ticket queues pile up. Platform teams burn out. Developers wait.
Enterprises today are regaining control and speed by standardising on Internal Developer Platforms (IDPs). An IDP is a central self-service layer that connects tooling and infrastructure so teams can build and ship without friction.
The best platforms pave golden paths that make approved patterns the default, with checks automated behind the scenes rather than enforced by tickets.

The result is compliance by design, fewer bottlenecks and delivery that scales with the business.
What Is an Internal Developer Platform?
An Internal Developer Platform (IDP) is the engine that powers developer self-service in the enterprise. Built by the platform engineering team, it unifies cloud infrastructure, CI/CD, databases, Kubernetes and observability into one governed system.
Developers get on-demand environments, standardised deployments and shared services without tickets or tool-specific know-how. The platform creates golden paths that lower cognitive load and make delivery repeatable at scale. It’s important to distinguish an internal developer platform from an internal developer portal though.
The platform is the automation and orchestration layer that enforces standards. The portal is the interface (web UI, CLI or API) that developers use to request and discover. Most IDPs pair a platform with a developer portal or service catalogue, but the real value sits in the platform’s automation.
A strong IDP does not lock teams into one rigid route. It abstracts repetitive infrastructure while keeping sensible escape hatches. Approved templates and automation make compliant defaults the easiest choice, yet teams can tune configurations for edge cases. That balance reduces rework, curbs shadow IT and keeps delivery fast, safe and scalable.
Why Enterprises Need an IDP
For large organisations, an IDP is moving from optional to essential. Here are the core challenges and how an IDP solves them through enablement and golden paths.
Managing multi-cloud complexity
Running across AWS, Azure, GCP and on-prem introduces inconsistent provisioning, configs and toolchains. An IDP unifies these into a single experience, abstracting cloud specifics and standardising workflows. Developers deploy without wrestling with each platform. Platform teams encode best practices once, then update centrally as clouds evolve, turning a messy estate into a coherent, governed environment.
Scaling developer productivity
Productivity stalls when teams wait on tickets or rebuild the same pipelines. An IDP provides self-service environments, preapproved templates and automated pipelines. New hires get what they need fast. Without an IDP, equipping a developer can take weeks; with a well-set-up IDP, that drops to days or hours. Boilerplate disappears, cognitive load falls and throughput rises across the organisation.
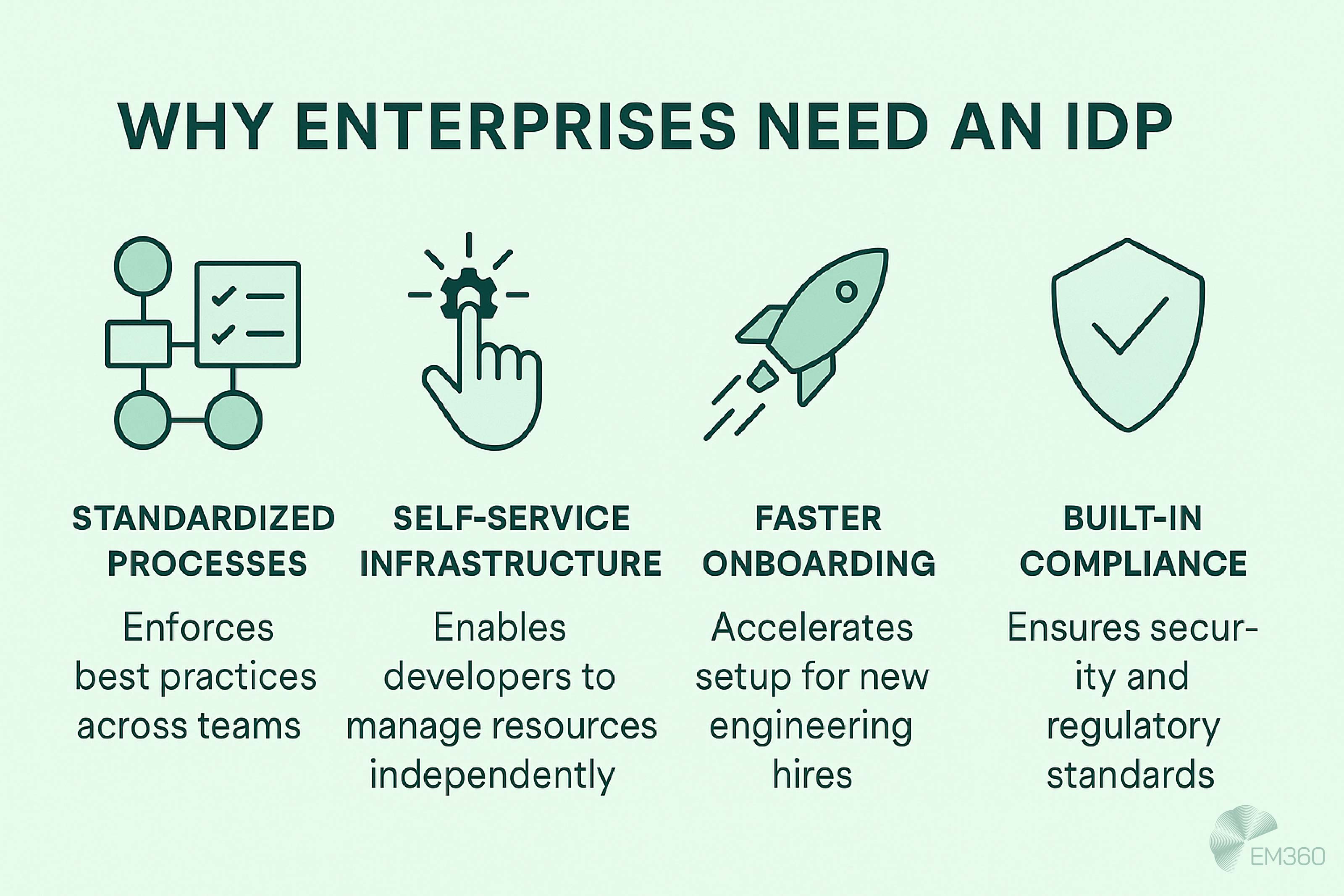
Enforcing compliance without bottlenecks
Manual reviews and change boards slow delivery. An IDP bakes security and compliance into templates and policies so every deployment inherits approved libraries, images and controls by default. Teams move quickly on paved, compliant paths while platform engineers adjust guardrails centrally and have them propagate everywhere. Compliance becomes an enabler, not a queue.
Reducing governance overhead
As services multiply, ownership, standards and audit evidence get hard to track. An IDP’s service catalogue and scorecards provide a single source of truth for what exists, who owns it and whether it meets policy. Automated reporting logs deployments, ties changes to tickets and tags resources for cost and accountability. Governance shifts to managing exceptions instead of chasing data.
Accelerating delivery at enterprise scale
From Audits to Continuous Trust
Shift compliance from annual snapshots to embedded, automated controls that keep hybrid estates aligned with fast-moving global regulations.

Self-service, automation and standardisation compress lead times and increase deployment frequency. The direction of travel is clear: by 2026, 80% of large software engineering organisations will have platform teams offering reusable services via internal platforms. Golden paths lift velocity without trading away stability, so enterprises can move fast and stay safe.
Top 10 Enterprise-Ready Internal Developer Platforms in 2025
When evaluating IDP solutions, enterprises should look for platforms that can meet their scale, integrate with complex toolchains, and provide robust security and support. Here are 10 leading internal developer platform solutions in 2025, each with a summary of what they offer, their pros and cons, and where they fit best.
AWS Proton
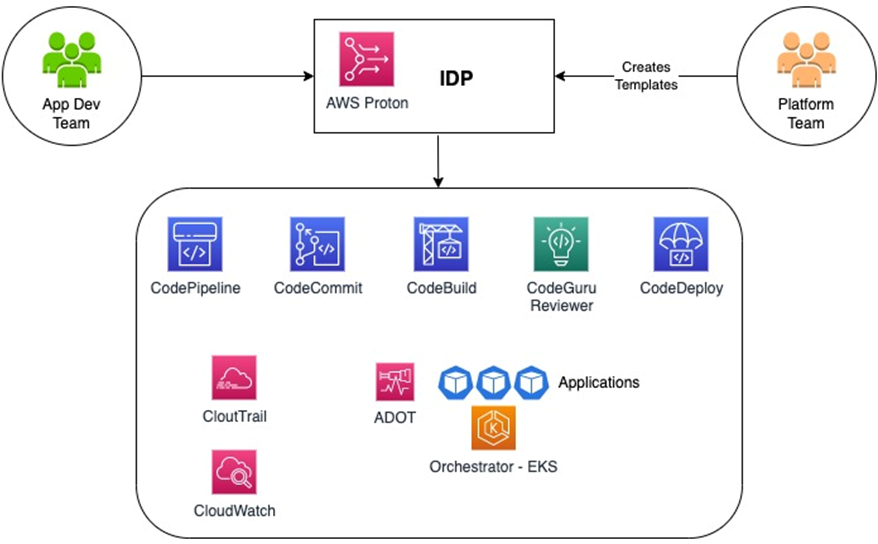
AWS Proton is Amazon’s managed internal developer platform for containerised and serverless apps on AWS. Platform teams define versioned templates. Developers deploy through self-service with consistent guardrails.
Enterprise-ready features
Proton bakes in IAM, VPC, KMS and tagging so every template meets policy. It supports CloudFormation, Terraform and CDK to codify best-practice architectures at scale. Recent additions include -based workflows and multi-account support. A console and CLI give central visibility across a large AWS estate.
Pros
- Fully managed; no platform to run.
- Deep integration with AWS security, observability and CI/CD.
- Standardises containers and serverless across teams.
- Governance by design via versioned templates and policies.
- Frequent AWS enhancements without upgrade overhead.
Cons
- AWS-only; no native multi-cloud or on-prem coverage.
- Template abstractions can limit complex edge cases.
- Learning curve to model existing IaC as Proton templates.
- Constrained to AWS-approved technologies.
- No on-prem option for strict residency needs.
Best for
Enterprises committed to AWS that want clean self-service without operating an IDP. Strong fit for teams on ECS, EKS, Fargate or Lambda in sectors like finance and biotech. If you need cloud-agnostic coverage, Proton only addresses the AWS footprint.
Cortex
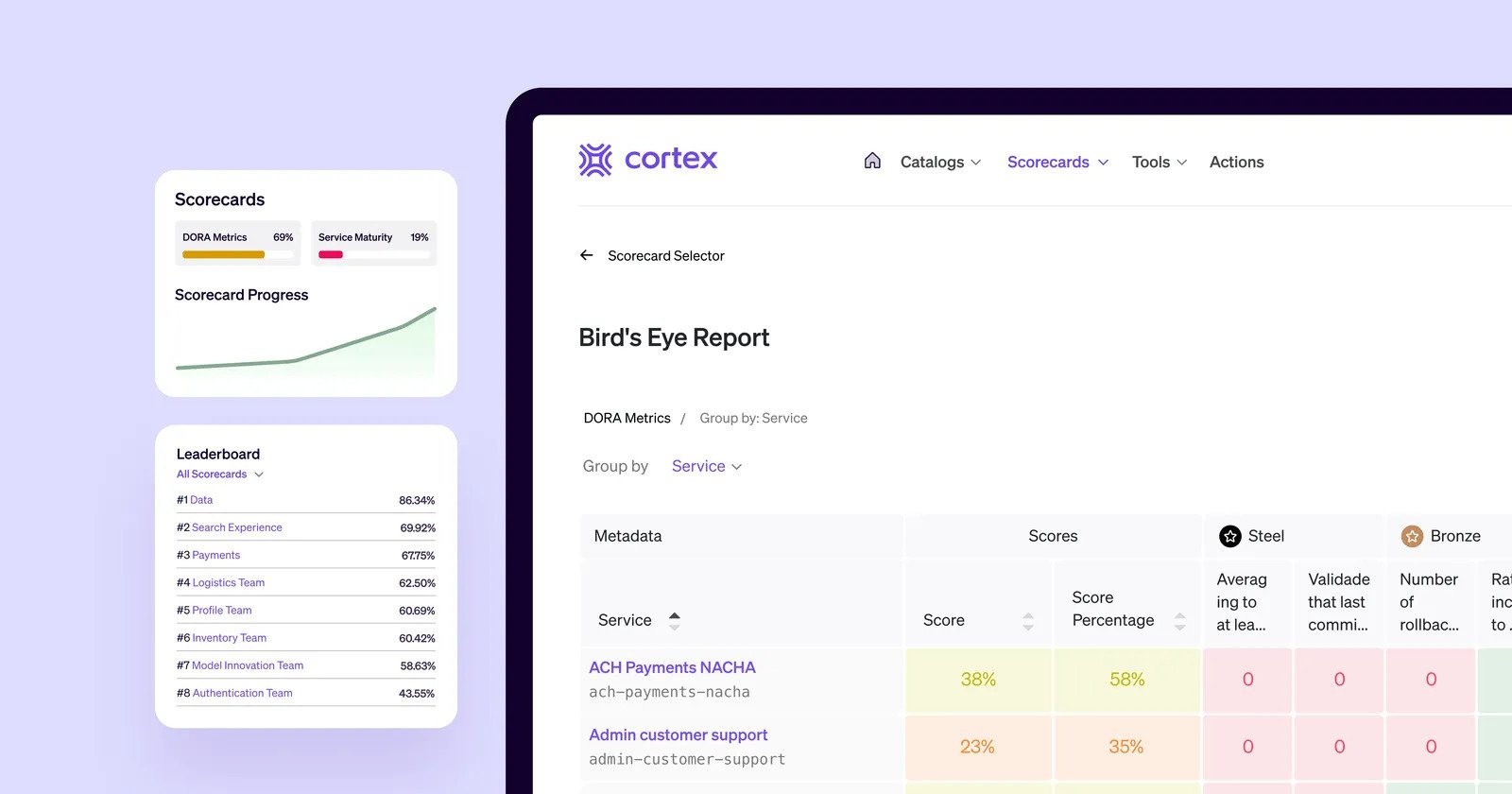
Cortex is an enterprise developer portal for microservices. It provides a central service catalogue, ownership and dependency mapping, plus scorecards to drive reliability and standards.
Enterprise-ready features
Inside the CI/CD Control Plane
How ephemeral runners, policy engines and signed artifacts harden software delivery without stalling developers.
Cortex integrates with , CI/CD, incident management and APM to auto-populate service data. Scorecards turn best practices into automated checks and metrics. APIs and webhooks let you gate deployments on standards. RBAC and SSO meet enterprise security needs. Cortex does not provision infrastructure; it excels at visibility and governance, often paired with an orchestrator.
Pros
- Rich catalogue with ownership, dependencies and metadata.
- Custom scorecards for security, SLOs and architecture hygiene.
- Broad integrations across repos, pipelines, incidents and APM.
- Enterprise controls: SSO, access policies, audit logs; on-prem option.
- Proven with growing teams and large service estates.
Cons
- Pricing can be high for smaller organisations.
- Portal focus; no native infra automation.
- Setup effort to wire integrations and maintain data quality.
- Overkill for simple or low-service-count environments.
- Younger product; some features still maturing.
Best for
Mid-to-large enterprises in tech, fintech and regulated sectors that need strong ownership, standards and service health at scale. A good fit if spreadsheets or homegrown registries are breaking down, and you already run CI/CD and deployment automation.
DuploCloud
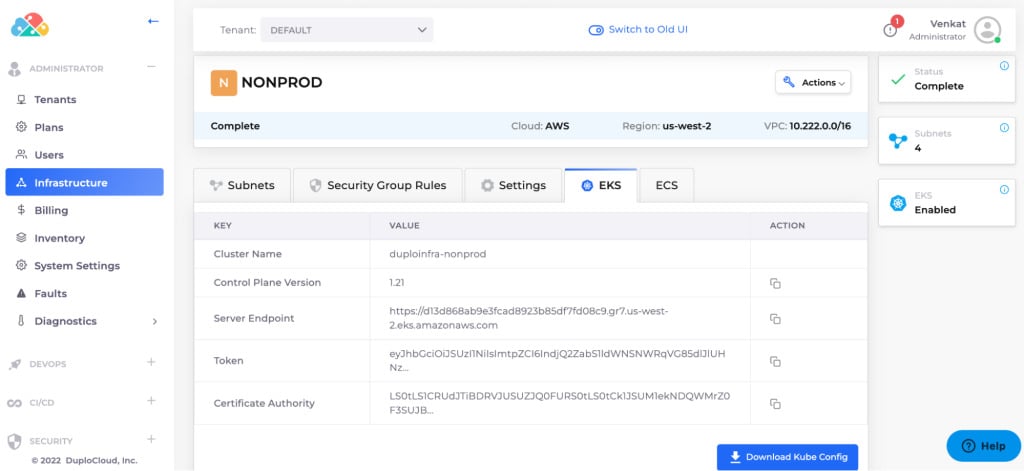
DuploCloud is a no-code/low-code DevOps automation platform that functions as an internal developer platform. It delivers provisioning, CI/CD, monitoring and security/compliance automation out of the box.
Enterprise-ready features
Supports AWS, Azure and GCP with low-code definitions via UI or JSON/YAML. Automates compute, networking, users, secrets and policies. Built-in frameworks map to SOC 2, PCI and HIPAA with controls for encryption, logging and access. Dashboards surface compliance status and reports. Integrated DevSecOps covers vulnerability scanning, threat detection and real-time monitoring. Runs in your cloud for data control while managed through DuploCloud’s interface.
Pros
- End-to-end automation across infra, pipelines, monitoring and security.
- Strong compliance posture with continuous checks.
- Low-code boosts speed and reduces specialist bottlenecks.
- Consistent multi-cloud workflows.
- Smaller platform teams can support larger estates.
Cons
- Opinionated abstractions can clash with bespoke setups.
- Vendor lock-in concerns despite multi-cloud support.
- Pricing can be significant versus DIY with open source.
- Limited fine-tuning for ultra-scale edge cases.
- Breadth introduces a learning curve for platform teams.
Best for

Machine Identity Risk in Cloud
Secrets sprawl, over-permissioned service accounts and orphaned tokens are reshaping breach scenarios for cloud-native enterprises.
Enterprises that need a compliant, full-stack cloud platform on day one, especially in regulated industries. Useful for organisations with constrained DevOps capacity that prioritise speed to value and security without building an IDP from scratch.
Humanitec
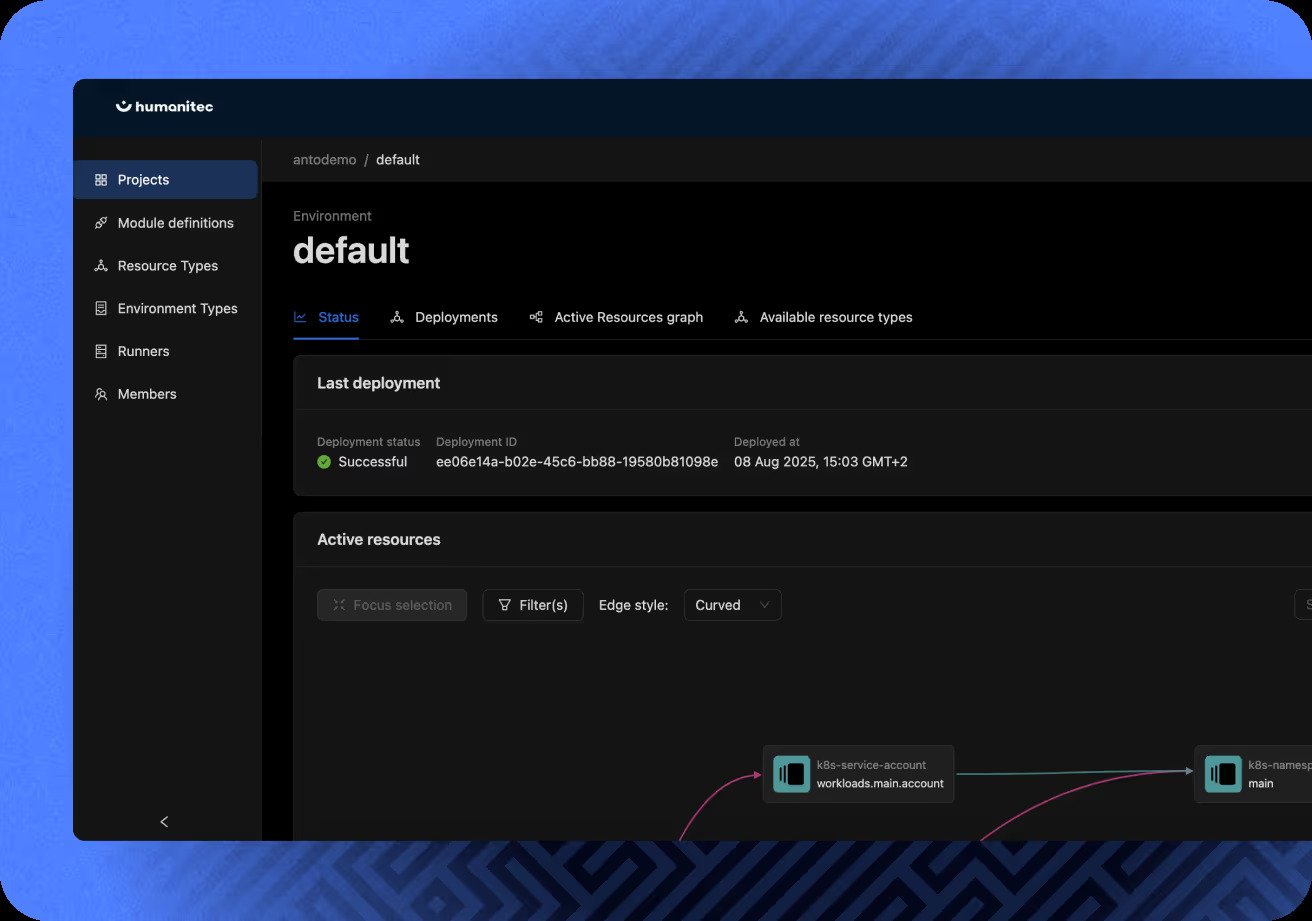
Humanitec provides a Platform Orchestrator, the engine that provisions and manages infrastructure for applications. It is not a portal. It connects to your clouds, Kubernetes and CI/CD to automate environment creation, configuration and deployments. Teams often pair it with Backstage or a similar UI.
Enterprise-ready features
Developers declare what an app needs, the orchestrator allocates the right resources through cloud APIs, Kubernetes or Terraform. Access it via CLI, REST API or GUI. Enterprises get fine-grained RBAC and policy controls, for example spend limits or naming rules. Integrations cover CI/CD, secrets and ITSM. Kubernetes is first class: Humanitec manages manifests, handles environment-specific differences and tracks drift. Audit logs and lifecycle tools support preview environments and safe teardown. Automation is the default, control stays with the platform team.
Pros
- Strong orchestration that removes manual DevOps work.
- Cloud-agnostic, suitable for hybrid environments.
- Self-service via UI, CLI or API.
- Reduces cognitive load, no need to learn Terraform or Kubernetes internals.
- Policy, auditing and identity integrations for enterprise governance.
Cons
- Not a full portal or catalogue, usually paired with one.
- Set-up requires deep understanding of your toolchain.
- Cost can rise with scale and usage.
- Edge legacy resources may need custom connectors.
- Cultural shift required as teams trust more automation.
Best for
Enterprises treating the platform as a product, especially those running Kubernetes at scale. Suits organisations replacing scripts with a flexible, cloud-agnostic core that powers their golden paths and plugs into existing tools.
OpsLevel
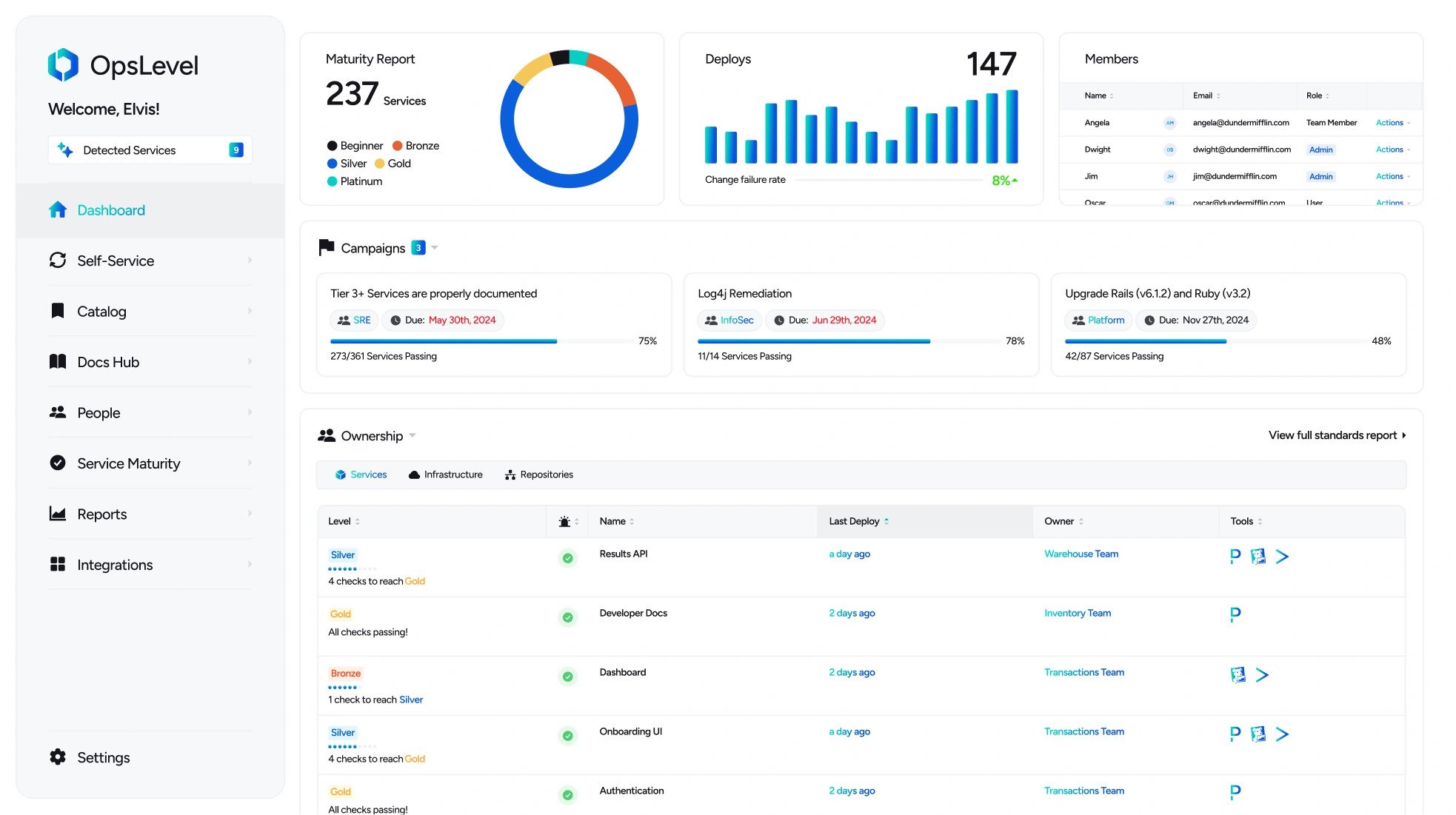
OpsLevel is a SaaS developer portal for microservices. It centralises a service catalogue, ownership and dependencies, and uses scorecards to raise reliability and standards. It also offers developer self-service actions.
Enterprise-ready features
Supply Chains Rewrite Security
How SBOMs, SLSA and Sigstore shift software security from patch-and-pray to verifiable trust in third-party code at enterprise scale.

OpsLevel discovers services from repos, registries and Kubernetes, then keeps metadata fresh. Scorecards enforce checks, with heatmaps to show compliance across teams. Self-service tasks trigger Terraform, Jenkins or custom automations with approvals and tracking. It integrates with on-call and incident systems for an operational view, and adds an AI assistant to help with documentation. SSO, access controls and scale to thousands of services support enterprise roll-outs.
Pros
- Unified catalogue and health dashboards reduce microservice sprawl.
- Custom scorecards for security, SLOs and engineering hygiene.
- Self-service actions cut tickets and toil.
- Broad integrations across code, pipelines, incidents and observability.
- Fast to adopt as SaaS, low maintenance for platform teams.
Cons
- SaaS may raise data residency concerns in regulated sectors.
- Not an infra provisioning tool, relies on your automations.
- User-based pricing can add up at large scale.
- Newer AI features may need time to mature.
- Migration effort if you already run a customised Backstage.
Best for
Growing engineering organisations with many services that need clear ownership, standards and operational visibility. A fit for teams pursuing SRE and DevOps maturity who want a commercial portal rather than maintaining open source.
Port
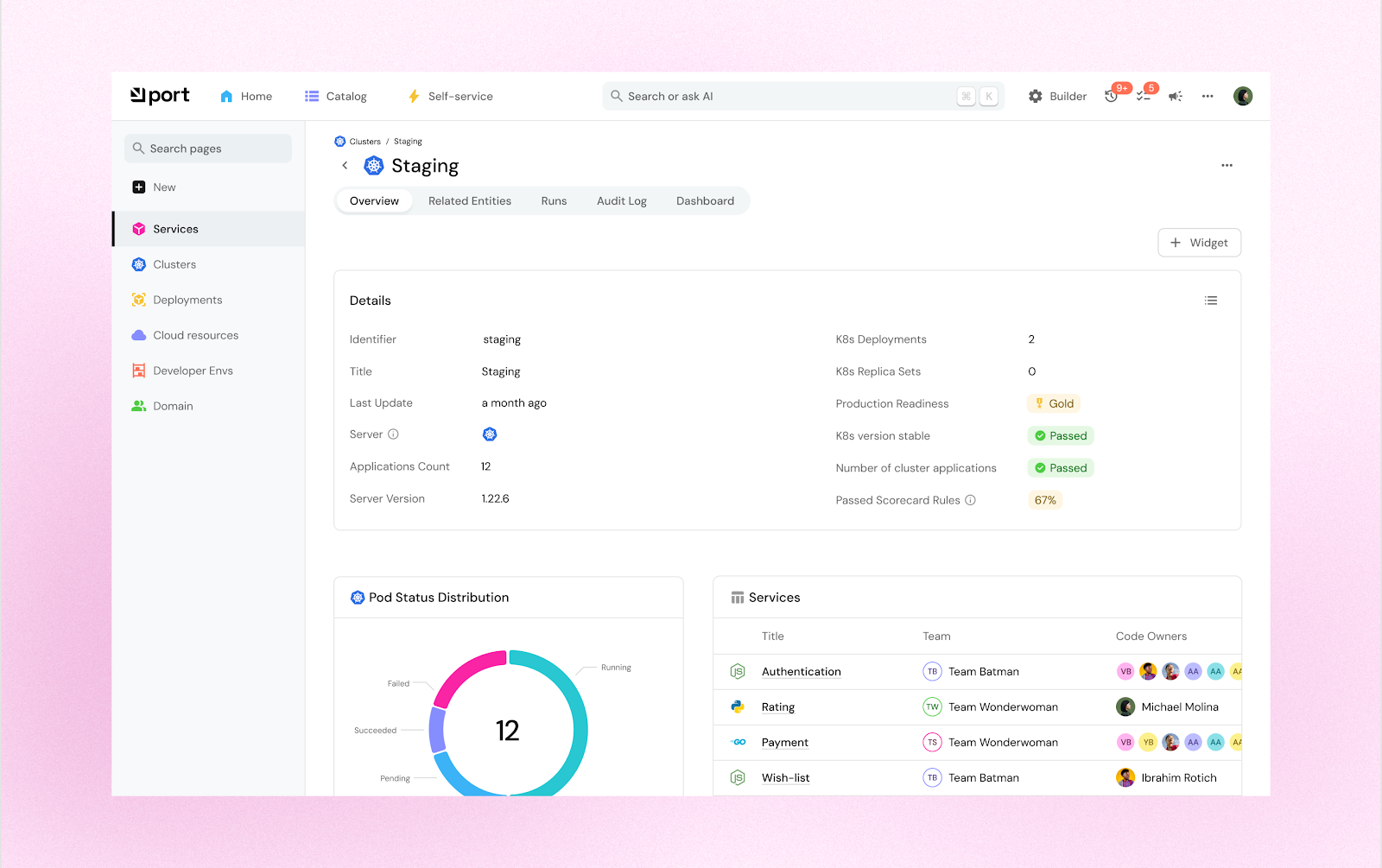
Port is a modern developer portal focused on no-code customisation and strong developer UX. It offers a composable software catalogue and self-service actions so developers can interact with infrastructure safely.
Enterprise-ready features
Port’s Blueprints let you model any component, from microservices to cloud resources, with the fields that matter to your business. A no-code editor shapes the UI and workflows. Event-driven automations invoke webhooks or pipelines, enabling one-click requests such as new environments. Scorecards surface health and compliance. SSO, RBAC and managed or on-prem deployment options meet security needs. A free tier and sandbox support rapid prototyping.
Pros
- Flexible data model tailored to your organisation.
- No-code and low-code configuration speeds iteration.
- Self-service automations enable golden paths with minimal coding.
- Quick time to value.
- Clean, developer-friendly interface drives adoption.
Cons
- Pricing can be high at enterprise scale.
- No-code patterns can limit very complex logic.
- Smaller ecosystem than long-standing open-source portals.
- Rework likely if migrating from a heavily customised Backstage.
- Potential data lock-in, plan for export and longevity.
Best for
Enterprises and mid-sized companies that want a tailored portal quickly, prioritising developer experience and maintainability. Strong option for teams replacing Backstage upkeep, or fast-growing firms that need a configurable portal aligned to their processes.
Qovery
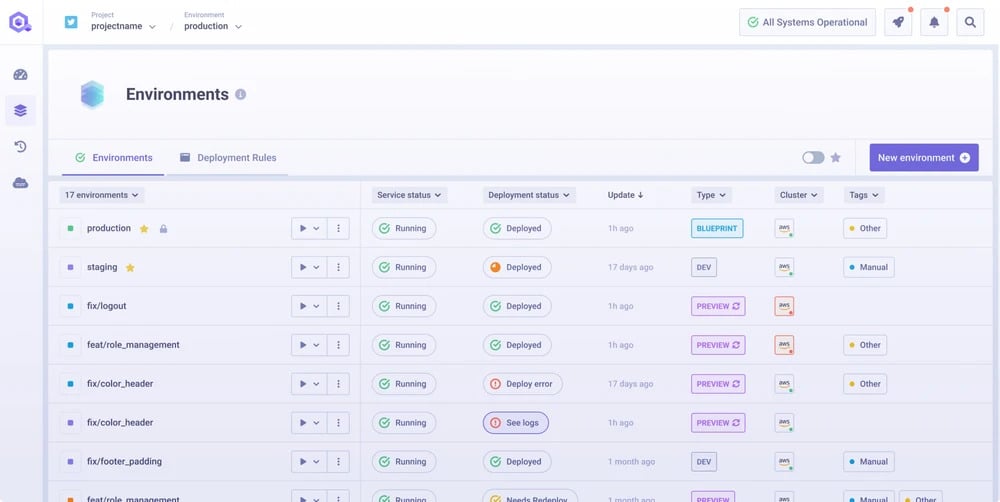
Qovery is a developer-first internal platform that automates application and database deployment to your cloud. Think Heroku experience on AWS, Azure or GCP. It abstracts Kubernetes, networking and infra so teams ship quickly via UI, CLI or .
Enterprise-ready features
Runs across multi-cloud and on-prem Kubernetes. Standout environment management creates full-stack preview environments per branch or PR, including database clones, speeding QA and experimentation. Handles autoscaling, rollbacks and CI triggers on push. Enterprise controls include RBAC, audit logs and VPC isolation, with built-in monitoring and basic cost insights. Qovery generates the required infra from high-level inputs, enabling self-service in your own cloud accounts.
Pros
- Fast, low-friction app and DB deployments.
- Multi-cloud and on-prem K8s support.
- One-click preview and environment cloning.
- Hides K8s complexity, reducing DevOps load.
- UI and API fit dev and platform workflows.
Cons
- Kubernetes under the hood limits very legacy workloads.
- Less direct control for ops in highly custom setups.
- Advanced networking integrations require validation.
- Additional platform cost on top of cloud spend.
- Overlaps with mature in-house K8s platforms.
Best for
Cloud-forward enterprises and product teams wanting a PaaS-like experience in their own accounts. Strong for fintech and SaaS scale-ups seeking rapid environments, -parity testing and reduced toil, while central teams retain governance.
Rafay Systems
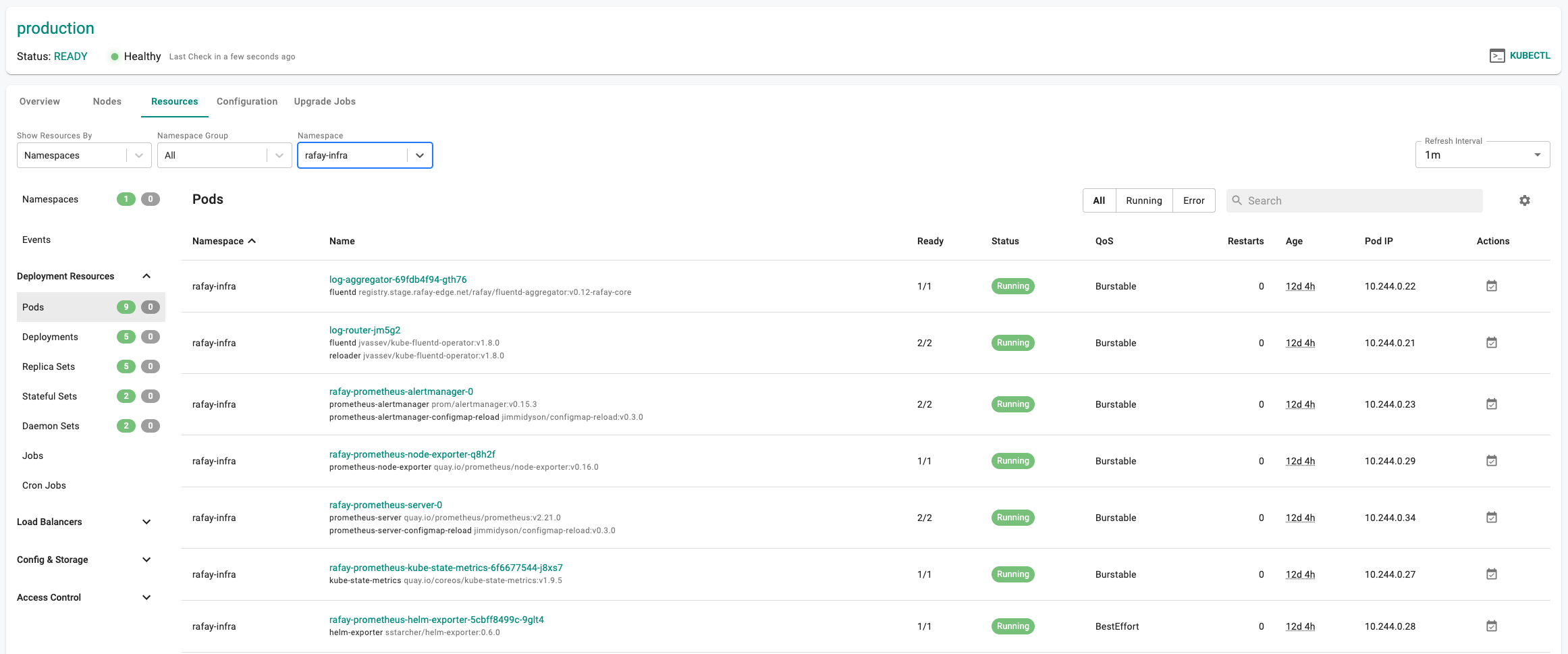
Rafay Systems is a Kubernetes Operations Platform that provides a central control plane for multi-cluster, multi-cloud estates. It automates cluster provisioning, security and lifecycle, forming a strong backbone for container-centric IDPs.
Enterprise-ready features
Global policy engine enforces security and network rules consistently across EKS, AKS, GKE and on-prem, covering admission controls, namespaces and guardrails. Cluster blueprints standardise add-ons like monitoring or service mesh. Supports SSO, multi-tenancy and RBAC, plus integrations with CI/CD, ITSM and observability. Zero-trust design secures control-plane interactions. Optimised for remote and edge clusters with low-bandwidth management and safe upgrades.
Pros
- Robust multi-cluster automation and upgrades.
- Strong policy, audit and compliance features.
- Enterprise identity and tooling integrations.
- Developer self-service within controlled boundaries.
- SaaS or self-hosted control plane options.
Cons
- Ops-first product; pair with a portal for dev UX
- Feature depth brings a learning curve.
- Overkill for small or single-cluster estates.
- Commercial cost versus DIY expertise.
- Highly bespoke, air-gapped networks may need services.
Best for
Enterprises standardising on Kubernetes at scale, including telco, IoT and regulated sectors. Ideal when you need consistent governance across dozens or hundreds of clusters while enabling safe, self-service deployments.
Red Hat Developer Hub
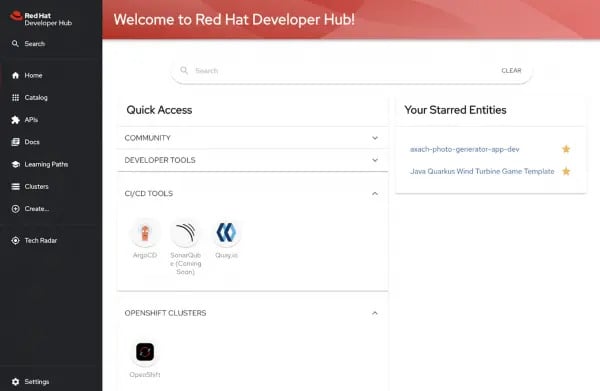
Red Hat Developer Hub is a supported, enterprise build of Backstage, tailored for OpenShift and Kubernetes organisations. It delivers a hardened developer portal with a curated plugin set and vendor backing.
Enterprise-ready features
Core software catalogue and templates for consistent scaffolding, plus a self-service provisioning dashboard integrated with OpenShift pipelines. Dynamic plugin management simplifies updates without rebuilds. Pre-built integrations cover CI/CD, issues and monitoring. Enterprise security with RBAC and SSO (e.g. Keycloak). Deep OpenShift API integration enables direct deploys and resource management, with Red Hat support and roadmap.
Pros
- Backstage benefits with enterprise hardening and support.
- RBAC and SSO aligned to corporate identity.
- Tight OpenShift/Kubernetes integration for faster delivery.
- Vendor roadmap and stability reduce maintenance risk.
- Golden-path templates and tested plugins out of the box.
Cons
- Best value in Red Hat/OpenShift environments.
- Newer product layer; assess maturity in your context.
- Subscription cost versus DIY Backstage.
- Still requires implementation effort and data ingestion.
- Less relevant if you are not Kubernetes-centric.
Best for
Large organisations already invested in Red Hat and OpenShift that want a supported portal to improve onboarding, consistency and DX, with minimal risk and a clear upgrade path.
Spectro Cloud Palette
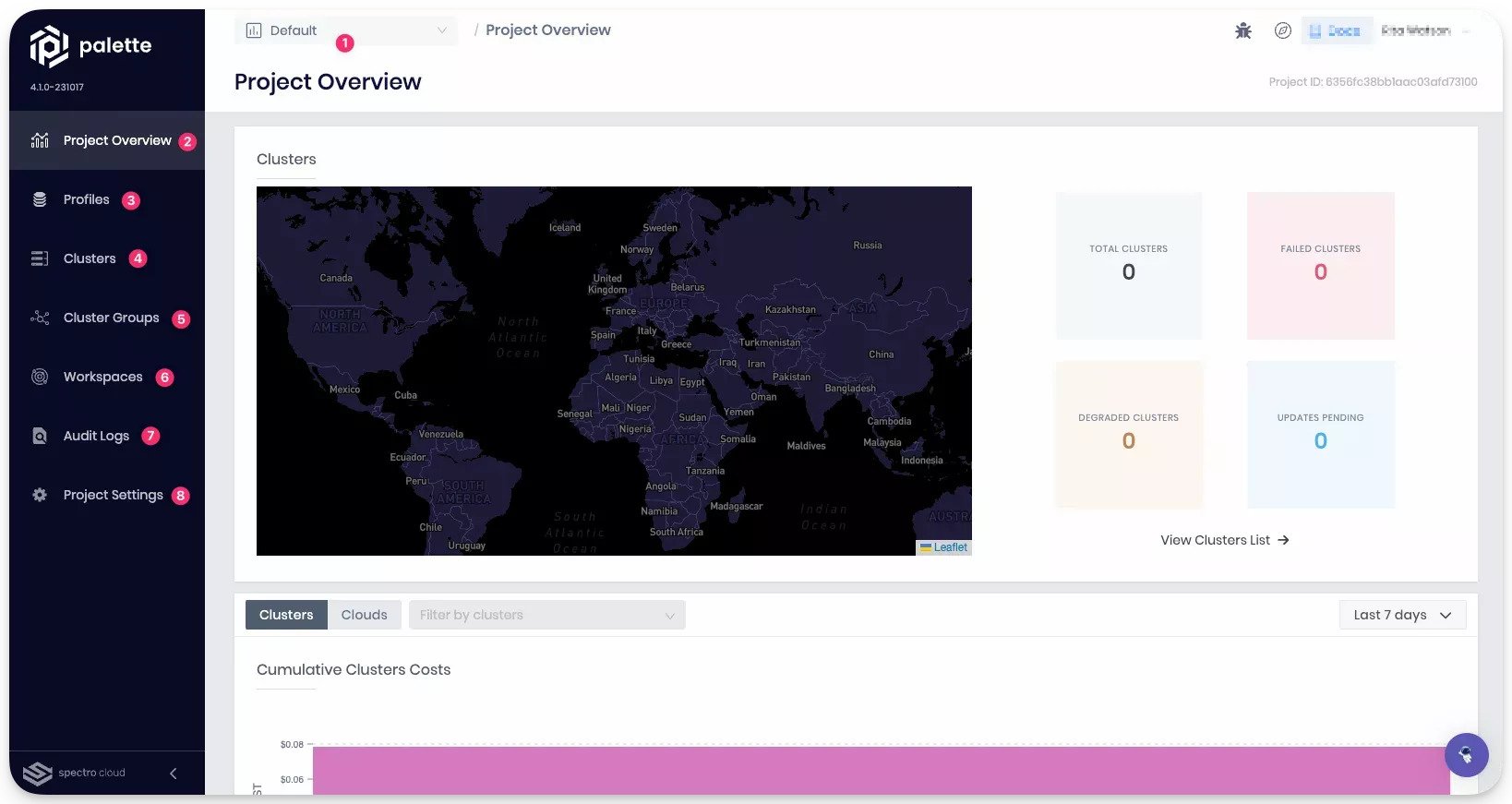
Spectro Cloud Palette is an enterprise Kubernetes platform for deploying and managing clusters and their full stacks declaratively. It balances ops control with developer self-service and is strong in edge and on-prem use cases.
Enterprise-ready features
Cluster Profiles define OS, K8s version and add-ons (CNI, CSI, ingress) to stamp out consistent clusters across clouds, VMware, bare metal and edge. Self-service and tenant isolation let teams request namespaces or clusters within approved profiles, creating golden paths. Palette Dev Engine layers developer tooling on top. Policy enforcement covers registries and mandatory agents, with SSO/RBAC, cost insights and drift management. Handles upgrades at scale with minimal disruption.
Pros
- Declarative stack management reduces drift and errors.
- Hybrid and edge support across diverse substrates.
- Strong governance and isolation patterns.
- Integrates with CI/CD, ITSM and monitoring.
- Cuts Kubernetes ops overhead at scale.
Cons
- Ops-led by default; often paired with a portal for DX.
- Requires K8s-savvy platform teams to design profiles.
- No built-in CI/CD or release tooling.
- Limited payoff for simple, few-cluster estates.
- Enterprise licensing requires clear value realisation.
Best for
Enterprises running Kubernetes across cloud, on-prem and edge that need standardisation and policy at scale while offering reliable self-service to development teams.
Build vs Buy: Which Approach Works for Enterprises?
Enterprises weighing an Internal Developer Platform face a strategic choice: build in-house or buy. The right call depends on maturity and needs, but the goal is the same — enable golden paths at scale rather than enforce golden rules.
Governance and security
Building gives precise control over policies, tools and checks. The risk is hard-coding mandates that block deployments or restrict technology, which drives workarounds and weakens security. Bought platforms bring proven guardrails from many environments, automate tagging and scans, and arrive with audits and certifications such as SOC 2 and ISO 27001. You may not get every internal policy on day one, but strong vendors allow extensions. Most enterprises find a good product covers 80–90% of needs and is configurable for the rest, turning governance into enablement.
Risk and resilience
Homegrown platforms concentrate risk in people and knowledge. If key engineers leave, the platform stalls. Integration gaps, performance issues and security defects are your burden, as are high availability and backup design. Buying shifts much of this risk to a vendor with SLAs, support and a battle-tested codebase. Vendor risk remains, so select an established provider or an open-source core with a strong community. Continuous updates help you stay resilient as the stack evolves.
Total cost of ownership
Open source can make building look cheaper, but a team of 5–10 platform engineers for a year or more is a high six to seven figure investment, plus ongoing maintenance, infrastructure and support. Opportunity cost is real. Buying has a clear price, often comparable to 1–2 full-time engineers annually, and reduces internal support load. You gain predictability and can redeploy talent to customer-facing work. Heavy customisation can tilt the maths, so model both paths carefully.
Scalability and flexibility
Building offers ultimate flexibility, yet many internal platforms become a “golden cage” that is hard to evolve or scale to hundreds or thousands of developers. Knowledge does not travel, and there is no external ecosystem to lean on. Vendor platforms are designed for scale — multi-tenant, high-concurrency, thousands of services — and expose plugins, APIs and webhooks for custom needs. They also nudge teams toward standard patterns that scale organisationally.
Time to value
Building is a long game. Enterprises routinely spend 12–18 months to reach an MVP, during which developer pain persists and requirements shift. Buying compresses the timeline to weeks, sometimes days for SaaS, with incremental wins such as a service catalogue and self-service arriving early. Implementation still takes work, but far less than writing the platform. If speed matters, buying typically wins on time to value by a wide margin.
Key Considerations for Choosing an Enterprise IDP
Choosing the right Internal Developer Platform is less about feature checklists and more about whether the platform will scale with your business. Here are the factors that matter most for enterprise leaders:
Integration with your stack: An IDP should connect cleanly into your existing estate — clouds, CI/CD, repos, ticketing, observability — without demanding a rebuild. Open APIs and strong connectors are non-negotiable.
Scale across hybrid and multi-cloud: Enterprises rarely operate in one environment. The platform must manage thousands of users and services consistently across AWS, Azure, GCP, on-prem and edge.
Compliance and security by design: Policy as code, RBAC, audit logs and integration with compliance tools should be built in. Encryption, tagging and access controls must apply automatically so you stay audit-ready without slowing delivery.
Adoption across teams: Developers, ops, and security all touch the platform. A clear self-service UI, role-specific dashboards and solid documentation reduce friction and drive real use, not shelfware.
Future-readiness: Check that the platform can support AI/ML pipelines, GPU workloads and edge deployments. Your IDP should evolve with your roadmap, not hold it back.
Developer experience at the core: Templates, paved workflows, fast feedback loops and one-click environments are what turn a platform into a productivity engine. The best IDPs lower cognitive load so developers focus on code, not infrastructure.
The right platform will enforce standards quietly, scale without friction, and give your teams the golden paths they need to deliver at enterprise speed.
FAQs on Internal Developer Platforms
What skills do teams need to manage an IDP?
A small platform engineering team with range. IaC, CI/CD, cloud services, APIs and automation. Product skills too: speak to developers, prioritise requests, ship improvements, measure adoption.
How do IDPs support AI and edge workloads?
They plug into MLOps pipelines, provision GPUs and treat models as deployable services with the same workflows as apps. For edge, they standardise rollouts to remote sites and handle constraints like intermittent connectivity and limited resources.
What role do IDPs play in reducing shadow IT?
They remove the reason to go around IT. Fast, compliant self-service makes the approved path the easiest path, with full visibility and audit by default.
How do IDPs improve developer onboarding in enterprises?
One portal, one set of templates, one-click environments. New hires discover services, owners and docs in minutes, then ship through the same pipelines they’ll use for real work. Onboarding drops from weeks to days.
What industries are adopting IDPs fastest?
Technology and SaaS led. Financial services, healthcare, telecoms and media are scaling next, with manufacturing and edge-heavy sectors close behind. By 2024, over 80% of organisations reported adopting platform engineering in some form.
How do IDPs support security and compliance automation?
Policy is encoded in the platform. RBAC, audit logs, encryption, approved images and regions apply by default. Pipelines run code scans and dependency checks automatically, so teams move quickly and stay audit-ready.
Final Thoughts: Enterprise Scale Demands Golden Paths, Not Golden Rules
Enterprise delivery moves fastest when the platform makes the right way the easy way. Internal Developer Platforms succeed by guiding teams along golden paths that bake in security, compliance and reliability, without slowing delivery or creativity.
This is a shift from control to enablement. Rather than gatekeeping tools and piling on reviews, the platform encodes policy as code, standardises workflows and removes manual toil. You gain speed and safety together, with fewer bottlenecks and far less shadow IT.
An IDP is not a switch. It is a product you nurture: start with clear use cases, listen to developer feedback, tune guardrails and measure outcomes. The payoff is consistent across high-performing teams: shorter lead times, fewer incidents and happier engineers.
If platform engineering is on your roadmap, make golden paths the organising principle. Let governance run quietly in the background and keep developer experience front and centre. For practical playbooks, metrics and case studies on making this work at scale, EM360Tech publishes ongoing guidance that can help you move from intent to impact.






Comments ( 0 )