It’s time to talk about ‘smishing,’ the less well-known brother of phishing. Though many people can spot email phishing attacks, they are much more vulnerable to the threat of smishing.
A big part of this increased threat is the lack of education among the general public. So, what is smishing? And why do people need to be aware of it?
This article delves into the meaning of Smishing and how to defend against it by providing 10 facts everyone should know about this unknown cyber threat.

What is Smishing?
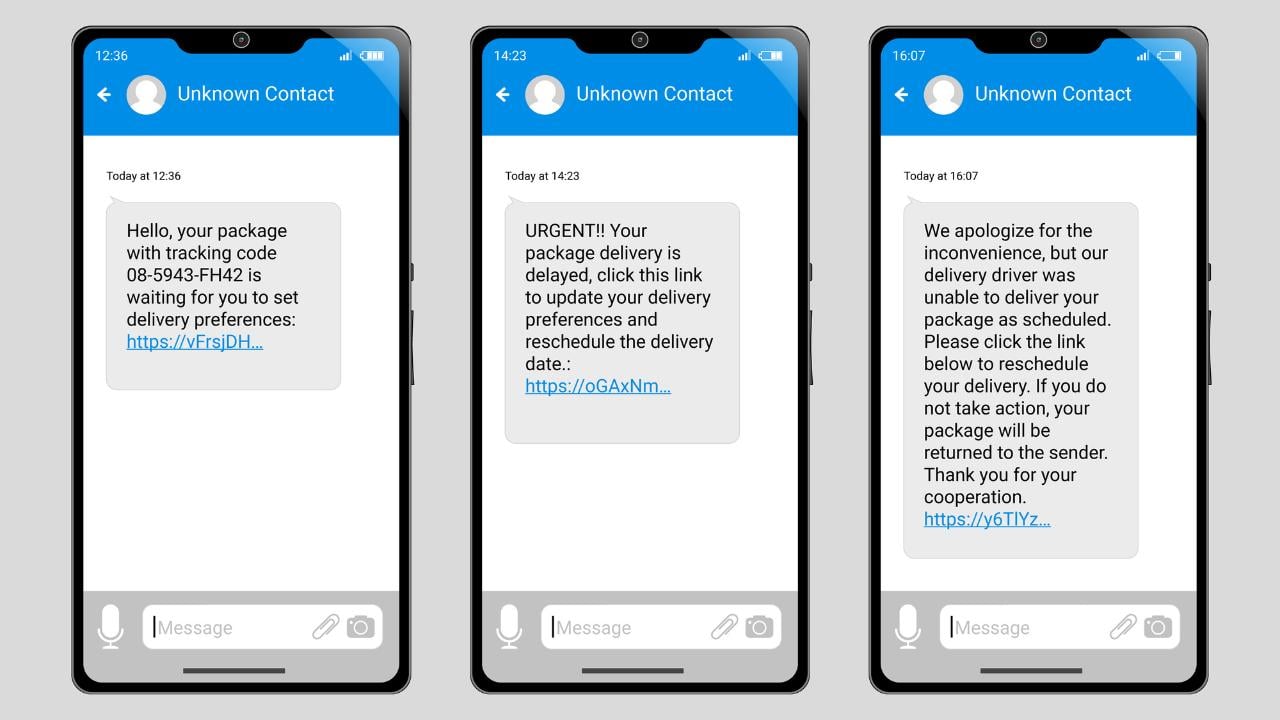
Smishing is a type of cyber attack where the criminal tries to get sensitive information by texting people. Scammers send messages that seem innocent, but they trick people into clicking bad links or downloading harmful content.
According to research, 97 per cent of Americans own a cell phone. This means that the vast majority of people are at risk of being defrauded by smishing. Unlike many forms of fraudulent activity, this attack affects all demographics.
Of course, it isn’t just the general public affected by smishing. Many businesses also need education. Smaller companies, in particular, are often victims of cyberattacks.
As such, raising awareness is of utmost importance. In this article, we’ll tell you ten key facts about this relatively unheard-of concept and the impact it can have. First of all, though, let’s look a little into its history.
The origins of smishing and its key characteristics
‘Smishing’ is a relatively recent addition to the cybersecurity lexicon. Yet, the concept goes back to the mid-2000s. As people started using cell phones and sharing numbers, cybercriminals began ‘smishing.’
Over time, smishing techniques have become more advanced, however, with hackers today using new technologies like generative AI to make attacks more convincing.
The SMS messages received look genuine and innocent. They look like they could come from a real organization like Amazon, PayPal, delivery services, and more. Psychological manipulation is commonplace. These cybercriminals use social engineering to prey on people’s emotions.
As useful concepts like preview dialling are introduced, cybercriminals soon latch on and use them for malicious intent. To make their smishing attempts more believable and successful, they learn about their potential victims.
How to defend against smishing
The threat of smishing is going nowhere. And phone users need to be proactive to remain one step ahead of hackers. The many ways that smishing tricks people make it hard to know what will happen next.
One hopeful defence is the role of technology. By using the power of artificial intelligence, we can better detect and prevent smishing attacks. Organizations can use AI to make mobile apps and messaging platforms smarter and more secure. AI can also analyze and identify suspicious patterns and behaviours to keep users safe.
Technology alone isn’t enough, however. Both organizations and individuals need to stay up to date on the latest scams. Awareness and education on smishing remain key to fighting this evolving and pervasive threat.

Mercenary Spyware as Statecraft
How commercial surveillance tools shift power in cyber conflicts, erode trust in tech, and challenge international cybersecurity governance.
10 Facts about Smishing
Without further ado, here are ten important facts you need to know about smishing if you want to defend yourself against this emerging threat.







Comments ( 0 )