AI-generated phishing. Faster ransomware crews. Clients who expect always-on protection without disruption. Managed service providers sit at the centre of that pressure. The tools are powerful, but time, staff capacity and alert noise are not. The gap is not technology as such.
It’s operationalising detection so incidents are found and contained quickly, regardless of the hour. That is where a layered approach earns its keep. Endpoint detection and response (EDR) is the essential foundation. Managed detection and response (MDR) unlocks its full potential — translating detection into resilience, and ensuring continuity even when the unexpected hits.

Set The Stage With Layered Security
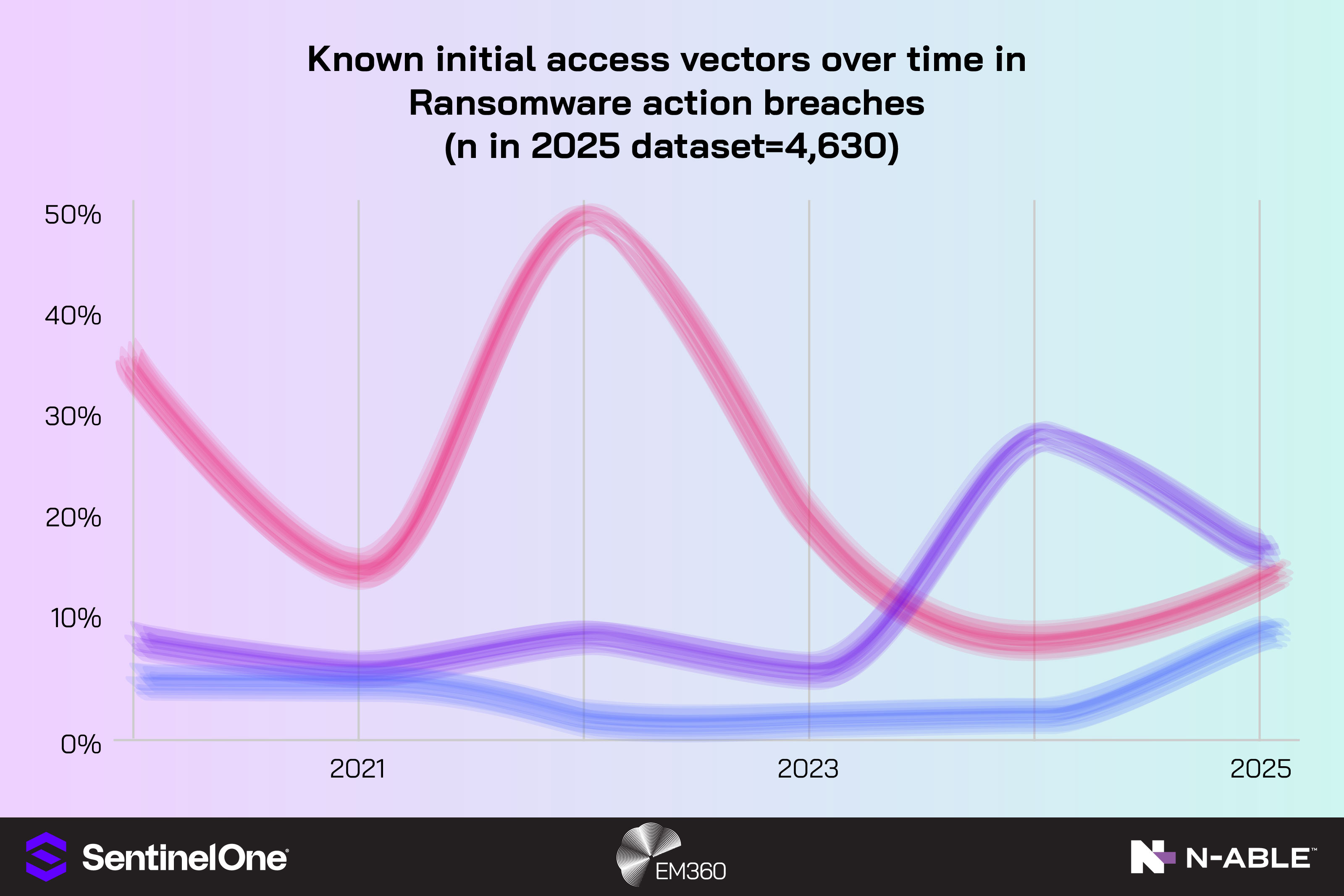
Verizon's 2025 DBIR links ransomware to 75% of system-intrusion breaches, making round-the-clock coverage essential for resilience. Boards and business owners also expect their MSP to keep the lights on through turbulence. That means planning for the before, during and after of a security incident.
A layered model is the most reliable way to do that. It builds operational resilience into every tier — ensuring incidents are not only detected and contained but absorbed and recovered from without halting business momentum.
Endpoint detection and response gives you sensor coverage, forensic depth and fast containment on the devices where attackers try to execute. Managed detection and response surrounds that foundation with 24/7 human expertise, triage, investigation and guided response.
The combination focuses your team on higher-value work, reduces the time an attacker has to move and gives clients the assurance that someone is watching when they are not. This article is a practical playbook. It shows how to run EDR and MDR together, so you can improve continuity, prove value, and grow with confidence.
Quick Shared Language For Busy Leaders
EDR is endpoint detection and response. Think of it as high-fidelity visibility across endpoint activities, backed by analytics that flag suspicious behaviour and give you controls to isolate, roll back, and remediate. It's the essential baseline for endpoint security.
MDR is managed detection and response. It's a human-led service that provides always-on monitoring, alert triage, threat hunting and incident response. MDR teams turn signals into decisions, then into action, and they do it every hour of every day.
An example is N-able’s layered model, which combines SentinelOne EDR as the endpoint foundation with Adlumin MDR as the operational layer. SentinelOne delivers the automated detection, telemetry and rollback capabilities that keep endpoints secure.
Adlumin brings the human expertise — continuous monitoring, triage and guided response — that turns those signals into decisions and action. It’s the human layer that operationalises detection, reduces dwell time and strengthens resilience across every managed environment.
Some providers add Extended Detection and Response (XDR) to correlate signals across identity, email, network and cloud. That human layer is what sustains resilience — the ability to anticipate, absorb, and adapt under constant pressure. You don't need to start there to get results though.
Begin with a sound EDR foundation and MDR to operationalise it, then expand correlation as your clients’ needs mature.
Detection Alone Doesn’t Keep You Resilient
Detection is vital. Resilience requires more. EDR will surface high-quality alerts and give you controls to contain them. Without defined handoffs and out-of-hours coverage, those alerts can queue up, context can be missed and an otherwise containable incident can become a business disruption. Alert fatigue is real. So are staffing limits.
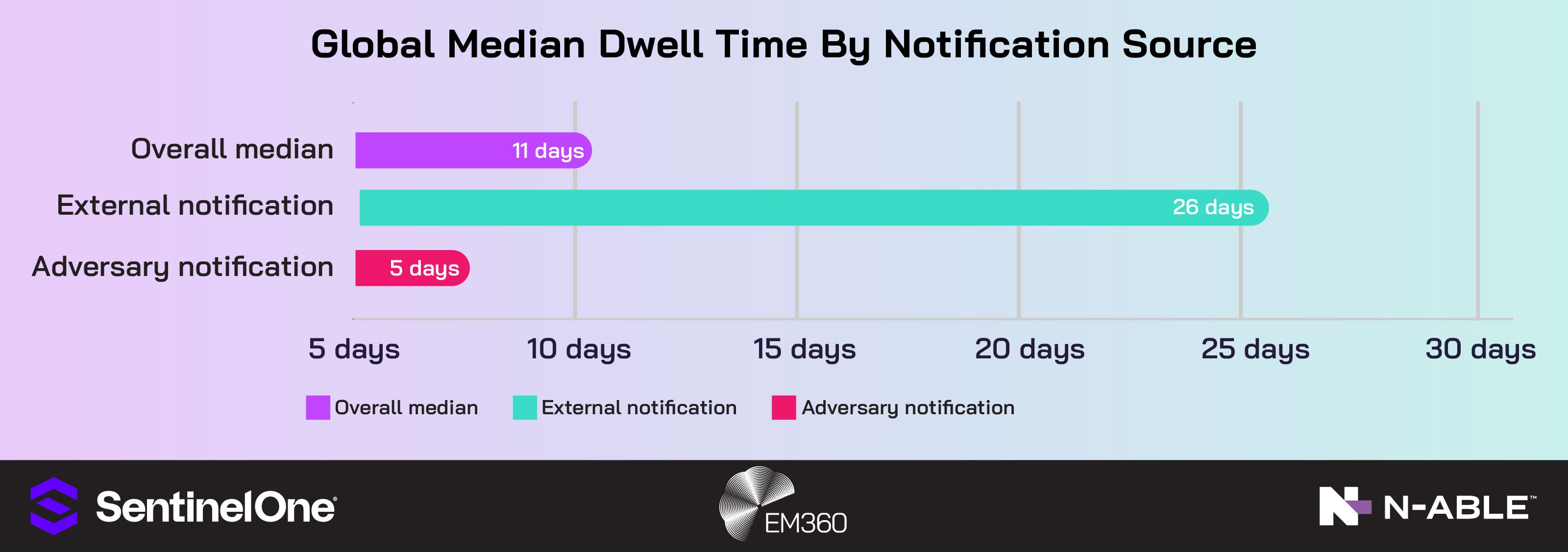
Mandiant’s M-Trends 2025 reports a global median dwell time of 11 days overall, rising to 26 days when discovered via external notification and dropping to 5 days when adversaries themselves notify in ransomware events. And every hour between detection and action increases the risk of lateral movement, data theft and downtime.
Rethinking EDR, XDR, MDR
Why real-time response lags despite advanced tools, and how CISOs must reset expectations and maturity around managed detection.
But regardless of which scenario you consider, it’s a window that only shrinks with continuous triage and action. MDR keeps eyes on glass after hours, applies playbooks consistently and escalates only what matters, with clear recommended actions. The outcome is a shorter path from detection to containment and fewer false positives reaching your engineers.
In other words, true resilience comes from closing the space between detection and response — ensuring every alert translates into action before it becomes an incident.
How MDR Unlocks The Full Value Of EDR
EDR produces rich signals. MDR ensures that the signal leads to the right action at the right time. Practically, that looks like this. Analysts monitor EDR telemetry 24/7. They triage alerts, enrich them with threat intelligence and hunt for related activities.
When an event crosses your agreed thresholds, they isolate and kill processes or quarantine artefacts within your authority model, then hand off a clean, concise ticket to your team with evidence and next steps. That measured flow reduces dwell time, speeds isolation and preserves your engineers’ focus for remediation and client work.
Executive-ready reporting shows incidents triaged, time to contain, rollback events and hygiene fixes driven each month. It turns a stream of technical alerts into a business narrative your clients can understand and trust. Together, they form a feedback loop that continuously strengthens resilience — faster recovery, smaller impact, and smarter prevention with every event.
In practice, the benefit shows up fast: an N-able customer reported preventing a ransomware attempt within six hours of MDR deployment, with 24×7 coverage sustaining outcomes thereafter.
Operating Model For Layered Protection
A good operating model is simple, predictable and auditable. Start with joint playbooks that define who does what, when and with what authority. Agree on the L1, L2, and L3 responsibilities between your team and the MDR provider. Set change windows for planned actions and policies for emergency response.
Inside AI-Driven MDR for MSPs
How MSPs can use AI, automation and co-managed SOC services to handle 90% of alerts and scale detection and response without new headcount.
Establish authority to contain so analysts can isolate endpoints out of hours when there is clear evidence of active compromise. Integrate telemetry in phases. EPP and EDR first, then identity and email, then cloud sources where needed. This gives you correlation benefits without overwhelming your team on day one.
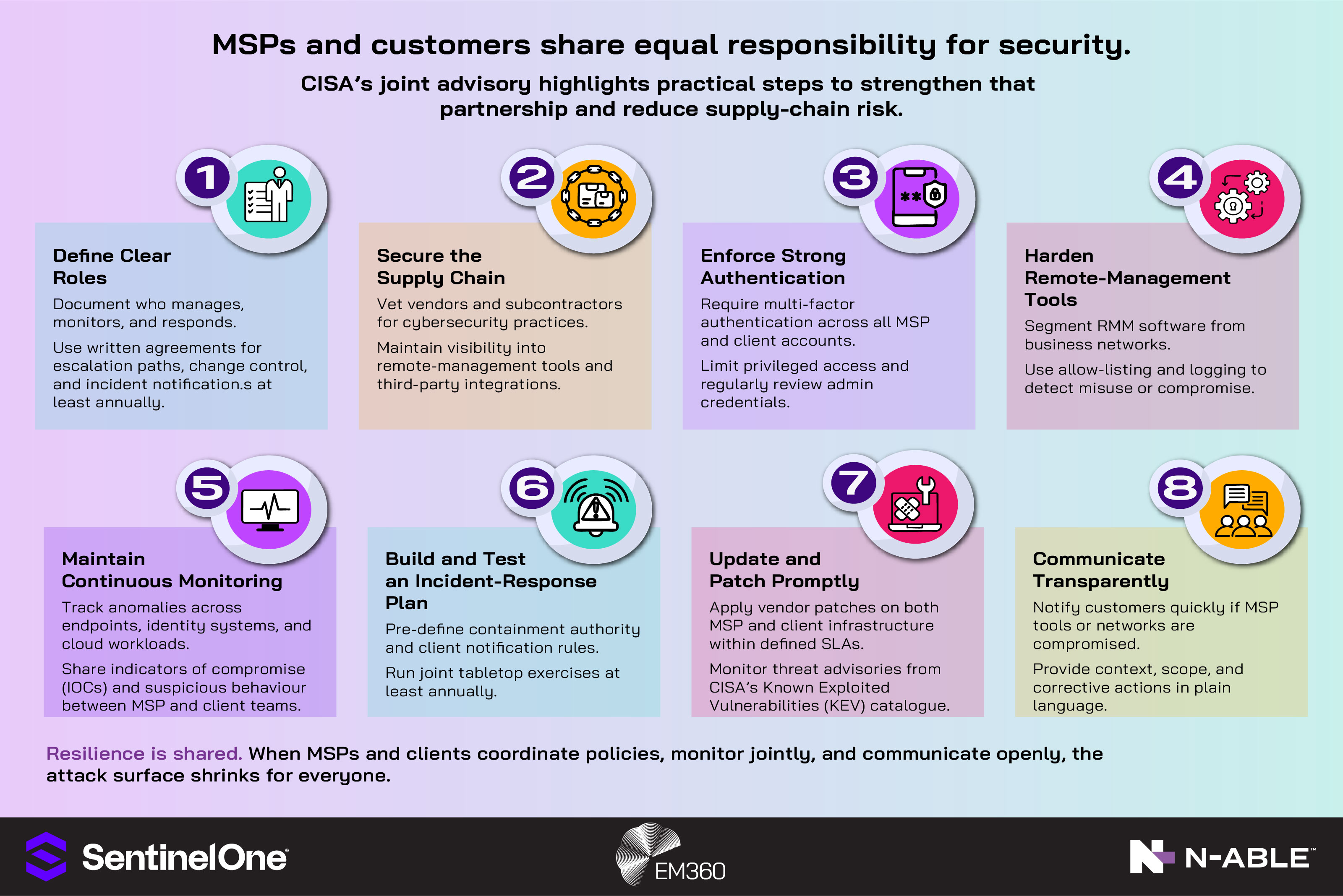
Each integration step adds depth to your defensive posture, reinforcing resilience through layered visibility and response readiness. The goal isn’t more tooling, though. CISA’s joint advisory for MSPs and their customers sets out concrete shared-responsibility actions and is a useful benchmark when finalising playbooks and containment authority.
And these show that it’s cleaner handoffs, faster decisions and consistent investigation workflow across tenants.
Define the handoffs that prevent gaps
Document the exact trigger points. EDR alerts that there are fires. MDR triages and enriches. If thresholds are met, MDR executes pre-approved containment and opens a ticket in your system with evidence, a root cause, and recommended remediation.
The escalation matrix sets service levels for acknowledgement and action. Client communications are templated, so you can update stakeholders quickly with facts, impacts, and next steps.
Prove value with the right reporting
Adopt a monthly MDR plus EDR scorecard. Show incidents triaged, time to contain, blocked lateral movement attempts, endpoint rollback events and hygiene improvements delivered. Include MTTR trends and open risks by tenant.
Keep it to one page for leaders, with a link to a technical appendix for your engineers. The aim is transparency and momentum. Clients should see risk reducing and the attack surface shrinking over time.
Two MSP Paths That Scale
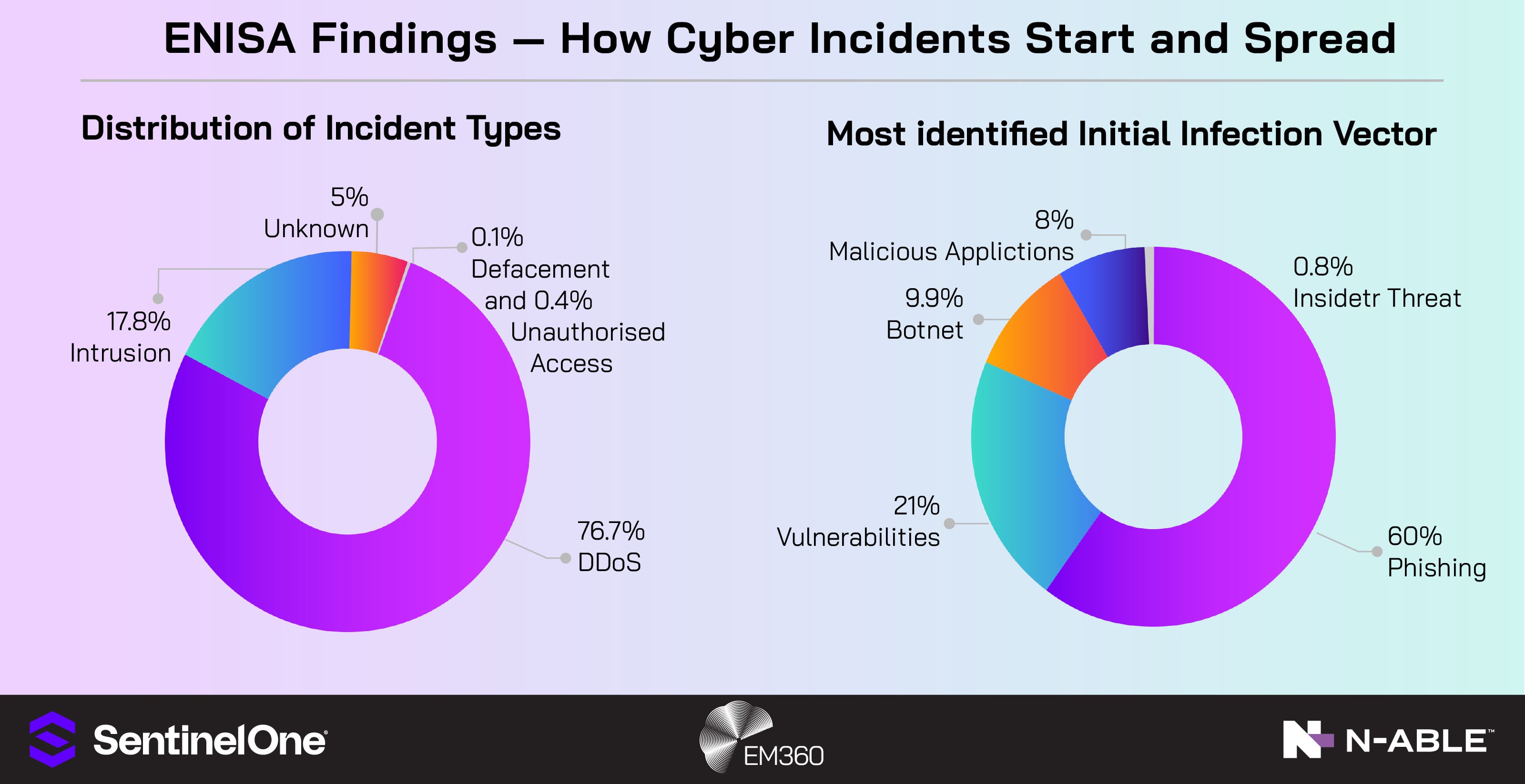
The current threat tempo justifies the investment: ENISA’s Threat Landscape 2025 analysed ~4,900 curated incidents from July 2024 to June 2025 and highlighted faster exploitation alongside ransomware’s continued centrality. Different MSPs start in different places. The layered model adapts.
Lean MSPs build resilience without a SOC
When Ransomware Tests MSPs
Explore how MSPs prepare for the inevitable breach, balance automated controls with human judgment, and keep client businesses running under attack.
If your team is 10 to 50 people, start with one standard. Roll out a strong EDR baseline across tenants and pair it with MDR for 24/7coverage. Begin with your top five clients by risk and exposure. Ensure that you pre-approve isolation and rollback within defined boundaries to prevent overnight delays in critical actions.
Use the monthly MDR reports as proof in QBRs to expand coverage across the rest of your client base. Document standard operating procedures, bake them into onboarding and give your engineers a single process to follow, regardless of tenant.
Larger MSPs scale consistency across accounts
If your organisation has more than 100 employees, treat MDR as a co-managed SOC. Use it for overnight coverage, overflow during peak events and deep triage on complex cases. Normalise playbooks across tenants, so investigations look the same every time. Add identity and email telemetry where you have higher risk or compliance needs.
Introduce targeted hunts based on recent campaigns and your clients’ verticals. The objective is consistency. Every client gets the same investigative depth and the same response quality, whether the alert lands at 2 p.m. or 2 a.m.
Whether you’re scaling or standardising, the objective is the same — to build resilience into every managed environment, so recovery is measured in minutes, not days.
Package And Position The Service Clients Actually Understand
Clients don't buy acronyms. They buy uptime, evidence and confidence. Package your layered service in plain language.
Essential packages give smaller environments a simple start. The EDR foundation provides business-hours monitoring, while the MDR authority is responsible for isolating high-confidence threats after hours. Clear reporting, clear boundaries.
Advanced packages add 24/7 MDR with pre-approved isolation and rollback, plus a monthly executive report that a finance lead can read. Decisions are evidenced. Hygiene is improving. Risk is trending down.
Complete packages are for regulated or higher-risk clients. Keep the Advanced features and add identity, email and cloud telemetry. Run quarterly tabletop exercises, breach simulations and recovery drills so leadership understands the plan and people know their roles when time matters most.

Why SMBs Now Lead Threat Maps
Industrialized attacks, AI-driven social engineering, and identity abuse are pushing midmarket firms into the center of the cyber threat landscape.
When you position this in proposals and QBRs, map features to outcomes. For business context at the board level, IBM’s Cost of a Data Breach 2025 pegs the global average breach at USD 4.44 million and flags shadow AI as an emerging driver of risk and cost, reinforcing the case for continuous monitoring and faster containment.
Reduced dwell time means a lower chance of lateral movement. Faster isolation means a smaller blast radius. Monthly reporting means your board has evidence for auditors and insurers. Tie every capability to continuity, compliance and business outcomes.
When framed this way, MDR + EDR isn’t just a security solution — it’s a resilience strategy that protects uptime, preserves reputation, and strengthens client trust.
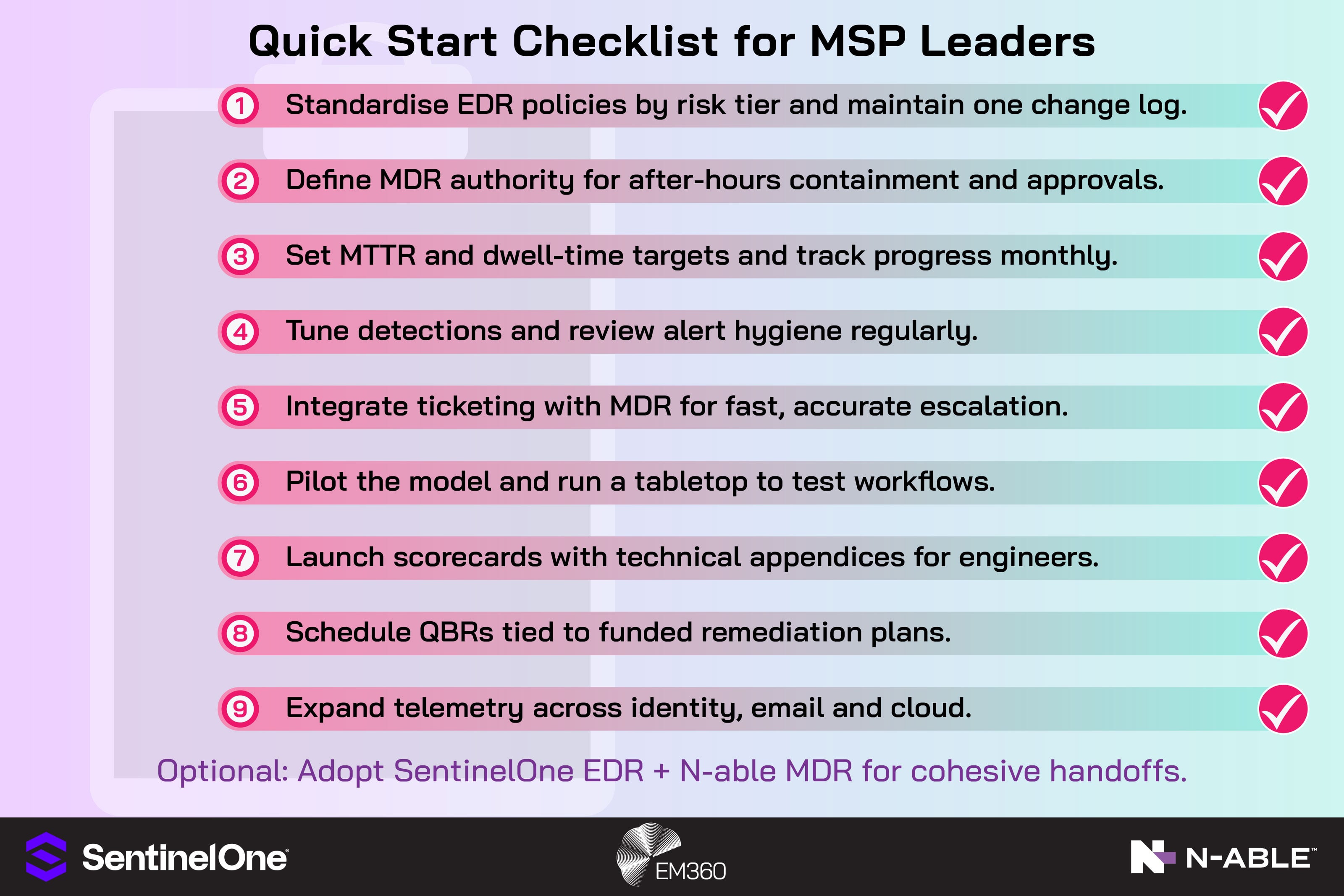
Quick Start Checklist For MSP Leaders
To make resilience measurable and repeatable, anchor it to a simple operating cadence. This playbook condenses the layered approach into concrete steps your team can execute and measure.
- Standardise EDR policies by risk tier across all tenants; align prevention, detection, isolation, and rollback settings; and keep a single change log.
- Define MDR containment authority for afterhours and critical events, spelling out permitted actions, evidence thresholds, notification paths and how approvals are recorded.
- Set MTTR and dwell-time targets, publish your baseline and surface trendlines in the executive scorecard so improvement stays visible and accountable.
- Tune for high-signal detections and suppress noisy rules responsibly, with before-and-after metrics and a scheduled hygiene review to confirm the signal stays strong.
- Integrate your ticketing workflows and escalation matrix with the MDR team so alerts land with the right people, first time.
- Pilot the model with a risk-weighted client cohort and run a tabletop to pressure-test roles, timing and decisions.
- Launch a monthly one-page executive scorecard with a technical appendix for the engineers.
- Schedule QBRs that turn findings into a funded remediation plan with owners and dates.
- Plan the next wave of telemetry across identity, email and cloud so correlation is ready for XDR.
- Optional: standardise on SentinelOne EDR with N-able MDR for clean handoffs and faster time to value.
Final Thoughts: Stronger Together Is The Resilience Play
EDR is the foundation. MDR unlocks its full potential so detection turns into timely action that protects continuity. The playbook is simple to state and powerful in practice: standardise EDR, give MDR clear containment authority, measure dwell time and MTTR, and prove progress with a one-page scorecard that business leaders can read.
In a world of AI-shaped phishing and faster ransomware crews, resilience is earned in the handoffs — through disciplined coordination between detection and response. If you want to see this model working end to end, explore how N-able EDR powered by SentinelOne delivers 24/7 triage, guided containment and executive-ready reporting across multi-tenant estates.
For broader context and practitioner guidance on MSP cyber resilience, follow EM360Tech's ongoing coverage and analysis across layered security, incident readiness and operational playbooks.






Comments ( 0 )