Small and mid-sized clients now expect the same outcomes that large enterprises demand. Always on protection. Fast response. Minimal disruption. At the same time, most MSPs are managing tight margins, rising tooling costs, and a market that assumes 24×7 vigilance.
The gap is no longer intent. It is the operating model.
MSPs that standardise a layered security stack and pair automation with co-managed detection and response can deliver enterprise-grade outcomes without enterprise-level headcount or spend. That approach turns security from a cost centre into a profitable growth engine.
Industry leaders are converging on the same conclusion: managed detection and response is now essential for MSPs supporting regulated sectors, and packaging security around measurable outcomes is what separates growth-focused providers from those falling behind.

The Cost Challenge Facing MSPs
Security has become a business of expectations. Clients assume round-the-clock monitoring, rapid containment, and clean recovery as table stakes. Meeting those expectations with a traditional build-it-yourself SOC is rarely feasible. The pressure points are clear and financial.
Staffing and specialist skills shortage
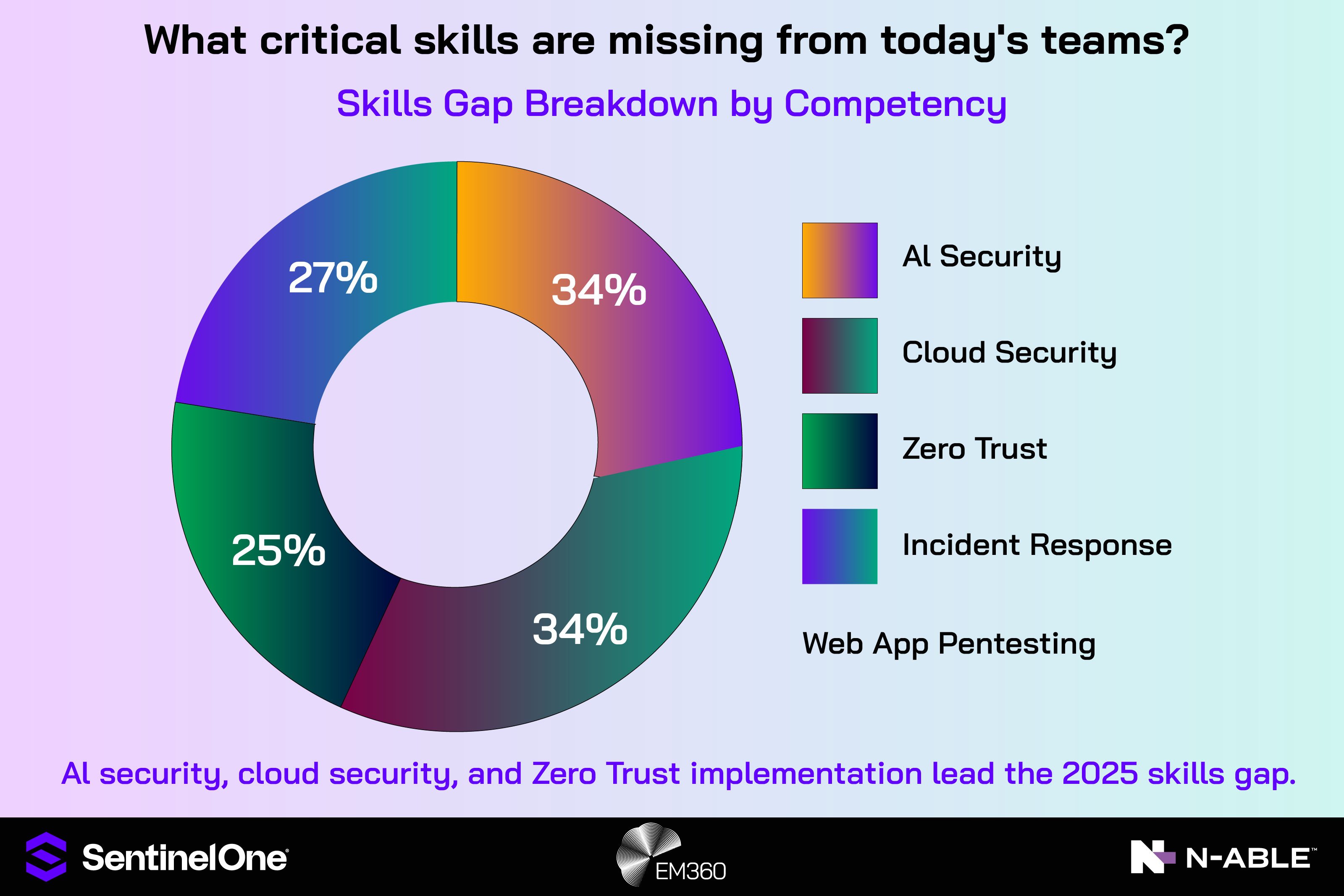
The security talent market is tight, and MSPs feel the strain quickly because they rely on smaller teams and tighter budgets. Finding analysts with the right blend of detection engineering, incident response experience, and platform knowledge takes time and pushes salaries up.
Even with the right people, maintaining full rota coverage across nights, weekends, and holidays is hard for small teams. This is why many providers extend their bench with co-managed SOC models that add 24×7 capability without adding permanent headcount.
Tools, infrastructure and operational burden
Security tooling is powerful, but it is not free to run. Telemetry collection, storage, and analysis can expand rapidly with every new client and integration. Licensing across endpoint detection and response platforms, log analytics, identity controls, and email filtering increases with each seat.
The hidden cost appears in daily operations. Tuning, detection content, upgrade cycles, and integration work pull engineers away from revenue-generating projects. That is how security stack cost quietly erodes margins.
Rethinking EDR, XDR, MDR
Why real-time response lags despite advanced tools, and how CISOs must reset expectations and maturity around managed detection.
24×7 coverage without breaking margins
Threats do not keep office hours. Clients still expect uptime, evidence, and clean recovery. Continual monitoring, rapid escalation, and out-of-hours response can quickly overwhelm margins if you rely only on your own rota. Co-managed MDR closes the gap. You add operational leverage, preserve service quality, and avoid turning your P&L into an overtime ledger.
Efficiency Through Automation, MDR And A Layered Security Stack
A scalable security model relies on structure, clarity, and the ability to reduce manual work. Automation absorbs repetitive tasks, MDR provides continuous human oversight, and the operating model becomes something MSPs can apply consistently across every client. That consistency is what strengthens long-term resiliency.
Role of EDR in the stack
Endpoint detection and response is your first responder. It observes behaviour, flags lateral movement, and blocks malicious activity before damage spreads. N-able EDR powered by SentinelOne is a strong example for MSPs because it combines behavioural analytics with rapid containment that scales across many tenants.
EDR is the starting point of the layered security model, and every other tool in your stack builds on its foundation.
Inside AI-Driven MDR for MSPs
How MSPs can use AI, automation and co-managed SOC services to handle 90% of alerts and scale detection and response without new headcount.
Why MDR extends and operationalises EDR
Managed detection and response (MDR) supplies the human layer that makes EDR consistently effective. Analysts triage alerts, correlate signals across sources, and guide response in real time. Co-managed models like what N-able offers give MSPs 24×7 eyes on glass, detection engineering updates, and playbook-driven actions without hiring a full shift team.
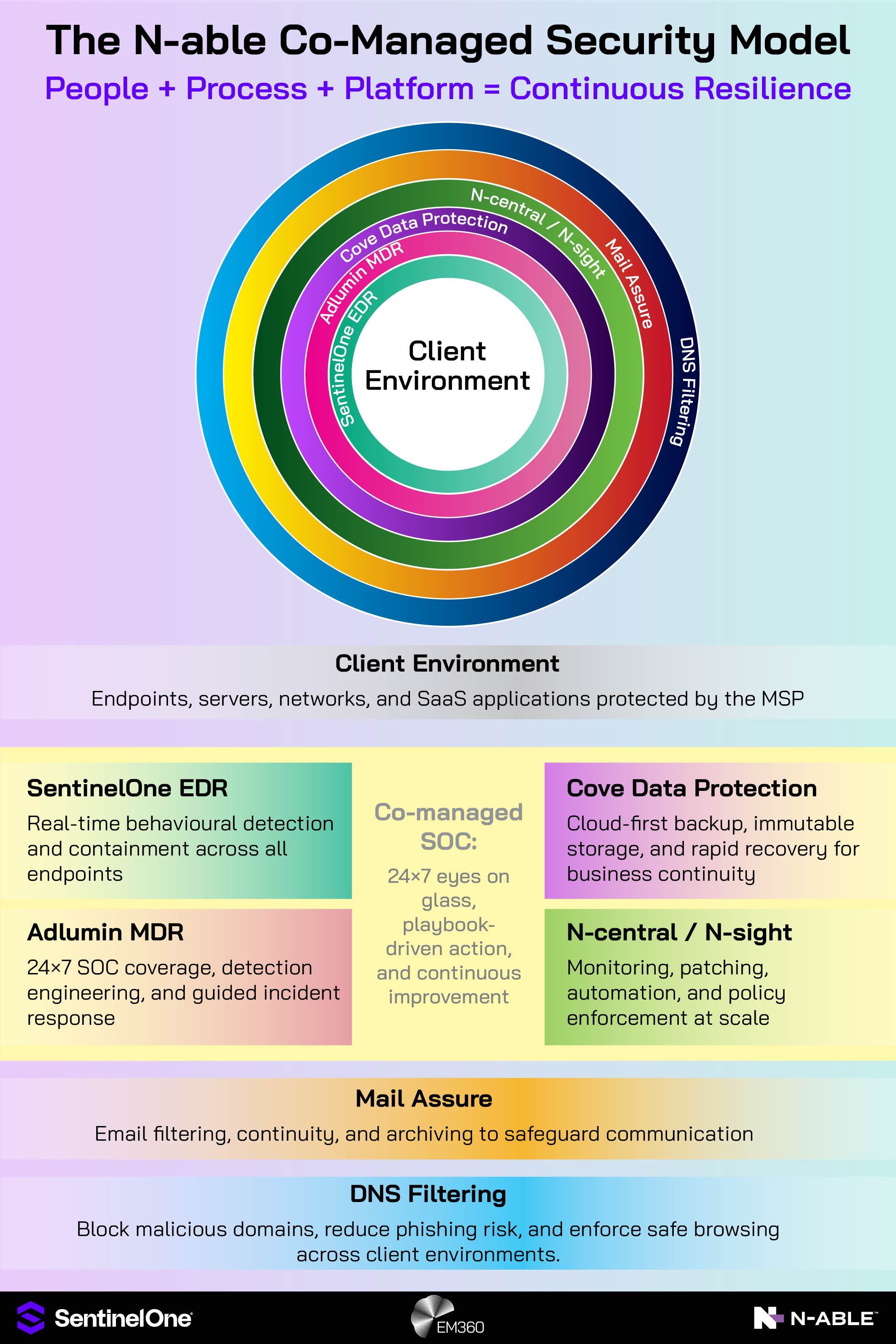
This is how EDR value is realised at scale, particularly across a diverse SMB client base that needs fast decisions and clear communication at any hour.
The layered security framework for MSPs
EDR and MDR form the core of the operating model. But resiliency depends on adding more than detection and response alone. For example, a backup and disaster recovery system with offsite, immutable copies. The point here is having a system in place that will supports recovery as quickly as the situation allows.
Then email security that will reduce initial access issues, as well as identity and access management tools to limit lateral movement if malicious actors do compromise a network.
Finally, package all this in a standard blueprint so every client benefits from the same outcomes. That is how MSPs deliver enterprise-grade protection everywhere, not just for the biggest accounts.
When Ransomware Tests MSPs
Explore how MSPs prepare for the inevitable breach, balance automated controls with human judgment, and keep client businesses running under attack.
Make Security A Profit Centre With Service Packaging
Profit follows clarity. When MSPs sell tools, buyers compare line items. When MSPs sell outcomes, buyers value risk reduction, speed to recover, and continuity. Turning security into a profit centre starts with how you package and position the service.
Designing tiered bundles anchored on outcomes
Offer clear, outcome-driven tiers mapped to a client's risk appetite and their regulatory needs. For example:
- Resilience Essentials: baseline hardening, email filtering, EDR on every endpoint, scheduled reporting, basic backup, and co-managed triage for 24x7 coverage of critical alerts.
- Resilience Plus: Everything in the Essentials tier as well as MDR coverage with guided response, identity and role-based access policy baselines, advanced backup and offsite recovery testing, and quarterly resilience improvement reviews.
- Business Continuity Premium: Everything in the Plus tier, with comprehensive backup and disaster recovery, recovery time objectives, incident response playbooks defined in advance, and documented board-level reporting.
Position each tier with simple language and evidence of value, and price them based on outcomes rather than the tools you’re using to provide your layered security. Map features to outcomes like preemptive defence, reduced dwell time, faster response, and defined recovery windows.
Aim to position your middle tier as the standard, with the top tier as best for clients with higher risk profiles or in regulated industries. This will help you encourage adoption while still protecting those all important margins.

Why SMBs Now Lead Threat Maps
Industrialized attacks, AI-driven social engineering, and identity abuse are pushing midmarket firms into the center of the cyber threat landscape.
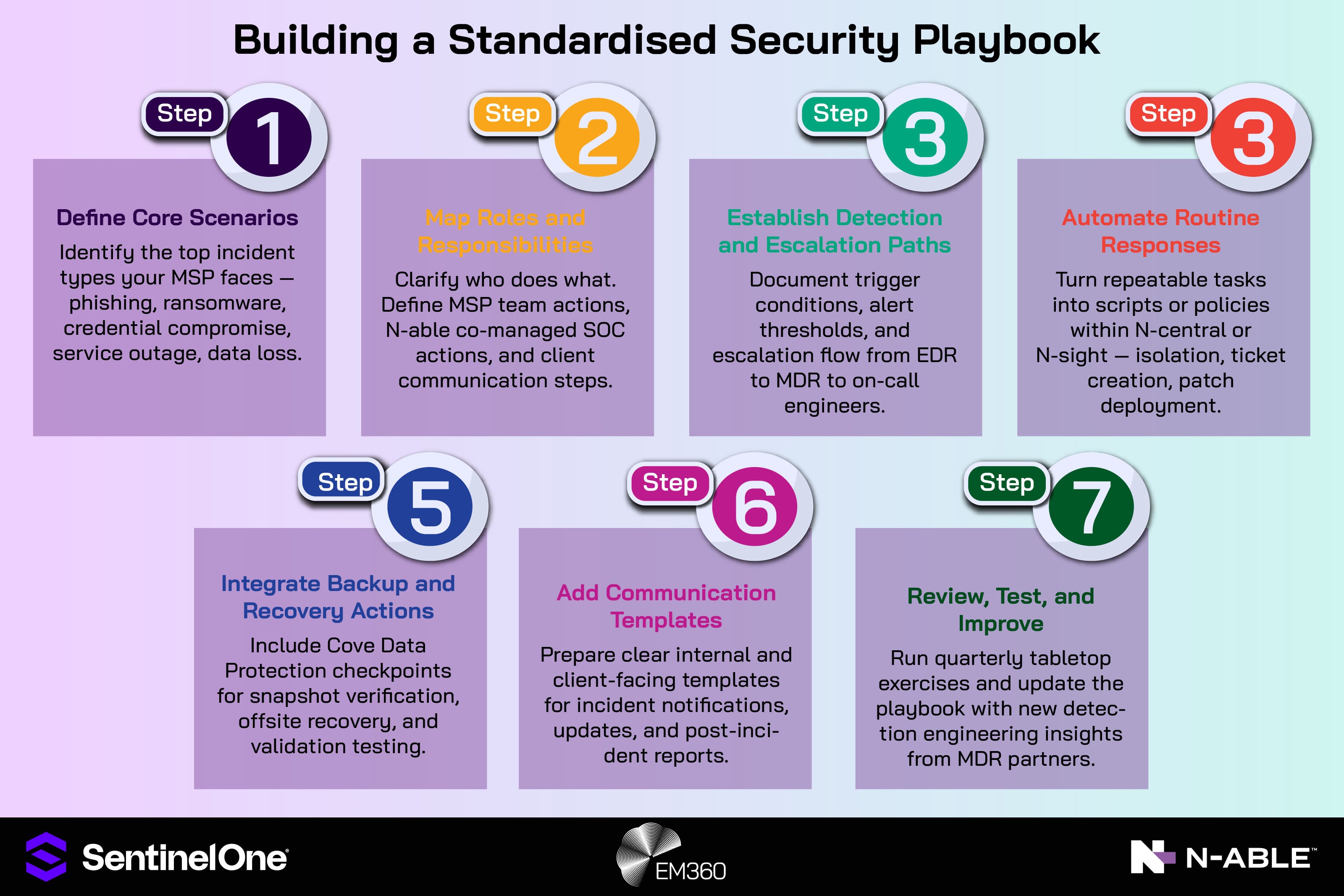
Operationalising for margin protection
Profitability depends on a repeatable delivery model. Use standard images, baseline policies, and a standardised security playbook that covers onboarding, tuning, alert routing, and response steps. Automate common tasks such as isolation commands, backup verification, and ticket creation.
Let EDR handle real-time detection and MDR manage after-hours surge while your engineers focus on projects and advisory work. The result is lower cost-to-serve with higher perceived value.
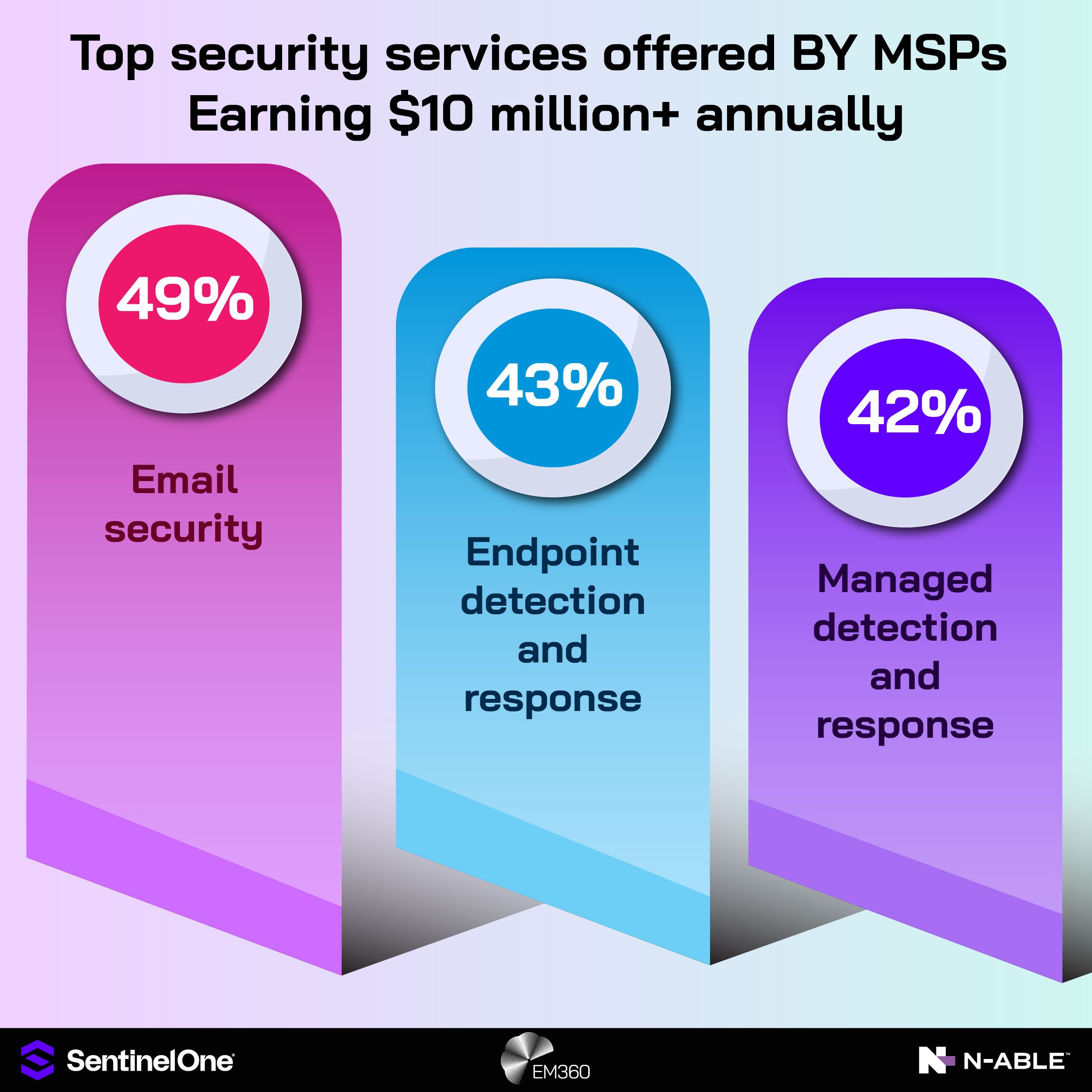
Differentiation and growth through enterprise-grade positioning
Most MSPs say they deliver strong security for their clients. Fewer can demonstrate a documented resilience model with measured recovery times and evidence of continuous improvement. Lead with outcomes and back them with transparent reporting. When you can credibly deliver enterprise-grade protection at SMB price, you set yourself apart with evidence rather than claims.
Protect Margins While Scaling With Real-World Resilience
A layered approach only proves its worth when tested. This was demonstrated earlier this year when CRS Technology Consultants supported a client during a ransomware attack using the services and products provided by N-able. What followed demonstrated how the right stack design and operating model can turn a crisis into a business continuity success story.
Incident chain: Attack, containment, recovery
Attackers linked to Akira exploited a firewall vulnerability, obtained valid credentials, and began lateral movement. N-able EDR powered by SentinelOne flagged the behaviour and blocked payloads. Local backups were destroyed when the adversaries pivoted, but offsite copies were intact.
Again, the N-able stack played a role, and CRS was able to restore their customers' priority systems from cloud backups. In this particular case, users returned to work by lunchtime, and full operations resumed by day-end. No ransom was paid and no data was lost.
What this incident shows is that the right prevention and containment tools can limit the impact of a cyberattack. And it's also possible to shorten downtime if the recovery systems you have in place have been fully tested and proven to be effective.
Translating the outcome into a standard service offer
After the incident, MDR became a non-negotiable standard for the MSP’s clients. That is the correct move. When you raise the minimum control set for all customers, you reduce the variance in exposure, simplify support, and improve your ability to meet service levels.
Turn post-incident learning into a formal service standard, update contracts to reflect response scopes, and publish recovery metrics. This protects margin and reputation because every client benefits from the same dependable baseline.
Building Trust And Retention Through Layered Protection
Security is not only about stopping attacks. It is about confidence that the business will be working tomorrow. Resiliency is the outcome clients rely on most — the assurance that operations can continue even when incidents occur. Clear packaging, measurable recovery times, and regular reviews build trust with owners, finance leaders, and boards.
Trust lowers churn, raises lifetime value, and opens the door to advisory work that lifts your blended margin. When a client can point to a documented plan, a tested backup regime, and a proven response model, they stay. The MSP that provides that level of assurance is seen as a partner, not a vendor.
Final Thoughts: Resilience Builds Profitable Growth
MSPs can deliver big-company outcomes without big-company resources when they standardise a layered security stack, anchor EDR with co-managed MDR, and hard-wire recovery into daily operations. The cost challenge is real, but efficiency, packaging, and proof of outcomes turn security into a profit centre.
The strongest signal in the market is simple. Providers who can detect quickly, contain reliably, and aim to minimise recovery time will build the trust that drives renewals and referrals. If you want a practical route to that model, N-able’s ecosystem gives you the components and operating patterns to make it work, with SentinelOne at the endpoint and managed response covering the gaps that headcount cannot.
For leaders ready to sharpen their blueprint, EM360Tech continues to share the strategies and real-world lessons from practitioners who are already running these playbooks and achieving the recovery times that win boardroom confidence.






Comments ( 0 )