From cloud-native infrastructure and remote workforces to sprawling SaaS portfolios and third-party integrations, the average organisation’s digital footprint is expanding faster than most security teams can map — let alone protect. In this increasingly perimeterless world, it’s not just known systems that are vulnerable. It’s the assets you’ve forgotten, the ones you never knew existed, and the ones created outside your control.
That’s exactly what today’s attackers are counting on.
Modern cybercriminals don’t storm the front gates — they look for the side doors you didn’t lock because you didn’t know they were there. And with the attack surface now stretching across physical, digital, cloud, and human vectors, the old approach of scanning known networks at regular intervals just doesn’t cut it.

So how do you stay ahead of what you can’t see?
What Is an Attack Surface?
An organisation’s attack surface is the sum of all the points where an unauthorised user — a cybercriminal, malicious insider, or even an accidental actor — could attempt to enter or extract data from its systems. These aren’t just firewalls or exposed endpoints. They include everything from misconfigured cloud buckets and forgotten subdomains to third-party software integrations and employee devices connected remotely.
Every connected asset, interface, user account, and line of exposed code contributes to the total attack surface. And the more complex your digital environment becomes, the more that surface expands — often invisibly.
Why you should know your attack surface
You can’t secure something if you don’t even know that it exists. Malicious parties are constantly searching for weaknesses, and these unknown assets are a favourite entry point because of how easy they are to manipulate.
Understanding your attack surface gives you the visibility and context to:
- Identify shadow IT and unmanaged assets
- Spot vulnerabilities before attackers do
- Prioritise risk based on real-world exposure
- Strengthen your security posture beyond just compliance checkboxes
At the end of the day, it’s not good enough to just know what is inside your perimeter. Half the battle these days is determining where your perimeter actually is.
Attack surface vs threat surface
Though often used interchangeably, attack surface and threat surface refer to different aspects of cyber risk.
- Your attack surface is made up of all the assets that could be exploited.
- Your threat surface reflects the actual attack vectors currently being targeted or exploited by active threats.
Think of it this way: the attack surface is the map; the threat surface shows where the fighting is happening. Effective security depends on understanding both — and reducing the gap between them.
Types of Attack Surfaces
The modern attack surface is more than just a collection of systems — it’s a living ecosystem of interconnected risks, shaped by how your business operates, scales, and transforms. To manage it effectively, security leaders need to understand the core domains that make up the full scope of exposure.
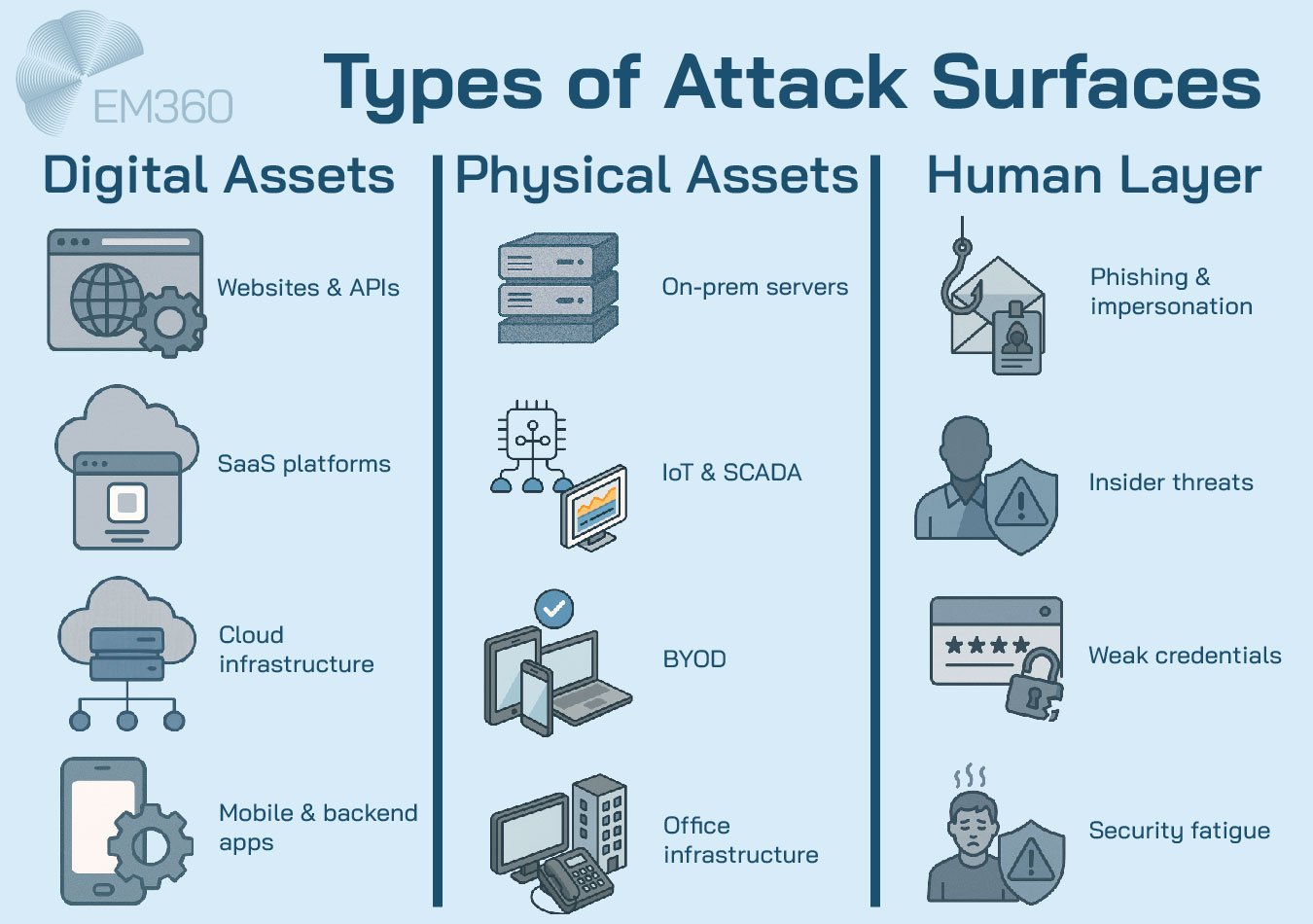
Digital assets (web, cloud, apps)
This is where most organisations start — and where the complexity tends to spiral. Your digital attack surface includes:

Rethinking Trust at the Edge
Why protocol-era VPN and IKEv2 assumptions undermine Zero Trust, and what boards should ask about hidden edge dependencies.
- Public-facing websites and Application Programming Interfaces (APIs): Often the most obvious targets, especially if they expose outdated code, directory structures, or admin access points.
- Cloud infrastructure and virtual machines: Misconfigured storage, excessive permissions, and forgotten test environments in platforms like Amazon Web Services (AWS), Azure, or Google Cloud Platform (GCP) represent some of the most common risks today.
- SaaS applications and third-party platforms: Every new integration adds new data flows and authentication pathways, many of which sit outside the security team’s direct control.
- Mobile apps and backend services: Vulnerabilities can be introduced not just through code but through unpatched Software Development Kits (SDKs), insecure data storage, or weak API validation.
Because these environments are built for speed and scale, they tend to change constantly — which means traditional point-in-time scans miss more than they catch. That’s why digital asset discovery and ongoing visibility are foundational to any serious ASM strategy.
Physical assets
Despite the cloud-first shift, physical assets are still a vital part of your attack surface — especially in hybrid workplaces and regulated industries. This layer includes:
- On-premises servers and networking equipment: Still widely used in finance, government, and healthcare where compliance or latency issues apply.
- Office infrastructure and workstations: Unattended terminals, shared logins, or even exposed printer ports can become access points for internal and external threats.
- Internet of Things (IoT) devices and industrial systems: From smart cameras to HVAC units and Supervisory Control and Data Acquisition (SCADA) systems, these assets often lack basic protections and are notoriously hard to patch.
- BYOD (Bring Your Own Device): Personal laptops, mobile phones, and tablets used for work introduce endpoints outside the IT department’s purview.
Physical attack surfaces are often the least visible — and therefore the least protected — even though they often connect directly into core digital systems.
Social engineering and human factors
People don’t patch as easily as software — and attackers know it. Human behaviour has become one of the most consistently exploited vectors in modern cyberattacks. This includes:
Chrome as Enterprise Control
How treating browsers like managed infrastructure changes patch SLAs, ownership models and controls for SaaS, identity and admin access.

- Phishing and impersonation attacks: From business email compromise (BEC) to voice phishing (vishing) and AI-generated deepfakes, attackers are increasingly mimicking trusted contacts to steal credentials or authorise payments.
- Insider threats: Whether accidental (misdirected emails, poor data handling) or malicious (data exfiltration, sabotage), internal actors can bypass even the best external defences.
- Weak credentials and poor security hygiene: Shared passwords, password reuse across tools, and delays in deprovisioning former employees are all common, preventable attack vectors.
- Security fatigue and over-reliance on tools: When employees are overwhelmed with alerts, pop-ups, and changing rules, they’re more likely to click without thinking or bypass basic controls.
What makes this layer so critical — and so dangerous — is that it’s not static. People change roles. They leave companies. They make mistakes. And often, they’re the last to know when something goes wrong.
Assessing the Attack Surface
You can’t reduce what you haven’t mapped. That’s the guiding principle behind attack surface assessment — the process of identifying, inventorying, and contextualising every potential entry point across your organisation’s digital, physical, and human domains.
But this isn’t a one-time audit. In modern environments, your attack surface changes every time someone spins up a test environment, pushes a new update, or adds a new SaaS integration. That’s why assessment needs to be continuous, automated, and contextual.
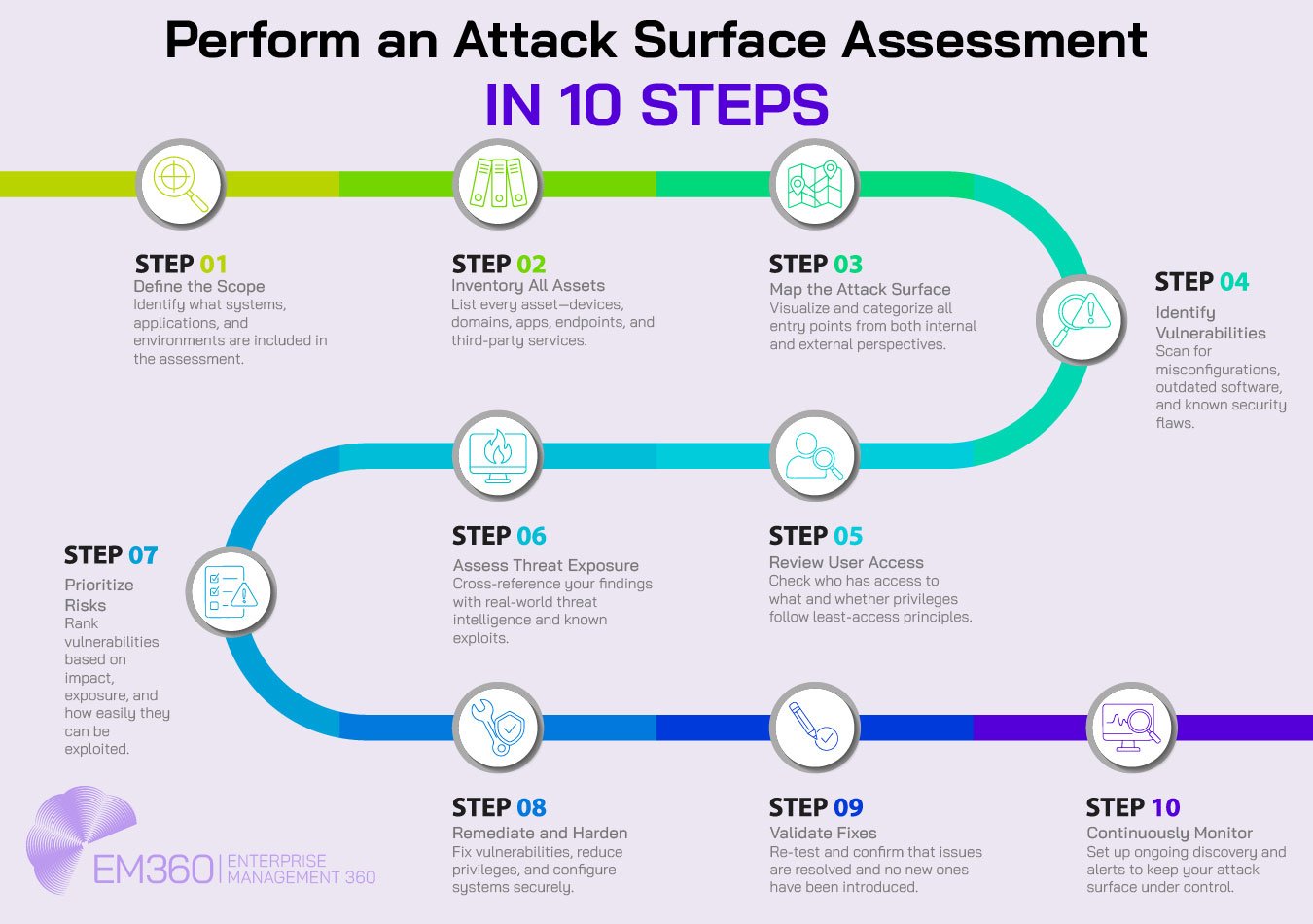
Here’s what a mature attack surface assessment typically involves:

Managing Cloud Risk with Prowler
Misconfigurations, weak IAM and exposed services raise breach risk; Prowler ranks issues by severity and maps fixes to GDPR, HIPAA and SOC 2 demands.
- Asset discovery: First, identify every internet-facing and internal-facing asset — including shadow IT, orphaned domains, misconfigured cloud resources, and exposed APIs. Tools with external scanning capabilities can uncover assets that internal teams may have overlooked.
- Vulnerability and exposure analysis: Determine not just what assets exist but which ones present real risk. This includes known Common Vulnerabilities and Exposures (CVEs), expired certificates, open ports, or weak authentication mechanisms.
- Attribution and ownership mapping: Assign each asset to a responsible team or owner. Knowing who “owns” a risk is essential for driving timely remediation and accountability across departments.
- Risk scoring and prioritisation: Not all exposures are equal. Prioritise assets based on likelihood of exploitation, sensitivity of the system or data involved, and potential business impact. This is where contextual risk intelligence — including threat intel and business logic — becomes invaluable.
- Change monitoring and alerting: Establish a feedback loop that alerts your security team when new assets appear, configurations change, or previously remediated vulnerabilities resurface. This is the foundation for real-time visibility and continuous improvement.
Importantly, effective assessment isn’t just about data collection — it’s about creating a living inventory of risk that’s tied to business operations. That means integrating ASM with your existing Security Information and Event Management (SIEM), Configuration Management Database (CMDB), and vulnerability management workflows so insights can drive action.
Determining Your Attack Surface
Assessments are one thing — visibility is another. Knowing where your organisation is most vulnerable starts with identifying the full scope of assets, connections, and behaviours that make up your unique attack surface. This process isn’t about cataloguing every system for the sake of documentation. It’s about gaining clarity on where risk lives — and where it’s most likely to spread.
Here’s how to start uncovering that reality.
Map known assets and shadow IT
Begin with what you think you know: your documented assets, internal inventories, and CMDB entries. But don’t stop there — in most organisations, these databases are outdated before the month is out. New assets spin up during product sprints. Marketing teams adopt new tools without looping in IT. Cloud services replicate across regions. And just like that, your shadow IT footprint expands.
Use external scanning tools to identify internet-facing assets that aren’t tracked internally. Look for rogue subdomains, unmanaged endpoints, forgotten SaaS accounts, and anything outside your known inventory. If it’s connected to your business, it’s part of your attack surface — even if no one’s claimed responsibility for it.
Classify assets by risk and ownership
Once you’ve uncovered what’s out there, the next step is to understand what it all means. That starts with classifying each asset by:
Inside Evil Corp's Cyber Empire
How a Russian-led syndicate industrialized bank fraud and ransomware, and what boards must demand from security teams to blunt its impact.

- Business criticality: What systems store customer data, financial records, or intellectual property (IP)?
- Exposure level: Is the asset public-facing, behind authentication, or internal-only?
- Known vulnerabilities: Are there any high-risk CVEs associated with the tech stack?
- Owner accountability: Which team or individual is responsible for its maintenance and security?
Establishing ownership is critical — not just for security, but for response. When something breaks, you need to know exactly who’s accountable for fixing it.
Look at external and internal exposure
Think like an attacker. What can they see? What systems are exposed from the outside? That’s your external attack surface — and it’s often far broader than expected, especially in cloud-native or hybrid environments.
But don’t overlook your internal exposure. Legacy systems, over-permissioned accounts, internal APIs, and shared development environments can all become lateral movement paths once an attacker gets inside.
The best ASM programmes combine both perspectives: the attacker’s view (what can be probed or discovered externally) and the defender’s view (what lives inside your environment and how it’s secured).
Don’t overlook the human layer
The most commonly missed part of the attack surface isn’t code — it’s people.

Consider the employee who reuses the same password across tools. The contractor whose access wasn’t revoked. The manager who unknowingly clicks a credential-harvesting link in a realistic-looking calendar invite. Every one of these is a potential entry point.
This layer includes:
- Unsecured or abandoned accounts
- Poor MFA adoption
- Social engineering risks (phishing, pretexting, vishing)
- Insider threats — accidental or deliberate
A true picture of your attack surface has to include the human layer. Because even the best technical controls mean nothing if someone lets the attacker walk through the front door.
Importance of Attack Surface Management
Attack surface management isn’t just a cybersecurity best practice — it’s an operational imperative. As the number of digital assets, integrations, and third-party connections grows, so too does the opportunity for exploitation. And in today’s environment, the speed of your visibility often determines the scope of your exposure.
Here’s why ASM matters now more than ever.
Risk reduction
The broader your attack surface, the harder it is to defend. But that doesn’t mean the answer is to lock everything down. The real goal of ASM is to give you smart visibility — so you can reduce risk without slowing innovation.
By continuously monitoring and managing your attack surface, you can:
- Spot vulnerable or misconfigured assets before they’re exploited
- Eliminate redundant or outdated systems that no longer serve the business
- Reduce lateral movement paths that attackers could use once inside
- Focus your security spend on the areas of greatest impact
Risk reduction through ASM isn’t about adding another layer of control. It’s about giving your existing security tools and teams the context they need to work better — faster.
Proactive threat identification
Most breaches don’t happen because a vulnerability was too complex to fix. They happen because no one knew it was there in the first place.
ASM shifts your security posture from reactive to proactive by:
- Continuously scanning for new or exposed assets
- Surfacing unknown entry points attackers could exploit
- Alerting teams when risk thresholds are exceeded — in real time
- Providing an attacker’s-eye view of your organisation at any moment
This kind of proactive detection reduces mean time to remediation (MTTR), improves incident response readiness, and helps security teams avoid blind spots that traditional vulnerability scans often miss.
Compliance and reporting
Visibility isn’t just a security issue — it’s a regulatory one. Whether you're operating under GDPR, HIPAA, PCI-DSS, or industry-specific frameworks, most compliance mandates now require demonstrable asset control, risk management, and breach prevention protocols.
ASM supports compliance efforts by:
- Generating up-to-date inventories of exposed assets
- Documenting the lifecycle of discovered vulnerabilities
- Supporting access control and privilege management audits
- Offering exportable logs and dashboards for audit-readiness
For leadership, this means fewer surprises and stronger alignment between security outcomes and business obligations. For security teams, it means less scrambling before audits and more confidence in everyday operations.
The Role of Continuous Monitoring in ASM
Your attack surface doesn’t wait for your next audit — and neither do attackers.
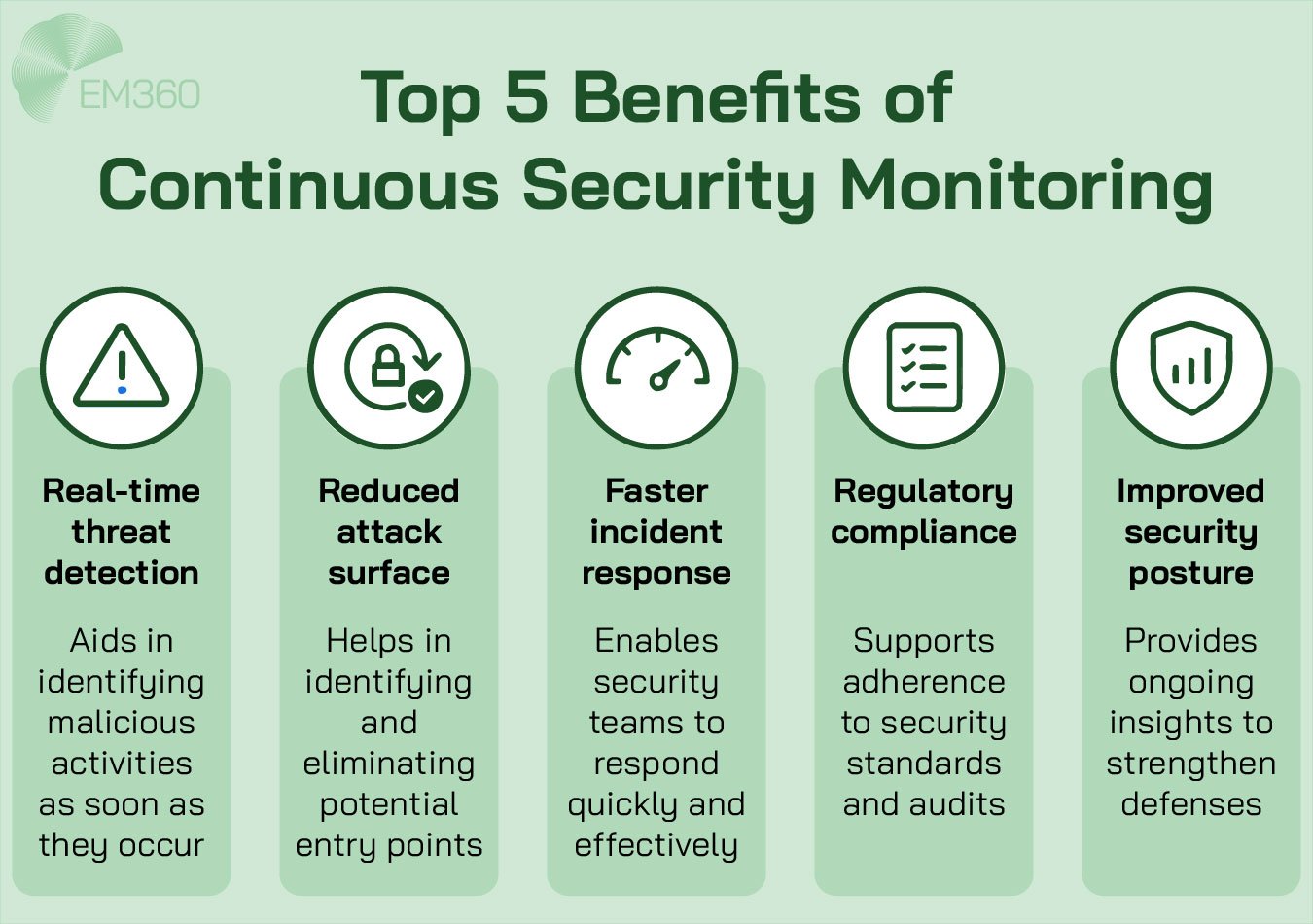
As organisations scale and evolve, their digital environments shift by the hour. Developers push new code. Marketing teams launch campaign microsites. Shadow IT spins up trial tools in the cloud. Every change introduces potential risk. And if you’re only scanning quarterly or even monthly, you’re already behind.
That’s where continuous monitoring comes in.
ASM powered by continuous monitoring gives security teams real-time visibility into how the attack surface is expanding, shifting, and responding to internal change or external threats. So instead of a static snapshot, your ASM policy becomes a dynamic feedback loop.
With continuous monitoring, you’re able to:
- Detect new assets as soon as they join your ecosystem — even if they’re untracked, unmanaged, or misconfigured
- Identify harmful changes to existing systems — such as an expired TLS certificate or a firewall rule that’s been configured incorrectly
- Monitor for signs of malicious activity — this would include checking for things like port scanning, credential stuffing, or enumeration attempts
- Track your remediation efforts and validate their outcomes — and also provide proof of closure once previously flagged issues are resolved
But continuous doesn’t just mean constant — it means automated, prioritised, and contextualised. The best ASM platforms integrate with SIEMs, Security Orchestration, Automation, and Response (SOAR) platforms, and vulnerability management tools to provide not just alerts, but also insight. They’ll tell you what changed, why it matters, and who should respond to the threat.
Dwell time is measured in minutes, not days, so continuous monitoring isn’t a nice-to-have — it’s your frontline defence. It makes sure that no blind spot goes unnoticed, no misconfiguration lingers too long, and no attacker has the luxury of time.
Popular Tools and Vendors for ASM
Attack surface management isn’t something that spreadsheets or static scans can really handle — at least, not anymore. As digital estates grow more dynamic and decentralised, organisations have started relying on specialised platforms that can automate discovery, contextualise risk, and integrate with existing security workflows more and more.
Whether you’re evaluating vendors or exploring open-source options, understanding the landscape is key.
Open-source vs. commercial options
Open-source tools can be a powerful starting point — especially for smaller organisations or those looking to test what ASM tools are capable of before making a larger investment. Tools like Amass, Recon-ng, and Shodan are often used for external reconnaissance and subdomain enumeration, offering visibility into publicly exposed assets.
But while open-source tools are flexible and cost-effective, they often require:
- Manual tuning and scripting
- Security expertise to interpret results
- Separate integrations for reporting, alerting, and automation
Commercial ASM platforms, on the other hand, offer broader coverage and deeper context. They’re designed to:
- Continuously scan both external and internal environments
- Correlate data with threat intelligence feeds
- Integrate with SIEM/SOAR, ticketing, and asset management systems
- Provide dashboards and alerts tailored to business risk
Leading vendors in this space include:
- CyCognito: Known for its attacker-centric view of the external attack surface
- CrowdStrike Falcon Surface: Focuses on visibility and continuous discovery
- Tenable.asm: Offers integration with vulnerability management and cloud security tools
- Qualys ASM: Pairs asset discovery with detailed configuration and compliance data
- Microsoft Defender EASM: Ideal for organisations that are already using other tools in the Microsoft ecosystem
- Hadrian: Automates external attack surface discovery with hacker-like reconnaissance and real-time threat validation
Choosing between open-source and commercial solutions often comes down to scale, maturity, and internal expertise.
Selection criteria
No two organisations have the same digital footprint — and no single ASM tool will be perfect for everyone. That’s why it’s critical that the tool you choose aligns with both the reality of your day-to-day operations and your business priorities.
Here are a few key criteria to guide the decision:
- Scope of discovery: Does the tool find both known and unknown assets? Can it handle hybrid or multi-cloud environments?
- Data accuracy: Are findings validated and prioritised based on real-world risk — or just flagged generically?
- Integration depth: Can it feed data into your SIEM, ticketing system, vulnerability management platform or the rest of your tech stack?
- User access and usability: Is it built for security teams alone, or is it something that your IT, DevOps, and risk teams can also use?
- Automation capabilities: Does the platform offer alert triggers, can it auto-classify new and existing assets, and does it support your existing remediation workflows?
The right tool looks different to everyone, but ultimately it’s the one that gives you the clearest view of your attack surface as it evolves — and helps your teams work together to quickly and confidently act on that insight.
Real-World Use Cases of ASM
Attack surface management isn’t just a theoretical framework — it’s solving real problems for real businesses every day. From securing hybrid environments to supporting digital transformation, ASM provides the visibility and responsiveness that modern operations demand.
Here are just a few of the ways organisations are applying ASM to drive meaningful security outcomes.
Supporting enterprise digital transformation
As businesses modernise their infrastructure, migrate workloads to the cloud, and adopt new SaaS platforms, their attack surfaces expand — often in unpredictable ways. ASM helps security teams keep up with this transformation by:
- Continuously mapping new assets as they’re created
- Identifying high-risk misconfigurations before they become liabilities
- Simultaneously maintaining visibility across legacy and next-gen environments
This is especially critical during mergers and acquisitions, when digital estates double overnight and inherited vulnerabilities can easily slip through the cracks.
Enhancing cloud security posture
In multi-cloud environments, even small configuration errors can open large vulnerabilities. ASM tools give organisations the ability to:
- Detect unsecured storage buckets or exposed services
- Validate cloud asset ownership and permissioning
- Spot shadow cloud environments spun up outside governance frameworks
By surfacing these risks in near real-time, ASM enables teams to take corrective action before misconfigurations are discovered by attackers — or auditors.
Reducing supplier and third-party risk
Every vendor you connect to widens your attack surface. ASM supports third-party risk management by:
- Identifying externally exposed integrations or APIs
- Highlighting inherited vulnerabilities via software supply chain connections
- Monitoring digital assets tied to subsidiaries or outsourced development teams
This extended visibility is crucial as supply chain attacks continue to rise, often bypassing traditional perimeter defences altogether.
Strengthening breach response and investigation
When a security incident occurs, time is everything. ASM accelerates incident response by:
- Providing a live map of the organisation’s exposed assets
- Helping teams understand potential entry points and paths of lateral movement
- Validating whether a compromised asset is known, managed, or entirely rogue
This context can shave critical hours — even days — off the investigation timeline, reducing impact and improving coordination with Incident Response (IR) teams, regulators, and executives.
Other Frequently Asked Questions About ASM
Even with a solid understanding of attack surface management, some questions still come up time and again — especially from business leaders trying to connect technical priorities to real-world impact. Here are some of the most common ones.
What is ASM in cybersecurity?
ASM — or Attack Surface Management — is a cybersecurity practice focused on identifying, monitoring, and managing all potential entry points that a threat actor could exploit. It includes digital, physical, and human-facing assets, whether known or previously unknown.
What is the difference between ASM and EASM?
ASM refers to the overall strategy of managing an organisation’s attack surface, both internally and externally.
EASM (External Attack Surface Management) is a specific subset that focuses solely on internet-facing assets — the parts of your environment visible to attackers from the outside. Think of EASM as a zoomed-out, attacker’s-eye view of your digital footprint.
What is the difference between ASM and CSPM?
ASM looks at your entire attack surface, across all vectors — digital, physical, and human.
CSPM (Cloud Security Posture Management) is a toolset specifically designed to identify and fix misconfigurations in cloud environments. CSPM is often one piece of a broader ASM strategy.
Is ASM the same as vulnerability management?
Not quite. Vulnerability management identifies and remediates weaknesses in known assets. ASM, by contrast, helps you discover all assets, including those not previously tracked, and then prioritises risk exposure — which may or may not include known vulnerabilities. ASM expands your awareness; vulnerability management helps you act on it.
How often should you assess your attack surface?
Continuously — or as close to it as possible. Since digital environments evolve constantly, point-in-time assessments leave gaps that attackers can exploit. That’s why leading ASM solutions operate in real time, offering live visibility into what’s changing and where new risk is emerging.
Who is responsible for attack surface management in an organisation?
While security teams typically lead ASM efforts, the responsibility is shared. IT teams, DevOps, compliance, and even marketing or product functions can all introduce risk. A successful ASM programme includes cross-functional collaboration, asset ownership, and clear accountability.
Can ASM be fully automated?
Some parts of ASM — like asset discovery, change detection, and alerting — can be highly automated. But interpretation, prioritisation, and remediation still require human oversight. The most effective programmes combine automation for scale with human judgement for context.
Final Thoughts: Adopt a Security-First Approach
As digital transformation accelerates, the ability to see — and secure — your entire attack surface has never been more critical. Attack Surface Management isn’t just a toolset; it’s a shift in mindset. It’s how forward-thinking organisations are reducing risk, improving responsiveness, and building cyber resilience into every layer of their operations.
To stay ahead of the curve, explore more expert insights, real-world case studies, and tech leader perspectives right here at EM360Tech.







Comments ( 0 )