For many enterprises, Web3 has quietly moved from experiment to strategy. It sits behind pilots in digital identity, tokenised assets, supply chain traceability and data sharing. The promise is compelling. Web3 offers a way to give users more control over data, reduce reliance on central intermediaries and build applications that can move value and information across ecosystems with far less friction.
The security equation, however, looks very different from traditional environments. Trust rests on cryptographic keys rather than accounts and passwords. Transactions are irreversible. Smart contracts execute business logic automatically, and a single line of code can move millions. Much of the infrastructure still runs on Web2 components, from web front ends to APIs and cloud platforms, that remain attractive targets for attackers.

Put simply, Web3 security is not a niche concern for crypto projects. It is a core element of enterprise risk. If organisations want to unlock value from Web3 without inheriting unmanageable exposure, security leadership has to treat it as a shift in data, identity and operations, not just a new technology stack.
What Web3 Security Means for Today’s Enterprise
At its core, Web3 is a different way of structuring applications and data. Instead of central platforms holding everything on behalf of users, Web3 spreads trust across blockchain security primitives, decentralised identifiers and smart contracts that run shared logic between participants.
Authorities like NIST frame Web3 as a shift in how trust and data ownership work. Instead of relying on central platforms, users hold their own cryptographic keys and decide how their information is shared. The applications built on top of this blend on-chain logic with off-chain storage and interfaces, so the stack still looks familiar even though the trust model has changed underneath it.
For an enterprise, the Web3 security picture is less about the underlying protocols and more about what those protocols demand from your organisation. You need confidence that the contracts running your business rules cannot be tampered with. You need a disciplined approach to keys and wallets because they function as the ultimate source of authority.
You need to know that data moving between chains, applications and internal systems stays authentic from end to end. And you need governance and response processes that hold up when transactions cannot be reversed and mistakes become visible to everyone.
In other words, it’s less about speculative assets and more about secure architecture for distributed systems that may span multiple chains and cloud environments. And before leaders can design controls, they need to understand how this reshapes the attack surface they are used to defending.
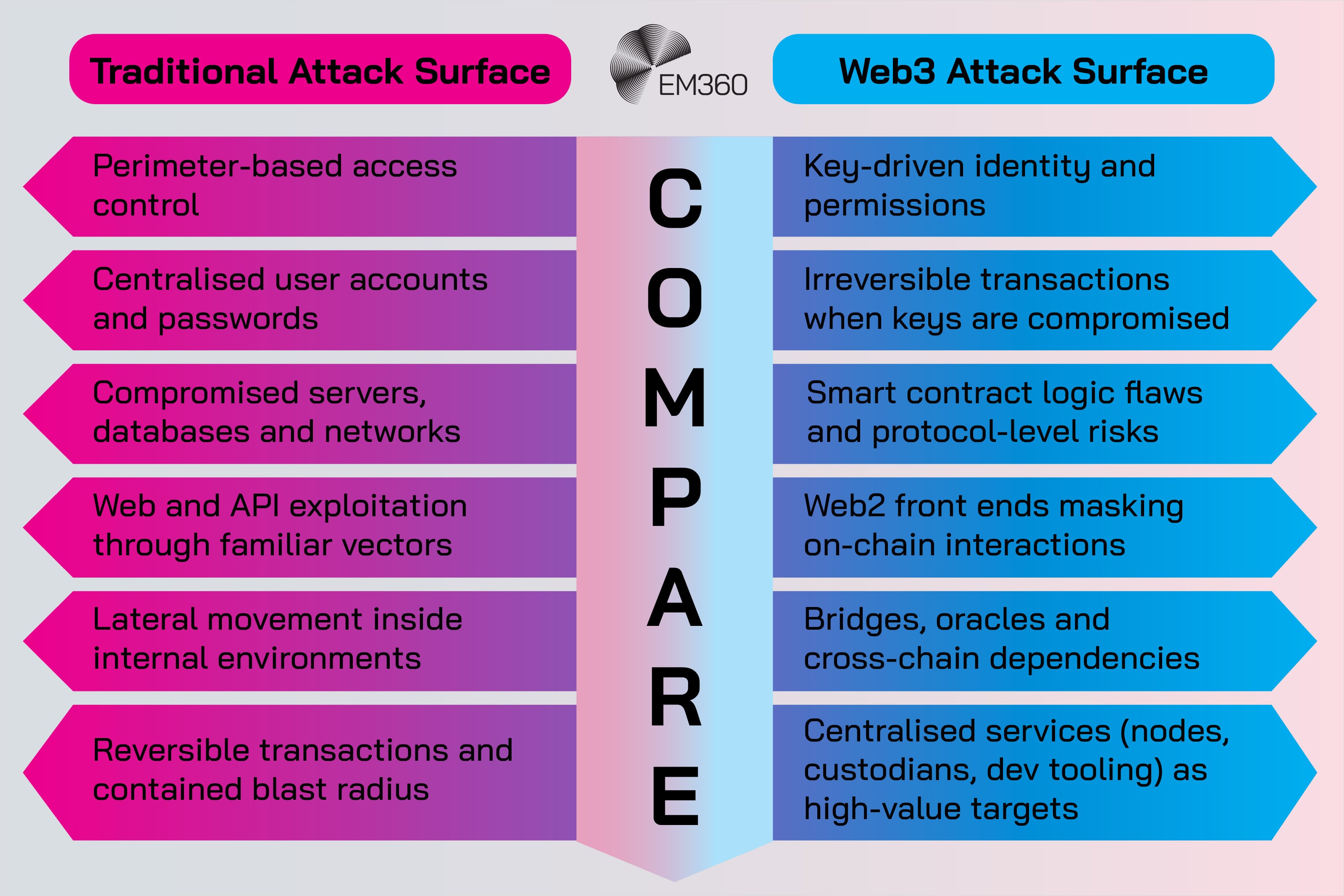
How Web3 Changes the Traditional Attack Surface
Traditional security models were built around networks, applications and users sitting either inside or outside a perimeter. Web3 changes that framing. Trust moves closer to the edge. The most sensitive asset becomes the cryptographic key that proves ownership and authorises action.
Instead of centralised sessions, wallets sign transactions that are broadcast to the network. A compromised wallet can drain assets, modify control over contracts or alter governance decisions in a way that cannot be undone. That makes private key management a board-level concern, not a technical detail.
Composability introduces another shift. Web3 applications often chain together multiple contracts and services. A flaw or misconfiguration in one component can cascade across others, creating business logic risks that are difficult to see through a traditional application lens.
For security leaders, this means:
- Thinking in terms of access control vulnerabilities in smart contracts and protocols, not only in web servers and databases.
- Treating wallet security and policies for multisignature (“multisig”) arrangements as part of core identity and access management.
- Recognising that contracts, bridges and oracles behave like new classes of infrastructure that need continuous assurance, not one-off reviews.
The perimeter has not disappeared, but it now shares centre stage with key-driven trust and shared logic that spans organisational boundaries.

When AI Agents Reshape Security
Why boards must treat autonomous agents as governance choices and redesign controls around authority, identity, and blast radius.
The Risks That Matter Most To Enterprise Security Leaders
The industry has now lived through several years of real incidents across exchanges, protocols and wallets. The data tells a clear story. The biggest losses do not come from exotic cryptographic failures. They come from keys, access controls and flawed logic.
Global Web3 reports from specialist firms show that a significant share of 2024’s stolen value flowed from key compromise and access control issues, not just traditional vulnerabilities. Major intelligence providers highlight that a large portion of overall losses can be traced back to private keys that were stolen, mismanaged or abused by insiders.
Smart contract weaknesses remain common, but many of the most damaging attacks exploit errors in how those contracts are wired into larger systems.
In parallel, infrastructure and centralised services such as exchanges, custodians and third-party tools continue to absorb some of the largest single incidents. Attackers target the points where Web3 and Web2 meet, from admin interfaces and CI/CD pipelines to cloud consoles.
For an enterprise, the practical picture looks like this:
- Keys and access policies sit at the heart of Web3 risk.
- Smart contracts and bridges extend the potential blast radius of any failure.
- Web2 front ends and APIs remain attractive, familiar targets.
- Supply-chain compromise of vendors and remote workers can translate directly into wallet and infrastructure compromise.
Security leaders who treat Web3 as “just another app” will miss where the real exposure lies.
Keys, Access Control and Human-Driven Compromise
Keys are the single point where cryptography meets human behaviour. When those keys are compromised, the consequences are immediate and public.
Inside Zero Trust Network Design
Break down how SSE, SASE and ZTNA vendors rewire connectivity, from device posture checks to microsegmentation across hybrid and multi-cloud.

Recent years have seen high-profile cases where individual wallets, treasury accounts and multisig arrangements were abused. In many of those, attackers did not break the underlying cryptography. They obtained keys through phishing, malware on developer machines, compromised build pipelines or abuse of internal privileges. The result was the same: drains of high-value assets that could not be reversed.
To reduce the impact of private key compromise, enterprises need to treat wallets and signing infrastructure as privileged systems. That means:
- Strong separation of duties between operational staff, signers and developers.
- Clear policies that define who can hold keys, what they can authorise and under what conditions.
- Multisig structures that require more than one person or system to approve high-risk transactions, backed by robust multisig governance rather than ad hoc arrangements.
- Hardware-backed wallets and secure enclaves for critical roles, reducing exposure to commodity malware.
Access control is no longer just RBAC in an application. It is the combination of key custody, transaction policies and monitoring that determines whether a single compromise becomes a catastrophic incident.
Smart Contract and Business Logic Failures
Smart contracts sit at the centre of many Web3 applications. They hold funds, control protocol parameters and enforce agreement rules. When they fail, they fail in public.
Industry reports still show smart contract vulnerabilities as one of the most frequent causes of loss. What is changing is the nature of those flaws. Many damaging incidents are now driven less by simple bugs and more by business logic vulnerability. The contract does exactly what it was coded to do, but the rules themselves are incomplete or exploitable in ways the designers did not anticipate.
Examples include:
- Reentrancy patterns that allow attackers to drain funds by repeatedly calling withdrawal functions.
- Oracle manipulations where contracts trust a single price feed that can be skewed.
- Incentive structures that let attackers profit by moving markets around protocol assumptions.
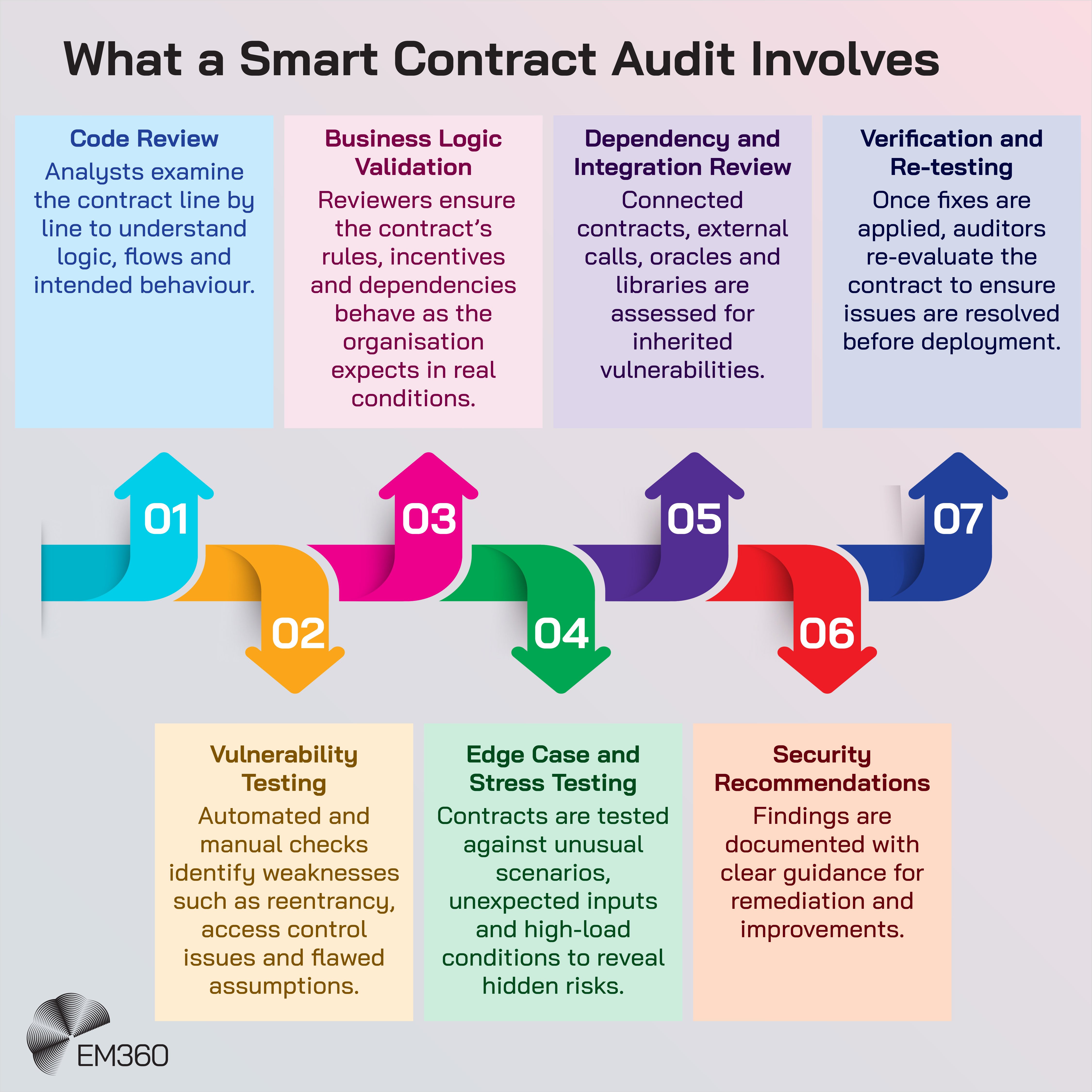
A traditional smart contract audit remains essential, but it is not enough. Contracts need ongoing assurance. That includes regression testing when logic changes, continuous scanning for known antipatterns and the use of formal verification tools where the stakes justify the investment.

Mitigating Breach Risk with MFA
Quantify how layered verification reduces account takeover exposure, and what to demand from vendors to address SMS, token and biometric weaknesses.
For enterprises, contract security should be treated like any other mission-critical system. It needs lifecycle management, not a one-time signoff.
Web2 Front Ends and API Weak Links
Most Web3 users never touch a blockchain node directly. They interact through web applications, mobile apps and APIs. Those surfaces look and behave like any other internet-facing service, which makes them familiar territory for attackers.
Security firms have highlighted multiple incidents where attackers bypassed on-chain controls entirely by compromising web front ends, DNS records or build pipelines. Users believed they were interacting with a legitimate application, but their actions were being proxied or modified.
On the API side, calls to node gateways and backend services are sometimes left unauthenticated or rely on static keys that are easy to leak. That turns API security and request signing into a critical part of Web3 risk management.
Enterprises should expect to:
- Apply layered controls such as WAF, bot mitigation and strong API authentication on all Web3-facing web properties.
- Treat connections between Web2 front ends and Web3 back ends as sensitive, using secure API delivery platforms and signed requests to reduce tampering.
- Harden node gateways and RPC endpoints, especially when they support internal applications or customer-facing services.
The attack surface is not confined to contracts and chains. It runs through the same web technologies attackers have been abusing for years.
Centralised Platforms and Supply-Chain Exposure
While Web3 is often framed as decentralised, many real-world deployments still rely heavily on centralised platforms. Exchanges, custodians, cloud providers, developer tools and infrastructure vendors all sit in the path of critical flows.
Several of the largest single incidents in recent years have involved centralised services such as exchanges and custodial platforms. Others have stemmed from compromised libraries, CI/CD pipelines or build systems that injected malicious code into widely used components.
For enterprises, this creates a familiar but sharper supply-chain challenge:
When AI Agents Run the Enterprise
How autonomous ChatGPT-style agents are shifting enterprise operating models and why governance now decides productivity gains or chaos.
- A compromise at a vendor can translate directly into infrastructure risk, affecting wallets, nodes or front ends.
- Remote developers and contractors with elevated access may be targeted by state-aligned actors, then used as a bridge into production systems.
- Custody arrangements have to be assessed not just on financial and regulatory grounds, but on technical controls and incident response maturity.
Security teams must treat vendor and platform selection as part of Web3 risk mitigation, not only a commercial decision.
How Enterprises Should Approach Web3 Security
Given this landscape, enterprises need more than a checklist. They need a coherent approach that connects architecture, governance and day-to-day operations.
At a minimum, any organisation moving into Web3 should treat Web3 security audit work as one element in a broader security programme that aligns with existing frameworks. The goal is not to reinvent security from scratch, but to adapt familiar risk management disciplines to a model where keys, contracts and cross-chain flows play a central role.
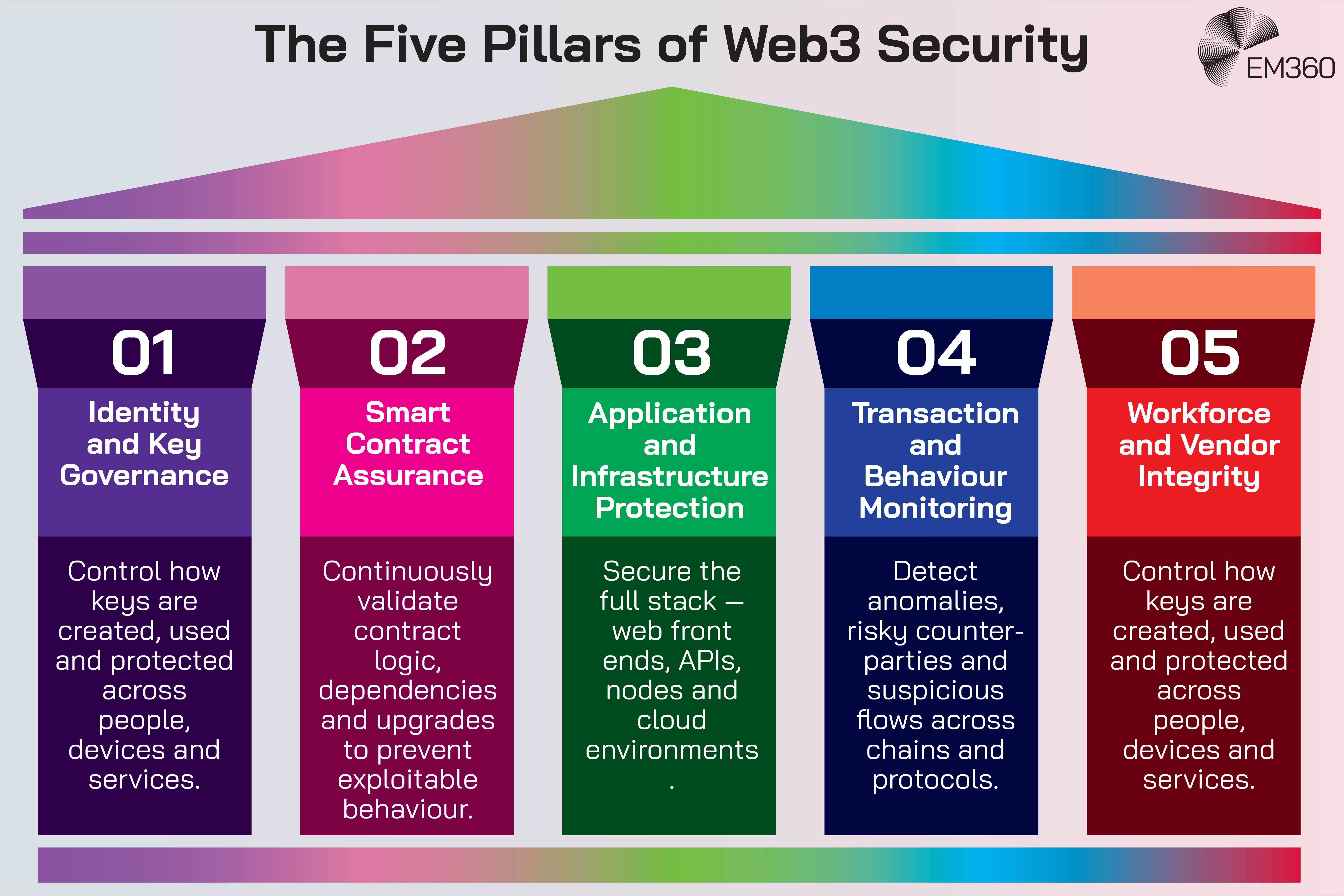
A practical enterprise approach rests on five pillars:
- Governance around identity and keys.
- Lifecycle management for smart contracts.
- Layered protection across the application stack.
- Strong fraud, AML and transaction monitoring.
- Workforce and vendor integrity as explicit controls.
Each of these has to be designed for the realities of distributed applications and shared infrastructure.
Build Governance Around Identity and Keys
Identity and access management has always been central to security. Web3 raises the stakes. Anyone with the right private key can act on behalf of the organisation.
Stronger identity and access management for Web3 starts with clear wallet governance:
- Define classes of wallets, from low-risk operational accounts to high-risk treasury and governance wallets.
- Establish policies for provisioning, rotation and revocation of keys across employees, devices and services.
- Implement transaction policies that set limits by value, asset, destination and context, with multi-party approvals for sensitive actions.
- Use decentralised identity and verifiable credentials to tie roles and permissions to cryptographic proofs rather than fragile manual processes.
This is not just about keeping seed phrases safe. It is about treating wallets and keys as part of the core identity fabric of the organisation, with the same discipline applied to admin accounts in traditional systems.
Treat Smart Contracts as Living Systems
Smart contracts should not be treated as “fire and forget”. Once they hold value or enforce critical workflows, they become living components of the enterprise architecture. So a mature security approach treats smart contracts the same way you treat any system that carries real business risk. They need more than a once-off audit. They need ongoing care.
That starts with a deep initial review of the code and the logic behind it, supported by the right tools for the job. Once those contracts go live, every change deserves the same scrutiny, whether it is a parameter tweak or a full upgrade.
From there, the focus shifts to how the contract behaves over time. On-chain activity tells its own story, and subtle patterns often surface long before anything breaks in a visible way. Monitoring those signals is how teams catch issues early, especially when a failed transaction or an unusual sequence hints at a vulnerability developing underneath.
The development work around the contract matters just as much. Secure coding, peer review and clear standards need to apply to the underlying business rules, not only the technical implementation. Smart contracts are automated commitments. If the logic behind them is flawed or incomplete, the code will simply enforce those flaws at scale.
The aim here is code assurance over time, not a one-off report that rapidly drifts out of date.
Secure the Full Application Stack
Enterprise Web3 deployments rarely exist in isolation. They sit alongside existing applications, APIs and services. A secure design acknowledges that and applies layered controls across the entire stack.
That includes:
- Traditional application security controls at the web and mobile layers, including WAF, bot management and robust authentication.
- Strong API authentication between front ends, back ends and node gateways, using mutual TLS, signed requests or token-based schemes that minimise key leakage.
- Hardened node infrastructure, with access controls, logging and monitoring that align with other critical systems.
- Segregation of environments so that development and testing nodes cannot be used as stepping stones into production.
When viewed through this lens, Web3 becomes one more layer in a broader security architecture, not a separate universe.
Strengthen Fraud, AML and Transaction Monitoring
Web3 changes how financial crime shows up inside an organisation. The movement of funds is public and verifiable, yet attackers have become skilled at hiding those movements through cross-chain hops and fast-moving obfuscation techniques. That combination creates a strange tension for enterprises. You have more visibility than ever, but only if you have the right systems to interpret it.
For organisations handling high-value activity on-chain, transaction monitoring needs to sit alongside other core risk functions, not apart from them. On-chain analytics help surface early signs of trouble by highlighting interactions with wallets tied to scams, sanctioned actors or known laundering patterns.
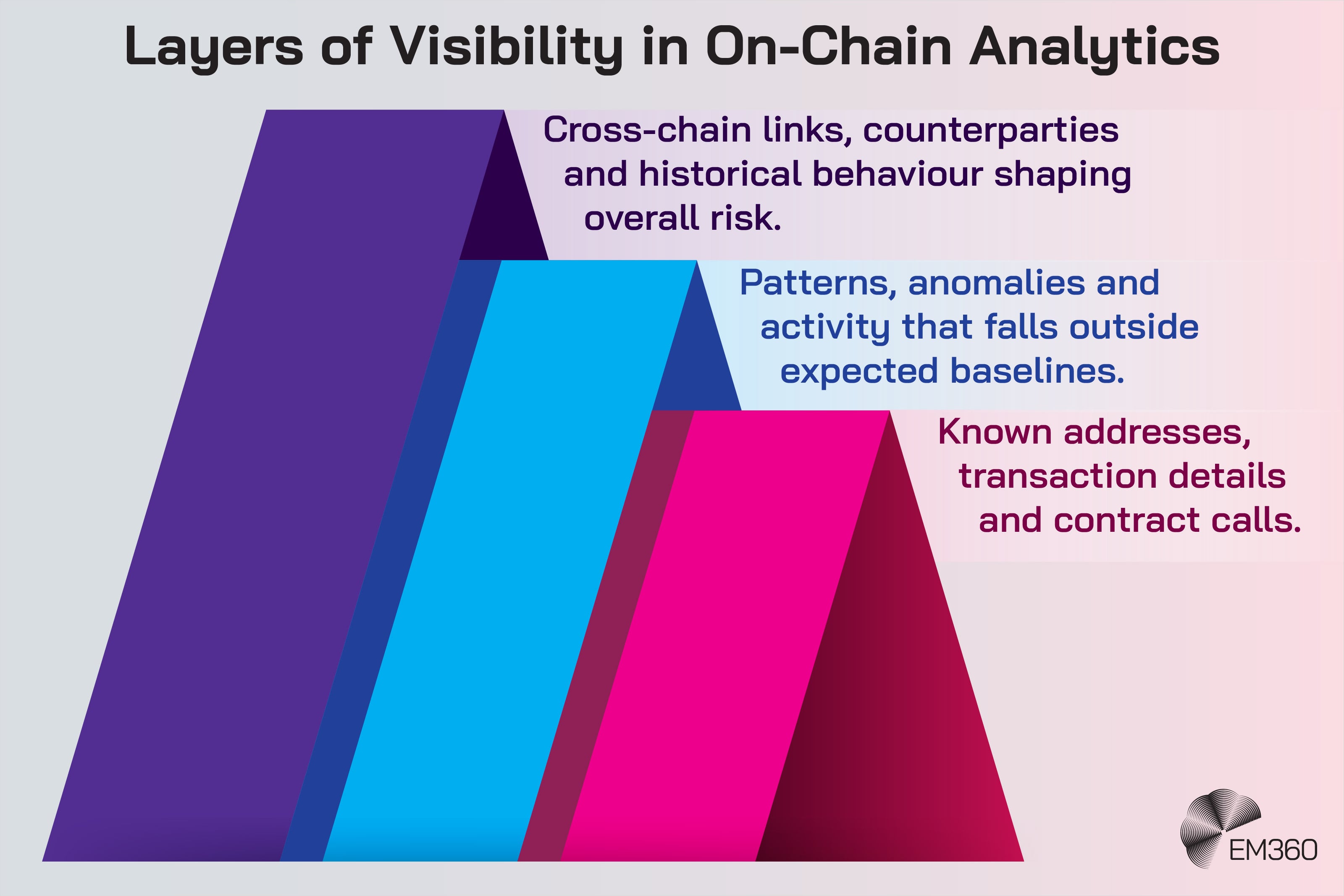
That insight becomes more effective when it’s tied back into your existing financial crime processes, giving teams a single picture of risk rather than two disconnected streams of information.
The same applies to approvals. High-impact transactions benefit from KYT-style checks that assess context and counterparties before anything is signed. Real-time signals from user behaviour, backend logs and blockchain events can also reveal subtle anomalies that would never appear in manual reviews.
This level of visibility matters to regulated institutions, but the operational value goes far beyond compliance. Any enterprise moving meaningful value on-chain needs the ability to see risk forming early, not after the damage has already settled into the ledger.
Treat Workforce and Vendor Integrity as a Security Control
Attackers have learned that it is sometimes easier to target people and vendors than code. Security intelligence reports have documented cases where state-aligned actors posed as remote developers, gained employment at Web3 firms and then abused their access to compromise infrastructure and keys.
Enterprises should build workforce and vendor integrity into their control set:
- Tighten background checks and identity verification for staff and contractors with elevated access to wallets, keys or infrastructure.
- Limit vendor access to the minimum required and monitor activity carefully, especially for third parties involved in development and DevOps.
- Include Web3-specific questions and tests in vendor due diligence, covering key custody, incident response, internal controls and previous security history.
- Treat vendor risk and workforce security as integral parts of the Web3 security programme, not separate HR or procurement issues.
People and suppliers can be either a strong line of defence or the path an attacker chooses. The policies you set determine which.
The Role of AI and Automation in Web3 Security
Web3 moves fast. Contracts call other contracts. Value shifts across chains in seconds. Attackers adapt quickly because the environment rewards anyone who gets there first. That pace alone makes manual monitoring unrealistic, which is why so many security teams are turning to AI and automation to keep up.
Modern tooling is starting to act less like static scanners and more like continuous sentinels. Some systems analyse code with models trained on thousands of past vulnerabilities, surfacing patterns that look harmless in isolation but risky when viewed in context. Others focus on live behaviour, learning what normal activity looks like for a protocol and calling attention to anything that falls outside that baseline. The goal is simple. Catch the signal before it becomes the story.
For enterprises, the value shows up in very practical ways. It reduces the burden on specialist talent that cannot be everywhere at once. It fills the gaps between scheduled reviews, where most incidents tend to happen. And it gives teams a broader view of low-frequency, high-impact risks that no one would realistically pick up through manual checks alone.
AI will not replace good architecture or disciplined governance, but it strengthens continuous monitoring and shortens the time between compromise and response. In Web3, that difference matters. Once an attacker moves, there is no rollback button waiting in the background.
From Point-in-Time Audits to Continuous Assurance
The biggest shift for enterprises is moving away from occasional audits toward an always-on model of assurance. Web3 environments evolve too quickly for periodic testing to offer real protection. By the time a point-in-time assessment lands, the system it reviewed may already look different.
Newer platforms are closing that gap. They track contract behaviour and protocol states in real time, flagging activity that falls outside expected patterns. They enforce policies automatically, limiting what a contract or wallet can do when risk conditions change. And they give security teams a consolidated view of how exposure is shifting across chains, nodes and front ends.
This mirrors the direction of broader application security, but Web3 raises the stakes. Transactions cannot be reversed, and mistakes are public the moment they occur. The organisations that adapt early gain something invaluable: time. Time to detect, time to intervene, time to contain a problem before it becomes irreversible.
For enterprises, that shift turns Web3 from a reactive scramble into a more predictable, manageable part of the technology landscape.
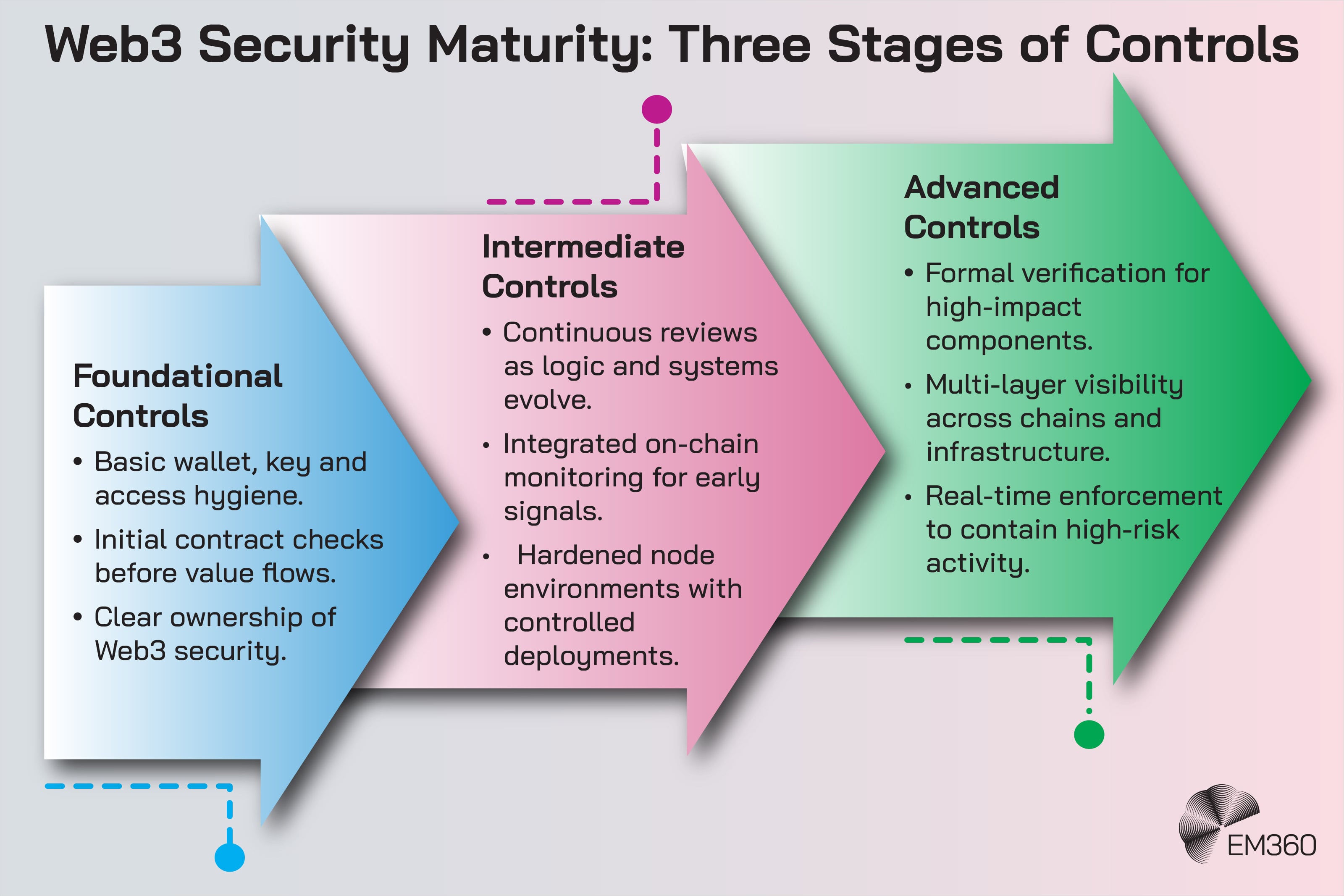
A Practical Web3 Security Maturity Path for Enterprises
Every organisation enters Web3 from a different place. Some are still running small experiments. Others already have customer transactions or internal processes tied to on-chain components. Progress does not need to be perfect. It just needs to move in the right direction.
A simple maturity path helps teams understand where they stand today and what should come next as risk and responsibility scale.
Foundational Controls
The foundational stage is about supporting early use cases without exposing the organisation to unnecessary risk. It blends familiar security fundamentals with the realities of Web3.
Typical characteristics include:
- Clear wallet policies for staff and contractors, supported by sensible device hygiene and reliable backup procedures.
- Basic access controls for nodes, APIs and admin interfaces, reducing the chance that development shortcuts spill into production.
- Initial smart contract assessments for any code that will hold value or enforce important business rules.
- Defined ownership for Web3 security inside the organisation, even if it is a small team or a single accountable lead.
This level is suitable for pilots and low-risk experiments. It is not designed for large balances or critical processes, but it gives the organisation a safer starting point.
Intermediate Controls
Once Web3 becomes part of day-to-day operations, the focus shifts to consistency and scale. The aim is to make security practices repeatable, visible and integrated into existing workflows.
Intermediate controls often include:
- Regular continuous audit cycles for contracts and configurations, especially when business logic or parameters change.
- Integrated transaction monitoring that feeds into existing SOC or fraud teams, giving them a clearer view of on-chain behaviour.
- Hardened node security, with separation between development, staging and production, and clear controls on who can deploy or modify those environments.
- Formal incident response playbooks that account for on-chain realities, including how to notify users, when contract functions can be paused and when to involve investigative partners.
At this stage, Web3 is treated like any other strategic technology domain, supported by repeatable processes and clear accountability.
Advanced Controls
In advanced programmes, Web3 is not an experiment. It is part of the organisation’s broader operating model. Security needs to match that ambition with deeper assurance and more automation.
Advanced characteristics include:
- Extensive use of formal verification and advanced testing for high-value contracts or cross-chain components that underpin critical business workflows.
- Multi-layer monitoring that merges on-chain analytics with infrastructure telemetry and application behaviour, providing a unified view of exposure.
- AI security automation that enforces policies in real time and reduces the risk that delayed human oversight leads to irreversible loss.
- Deep integration of Web3 considerations into enterprise governance, from risk committees to reporting cycles and audit programmes.
Organisations operating at this level can run large-scale Web3 initiatives with a resilient security posture and demonstrate that confidence to regulators, partners and customers.
Final Thoughts: Security Leadership Defines Enterprise Web3 Success
Web3 will not succeed in the enterprise because it is novel. It will succeed because it delivers real value in identity, data sharing and new business models without introducing unacceptable fragility.
The record so far is clear. The biggest losses have not come from broken maths. They have come from weak governance, poor key management, flawed logic and gaps between Web2 and Web3 components. The organisations that fare better are the ones that treat enterprise Web3 security as a leadership issue, not a bolt-on to existing controls.
For security leaders, the mandate is straightforward but demanding. Build governance around keys and identity. Treat smart contracts and protocols as living systems. Secure the full stack, from browser to node. Use monitoring, analytics and automation to shorten the distance between threat and response. Above all, make sure Web3 decisions sit inside the same disciplined risk posture that guides the rest of the business.
The enterprises that do this will be able to move beyond cautious pilots and turn Web3 into a durable part of their operating model. Those who move without that foundation will simply trade one set of legacy risks for another, more unforgiving version.
If you are shaping that journey inside your organisation, EM360Tech is a useful place to keep learning from peers, vendors and analysts who are facing the same questions and pressure to get it right.







Comments ( 0 )