If you work in cybersecurity, chances are you’ve heard about Zero Trust Security. Far from being a one-size-fits-all solution, Zero Trust (ZT) is a strategic journey that transforms how we think about protection in a hyper-connected world.
The rise of Zero Trust is a direct response to evolving enterprise trends like remote work, Bring Your Own Device (BYOD) policies and the proliferation of cloud-based assets beyond traditional network boundaries. Unlike legacy models that rely on securing network segments, Zero Trust prioritises protecting resources—data, services, or accounts—ensuring security keeps pace with digital transformation.
By adopting Zero Trust principles, organisations can strengthen their cybersecurity posture and effectively safeguard operations, even in complex, distributed environments.
This article breaks down Zero Trust Architecture, its core components, and how to implement it to future-proof your enterprise.

What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture (ZTA) was introduced in 2011 by John Kindervag, a former Forrester Research analyst, and has become a critical cybersecurity framework for organisations worldwide.
ZT is a modern cybersecurity framework that shifts the focus from traditional, static perimeters to securing users, assets, and resources wherever they exist. ZTA operationalises these principles, designing infrastructures and workflows that assume no implicit trust—not for devices, users, or systems, regardless of physical or network location.
Key Assumptions in Zero Trust Architecture
When implementing ZTA in any organisation, several key assumptions guide the planning and deployment of enterprise-owned network infrastructure:
- Both enterprise-owned and non-enterprise-owned network infrastructures require stringent controls and monitoring.
- Resources operating on these networks must align with ZT principles, ensuring security across all environments.
ZT models remove reliance on wide-area perimeter defences. Instead, concepts like microsegmentation and software-defined perimeters are central to enabling dynamic, fine-grained access control across the entire infrastructure.
How Zero Trust Enhances Security
By employing ZTA, organisations can enforce:
- Software-defined perimeters to secure sensitive systems.
- Microsegmentation to limit lateral movement within the network.
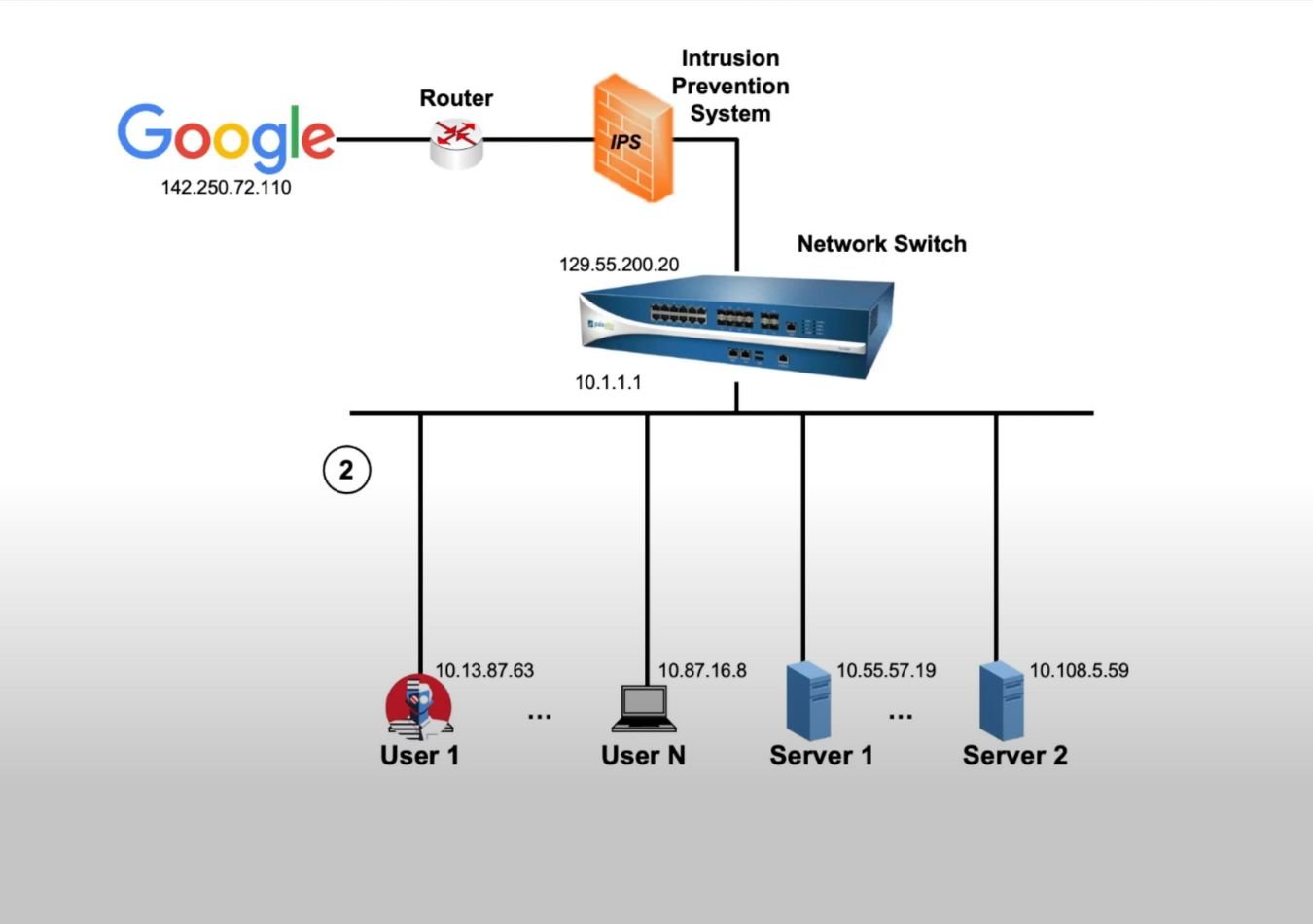
- Continuous validation of user identity and device compliance across multiple environments.
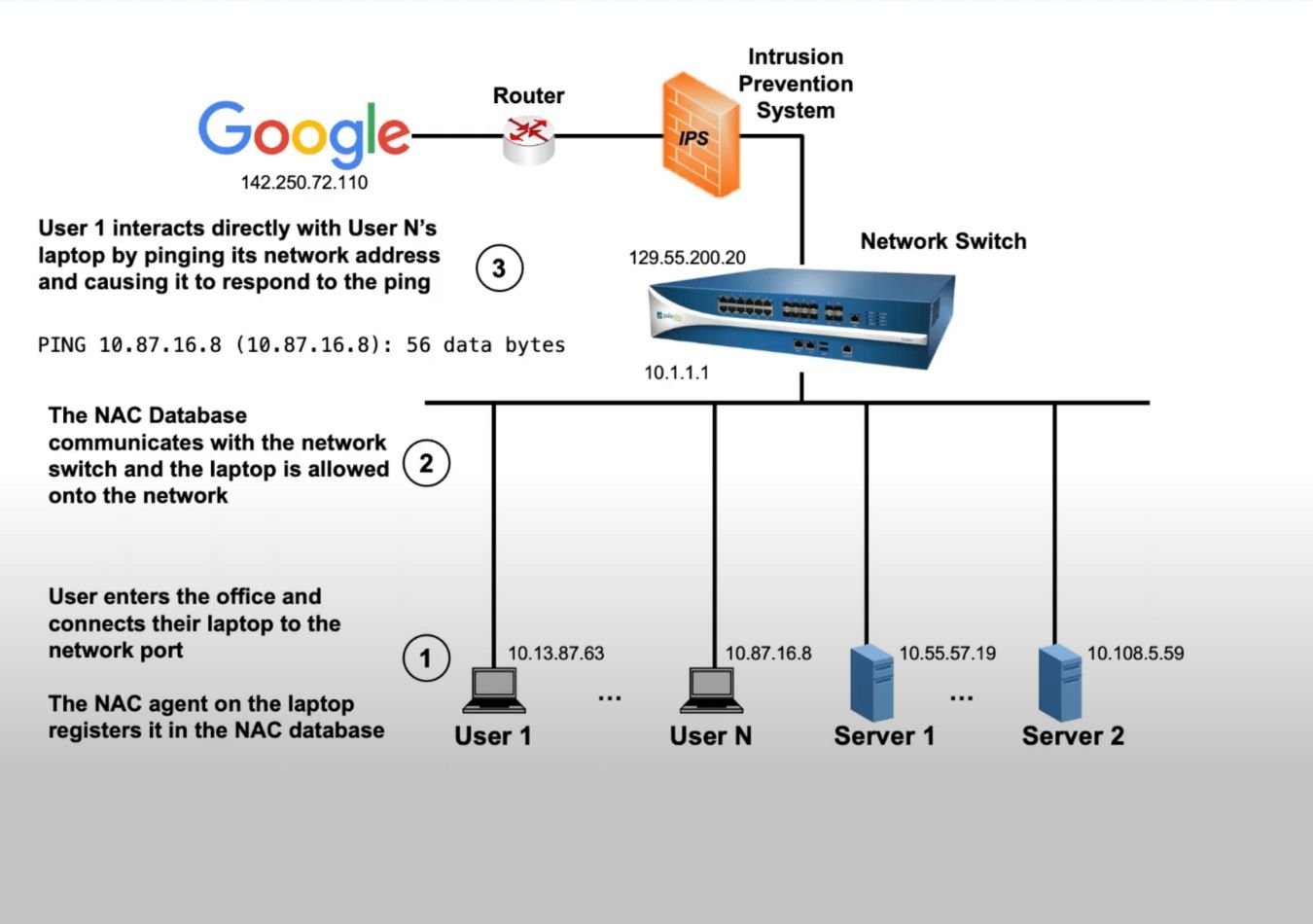
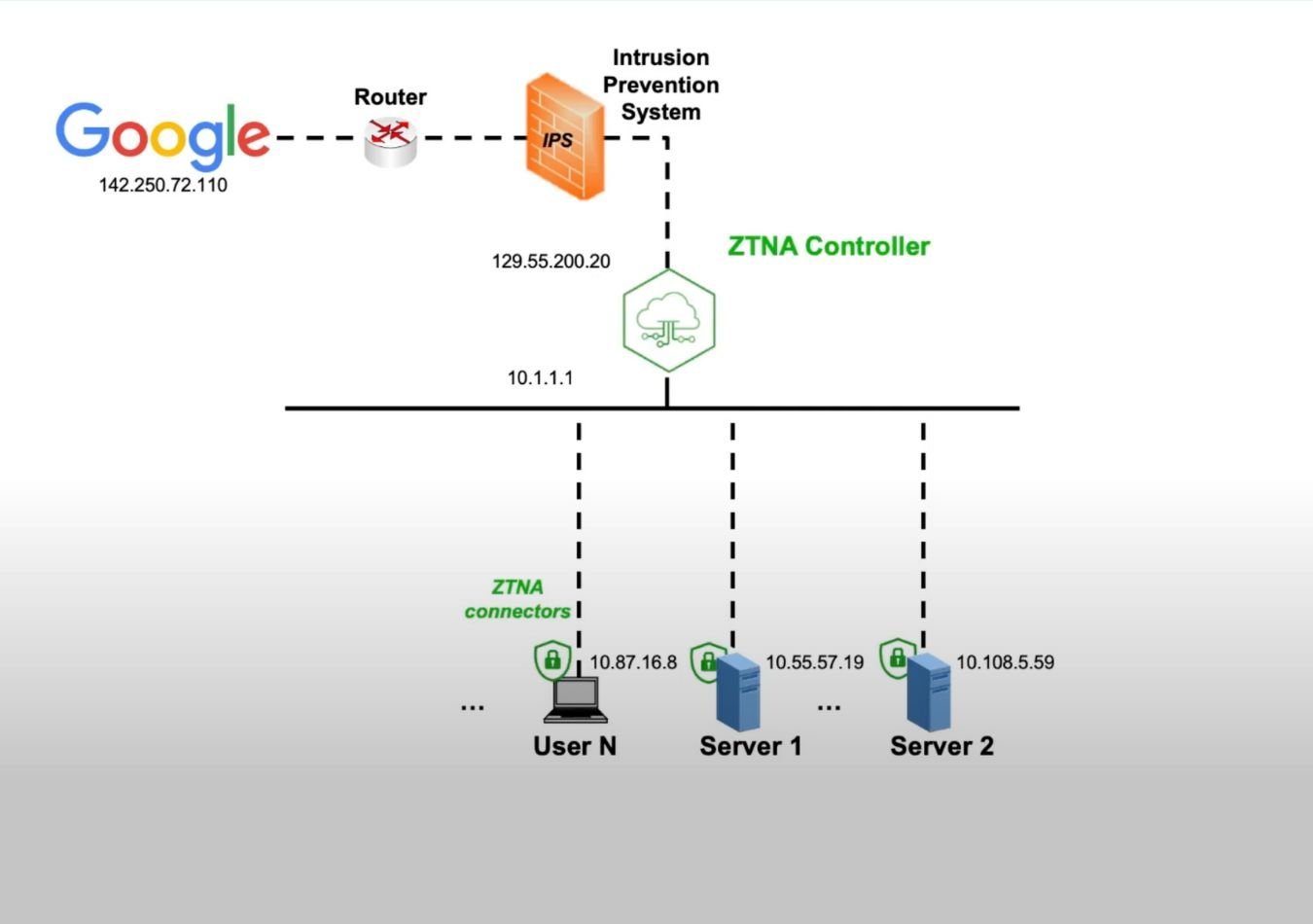
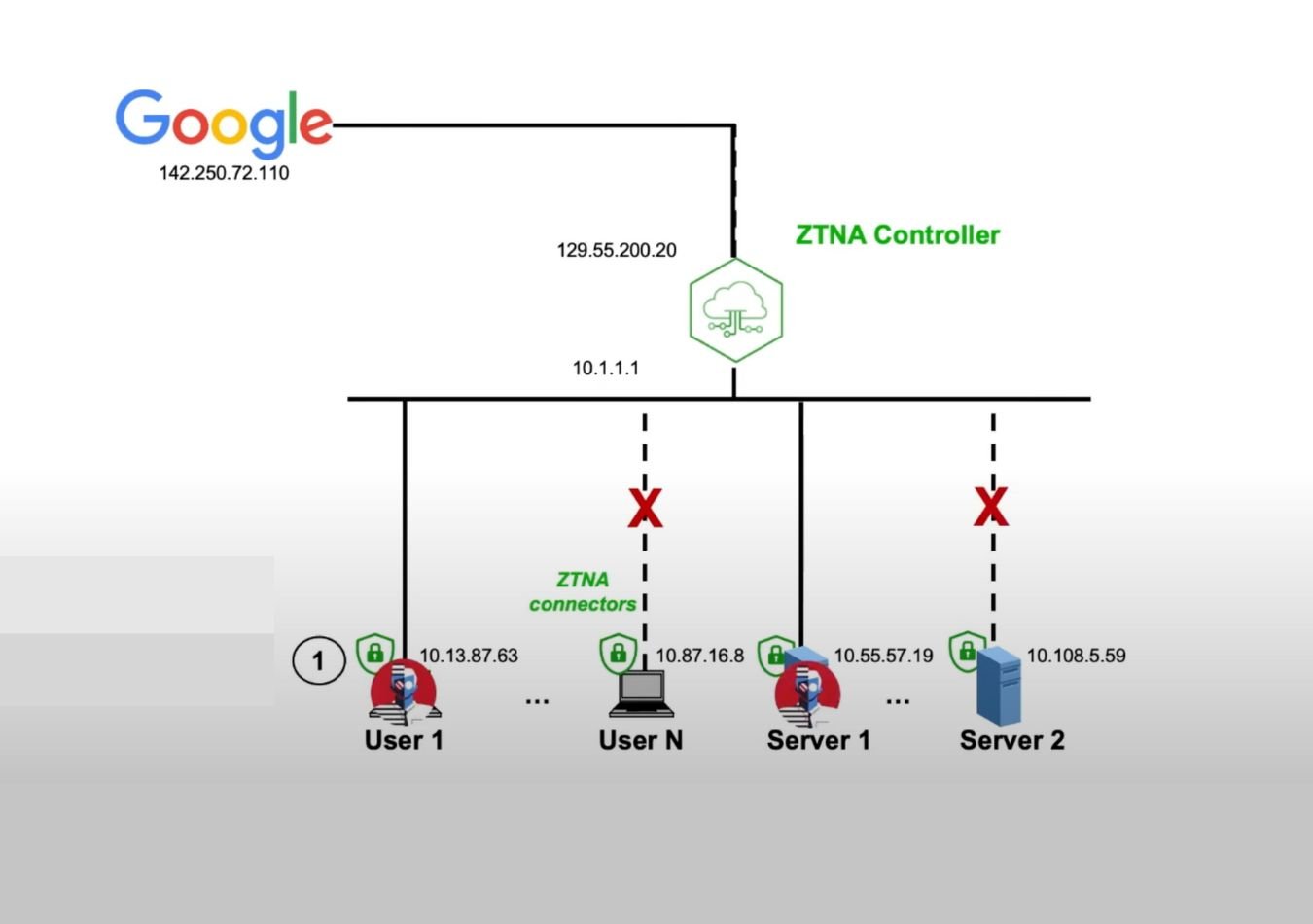
Core Principles of Zero Trust
A comprehensive Zero Trust framework secures users, applications, and infrastructure holistically. Zero Trust Network Access (ZTNA) ensures user privileges are dynamically validated and consistently applied across multiple environments.
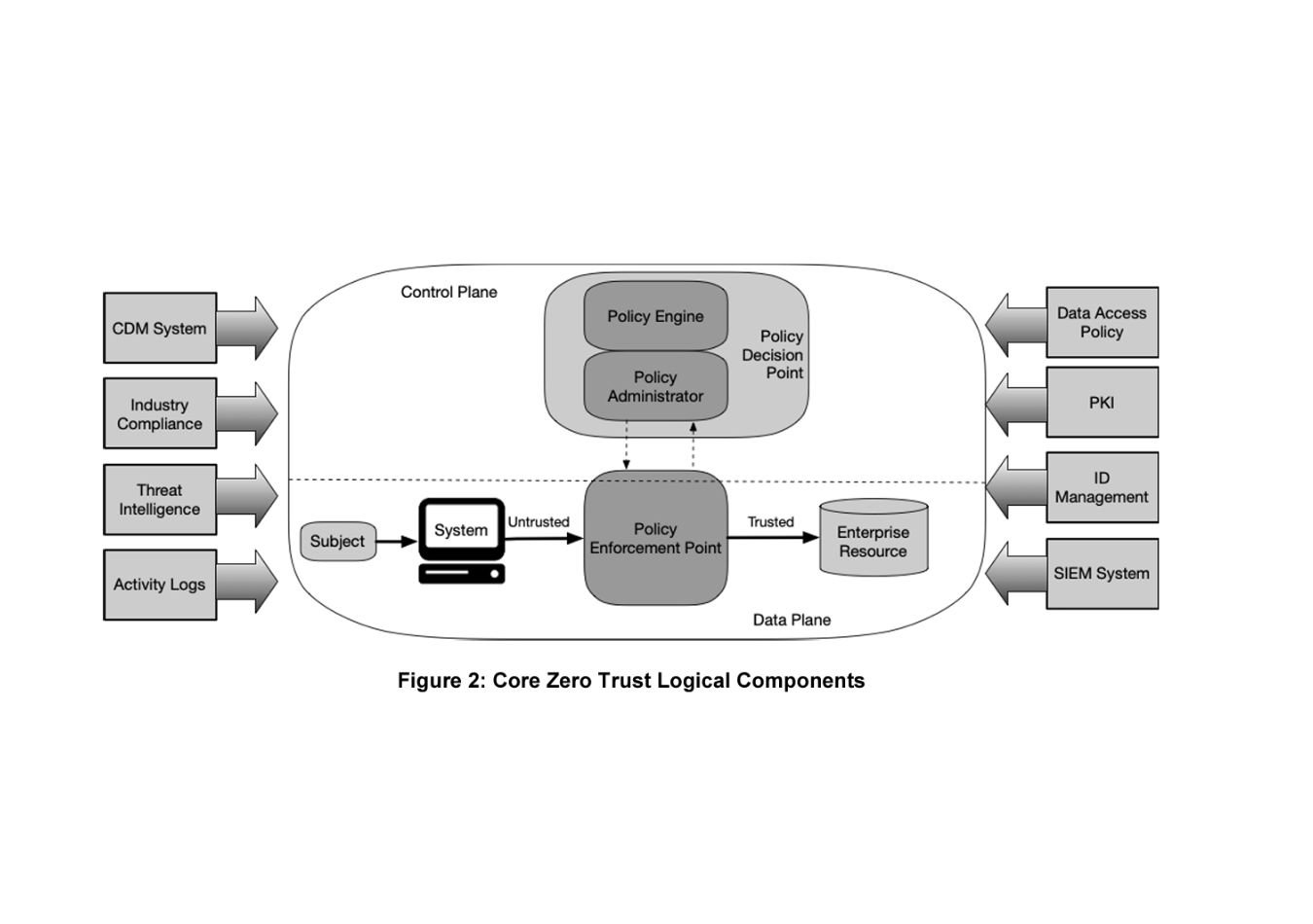
This enhances an organisation's security posture by adhering to the following Zero Trust tenets:
- All data sources and computing services are treated as resources. Networks may include diverse devices, from servers to personally owned devices, which must be considered potential resources accessing enterprise-owned systems.
- All communication is secured, regardless of location. Trust is never granted based solely on the network’s physical boundaries. Every access request must meet the same security requirements, whether internal or external.
- Access is granted per session. Evaluations are dynamic, with trust established for the minimum privilege required to complete the task.
- Dynamic policies determine access. Policies evaluate client identity, application use, and behavioural and environmental attributes.
- Continuous monitoring ensures asset security. Organisations must maintain visibility over all devices and apply patches as necessary to uphold security integrity.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a security model designed to protect organisations by ensuring that access to resources is granted only to verified users and devices, regardless of their location. Unlike traditional network security approaches, which rely on a perimeter-based defence, ZTNA operates on a “never trust, always verify” principle. This means that no user or device is trusted by default, even if they are within the corporate network.
By adopting a Zero Trust Network Access strategy, businesses can enhance their cybersecurity posture, reduce the risk of data breaches, and provide secure remote access to sensitive information. ZTNA solutions ensure continuous authentication and authorisation, leveraging advanced technologies like multi-factor authentication (MFA), micro-segmentation, and behaviour analytics.
The growing need for secure remote access and cloud adoption has made ZTNA a crucial component of modern cybersecurity. Businesses across the UK are increasingly implementing ZTNA to comply with stringent data protection regulations and safeguard against evolving cyber threats.
Benefits of Zero Trust Network Access
Enhanced security: ZTNA minimises attack surfaces by limiting access to only what is necessary.
Improved compliance: Helps meet data protection requirements like GDPR by ensuring secure access.
Scalable remote work: Supports flexible working environments while maintaining robust security.
What Are the Three Principles of Zero Trust?
Understanding the three principles of Zero Trust is essential for organisations looking to strengthen their cybersecurity posture. These principles form the foundation of an effective ZTA, ensuring enhanced protection against modern cyber threats.
Verification
At the core of Zero Trust is continuous verification. Every user and device must consistently validate their identity and authorisation before accessing systems or data. Verification is not a one-time event; it leverages technologies like multi-factor authentication (MFA), endpoint security, and behavioural analytics to ensure trustworthiness throughout a session.
Least Privilege Access
The principle of least privilege access restricts user rights to the bare minimum required for their tasks. By limiting access to only the necessary data, applications, and services, organisations can significantly reduce their attack surface.
This key ZT principle is implemented through:
- Granular access controls
- Just-in-time (JIT) and just-enough access (JEA) mechanisms
Additionally, risk-based adaptive access policies balance security and productivity, ensuring users have secure access without hindering operations. Adhering to least privilege access minimises potential exposure to insider threats or compromised accounts, reducing the risk of unauthorised data access.
Assumption of Breach
The assumption of breach acknowledges that no system is impervious to threats. This principle operates on the belief that breaches are inevitable, whether from external attackers or internal vulnerabilities.
The goal of ZTA under this principle is to limit the blast radius of any security incident. This is achieved through:
- Micro-segmentation of sensitive resources
- End-to-end encryption
- Continuous monitoring of user and device behaviour for anomalies
- Strong incident response and recovery strategies
By assuming a breach is always possible, organisations can adopt a proactive approach to mitigating the impact of cyberattacks.
Key Benefits of Zero Trust Architecture
ZTA creates a more secure and adaptable environment for modern businesses, reducing the risk of attacks and ensuring comprehensive protection across diverse and complex IT infrastructures. With cybersecurity threats evolving rapidly, ZTA offers several key benefits to organisations striving for robust data security and operational resilience.
Enhanced Security with Least-Privilege Access
ZTA enhances security by enforcing the principle of least privilege, ensuring users and devices access only what is necessary. Continuous authentication and authorisation prevent unauthorised access to sensitive systems or data, significantly reducing risks from both insider and external threats.
Protection Against Data Breaches
By requiring authentication for every request, ZTA protects against data breaches. Even if a user or device is compromised, the assumption of breach and lack of implicit trust restrict attackers' lateral movement within the network.
Improved Visibility and Monitoring
ZTA improves visibility by relying on continuous monitoring and logging of all network activities. This enhanced oversight enables organisations to detect and respond to threats swiftly, while providing detailed audit trails for compliance and forensic analysis.
Reduced Risk of Advanced Persistent Threats (APTs)
By isolating network segments and verifying access at every level, ZTA minimises the risk of APTs. These threats, which rely on undetected lateral movement, are effectively contained through ZTA’s strict verification processes.
Scalability for Growing Businesses
ZTA is highly scalable, accommodating increasing numbers of users, devices, and applications. Whether for small or large organisations, ZTA’s architecture adapts seamlessly, making it ideal for modern, dynamic businesses.
Improved Incident Response
Granular control over networks provided by ZTA allows security teams to rapidly identify and isolate compromised resources. This minimises the impact of incidents and shortens response times, enabling businesses to resume operations faster.
Reduction in Insider Threats
By enforcing strict access controls, ZTA significantly reduces risks from insider threats. Access is restricted to essential functions, limiting lateral movement and minimising exposure to malicious or accidental insider activities.
How to Implement Zero Trust Architecture?
Implementing ZTA involves a series of strategic steps to enhance your organisation's cybersecurity posture. By focusing on ZT security principles, you can effectively protect sensitive data, reduce risks, and prevent cyber threats.
Here’s a detailed guide to implementing ZTA for businesses:
Understand the Core of Zero Trust Security
Begin by acknowledging the principle of "never trust, always verify." Unlike traditional security models, ZTA assumes that threats can come from inside or outside your network, and no entity is trusted by default.
Identify and Protect Critical Assets
Conduct a comprehensive audit to identify sensitive data, systems, and processes that require protection. Use microsegmentation to divide your network into secure zones, limiting access to each based on user roles and permissions.
Implement Strong Identity Verification
Adopt multi-factor authentication (MFA) to verify user identities at every access point. Integrate identity and access management (IAM) systems to ensure that users only access resources they are authorised for.
Monitor and Analyse Network Traffic Continuously
Use advanced tools like Security Information and Event Management (SIEM) systems to monitor traffic and detect anomalies in real time. Continuous monitoring is a cornerstone of Zero Trust Network Access (ZTNA), allowing rapid response to potential breaches.
Deploy Context-Based Access Controls
Implement least privilege access policies, granting users only the permissions they need for specific tasks. Leverage dynamic access controls that adjust based on user behaviour, location, or device security status.
Encrypt All Data
Ensure that data is encrypted both in transit and at rest. Strong encryption protocols protect sensitive information and comply with GDPR requirements.
Regularly Update Security Policies
Adapt your security measures to evolving threats. Conduct regular assessments and simulations to test your ZTA and refine your policies accordingly.
Train Your Workforce
Educate employees about ZTA and the role they play in safeguarding systems. Awareness campaigns can significantly reduce the risk of human error.
Leverage Automation
Automate processes like user authentication, threat detection, and response. Modern tools powered by AI and machine learning enhance the efficiency of your ZTA.







Comments ( 0 )