The rapid rise of non-human identities - such as service accounts, secrets, API keys, tokens, and certificates - poses a dual security and operational challenge for security teams.
Non-human identities (NHIs) have outnumbered human identities by a factor of 50 to 1, yielding a considerably large attack surface and making them a primary target of malicious actors.
The security risks are substantially exacerbated considering that on average, there are 5 times more NHIs with greater access privileges to sensitive data than there are humans.
Now with more and more organization functionalities being automated by AI workflows and accessed by machines, a need to deploy an enterprise-wide non-human identity strategy has become vital.
One such organization tapped the gap between security and digital entities for organizations. Oasis Security, a New York (US) based computer and network security company came up with an integrable solution that for the first time automates the entire lifecycle of NHI management.
The platform called Non-Human Identity Management (NHIM) can now be used by security teams to enable easy and efficient management of NHIs.

What is Oasis NHI Management?
Oasis NHI Management is a specialized platform designed to manage and secure Non-Human Identities (NHIs) within an organization. The platform empowers security, engineering, and development teams to improve security posture, implement stronger governance, and simplify compliance by taking control of the non-human identity lifecycle without risking system resilience and operational complexity.
With Oasis NHI Management, the lifecycle of cloud services’ security systems is monitored from inception to retirement. The solution leverages holistic contextual visibility to provide a complete view of all NHIs including the digital accounts’ usage patterns, and relationships with other entities. It also works across a hybrid cloud system where it manages NHIs across on-premises and cloud environments.
Along with automating NHI lifecycles, Oasis NHI Management offers posture management by constantly monitoring the security posture of NHIs, allowing them to rapidly detect potential risks and resolve them quickly and efficiently before an error has even occurred. Lifecycle management and automation enable the organization to automate the creation, rotation, and decomposition of NHIs depending on the situation.
How does Oasis NHI Management work?
Designed to be an easy-to-use system that can be integrated with all common cloud and on-premise identity sources, NHI Management continuously monitors non-human identities with instant holistic visibility on every NHI. It manages things like who owns it, consumes it, what resources it grants access to, and how privileged.
The platform has also been equipped with a built-in Oasis Posture and Remediation Intelligence (PRI) module which automatically detects vulnerabilities, prioritizes the most severe issues, and generates remediation plans. This instantly shortens the time of identification and enables immediate resolution of incidents, reducing security risks significantly.
Features of Oasis NHI Management
Oasis NHI Management comes with a range of functions and capabilities designed to efficiently optimize NHI digital entities for an organization's security actions.
Some of these features include:
1. Automated lifecycles of NHIs
Oasis NHI Management comes with powerful automated lifecycle management capabilities out of the box, streamlining the process of managing NHIs from creation to decommissioning. This automation not only enhances efficiency but also strengthens security by reducing human error and minimizing the risk of misconfigurations.
Oasis can automatically create new NHIs based on predefined templates or policies, ensuring that NHIs are provisioned with the appropriate access rights and attributes to reduce the risk of unauthorized access. The platform can also automatically rotate credentials associated with NHIs, minimizing the risk of credential theft and unauthorized access, which is particularly important for NHIs with privileged access.
When NHIs are no longer needed, Oasis can automatically decommission them to prevent them from becoming security risks by revoking access privileges and removing associated resources.
You can also define policies that govern the lifecycle of NHIs. This can be used to automate various tasks, such as provisioning, rotation, and decommissioning, based on specific criteria.
2. Holistic Visibility
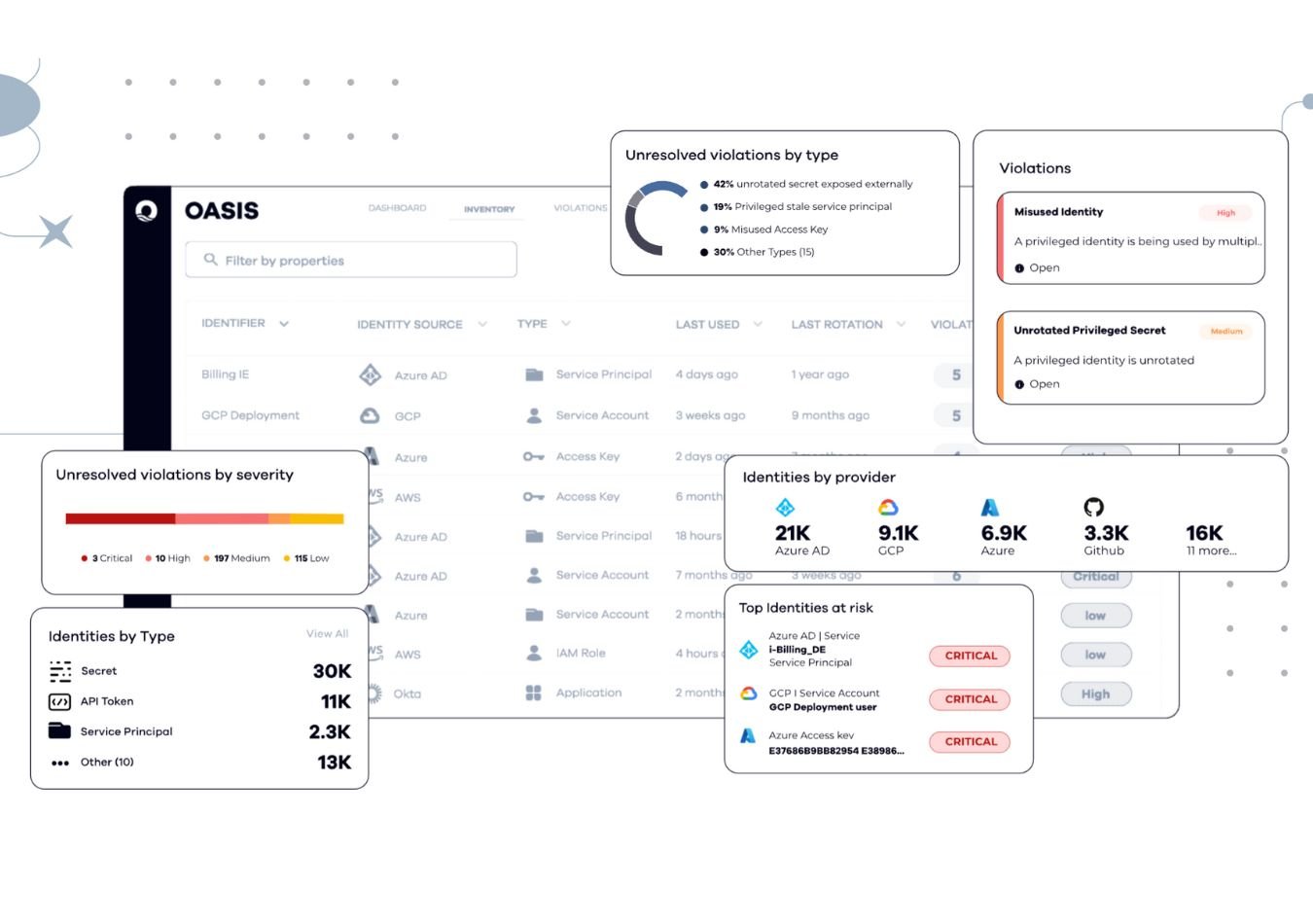
The system ensures holistic contextual visibility by shedding light on NHI’s usage patterns, operational dependencies, and ownership details. The visibility feature makes errors easy to spot by tackling vulnerabilities and cyber-attacks before they’ve happened. The system has been backed up with data from across the IT ecosystem, including interactions with infrastructure as code (IaC), IT service management (ITSM) systems, logs, and development tools. This information allows the platform to visualize the data and present a comprehensive perspective of NHI functions, allowing for informed decision-making and boosting security and compliance strategies.
Along with visualizing data, NHI Management also shows certain classifications of the NHI lifecycle to make it easy for security teams to distinguish between the data that’s been decommissioned, in the process of being decommissioned and observations. Options are displayed in a circle – from rotation, decommission, provisioning, ownership, and posture monitoring – through a unified interface for managing NHIs.
3. Seamless integrations
Oasis NHI Management automates the identification of threats and vulnerabilities and updates the centralized inventory of all NHIs across different platforms, including hybrid cloud environments like laas such as AWS, Azure, GCP; Paas/SaaS; and on-prem systems like Active Directory and database local accounts.
The Oasis platform is designed in such a way that the integration pointers are merged into various systems and teams within an organization, including security teams, developers, and third-party systems. These could be SIEM (Security Information and Event Management) systems, vulnerability scanners, and privileged access management (PAM) solutions. This integration can provide a more complete picture of the security landscape and enable coordinated threat response.
4. Priority-based risk management
Oasis NHI Management automatically examines and ranks posture-related problems based on levels of severity, spontaneously checking risks based on priority. These risks are usually visible in the form of red, orange, and yellow colors on the platform’s ‘Unresolved violations by severity’ selection.
The platform also goes beyond raw data by providing key insights into NHI Ownership, Usage, Consumers, Resources & Privileged status, and assesses the risks linked to each NHI based on these factors. This makes it easy for the system to spot the most critical risks to resolve first, allowing teams to proactively prioritize risks based on data.
5. Customizable dashboards
Oasis Security NHI Management platform is designed to visualize NHI data to present security risks as coherently as possible. The platform creates customized dashboards and automatically issues alerts to meet specific needs. It also grants the users authorization to customize NHI data for certain purposes, such as for issuing customized alerts that can be configured to notify teams of suspicious activity or potential security threats. Organizations can also customize workflows, helping them automatically conduct routine tasks, reduce errors, and save time due to quick and efficient resolution actions.
What makes Oasis NHI Management different?
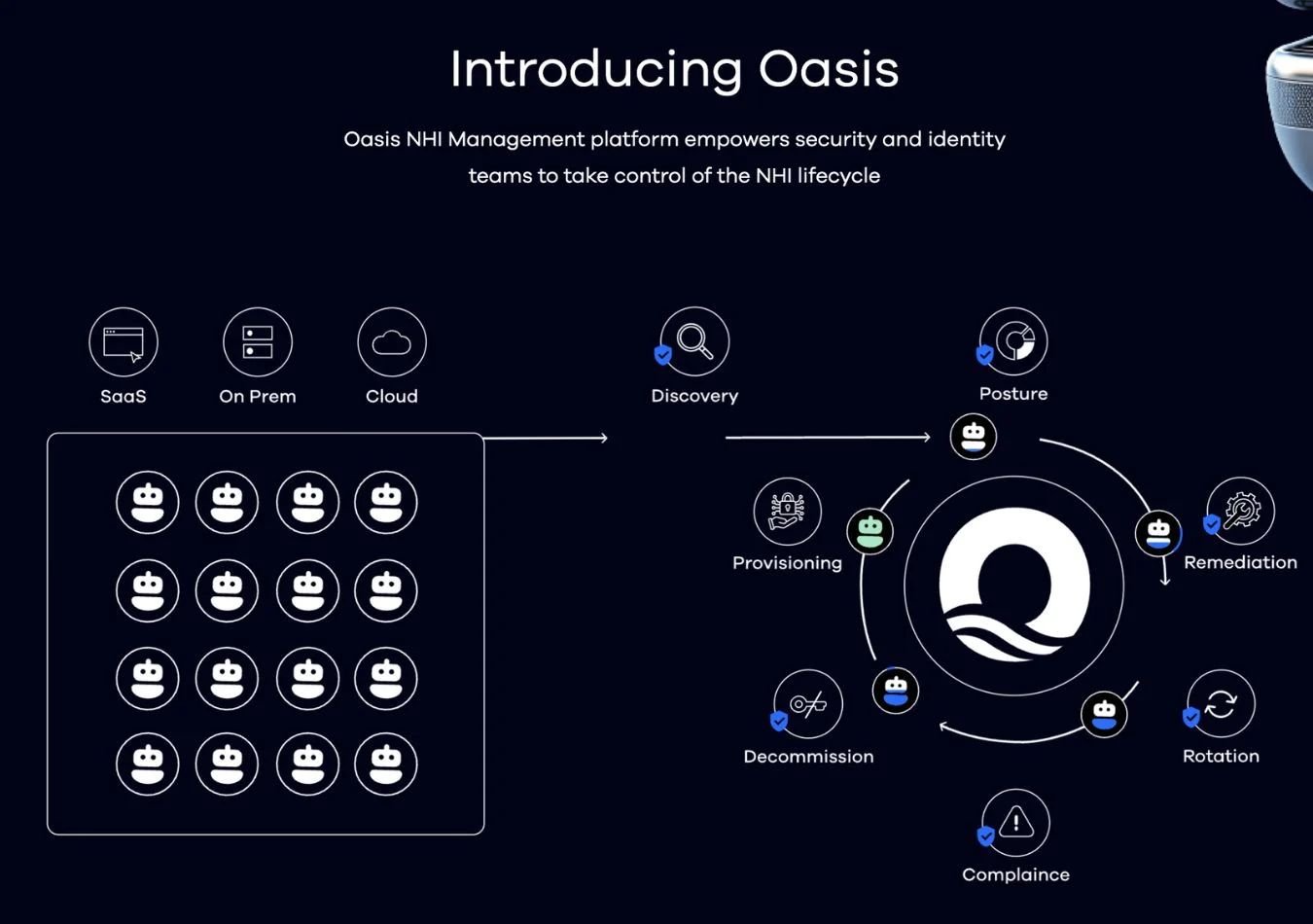
Oasis NHI Management is the first NHIM platform to automate the entire lifecycle of non-human identity management. The platform provides a comprehensive view of NHIs – including their usage patterns, dependencies, and relationships within the IT ecosystem – to enable organizations to make informed decisions and identify potential security risks.
It also aggregates data from various systems, such as IDPs, event logs, secret managers, and ASPMs, to create a unified view of NHIs, allowing for effective management across different environments and technologies. Oasis features unique APIs that seamlessly integrate with a range of applications and services, supporting automation and customization.
Oasis NHI Management in the real world
With an emphasis on third-party access management, Oasis Security’s NHI Management platform ensures that data is secured and only accessible to authorized personnel. Secure management is at the forefront of their mission.
Attacks involving NHIs owing to the shift to cloud-based platforms that are vastly operated by development teams, communication between services needs to be seamless. For example, in a company using Amazon Web Services (AWS), dealings with S3 buckets and EC2 along with applications such as ServiceNow and Salesforce have dramatically increased the number of NHIs over human resources.
When adopted by an organization using AWS, Oasis’ NHI Management platform could integrate the platform with AWS environments to efficiently manage security targeting NHIs. The system would automatically discover and present an inventory of NHIs such as IAM roles, EC2 instances, S3 buckets, and other AWS resources.
The platform would also provide contextual information about NHIs, including their usage patterns, dependencies, and access privileges within the AWS environment by leveraging AWS APIs and metadata. It would be able to help AWS users ensure compliance with AWS security best practices and industry standards like PCI DSS and HIPAA. Micnconfiguartions, unauthorized access, and data breaches would be much faster and easily detected.
NHI Management platform integration with AWS could also provide comprehensive insights on both human and NHI within the AWS system. Detection of unused or underutilized NHIs is another feature of the Oasis security solution platform that could help optimize costs better and avoid unnecessary expenses. The system will issue security alerts to those within the AWS system in case of suspicious activity, security threats, or system breaches. Overall the automation of NHI identifications and classifications can help tackle and prevent security pitfalls.
Ido Geffen, VP of Product at Oasis Security spotlighted that the service offers posture violation alerts, providing concise descriptions of security issues, their severity, and detailed, actionable recommendations. These can be addressed manually or through automated actions aligned with your internal workflows.
“Over time, we aim to shift from reactive to preventive security management, akin to preventive medicine: better to maintain ongoing health through regular checks and balances than to deal with emergencies as they arise,” he added.
Solution Overview: NHI Management (NHIM)
NHI Management platform by Oasis Security aims to bridge the gap between traditional security practices and the management of digital entities. By automating the entire lifecycle of NHI management, the platform simplifies the process for security teams, making it easier to efficiently manage and secure NHIs within their systems.
The platform helps security and development teams to improve security posture, implement stronger governance, and simplify compliance by taking control of the non-human identity lifecycle without risking system resilience and operational complexity. This is why the NHI Management platform by Oasis Security has been awarded the Niche Player Badge.

About Oasis Security
Oasis Security, a computer and network security company based in New York has established itself as a market-leading platform for non-human identity management. The organization’s mission is to fortify cybersecurity defenses by enabling enterprises to efficiently secure non-human identities throughout their lifecycle.







Comments ( 0 )