The cybersecurity industry shuddered in May 2023 when Progress Software revealed a ransomware gang known as Clop had abused a zero-day vulnerability in its MOVEit file transfer software and gained access to its systems
The incident would impact thousands of organizations globally in the months that followed, with malicious actors from all over the world exploiting the vulnerability to steal sensitive data from MOVEit’s customers, including New York City’s public school system, a UK-based HR solutions and payroll company with clients like British Airways and BBC, and many others.
According to a running tally by EMISOFT, who has kept a running tally about the number of organizations impacted by the breach, the vulnerability has now impacted 2752 organizations and the data of over, 94 million people.

And today, long after what has become known as one of the biggest cyber attacks in history, clop continues to be active and continues to steal data using the MOVEit Transfer vulnerability.
But Clop's story extends far beyond this single incident. In this article, we’re delving into what is the clop ransomware gang, exploring their origin, criminal activities, and methods of attack.
What is clop? The ransomware gang explained
Clop, sometimes written Cl0p, is a Russian-speaking ransomware gang that uses a ransomware-as-a-service (RaaS) model of attack where malicious actors rent their malware for a share of the profits.
The gang emerged in 2019 as a variant of the well-known CryptoMix ransomware but has grown from spear-phishing campaigns to exploiting major vulnerabilities like SolarWinds and MOVEit.
Clop's attacks go beyond simply encrypting files. They employ a complex, "double extortion" tactic to simultaneously steal sensitive data alongside encryption.
This stolen information serves as a bargaining chip, threatening public exposure if the ransom isn't paid, adding another layer of pressure and fear to their attacks.
Clop also employs more complex attacks, such as zero-day, that have a significant impact and allow them to demand higher ransom payments.
What is a Clop Ransomware attack?
A Clop ransomware attack is a sophisticated cyber attack that uses a specific type of malware called Clop ransomware to extort money from victims.
Clop is known for its multi-pronged approach to this attack, often combining data encryption with data exfiltration and extortion.
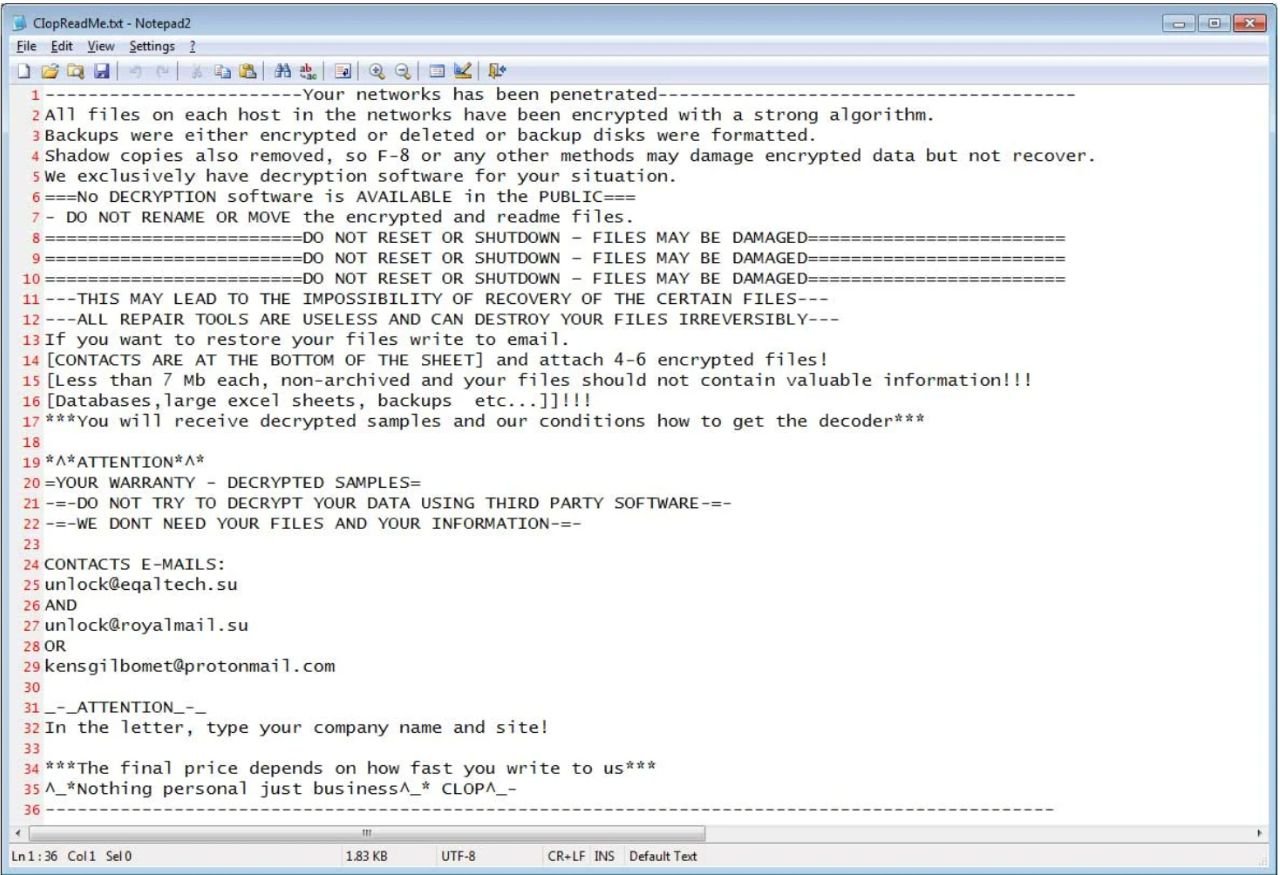
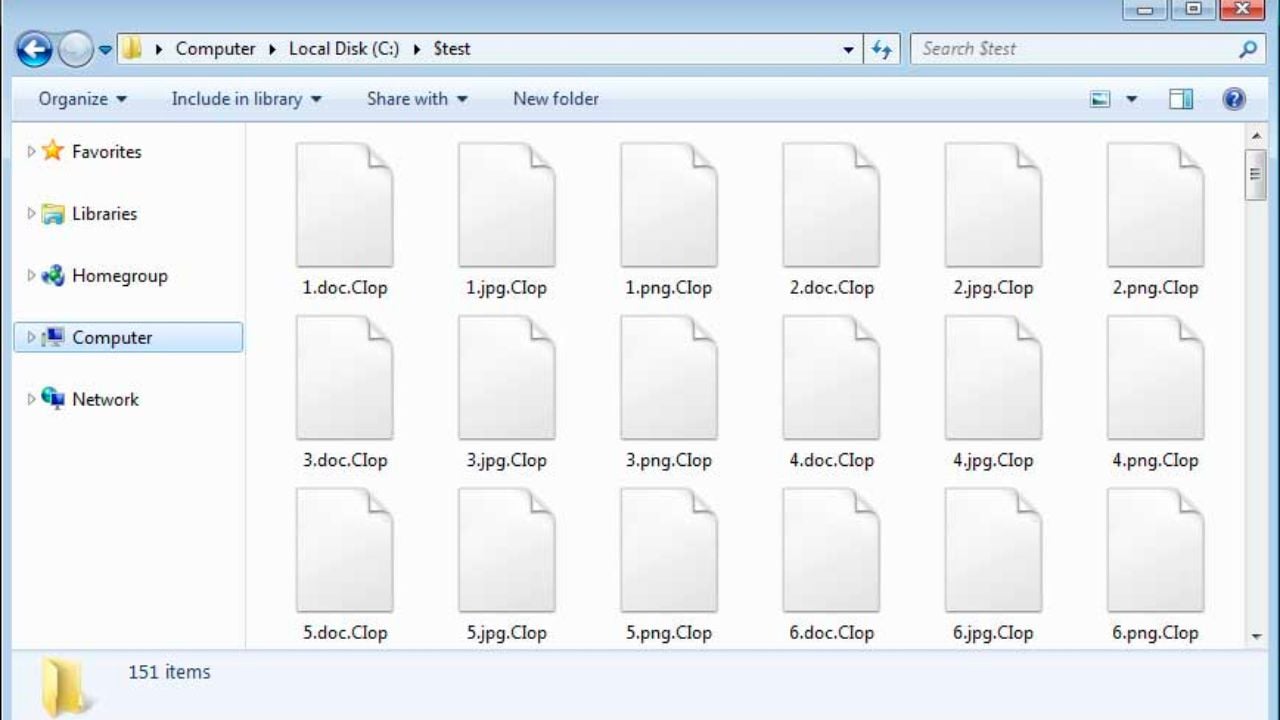
The group uses strong encryption algorithms to render essential files on a victim's device inaccessible, with the encrypted files typically appended with a specific extension, like ".clop" or ".ciop," indicating the attack.
Victims then receive a ransom note demanding payment in cryptocurrency (like Bitcoin) in exchange for the decryption key.
As well as encryption, Clop often steals sensitive data from the victim's system before encryption. This data could include financial records, personal information, or intellectual property
The gang then threatens to publicly release the stolen data if the ransom demand is not met. This tactic adds further pressure on the victim to pay, as the potential reputational damage and financial losses can be devastating.
Who does Clop target?
Reports and investigations consistently show Clop targeting a wide range of organizations all over the world, spanning various industries and locations.
These targets include healthcare providers, energy companies, government agencies, and universities, as well as any large enterprise it believes will be able to afford its ransom demands.
The only organizations exempt from Clop’s radar appear to be those directly linked with Russia. As of February 2024, the gang is yet to target any Russian organization, suggesting they may be of Russian origin themselves.
Despite their global impact, the true identities of the individuals behind Clop remain a mystery. While linked to Russian-speaking countries, they operate anonymously through the dark web, constantly evolving their tactics to evade detection.
History of Clop Attacks

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
Clop was first spotted by researchers in February 2019 and quickly evolved from a variant of the "CryptoMix" ransomware family to the RaaS model it uses today.
Since then, they’ve targetted a range of organizations across the globe – from energy companies and government agencies to universities, as well as any large enterprise it believes will be able to afford its ransom demands.
Here's a timeline highlighting some of Clop’s most notable cyber attacks attacks:
Maastricht University Attack (December 2019)
In December 2019, Clop attacked Maastricht University in the Neverlands. The ransomware encrypted almost all Windows systems used by the University, making it impossible for students and staff members to access any university online services during the Christmas break.
Maastricht University ended up paying the €200,000 ransom set by Clop in a Bitcoin transfer to restore its systems. This would later be seized by the public prosecutor service. Once the ransom was converted from Bitcoin to Euros, the university was able to recover €500.000, double the ransom it paid.
Accellion FTA Attack (December 2020)
The Accellion FTA attack in December 2020 was a major cyber attack perpetrated by the Clop ransomware group where the gang It targeted a vulnerability in the Accellion File Transfer Appliance (FTA) software, impacting over 130 organizations worldwide, including major companies like SolarWinds, Microsoft, and Cloudflare. Here's a breakdown of the attack.
Clop leveraged zero-day vulnerabilities in Accellion FTA, meaning these flaws were unknown and unpatched at the time. This allowed them to gain unauthorized access to victim networks. They used these vulnerabilities to install a custom web shell called "DEWMODE" on compromised servers. This web shell gave them remote control and enabled further infiltration and data exfiltration.
Once inside, Clop exfiltrated sensitive data from compromised systems, including financial records, personal information, and intellectual property. They then used this stolen data as leverage, demanding ransom payments in cryptocurrency from the affected organizations.
Law enforcement agencies worldwide investigated the attack, but details about arrests or prosecutions remain limited.
When Case Systems Become Weapons
Examines how a case-management platform became alleged intelligence infrastructure, blurring lines between legal IT and covert operations.

GoAnywhere MFT attack ( January 2023)
In January 2023, the Clop ransomware group launched another significant attack, targeting the Fortra GoAnywhere MFT secure file transfer solution. Here's a breakdown of the incident. Clop exploited a zero-day vulnerability in GoAnywhere MFT, identified as CVE-2023-0669. This vulnerability, classified as "high severity," allowed for remote code execution (RCE) on vulnerable systems.
The vulnerability resided in the software's License Response Servlet, enabling attackers to inject malicious code and gain unauthorized access to victim networks.
Similar to the Accellion attack, Clop exfiltrated sensitive data from compromised systems before encrypting files with ransomware They could then deploy malware, steal data, and potentially install ransomware.
The vulnerability was initially disclosed on February 1, 2023, and Fortra released an emergency patch shortly after. However, some organizations were already compromised before the patch became available.
In the end, over 130 organizations were impacted worldwide, including large enterprises like Honda, Yamaha, and Procter & Gamble.
MOVEit Vulnerability (May 2023)
In mid-2023, the Clop ransomware group exploited a critical vulnerability in Progress Software's MOVEit – a widely used managed file transfer (MFT) platform.
The specific vulnerability exploited was CVE-2023-34362, a SQL injection flaw in the MOVEit Transfer web application. This allowed attackers to execute arbitrary SQL commands on vulnerable servers, enabling them to gain unauthorized access, install malware, and steal data.
Clop allegedly started exploiting this vulnerability in late May 2023. They gained access to MOVEit servers, installed a web shell named LEMURLOOT, and used it to exfiltrate sensitive data before deploying ransomware. Clop primarily focused on stealing sensitive data before encrypting files. This data could include financial information, personal details, and intellectual property.
Although Progress Software released a patch on the same day they acknowledged the vulnerability, attackers had already compromised many companies’ systems.

Data Trust Erosion in Niche Apps
What a delayed breach disclosure, insecure password practices, and account removal reveal about security risk in smaller networks.
These victims included New York City’s public school system, US Government Agencies, and a UK-based HR solutions and payroll company with clients like British Airways and BBC, among others.
So far, they attacked over 2,700 organizations and impacted over 62 million individuals. Based on the number of confirmed organizations affected, the cost of the MOVEit incident stands at around $9.9 million. However, considering not all victims have reported the number of individuals impacted, the potential cost could continue to rise to as much as $65 million.
Defending Against Clop
While Clop is a sophisticated and resourceful group, there are several steps companies can take to protect themselves from falling victim to one of their ransomware attacks.
Defending against Clop, or any sophisticated ransomware group, requires a multi-layered approach and a strong security posture.
Here are some key strategies companies can implement:
1. Prevention
- Patch Management. Regularly update software and applications with the latest security patches to address known vulnerabilities. This is crucial as Clop often exploits zero-day vulnerabilities.
- Robust Security Solutions. Implement endpoint protection, firewalls, and intrusion detection/prevention systems (IDS/IPS) to monitor network traffic and detect suspicious activity.
- Multi-factor Authentication (MFA). Enforce MFA on all sensitive accounts and systems to add an extra layer of security beyond passwords.
- Data Backups. Regularly back up critical data offline and test restoration procedures to ensure quick recovery in case of an attack.
- Network Segmentation. Segment your network into smaller zones to limit the potential impact of a breach.
- Employee Education. Train employees on cybersecurity best practices, including phishing awareness and avoiding suspicious attachments or links.
- Software Restriction. Restrict access to unnecessary software and applications to minimize the attack surface.
2. Detection and Response
When Breach Containment Fails
What a 560m-record heist exposes about outdated perimeter defenses and why boards must pivot to an assume-breach, limit-and-contain security model.

- Security Information and Event Management (SIEM). Implement an SIEM to collect and analyze security logs from various sources to identify potential threats.
- Incident Response Plan. Have a well-defined incident response plan outlining steps to take in case of a cyberattack. Regularly test and update this plan.
- Threat Intelligence. Subscribe to threat intelligence feeds to stay informed about the latest threats and vulnerabilities.
- Testing. Conduct regular tests to identify and address security weaknesses in your systems. There is a range of pentesting tools on the market to help you do this.
Final Thoughts
Clop consistently demonstrates a high level of technical expertise and the ability to exploit both known and zero-day vulnerabilities. They adapt their tactics to current events and trends, making them a persistent threat.
The combination of data exfiltration with encryption adds another dimension to their attacks, increasing pressure on victims and complicating recovery efforts. Data protection and backup strategies are crucial.
While many efforts are underway to combat ransomware, challenges remain. Continued research, collaboration, and investment in cybersecurity are essential to protect businesses and individuals from these evolving threats.
As Clop operates globally, international cooperation between law enforcement agencies and security researchers is critical to tracking their activities and preventing them from continuing to wreak havoc in 2024.







Comments ( 0 )