Police have arrested a teenager from Walsall in connection with the recent cyber attack on TfL, which is now known to have exposed thousands of commuters’ data in the UK capital.
The National Crime Agency (NCA) revealed the 17-year-old male was detained on suspicion of Computer Misuse Act offences following the attack launched on TfL’s systems on Sunday 1 September.
The breach is believed to have exposed the bank account details of about 5,000 passengers – either via activity on their Oyster card account or refund data. This includes account numbers and sort codes.
Names and phone numbers of passengers are also thought to have been breached, including some personal data from Oyster cards and Contactless bank cards used to make journeys on the capital’s public transport network.
The NCA deputy director, Paul Foster, the head of the agency’s cybercrime unit, said: “We have been working at pace to support Transport for London after a cyber attack on their network, and to identify the criminal actors responsible.
“Attacks on public infrastructure such as this can be hugely disruptive and lead to severe consequences for local communities and national systems.
“The swift response by TfL following the incident has enabled us to act quickly, and we are grateful for their continued cooperation with our investigation, which remains ongoing.”]

Impacted Customers Contacted
TfL said it was contacting impacted customers as a precaution to warn that their email and bank account details could have been exposed, many of whom had applied for refunds on journeys made using Oyster cards.
It said the cyber-attack would also hold up the rollout of contactless travel to dozens of railway stations around south-east England, which had been due to allow commuters to travel ticket-free into London from 22 September.
Shashi Verma, TfL’s chief technology officer, said a thorough investigation was continuing in tandem with the NCA and the National Cyber Security Centre.
“Although there has been very little impact on our customers so far, the situation continues to evolve and our investigations have identified that certain customer data has been accessed,” Verma said. “This includes some customer names and contact details.”
“Some Oyster card refund data may also have been accessed. This could include bank account numbers and sort codes for a limited number of customers.
Pay-as-you go gone
Following the breach, all TfL staff will have to report to have to report to the transport body’s HQ in Southwark to reset their digital identities for email access.
TfL said the all-staff IT identity check would be done on appointments in the coming week and it did not expect any significant impact on customer journeys.
Verma added that this meant it was now not possible for TfL to carry out planned system changes to allow another 47 rail stations to operate pay-as-you-go contactless travel later this month, but it was working with the government and the rail industry to reschedule.
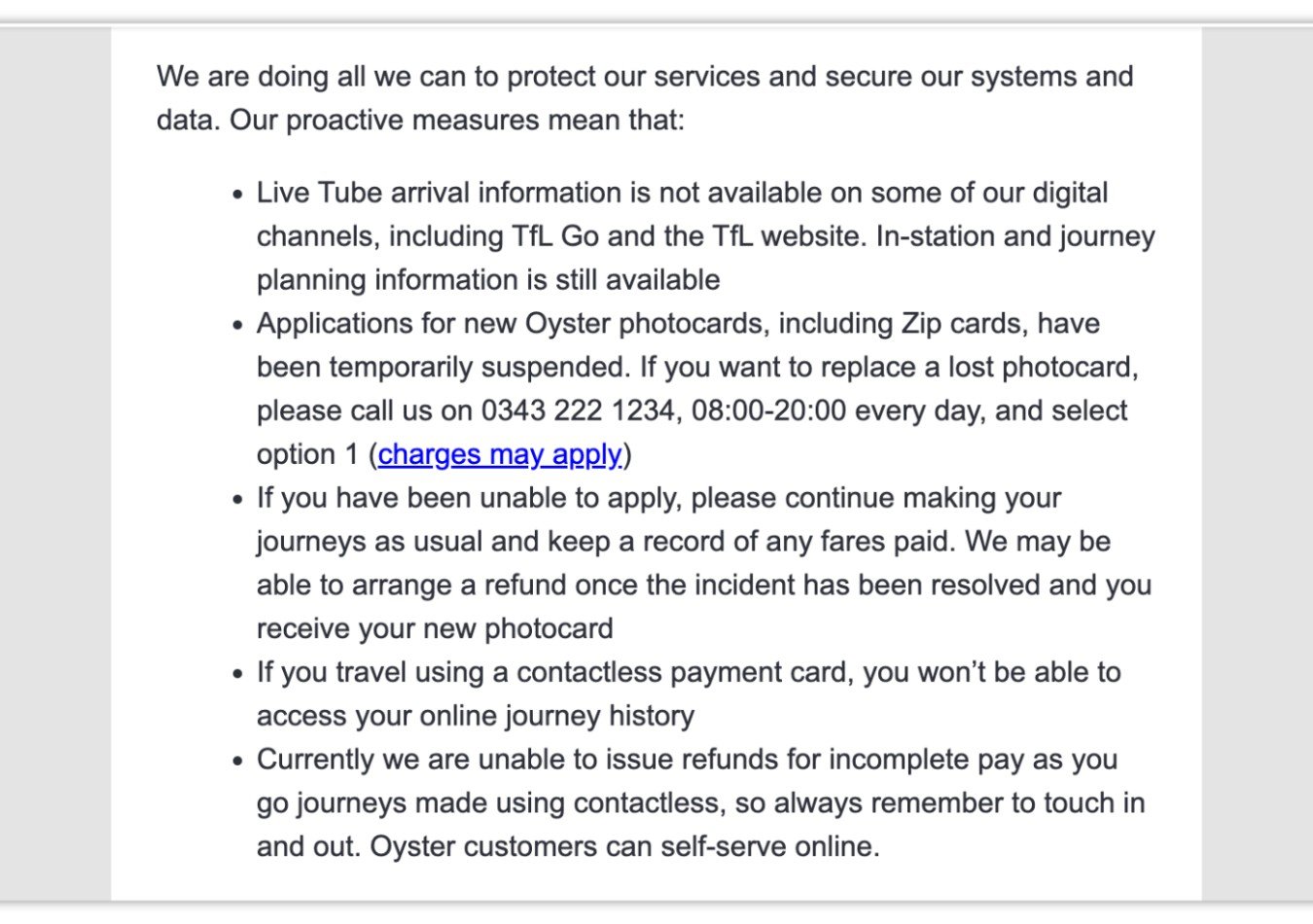
The attack has also affected live data feeds serving travel apps such as Citymapper and TfL Go, but public transport services have been running as normal and have not been directly affected. Many TfL office staff have been asked to work from home.
This has stopped customers accessing information including journey history and photocard registration as part of measures to tackle the breach.







Comments ( 0 )