Nineteen Train stations across the UK have been impacted by a cyber attack on National Rail’s Wifi network that showed passengers Islamophobic messages.
Manchester Piccadilly, Liverpool Lime Street, Birmingham New Street and 11 stations in London were affected by the cyber attack this morning, with commuters shown Islamophobic messages when they logged onto Network Rail's wifi system.
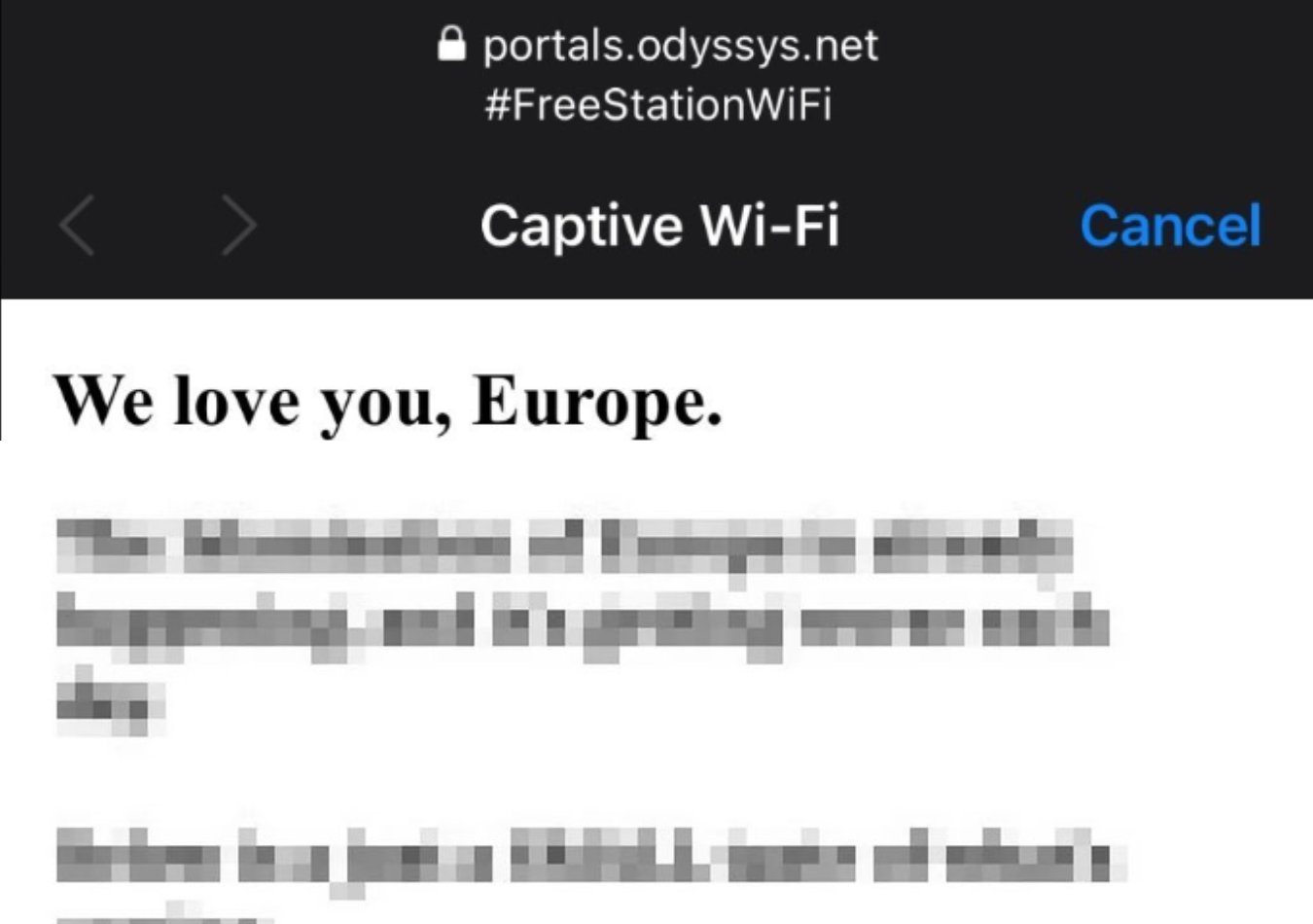
Passengers trying to log on to public WiFi at the Network Railway-managed stations were shown a message in place of the WiFi login page that contained a passage referring to a UK terror attack.
The message was displayed on people's devices when they logged onto Network Rail's wifi system. The system is run by a third party, Telent, with the actual internet service provided by another company, Global Reach.
Following investigations with Global Reach, Talent believes the attack came from someone working for the company running the WiFi homepage. In a statement, it said that the matter is now being dealt with by the police.
"An unauthorised change was made to the Network Rail landing page from a legitimate Global Reach administrator account and the matter is now subject to criminal investigations by the British Transport Police," Telent said in a statement.
Network Rail has suspended WiFi services at stations across the country following the incident. The only Network Rail-managed station not affected was London's St Pancras.
A Network Rail spokesperson said: "Last night the public WiFi at 19 of Network Rail's managed stations was subjected to a cyber security incident and was quickly taken offline.
"The incident is subject to a full investigation. The WiFi is provided by a third party, is self-contained and is a simple 'click & connect' service that doesn't collect any personal data.
"Once our final security checks have been completed, we anticipate the service will be restored by the weekend."

Third-party cyber attack
Network Rail said it believed other organisations, not just railway stations, had been affected.
"This service is provided via a third party and has been suspended while an investigation is underway," the spokesperson said.
The attack is just one of many recent third-party cyber attacks targetting UK critical infrastructure. Earlier this month, Transport for London (TfL) was hit by a cyber attack that saw employees being forced to work from home as systems remained offline.
“The recent cyber attack on a third-party public WiFi provider, in multiple UK railway hubs highlights the increased risk of supply chain attacks; as more and more organisations depend on external vendors for essential services, the chances of these attacks just keep increasing," said Sylvain Cortes, VP Strategy at Hackuity.
“This incident is a clear reminder of why organisations need strong risk-based vulnerability management and constant monitoring to isolate holes in any network before an attacker can slip through.”
Unlike the TfL attack, the National Rail cyber attack appears to only impact public wifi connections and the transport body’s internal IT systems remain intact.
But according to Akhil Mittal, senior security consulting manager at the Synopsys Software Integrity Group, this shouldn’t leave any room for comfort.
“What’s worrying is the growing trend of cyberattacks aiming not just to steal data but to manipulate public perception and create chaos,” Mittal told EM360Tech.
“The question is no longer if hackers will strike, but how disruptive they’ll aim to be. This incident is a clear signal for public service providers to tighten their security and ensure they can protect the trust people have in these vital networks."







Comments ( 0 )