The U.S. Federal Bureau of Investigation (FBI) has seized 48 domains providing services to conduct distributed denial of service (DDoS) attacks on behalf of other threat actors.
The mass takedown, announced yesterday in a public statement published by the U.S. Department of Justice (DoJ), also led to six people being charged for their alleged connection to the DDoS-for-hire platforms.
The DoJ reported that the ‘Booter’ or ‘Stresser’ websites "allowed paying users to launch powerful distributed denial-of-service, or DDoS, attacks that flood targeted computers with information and prevent them from being able to access the internet.”
Although claiming to offer services to assess the resilience of a paying customer’s web infrastructure, the DoJ noted that threat actors were using the platforms to attack millions of individuals and organisations around the world.
“Some sites use the term "Stresser" in an effort to suggest that the service could be used to test the resilience of one's own infrastructure,” FBI Special Agent Elliot out of the Alaska Office wrote in an affidavit filed in support of a court-authorised warrant to seize the sites.
“I believe this is a façade and that these services exist to conduct DDoS attacks on victim computers not controlled by the attacker,” he explained
One of the sites seized by the FBI, IPStresser[.]com ran for almost 13 years until its takedown, garnering more than two million registered users and launching approximately 30 million DDoS assaults between 2014 and 2022.

A collaborated effort against DDoS
The move arrives four years after the DoJ and FBI took similar steps in December 2018 to take down 15 domains advertising computer attack platforms.
It is part of an ongoing coordinated effort in collaboration with the UK, the Netherlands and Europol, codenamed operation POWEROFF, that serves to dismantle DDoS platforms.
DDoS-for-hire services have posed particular challenges for security agents due to customers being able to obtain services through a cryptocurrency payment and thus avoiding detection.
"These booter services allow anyone to launch cyberattacks that harm individual victims and compromise everyone's ability to access the internet,” United States Attorney Marin Estrada told BleepingComputer.
"This week's sweeping law enforcement activity is a major step in our ongoing efforts to eradicate criminal conduct that threatens the internet's infrastructure and our ability to function in a digital world,” he added.
Once the domains have been officially seized and transferred to DNS used by law enforcement, they will display a warning message warning that the websites have been seized and their services are illegal, as seen below:
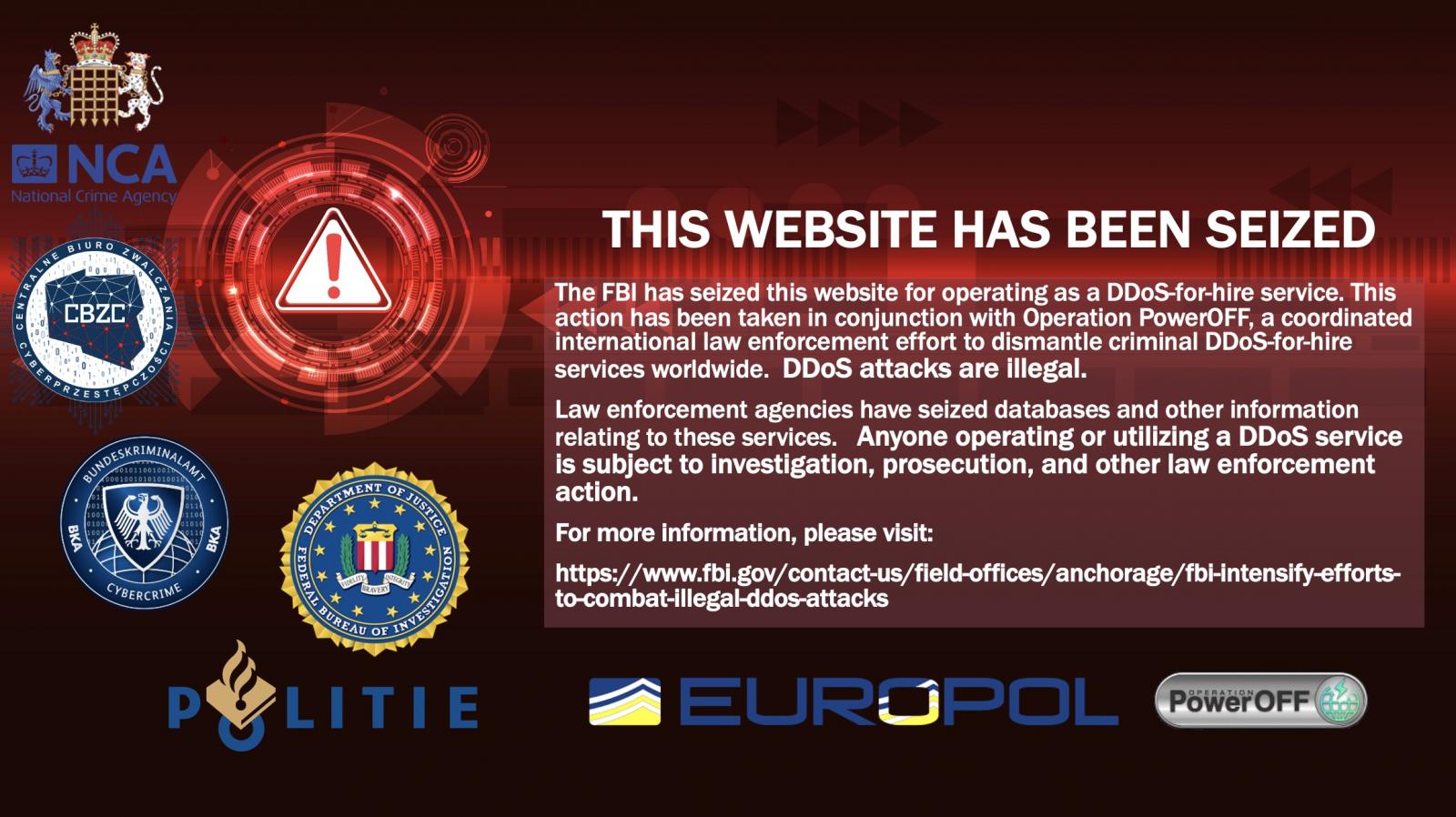
FBI is also working with the UK’s National Crime Agency, and the Netherlands Police to launch a campaign using targeted ads placed at the top of search engines when people search for booter services like those seized by the FBI.
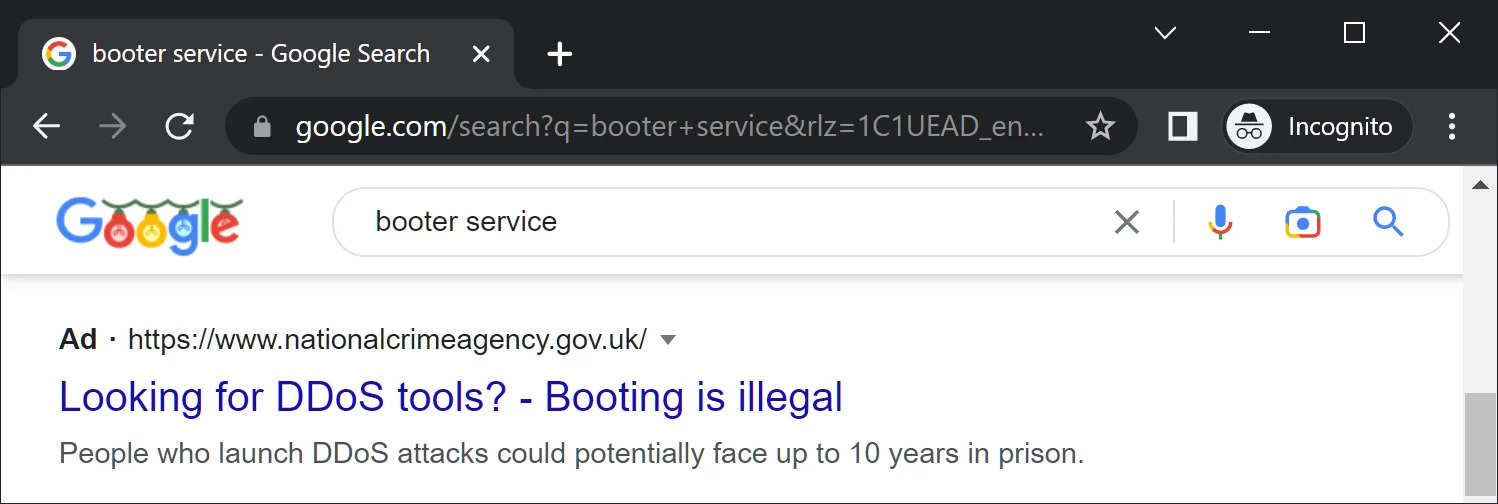
These warnings will lead to a Cyber Choices Page that offers information on how people “can make informed choices and use their cyber skills in a legal way, according to the site.
It is hoped that these collaborated efforts may help to deter threat actors from using DDoS-for-hire services and remind them of the cybercrime legislation
Flattening the DDoS curve
Criminal activity has surged worldwide over the past few years, with a staggering 90% of organisations reporting falling victim to cyber-attacks in the second half of 2022.
Next year, cybercrime is only set to worsen, potentially costing organisations around upwards of $8 trillion, according to Cybersecurity Ventures.
As the new year approaches, cybersecurity experts warn that newly evolved DDoS attacks such as the DDoS Botnets will pose the biggest challenge to the enterprise
“Due to the new nature of the malware – its impact is more likely to be that similar real-time emerging malware-related DDoS attacks like this one will be used in 2023, H.E. Dr Mohamed Al Kuwaiti, UAE Cyber Security Council explained.
It will be up to organisations to ensure they have apt security measures in place to prevent their attacks from causing serious damage to their organisations.
It is not known how much of an effect removing access to DDoS-for-hire will have on the number of attacks occurring, but it is hoped it may lower the barrier of entry for new malicious actors.
To read more about DDoS attacks, visit our dedicated Business Continuity Page.







Comments ( 0 )