Hypertext Transfer Protocol Secure (HTTPS) is not a box to tick. It is the baseline for trust, privacy, and integrity on the modern web. The protocol you choose to deliver content has real consequences — for data protection, regulatory posture, user experience, and even conversion.
Below, we unpack what HTTPS is, why it matters, how it works, where adoption stands, common pitfalls, and the practical steps teams can take to secure digital communication end to end.
From HTTP to HTTPS
The early web ran on Hypertext Transfer Protocol (HTTP) — quick, simple, and entirely in the clear. That simplicity came at a cost: anyone on the path could read requests, capture cookies, or tamper with content. As the web commercialised in the mid-1990s, Netscape introduced Secure Sockets Layer (SSL) to wrap HTTP in encryption. SSL 1.0 never shipped due to security flaws; SSL 2.0 arrived in 1995 and paved the way for “HTTP over SSL,” which evolved into HTTPS.
Today’s secure web runs on Transport Layer Security (TLS), the successor to SSL. TLS 1.3 — finalised in 2018 — tightened the design, removed weak ciphers, improved forward secrecy, and cut handshake latency. We still say “SSL certificates,” but modern HTTPS uses TLS under the hood. The shift from HTTP to HTTPS was gradual; now it’s essential to digital trust.
Why HTTPS matters
Encryption and confidentiality
At its core, HTTPS encrypts the connection between client and server. When you visit https://example.com, your browser and the server negotiate a cipher suite, conduct a handshake to agree keys, and then encrypt everything that follows.
The traffic is protected from passive observers — they cannot read page content, credentials, or form data. The application data uses symmetric encryption for speed; the handshake uses asymmetric cryptography and certificates to exchange the session key securely.
Integrity and authenticity
HTTPS is more than scrambling traffic. TLS adds message integrity to detect tampering and authentication to verify you’re talking to the real site, not an impostor. A certificate signed by a trusted Certificate Authority (CA) anchors that trust.
The padlock in the address bar indicates two things: the certificate chains to a trusted CA and the connection is encrypted.
Trust, SEO, and user perception
Security outcomes show up in business metrics. HTTPS underpins customer confidence by safeguarding sensitive data and assuring users they are on the legitimate site. Search engines have rewarded secure sites since 2014, and modern browsers flag HTTP as “Not secure.”
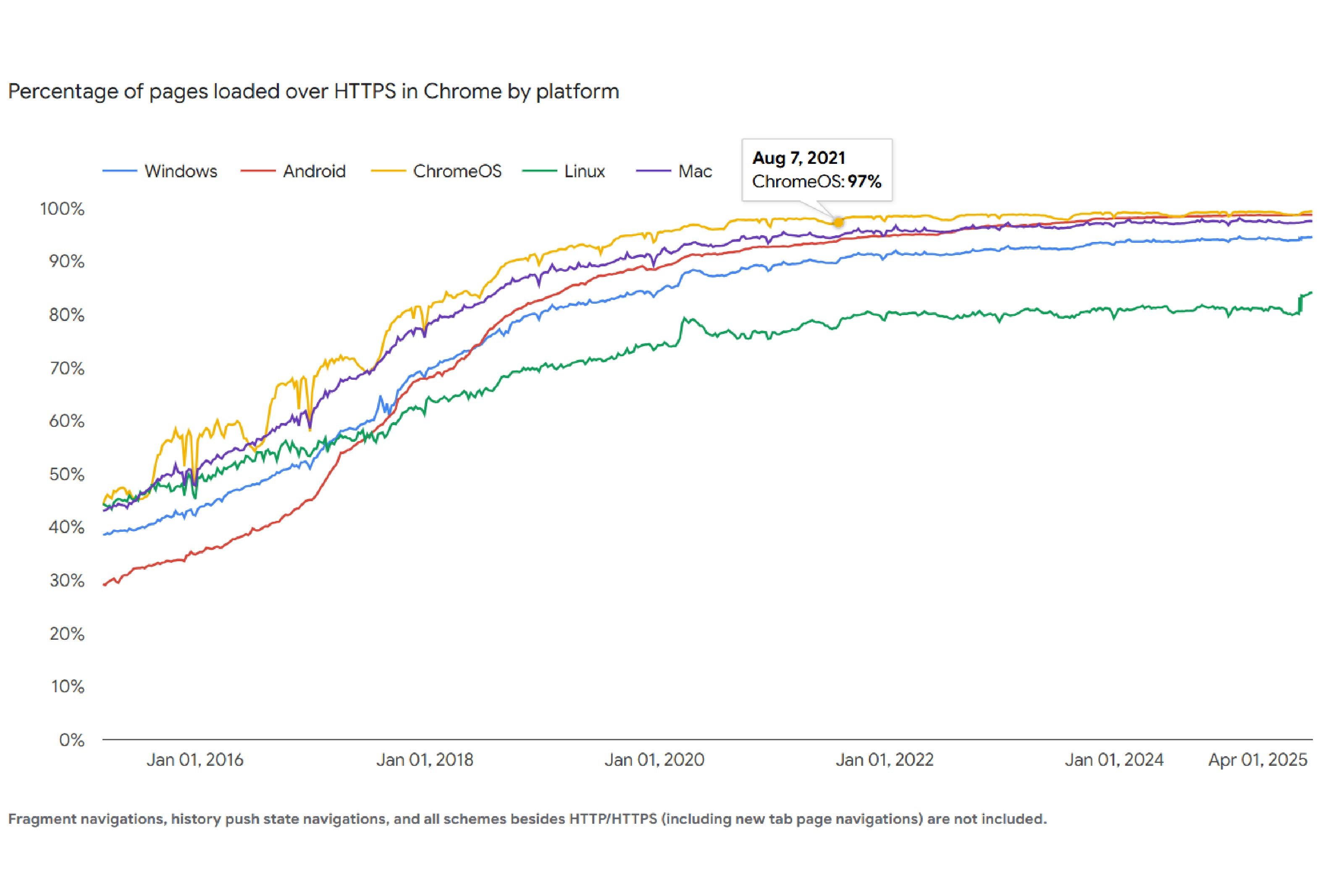
Many users bounce the moment they see that warning. Independent data sets also show how the web has moved: Google’s Transparency Report indicates that most Chrome browsing time happens over HTTPS, and W3Techs tracking shows the majority of websites now present valid TLS certificates. Security, trust, and visibility reinforce one another.
Functional benefits
A growing set of powerful web capabilities only work in secure contexts. Service workers, Push API, Payment Request API, geolocation, and other features are gated behind HTTPS to protect users. HTTP Strict Transport Security (HSTS) — defined in RFC 6797 — lets a site tell browsers to always use HTTPS and to auto-upgrade any HTTP attempts.
HSTS also blocks “click through” on certificate errors, closing down avenues for SSL stripping and downgrade attacks. With HSTS preload, major browsers ship a list of domains that must always be loaded over HTTPS, making even first visits safe.
How HTTPS works
Think of HTTPS as a short conversation that sets up a private tunnel, then moves your data through it.

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
- Hello from the browser: The client opens a connection on port 443 and lists the TLS versions and cipher suites it can use. It also sends a random value.
- Hello from the server: The server picks a compatible set of options, replies with its own random value, and presents a digital certificate that proves who it is.
- Prove the certificate is real: The browser checks the chain of trust, expiry, and revocation, and confirms the certificate’s subject matches the requested domain.
- Agree the secret: Using Diffie–Hellman or Elliptic Curve Diffie–Hellman, both sides derive a shared secret that even an eavesdropper cannot reconstruct. This gives you forward secrecy.
- Make the working keys: The browser and server turn that shared secret and the random values into symmetric session keys.
- Lock the tunnel: Each side sends a small “finished” message using those new keys to prove they hold them. From this point, the HTTP traffic runs inside the encrypted tunnel.
For repeat visitors, session resumption lets both sides reuse key material safely, cutting the time spent on the handshake without reducing security.
Choosing and managing certificates
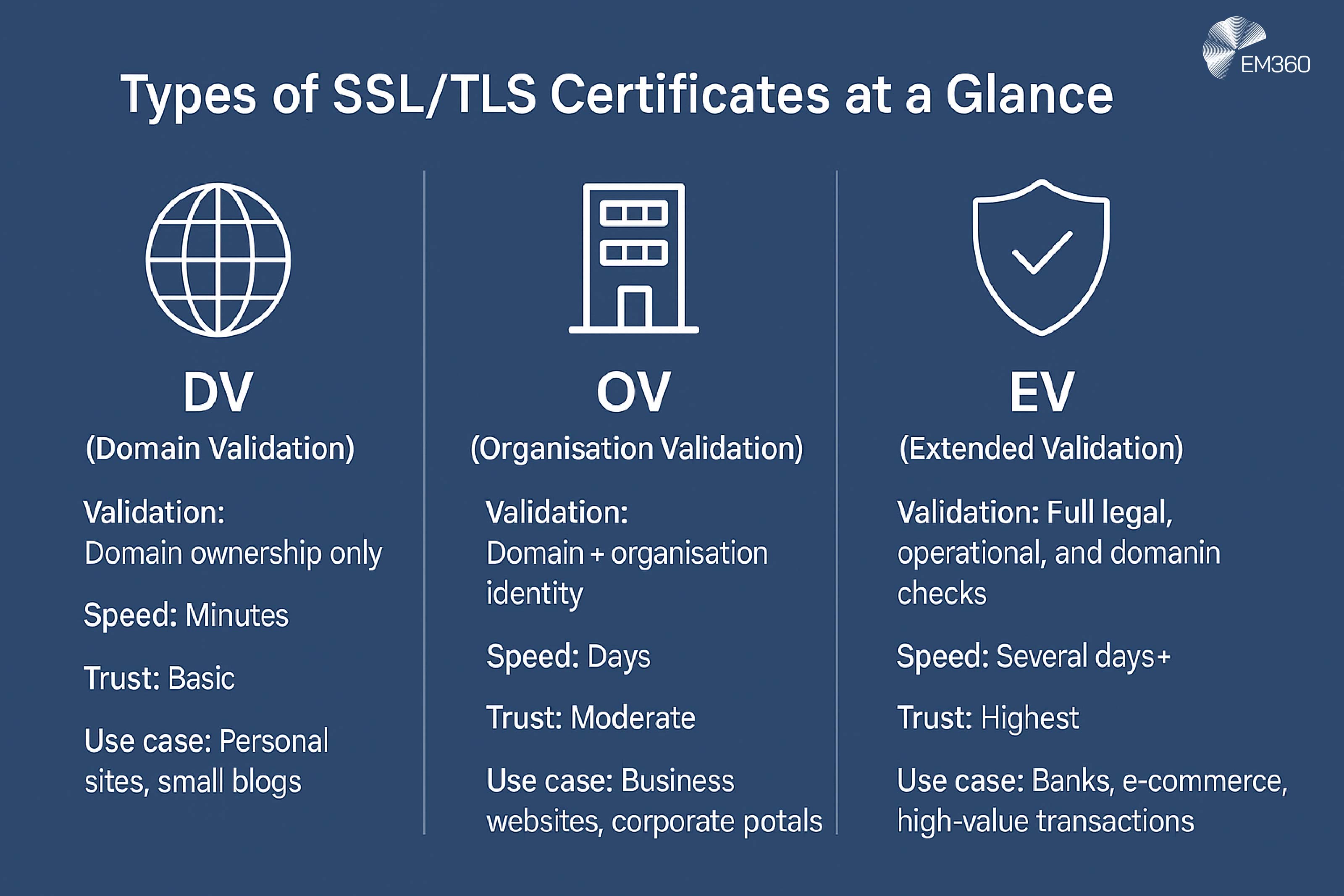
Not all certificates are equal. Validation level influences user and auditor confidence, and domain coverage affects scope and cost.
- Domain Validation (DV) — Proves control of the domain (for example, via DNS or email). Fast to issue and by far the most common. It secures the transport but does not verify the legal entity behind the site.
- Organisation Validation (OV) — Adds checks that the operator is a legally registered organisation. The issuing authority verifies company details — name, address, phone — and includes the organisation’s name in the certificate. It takes longer to obtain but gives higher credibility.
- Extended Validation (EV): The strictest option. The provider confirms legal status, operational history, and domain control. EV certificates make the company name visible in certificate details and are still the standard for sectors like banking and finance.
Coverage works differently:
- Single-domain: Protects one fully qualified domain.
- Wildcard: Protects a domain and all of its first-level subdomains (for example, *.example.com).
- Multi-domain/SAN secures multiple, unrelated hostnames in one certificate.
Choosing correctly reduces cost and complexity while ensuring every public surface is covered.
Adoption and what’s driving it
HTTPS adoption has surged in the last decade. Public datasets show strong progress: the majority of Chrome browsing time is now over HTTPS, and most websites present valid certificates. Several forces drove this shift:
Inside a Social Graph Collapse
A case study in weak mobile-era adaptation, algorithm shifts, and feature deprecation eroding network effects in visual platforms.

- Let’s Encrypt and automation — Since 2015, free and automated certificates via ACME made HTTPS the default. No invoices. No calendar reminders. Certificates issue and renew themselves.
- Search and browser pressure — Google treats HTTPS as a ranking signal. Chrome and other browsers label HTTP as “Not secure.” Many modern APIs only run in secure contexts. Upgrading stopped being optional.
- HSTS and preloading — HSTS reduces downgrade risk and makes upgrades sticky; preloading ensures first-visit safety.
- Regulation and assurance — Frameworks such as GDPR and South Africa’s POPIA expect “appropriate technical and organisational measures” to protect personal data. HTTPS is a baseline control that auditors recognise.
Adoption is not uniform. Gaps still happen. Legacy stacks, forgotten subdomains, and old API endpoints slip through. Map the estate across public sites, internal apps, and services. Close what you find, then keep it current.
Vulnerabilities and what they taught us
Incidents like BEAST, POODLE, Heartbleed, DROWN and ROBOT were not trivia, they reshaped how we configure TLS. Here is what each one actually means for your estate today, and what to do about it.
BEAST (2011)
What it exploited: TLS 1.0 in CBC mode with predictable IVs, leading to session cookie theft.
What matters now: You should not be serving TLS 1.0 at all. Prefer AEAD ciphers that avoid CBC altogether.
Do this: set a protocol floor of TLS 1.2, target TLS 1.3, allow only AEAD suites such as AES-GCM and ChaCha20-Poly1305, and remove legacy CBC suites from 1.2.
POODLE (2014)
What it exploited: forced downgrade to SSL 3.0, then a padding oracle to recover cookies.
What matters now: Downgrade avenues are the problem, not just SSL 3.0.
Do this: disable SSL 2.0 and SSL 3.0 everywhere, enable TLS_FALLBACK_SCSV on edges and load balancers, and enforce a strict minimum of TLS 1.2 so clients cannot negotiate anything weaker.
Heartbleed (2014)
What it exploited: the OpenSSL heartbeat extension, which leaked server memory and could expose private keys and credentials.
What matters now: if you were exposed in that window, assume keys may have leaked, logs will not prove otherwise.
Do this: patch promptly, rotate private keys and reissue certificates, revoke the old ones, clear session tickets, and keep a standing key-rotation runbook so this is muscle memory, not a scramble.
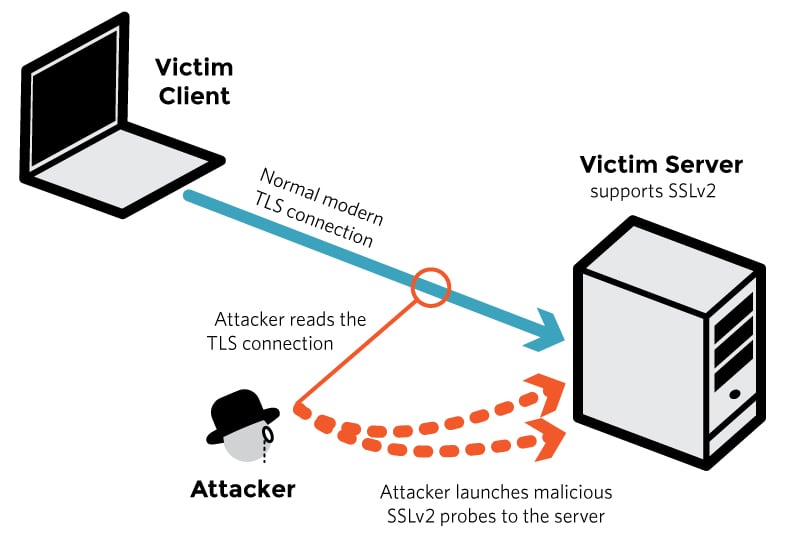
DROWN (2016)
What it exploited: a cross-protocol attack that used any server still speaking SSLv2, often a forgotten service that shared the same certificate or key, to weaken TLS.

Why Cyber Attacks Are So Costly
Explores how modern attacks convert data loss and downtime into escalating fines, customer churn, and strategic security spend.
What matters now: legacy services anywhere in the environment can put modern endpoints at risk if they share keys.
Do this: disable SSLv2 and export ciphers across all services, separate keys and certificates per service, and audit non-web endpoints such as mail, VPN and admin interfaces for old protocol support.
ROBOT (2017)
What it exploited: RSA padding oracles in TLS implementations, enabling decryption and signature forgeries.
What matters now: static RSA key exchange is the weak link.
Do this: remove TLS_RSA_* key exchange from your policy, use ECDHE for forward secrecy, and keep device firmware, proxies and TLS libraries current so vendor fixes actually land.
The lesson across all five is the same: protocol floors, strong ciphers, and timely patching prevent yesterday’s mistakes from becoming tomorrow’s breach.
Best practices that hold up
- Use modern TLS only: Support TLS 1.2 and TLS 1.3. Disable SSL, TLS 1.0, and TLS 1.1. Prefer ECDHE suites. Turn off RC4 and MD5. Validate against a recognised baseline and run a server test.
- Automate certificates: Expiry is the number one cause of outages. Use ACME clients such as Certbot for issue and renew. In larger estates use a certificate management platform with inventory and alerts.
- Enforce HSTS and set cookies correctly. Add Strict-Transport-Security with a long max-age and includeSubDomains. Consider preload once everything is on HTTPS. Mark cookies Secure and HttpOnly. Set SameSite where appropriate.
- Eliminate mixed content. Do not load any HTTP assets on HTTPS pages. Fix references. Use Content Security Policy with upgrade-insecure-requests and reporting to catch stragglers.
- Harden and monitor. Keep web servers, TLS libraries, frameworks, and proxies updated. Subscribe to advisories and scan for weak configs. A CDN with managed TLS and DDoS protection can simplify the edge.
- Make it easy for teams. Ship secure defaults in frameworks and templates. Redirect to HTTPS automatically. Enable HSTS out of the box. Explain to stakeholders how HTTPS affects reputation, funnel health, and compliance.
Compliance As A Board Priority
Why boards are shifting from ad hoc controls to integrated compliance platforms to manage DMA, GDPR and AI obligations at scale.

Beyond browsers
HTTPS is not just for websites. It is also table stakes for REST and GraphQL APIs powering mobile apps and microservices. Many auth schemes depend on the confidentiality of OAuth bearer tokens; sending them over HTTP is an open invitation to attackers.
Mobile platforms enforce strong norms as well. Apple’s App Transport Security (ATS) expects HTTPS with modern TLS by default, and Android’s guidance encourages secure transport. In the IoT world, unencrypted HTTP has led to compromise and botnets. Provision device identities, enforce TLS on device-to-cloud and device-to-device channels, and plan for secure firmware updates throughout the lifecycle.
What’s next for HTTPS
Performance with TLS 1.3
TLS 1.3 reduces round trips and removes legacy baggage, narrowing the gap between HTTP and HTTPS performance. 0-RTT resumption allows near-instant reconnects for returning clients, subject to replay-safe designs at the application layer.
Privacy with Encrypted Client Hello
The Server Name Indication (SNI) value in the handshake historically leaked the destination hostname. Encrypted Client Hello (ECH) aims to encrypt that metadata, making network surveillance and domain-based censorship harder. As ECH matures, expect privacy benefits without sacrificing operability.
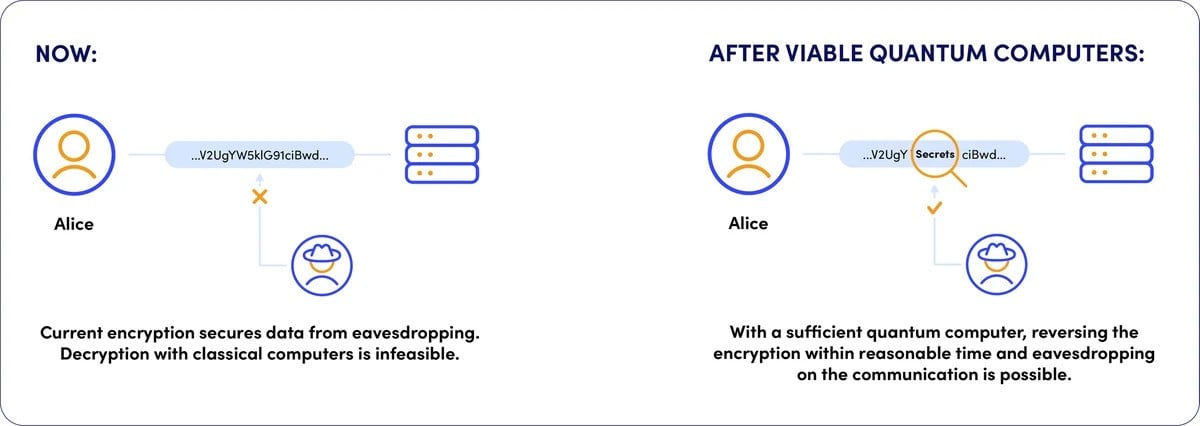
Preparing for post-quantum
Large-scale quantum computers would threaten widely deployed asymmetric algorithms (RSA, ECC). Standards bodies are advancing post-quantum cryptography (PQC). Over time, TLS stacks, HSMs, and certificate ecosystems will migrate. For now, keep an eye on NIST’s PQC standardisation and the emergence of hybrid (classical + PQC) key exchange options.
Encrypting the internal estate
A zero-trust mindset assumes hostile networks and verifies every request. Encrypting internal traffic — service mesh with mutual TLS (mTLS), API gateways with strict policies — limits lateral movement and shrinks blast radius. “HTTP by default” inside the perimeter is a habit to retire.
Final Thoughts: HTTPS Is The Baseline For Digital Trust
HTTPS is no longer optional. It protects users against eavesdropping and tampering, preserves content integrity, unlocks modern web capabilities, improves discoverability, and supports compliance. But it is not a one-time project. The details matter: current protocols, hardened ciphers, automated renewals, HSTS, clean asset pipelines, and informed teams.
The web is moving toward an encrypted-by-default future. Organisations that commit to HTTPS everywhere — public sites, APIs, internal services, and devices — build resilience, strengthen their brand, and meet user expectations. If you need support shaping a secure-by-design approach, explore more of EM360Tech’s resources and expert insights.







Comments ( 0 )