Modern revenue teams don’t run on one platform anymore. They run on an ecosystem. A CRM platform, an engagement tool, a conversation intelligence layer, data enrichment, routing, chat, meeting scheduling, automation, analytics, and a long tail of plug-ins that exist because someone needed to move faster this quarter.
That stack can be brilliant for growth. It can also become a quiet concentration of sensitive data and privileged access that isn’t governed like critical infrastructure. Not because anyone’s careless, but because sales technology tends to be treated like productivity tooling while it behaves like a distributed system.
The hidden risk is rarely “a tool is insecure.” It’s the gap between how much access the stack has and how little end-to-end visibility most organisations have into the identities, integrations, and data flows that keep it running.

What Is B2B Sales?
B2B sales is the process of selling products or services from one business to another, usually through a longer buying cycle with multiple stakeholders. In practice, that means sales is less about one conversation and more about coordinated execution across marketing, sales development, account executives, customer success, and finance.
A modern B2B motion is multi-touch and data-driven. It relies on accurate contact data, clean account hierarchies, real-time intent signals, and consistent messaging across channels. It also relies on speed. Leads need to be routed, meetings need to be booked, follow-ups need to happen, and forecasts need to reflect reality closely enough for leadership to make decisions.
That’s where the B2B sales stack comes in. It’s the operational layer that turns signals into action. It also becomes a place where valuable information accumulates, including customer communications, prospect lists, pricing context, deal strategy, and the metadata that explains who spoke to whom and when.
What Makes a Modern B2B Sales Stack So Complex
Most sales stacks didn’t start as stacks. They started as a CRM and a few add-ons. Then the company grew. The market tightened. Sales cycles changed. Teams added tools to solve very specific problems, and each tool introduced new permissions, new syncs, and new dependencies.
The result is often SaaS sprawl that feels invisible from the inside because every addition made sense at the time. One tool enriches contact records, another logs calls, another automates sequences, another routes inbound, another analyses sentiment, another pushes data into a warehouse, another pulls data back out.
Complexity isn’t just “more tools.” It’s more connections. Every integration is a decision about what data can move, who can access it, and what happens when something goes wrong. When those decisions are made by different teams at different times, the stack can become hard to reason about as a single system.
That’s why risk hides here. Not because sales teams are reckless, but because the architecture is emergent. Convenience drives adoption faster than governance can keep up.
Where Security Risk Actually Hides in Sales Technology
Security risk in sales technology rarely shows up where organisations expect it to. It doesn’t sit neatly inside a single tool or announce itself through an obvious misconfiguration. It tends to emerge in the spaces between platforms, where access is shared, data moves automatically, and ownership becomes blurred.
Over-permissioned connected apps and OAuth grants
Sales platforms are built to connect. That’s the point. The problem is that the easiest way to connect is often the least controlled way to connect.

When AI Agents Reshape Security
Why boards must treat autonomous agents as governance choices and redesign controls around authority, identity, and blast radius.
A third-party integration might request broad access to your CRM to “work properly,” and it can be granted in minutes by a user with the right permissions. Once that access is granted, it can persist far longer than anyone remembers, especially when authorisation is handled through connected apps that sit outside normal user lifecycle controls.

If an attacker steals or abuses OAuth tokens, they don’t need a password prompt or a second factor in the moment. They have the authorised session, which means the behaviour looks legitimate unless you’re actively monitoring for unusual API patterns.
The hidden risk isn’t OAuth itself. It’s long-lived access paired with weak review habits. If nobody’s asking what an integration can do today, access tends to drift toward “whatever it asked for at the beginning.”
Identity sprawl beyond human users
Most organisations have at least a basic process for employee access reviews. Sales stacks complicate that because a large portion of access isn’t tied to a person at all.
Service accounts, automation users, integration identities, bots, webhooks, and background jobs create a layer of non-human access that often has broad permissions because it’s “operational.” That layer is rarely held to the same standard as a human user. It’s also rarely mapped cleanly to business ownership.
Single sign-on can help, but it doesn’t automatically solve authorisation. A user can be properly authenticated and still have access to far more than they should. Worse, a non-human identity can be perfectly “valid” while behaving in ways nobody’s watching.
This is how identity and access management becomes a sales stack risk. It isn’t only about employee logins. It’s about the identities you don’t see in the org chart.
Data duplication across the revenue pipeline
Inside Zero Trust Network Design
Break down how SSE, SASE and ZTNA vendors rewire connectivity, from device posture checks to microsegmentation across hybrid and multi-cloud.

Revenue data rarely stays in one place. Prospect records flow from marketing automation into the CRM. Enrichment tools append new details. Engagement platforms copy contact lists and log activity. Conversation intelligence tools store recordings and transcripts. Analytics layers pull everything into dashboards. Sometimes the same dataset ends up in half a dozen places with slightly different retention, access rules, and audit trails.
That duplication matters because it expands the blast radius. One compromised system can expose data that leadership assumed was “in the CRM.” It also increases the chances that sensitive information appears where it shouldn’t, like access tokens pasted into notes, deal strategy copied into a shared field, or customer details exported into spreadsheets for convenience.
When data moves through a revenue pipeline, the question isn’t only “where is it stored?” It’s also “how many copies exist, and who can pull them out quickly?”
Shadow SaaS inside revenue teams
Shadow SaaS isn’t always rogue. It’s often a response to friction. A rep installs a browser extension because it saves time. A team signs up for a freemium tool to test a workflow. A manager adds a plug-in to improve reporting. It works, so it stays.
The risk is that these tools can end up with meaningful access without going through procurement, security review, or even basic inventory. They may connect directly to the CRM, email accounts, calendars, and communication platforms. They may also collect data in ways you didn’t intend, then store it in places you don’t control.
If security teams only look at sanctioned platforms, they miss the layer where fast adoption lives. That’s the problem with shadow IT in revenue operations. It survives because it solves real problems, not because someone wants to break rules.
Why Traditional Security Models Miss Sales Stack Risk
Many security programmes are built around infrastructure and endpoint realities. Networks, devices, patching, identity for employee systems, and visibility into central platforms. Sales stacks sit in a different ownership model.

Mitigating Breach Risk with MFA
Quantify how layered verification reduces account takeover exposure, and what to demand from vendors to address SMS, token and biometric weaknesses.
RevOps, marketing operations, and sales enablement often own tool selection and configuration. Security teams may own policy. IT may own identity. Data teams may own the warehouse. Legal may own regulatory responses. Everyone touches the stack, but no one team fully “owns” the risk end-to-end.
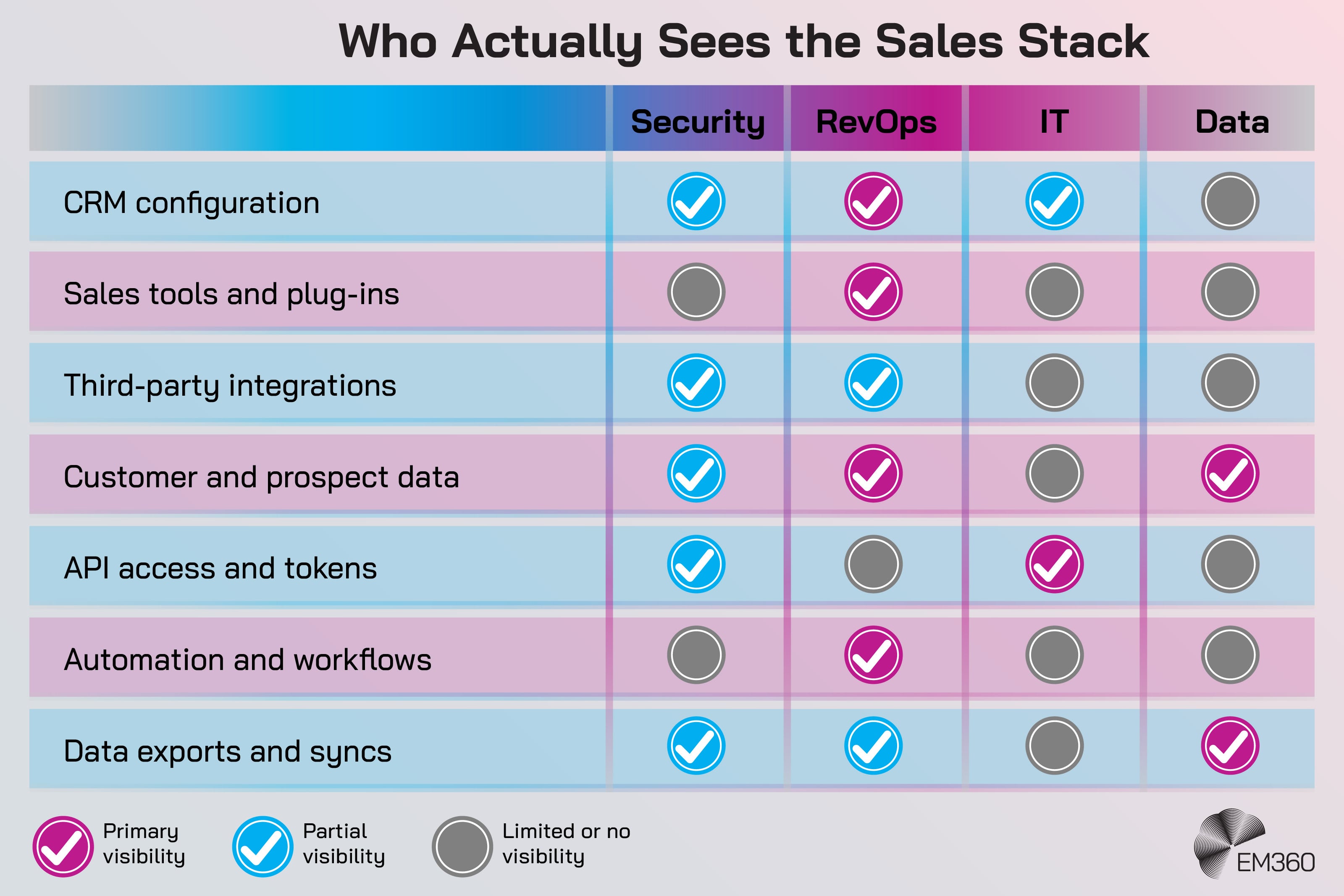
That’s how accountability fractures. When something goes wrong, organisations discover they don’t have a single, reliable map of the sales stack, its integrations, and its access paths. They have partial visibility in different tools, and those tools don’t always agree.
This isn’t a tooling problem. It’s a governance design problem. Sales stacks are cross-functional by nature, so security controls have to be cross-functional too.
The Business Impact of Sales Stack Breaches
It’s easy to treat sales stack security as technical hygiene until you translate the impact into business outcomes.
A breach in revenue tooling can erode customer trust quickly because it touches communication. Prospects and customers don’t care which system was compromised. They care that their data was exposed and that the company didn’t prevent it.
There’s also operational disruption. If teams lose confidence in the CRM or engagement tools, pipeline execution slows. Sales cycles lengthen. Forecasting becomes less reliable. Leadership decisions become riskier because the data they rely on is suddenly suspect.
Compliance exposure can follow. The stack often contains personal data, communications, and records that fall under regulatory expectations depending on region and industry. When the data has been duplicated across multiple tools, incident response becomes harder because discovery takes longer and confidence is lower.
The long-tail impact is reputational. A company can recover from a single incident. It’s harder to recover from the perception that basic governance didn’t exist where it mattered.
How Security and Revenue Teams Can Reduce Risk Without Slowing Growth
Reducing risk in the sales stack doesn’t require slowing teams down or locking tools behind layers of approval. It requires shifting focus from control after the fact to clarity up front.
Map the full sales stack and its access paths
Why UEM Now Anchors Security
See how unified endpoint platforms secure a dispersed workforce and centralize control across laptops, mobiles and IoT devices.

Visibility isn’t a one-time inventory exercise. It’s a living map of what’s connected, what data is flowing, and which identities have access. Asset inventories that stop at “these are our core tools” won’t catch the plug-ins, the OAuth grants, the enrichment syncs, and the automation users that create real exposure.
A practical approach is to map the stack as a set of access paths. Which tools can read from the CRM. Which tools can write to it. Which tools can export. Which identities can grant access. Once you can see the paths, you can prioritise the ones that create the most risk.
Apply least privilege to integrations, not just people
Organisations often do role-based access control for employees, then treat integrations as exceptions because they “need access to work.” That’s where permissions drift.
Least privilege should be applied to integrations as a design principle. If an enrichment tool only needs to read account and contact fields, it shouldn’t have broad export permissions. If a scheduling tool only needs calendar availability, it shouldn’t have access to email content. If a tool claims it needs full admin access to function, that’s a procurement and risk conversation, not a technical footnote.
The goal isn’t to block integrations. It’s to keep them honest and scoped.
Treat tokens and APIs as high-value assets
Token access is often treated as plumbing. In practice, tokens are credentials. They’re just credentials that don’t look like passwords.
If you’re serious about API security, you need to monitor for behaviours that indicate misuse: unusual volumes of API calls, mass exports, access from unfamiliar locations, abnormal query patterns, and integrations suddenly requesting new permissions. Some of this is available through native platform logging, and some may require centralised monitoring, but the principle stays the same.
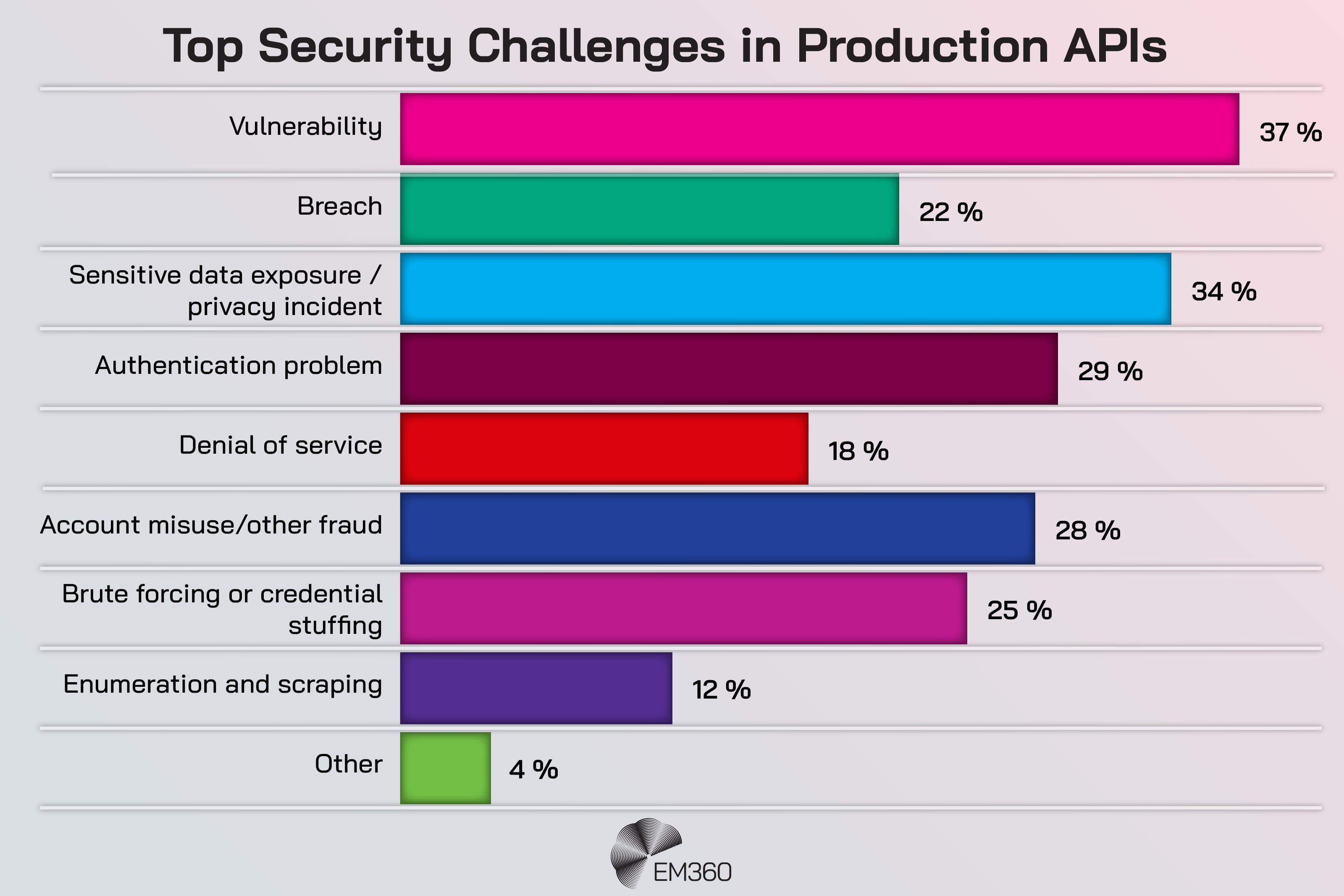
Tokens should also have lifecycle discipline. If you can’t answer who owns a token, what it enables, and when it was last reviewed, it’s a liability.
Build shared ownership between security and RevOps
Security can’t govern what it doesn’t understand, and RevOps can’t reduce risk if security only shows up to say no.
A workable model is shared ownership with clear rhythms: joint quarterly reviews of integrations and permissions, a defined process for approving new tooling, and shared metrics that reflect both speed and safety. If RevOps is measured only on velocity, shadow SaaS will keep thriving. If security is measured only on control, revenue teams will keep working around it.
The organisations that get this right treat sales stack security as operational resilience. It supports growth because it reduces surprise.
What to Look for When Assessing Sales Tech Vendors
Vendor assessments can become checkbox theatre. The goal isn’t to produce a procurement document. It’s to identify whether a vendor will reduce your risk or quietly amplify it.
Start with access scope. What permissions does the tool request, and can it operate with restricted access? Mature vendors can explain why each permission is needed and offer configuration paths that reduce exposure.
Look at identity support. Does it support single sign-on and granular roles? Can you enforce strong authentication? Can you limit admin privileges? Can you audit who changed what?
Ask about data handling. Where is data stored? How long is it retained? Can you control retention? Can you delete data reliably? Does the vendor support logging that helps you investigate abnormal behaviour?
Finally, look for operational maturity. How does the vendor communicate incidents? What is their approach to security testing? How do they manage third-party dependencies? You’re not trying to find a perfect vendor. You’re trying to avoid vendors that normalise broad access, vague answers, and weak auditability.
That’s the real centre of third-party risk management in the sales stack. It’s less about paperwork and more about whether the vendor behaves like a responsible steward of access.
Final Thoughts: Sales Stack Security Is a Revenue Responsibility
Modern sales stacks concentrate valuable data and privileged access in systems designed for speed, not scrutiny. The risk doesn’t come from sales teams doing the wrong thing. It comes from the stack behaving like critical infrastructure while still being governed like a collection of tools.
Organisations that want secure growth will need to treat revenue systems as part of their core security surface area, with shared ownership across security, IT, and RevOps. The companies that align those teams early won’t just reduce breach risk. They’ll make faster decisions with fewer blind spots.
EM360Tech covers the practical realities at that intersection, where security decisions have to hold up in the real world and still support how modern organisations actually sell.







Comments ( 0 )