The increasing adoption of cloud comes with new complexities that make it challenging for organizations to manage their infrastructure, applications, and data.
From challenges managing hybrid-multi-cloud environments to misconfigurations within specific systems and solutions, this increasing complexity makes it difficult to spot and address potential vulnerabilities in IT systems.
For security teams, the need to identify and mitigate security threats within cloud environments has become crucial.
Gartner forecasted a 24% growth in spending on cloud security in 2024, making it the highest growth sector across the security and risk management market.
While this transition offers numerous benefits, it also presents new challenges and opportunities for cyber-criminals to exploit vulnerabilities in cloud-based systems.

So how do organizations tackle the growing challenges of cloud environments?
This is where Wiz comes in. This article tells you everything you need to know about WIZ security solutions, including what it is, some of its key features, and its use cases.
What is Wiz?
Wiz is a unified cloud security platform that provides prevention and response capabilities to help security teams identify and mitigate risks in their cloud environments.
The platform combines prevention and response capabilities, allowing security and development teams to collaborate and build a secure cloud infrastructure. This ensures that security is integrated into the development process from the initial stages itself.
Wiz also helps identify and tackle vulnerabilities before they are exploited and efficiently responds to incidents upon detecting threats in real time, providing tools to immediately contain and remediate vulnerabilities and threats.
The platform enables organizations to rapidly identify and remove the most pressing risks in the cloud. It employs an agentless approach – a single API connector per cloud and Kubernetes environment to scan deep within every cloud resource.
Wiz also analyzes cloud stack and evaluates cloud design and risk factors such as internet exposure, software and configuration vulnerabilities, identities, secrets, and malware. Based on this data, it conducts a contextual analysis using a cloud graph to detect the toxic combinations that make the cloud susceptible to a breach.
It also provides a cloud control workflow to manage security, DevOps, and design through a single workflow. This allows teams to gain visibility into all cloud security risks – whether they be within DevOps environments, the software supply chain, or the cloud infrastructure itself.
How does Wiz work?
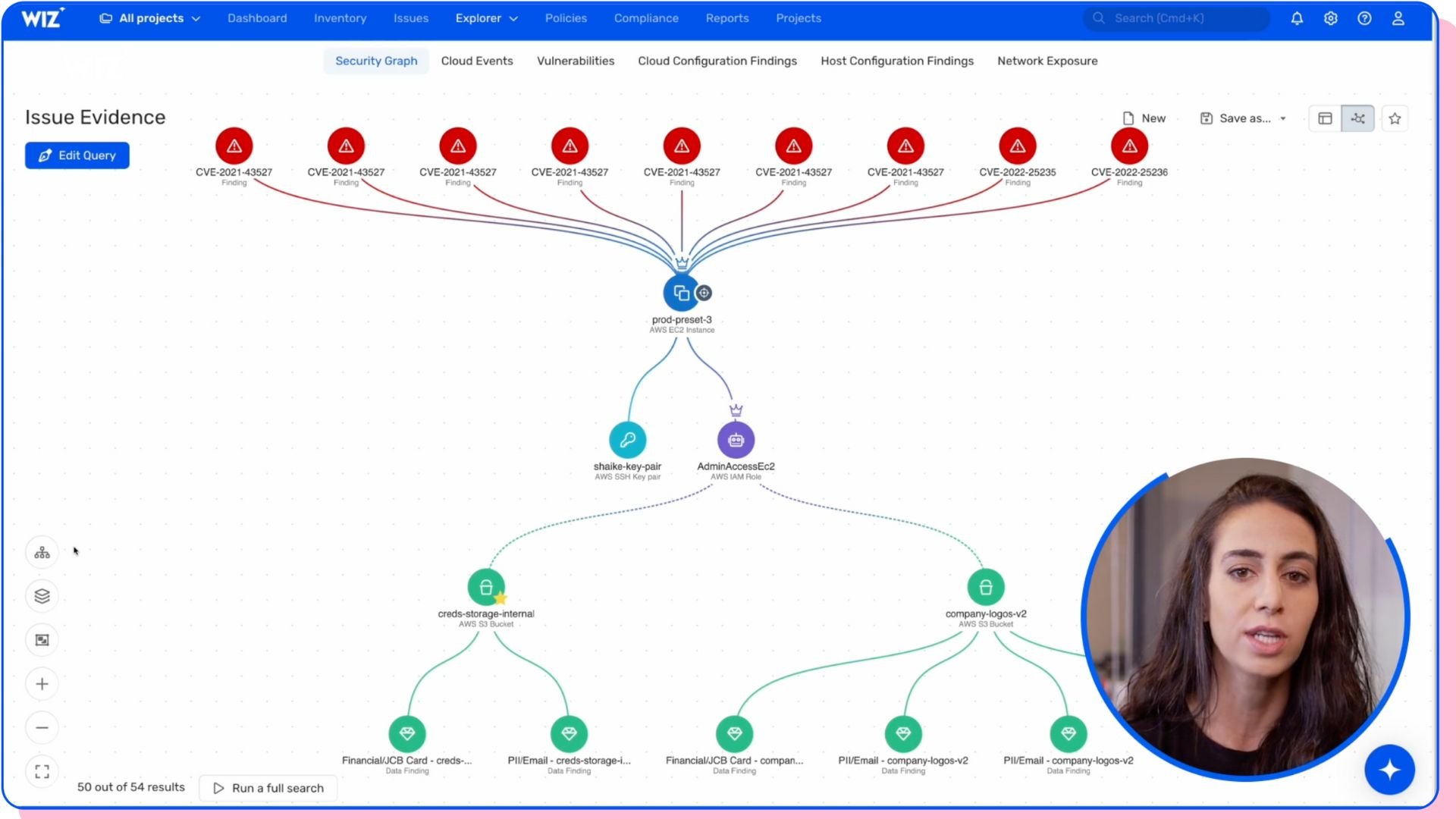
Wiz leverages machine learning (ML) to investigate huge amounts of data and pinpoint patterns showing malicious activity or vulnerabilities.
The platform is designed with algorithms that continuously learn and adapt, improving their accuracy over time, and can be integrated with public cloud platforms like AWS, Azure, GCP, OCI, Alibaba Cloud, and Kubernetes.
Through seamless integration with major cloud providers, Wiz rapidly identifies and removes the most critical risk factors from these cloud platforms. It also allows them to leverage their native security features into cloud environments, presenting deeper insights as a result.
The unified cloud security platform also monitors and detects anomalies that could be signs of security threats by monitoring the behavior of systems and users, including spotting unusual traffic, unauthorized access attempts, or abnormal resource consumption.
Key features of Wiz
1. Seamless and agentless scanning
Wiz offers a seamless and effective cloud security solution that enables easy and quick integration with an organization’s cloud environment through API. It provides comprehensive coverage for various resources including PaaS resources, virtual machines, containers, serverless functions, or sensitive data stored in public buckets, data volumes, and databases without disrupting your business operations or requiring ongoing maintenance. This minimizes maintenance and ensures organizational operations continue uninterrupted. The platform also scales easily to accommodate any cloud environment without affecting an organization’s resource or workload performance.
2. Foundational risk assessment
When Hackers Define Strategy
Why boards must use offensive security insights to close the gap between perceived protection and real cyber exposure.
Wiz presents a comprehensive cloud security solution that helps organizations identify and address vulnerabilities across their cloud environment. The platform enforces correct configurations across cloud resources and continuously monitors workloads for vulnerabilities, malware, and exposed secrets across packages, libraries, and applications. It also estimates required permissions to maintain the least privileged access, reducing the risk of authorized access to sensitive information especially. The platform champions a list of security tools as part of its cloud security solution including CSPM, KSPM, CWPP, IaC scanning, CIEM, and DSPM. These are described in more detail further down the article.
3. Graph visualizations
Wiz’s graph visualization tool allows users to a view clear and intuitive approach to comprehending the connection between cloud environments in use. It visually maps out the relationships between different technologies, depicting potential pathways that could lead to a security breach. By examining these connections, an organization can identify vulnerabilities and take measures to improve cloud security posture.
4. Systematic elimination of risk
Wiz proactively and systematically detects and eliminates the most critical security vulnerabilities in cloud environments through analysis of configurations, vulnerabilities, network settings, identities, access controls, secrets, and data storage. It spotlights combinations of issues that pose the greatest threat, allowing an organization to focus its security efforts on priority. This reduces the organization’s exposure to cyber-attacks.
5. Real-time threat assessment
Wiz has a threat center that provides real-time information on the latest security threats and vulnerabilities impacting the user organization’s workloads. It leverages Wiz Research and third-party threat intelligence to rapidly identify potential risks and implement action immediately. The organization can choose to remediate manually or automate the process as the platform responds effectively to emerging threats.
6. Developer collaboration
Wiz provides developers with tools to enhance collaboration and make the development process easy and efficient. The platform allows developers with a visible infrastructure and applications for them to take ownership of security via pre-built integrations and customizable automation flows. As a result, security issues can be efficiently routed to the appropriate teams for remediation. Wiz also integrates with CI/CD pipelines to prevent vulnerabilities from being deployed in the first place.
7. Wiz Sensor – last line of defense
Inside the iGaming RNG Stack
Dissects the tech stack behind digital chance, from PRNG choices to APIs and supply chain, exposing weak links in casino infrastructure.

Wiz has cloud detection capabilities and response solutions in place which take a comprehensive approach to detecting and responding to threats in cloud environments. The Wiz Sensor is a feature of the platform that acts as a final line of defense and identifies and responds to emerging threats in real time. The platform allows security teams to combine the sensor with cloud activity logs and Wiz’s agentless attack path analysis. This enables organizations to gain a complete view of cloud-native attacks for more efficient and effective incident response.
8. Automated attack path analysis (APA)
Wiz is equipped with advanced controls, providing a deeper analysis of an organization's cloud environment to also explore the most refined hidden risks. The automated attack path analysis (APA) feature spots complex chains of vulnerabilities and how attackers could potentially move laterally within an organization’s network to reach valuable assets. The platform also has container scanning capabilities that extend beyond runtime analysis to include scanning of container registries, ensuring that even unused images are checked for vulnerabilities and compliance issues.
9. Integrations into existing workflows
Wiz's advanced workflow features smoothly enable an organization’s cloud security operations by automating processes and integrating them with existing workflows. This includes features like auto-remediation, customizable dashboards, and pre-built integrations with third-party tools. The platform automates tasks and provides flexibility in customization to help optimize an organization’s cloud security posture while reducing manual effort.
What are some of the key security cloud solutions provided by Wiz?
Wiz’s secure cloud environments solution is designed to protect organizations from a wide range of cyber threats in their cloud infrastructure. The team behind the software organization built an operating model that seamlessly integrates with cloud platforms to conduct a comprehensive analysis of security threats and potential vulnerabilities.
But how does Wiz target different threats? They developed unique solutions which are explained here:
1. CSPN (Cloud Security Posture Management)
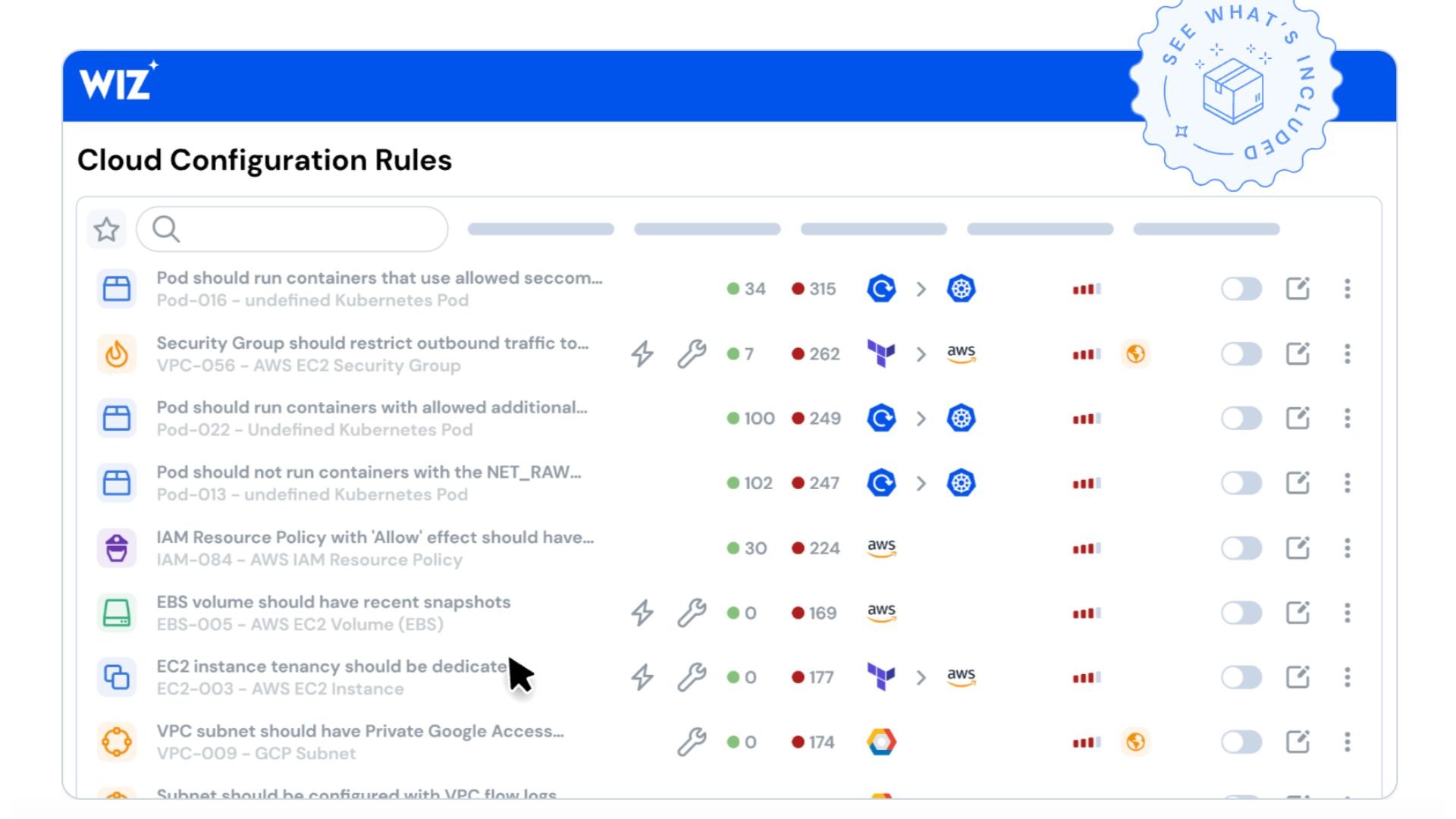
Wiz offers a real-time contextual CSPN security solution that continuously identifies and remediates misconfigurations from development time to runtime across hybrid clouds such as AWS, GCP, Azure, OCI, Alibaba Cloud, and VMware vSphere.
The solution enables inventory management, configuration assessment, vulnerability scanning, compliance reporting, and threat detection. Through these, Wiz helps organizations gain visibility into their cloud infrastructure, identify and address risks, and ensure compliance with industry standards, reducing cyber threats.

Inside AI Agent Attack Surfaces
Prompt injection, tool abuse and poisoned models turn agents into new attack surfaces. Match leading platforms to each threat to build layered AI defense.
In this solution, Wiz conducts 2,300+ cloud misconfiguration rules to identify and address potential vulnerabilities, continuous CIS and compliance monitoring over 150 frameworks, IaC scanning, real-time detections, data-specific CSPM rules, custom OPA-based rules, and auto-remediations.
The Wiz Security Graph can be deployed to contextualize misconfigurations that show the priority misconfigurations. Also, the solution enforces built-in Wiz policies and compliance frameworks across an organization’s cloud environments and IaC code, helping development and security teams build their own custom policies and frameworks.
2. CIEM (Cloud Infrastructure Entitlement Management)
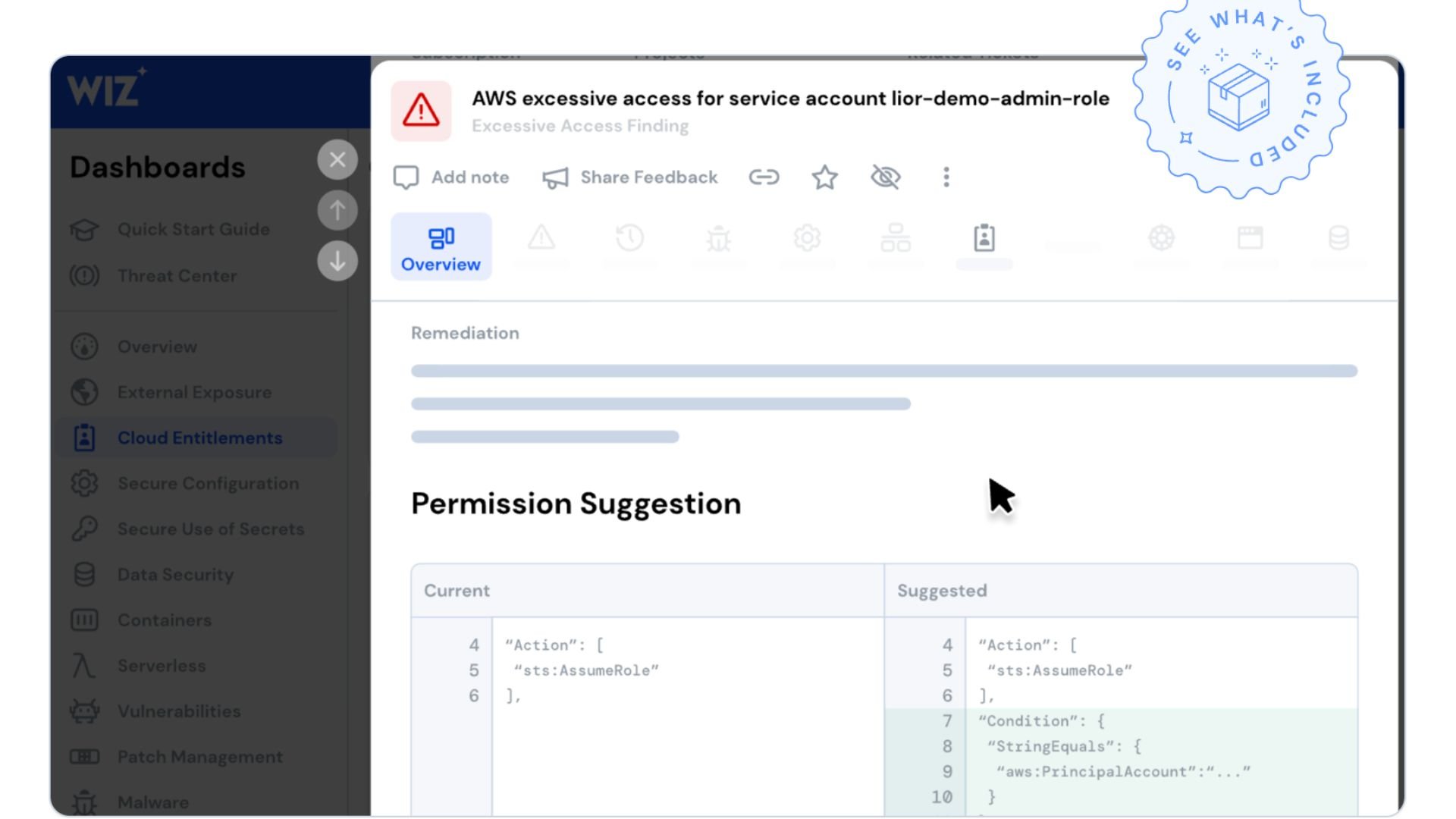
Wiz’s CIEM solution focuses on managing access to cloud resources by analyzing cloud entitlements and auto-generating least privilege policies across an organization’s cloud. It helps the security and development teams visualize, detect, prioritize, and remediate identity (IAM) risks.
The solution identifies identity risks including excessive or admin permissions, high privileges, and identity misconfigurations such as no MFA enabled or inactive users. It also reduces identity attack surface by effectively discovering and removing identity attack paths which often lead to high-value assets. These could include admin identities or crown jewel data with cloud context on the Wiz Security Graph.
Another feature of this solution is to ensure effective governance by hosting access analysis for both human and non-human identities (NHIs) mainly to answer "who can access what in my environment" across IdP, SaaS, and cloud-mapped on the Wiz Security Graph.
3. CWPP (Cloud Workload Protection Platform)
Wiz’s CWPP solution protects workloads running in the cloud, including containers, virtual machines, and serverless functions, from threats like malware, vulnerabilities, and unauthorized access. It secures hosts, VMs, containers & serverless functions by unifying an organization’s workload protection from prevention to real-time detection and response.
Through this in-depth approach, the solution proactively reduces attack surface through full-stack visibility into an organization’s complete cloud environment in minutes. Also, it used agentless scanning tools for vulnerabilities, secrets, malware, and misconfigurations across virtual machines, containers, and serverless functions to minimize workload risk.
Rethinking Trust in CI/CD
Why boards must treat CI/CD as critical infrastructure, with Zero Trust controls replacing perimeter-based security assumptions.

CWPP is the real-time last line of defense through complete monitoring from inside the workload using the Wiz Runtime Sensor. It identifies threats and malicious behavior so the organization’s teams can respond quickly and with context to any potential unfolding threat.
Wiz continues to spotlight one policy approach across cloud and code to ensure workload issues are caught and remediated before they hit production by shifting security left during the software development cycle.
4. AI Security Posture Management (AI-SPM)
With the rapid advancement and rapid adoption of artificial intelligence (AI) technologies, Wiz like many other organizations integrated AI into security solutions. It proposes AI adoption securely with continuous visibility and proactive risk mitigation across organizations’ AI models, training data, and AI services.
Wiz leverages AI to simultaneously assess and improve the security posture of cloud environments. The platform protects machine learning models within cloud environments by discovering AI pipelines, detecting pipeline misconfigurations, and uncovering attack paths to the organization’s AI services, enabling the secure introduction of AI into the environment.
It grants the security and development team full-stack visibility into the AI pipeline. AI services, technologies, and SDKs can be discovered without any agents through Wiz’s AI-BOM. The solution also detects any AI misconfigurations by enforcing secure configuration baselines for the organization’s AI services with built-in rules. These help detect misconfigured AI services.
Also, Wiz’s AI solution eliminates AI attack paths, boosting security in cloud environments further. The model proactively removes attack paths and protects sensitive training data from being compromised.
5. Compliance management
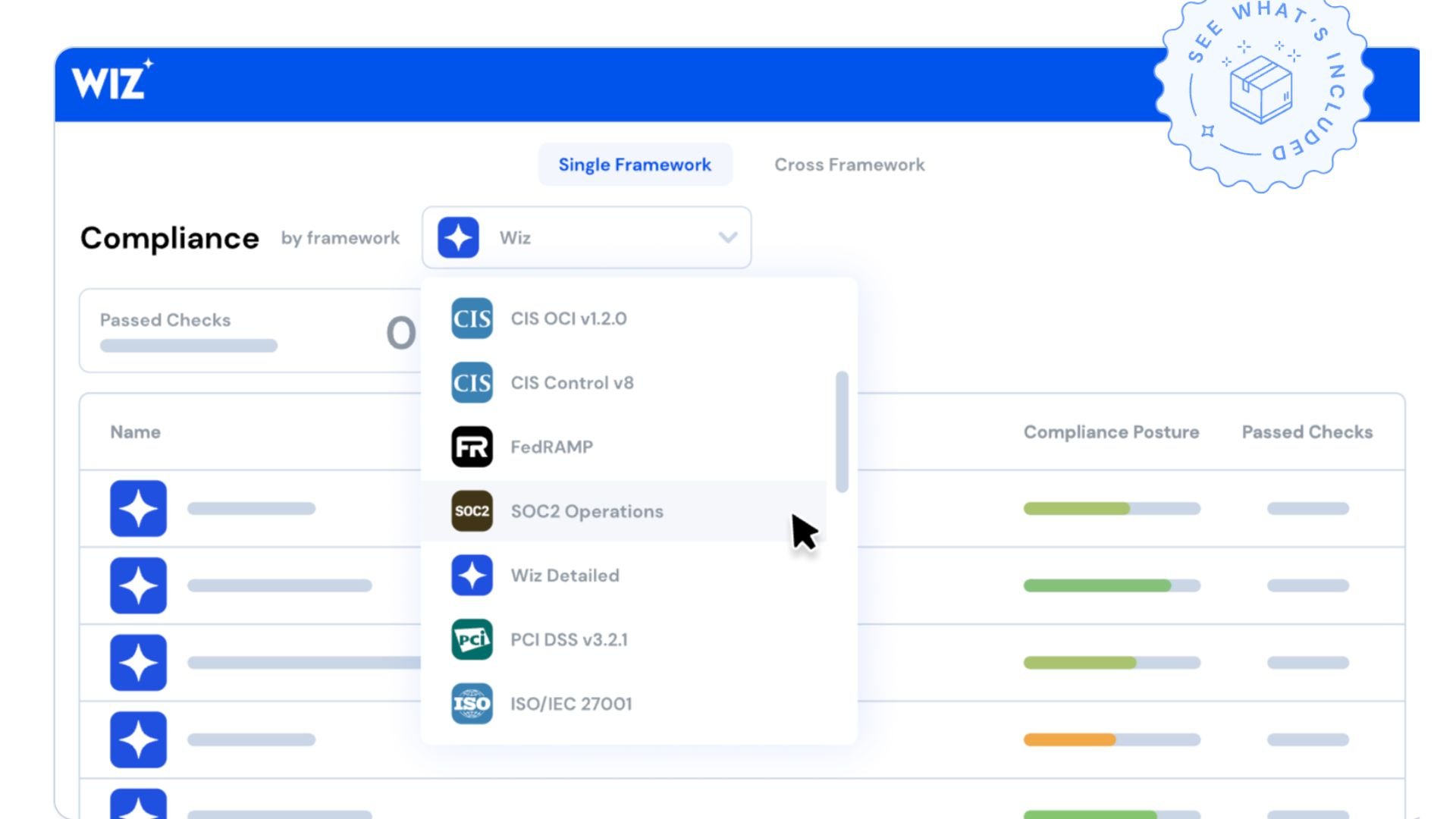
Wiz developed a solution to ensure compliance through the maintenance of automated compliance against industry standard regulations and benchmarks like PCI, GDPR, HIPAA, and more, and custom frameworks.
The solution enables continuous automated compliance assessment to reduce compliance friction and provides posture scores across industry standard compliance frameworks or custom frameworks, allowing organizations to quickly assess their compliance.
Wiz’s compliance framework features over 100 built-in frameworks such as NIST, HIPAA, CIS, HiTrust, and SOC2. It allows users to create custom frameworks from scratch or duplicate a built-in framework to align with compliance posture as per the organization’s unique needs. Organizations can also use compliance posture per framework for different business units or applications for granular and flexible reporting.
6. Software Supply Chain Security
Wiz made it easy to secure all segments of an organization’s software supply chain with complete visibility into software bill of materials and risk assessment across container and machine images, IaC templates, and code repositories.
The solution enables agentless visibility through Wiz’s SBOM (Software Bill of Materials) capabilities which details all inventories, allowing users to gain instant and agentless visibility into every software component in their environment. It provides visibility into packages, open-source libraries, and their versions.
To detect supply chain security risks, cloud environments can be analyzed and identify vulnerabilities, misconfigurations, and exposed secrets in first-party, OSS, or 3rd party components. Security can be enhanced from build to runtime – Wiz’s single security policy across the software lifecycle from scanning IDE, code repositories, CI/CD pipelines, and in runtime.
7. DSPM (Data Security Posture Management)
Wiz protects critical data through its DSPM solution which continually discovers and classifies sensitive data, detects data risks and attack paths with context, and attack paths with context, and automates compliance assessment against data regulatory frameworks.
Since traditional tools often miss the cloud context required to identify attacks leading to critical data, Wiz has introduced DSPM as part of a comprehensive CNAPP (Cloud Native Application Protection Platform) which quickly detects and fixes such vulnerabilities.
The solution allows users to discover and classify sensitive data in their cloud system through built-in classification rules including PII, PHI, PCI, and secrets, or define custom classifiers, without agents. Data scanning can also be extended to code and CI/CD pipelines.
It mitigates data risks by identifying potential attack paths to critical data using context derived from the Wiz Security Graph. This enables organizations to quickly pinpoint the location of sensitive data and take appropriate measures to protect it.
Also, the DSPM solution ensures regulatory compliance is met through constant evaluation against data security frameworks like PCI DSS, GDPR, HITRUST, and others in addition to detecting geographical locations of sensitive data, ensuring data sovereignty.
8. IaC (Infrastructure-as-Code) Scanning
WIz can be integrated with an organization’s development workflows to securely handle their infrastructure as code, particularly built for Dev and DevOps teams. The solution helps identify secrets, vulnerabilities, and misconfigurations in the organization’s IaC, containers, and VM images.
The unified cloud security platform helps security and development teams gain immediate security insights for developers and policy enforcement for security teams. “One platform, zero silos,” WIz says.
Applications can be shipped faster helping developers repair vulnerabilities, misconfigurations, and exposed secrets before deployment. The cloud environment can be analyzed detecting risks based on priority by enforcing policy in the pipeline.
A single policy is applied across the software lifecycle and Wiz provides 100s of policies and frameworks that are already built-in. The solution allows some flexibility by enabling, organizations to custom-create policies as per their requirements.
9. Container and KSPM (Kubernetes Security Posture Management)
Wiz makes it possible for organizations to have complete visibility across containers, Kubernetes, and cloud environments within minutes without agents. It leverages the functions of Wiz Security Graph to analyze and prioritize risk with full context.
Also, the solution identifies real-time malicious behavior in Kubernetes clusters for rapid response, allowing opportunities for developers and security to collaborate across the SDLC and resolve issues across the lifecycle of the containerized application.
Use cases
1. Healthcare
Wiz helped Artisan, a cloud-based technology company in the healthcare industry optimize their AWS platform by providing a comprehensive cloud security solution that helped them identify and address vulnerabilities, improve compliance, and streamline their security processes.
Artisan particularly sought a cloud security solution to protect sensitive patient data without hiring a dedicated security team. In this case, CSPM helped them gain visibility into their cloud environment – AWS, identify and prioritize risks, and automate compliance management.
Since healthcare data necessitates strict protection, Artisan’s goal was to ensure compliance with regulations like SOC and HIPAA. The organization wanted to streamline its security processes and focus on improving patient care, allowing Artisan to maintain a strong security posture while meeting targets to provide quality patient care.
2. Government
Wiz helped a U.S. Navy Cloud Broker to improve the performance of a combination of cloud security platforms including AWS through its CSPM solution which helped them with better visibility, identification, and addressed vulnerabilities, also, automated compliance management.
The Navy faced challenges in managing and securing multiple cloud security platforms, necessitating enhancements in their cloud security posture to protect sensitive data, comply with regulatory requirements, and accelerate the execution of new capabilities.
The U.S. Navy partnered with Wiz and Strategic Business Systems (SBS) to develop COSMOS, a platform designed to streamline cloud onboarding, security, and compliance processes. Wiz centralized visibility by providing a comprehensive view of the Navy's cloud environment. It also automated security and compliance, identified and mitigated security risks as well as continuously monitored to rapidly detect and address vulnerabilities.
3. Manufacturing
Wiz's CSPM solution was used by Siemens, a global industrial manufacturing company to help them gain visibility into their cloud environment using a combination of cloud platforms, identify and address vulnerabilities, and automate compliance management. The cloud platforms particularly included AWS (Amazon Web Services) and Azure (Microsoft Azure).
Wiz addressed the increasing footprint of cloud environments which was becoming more complex, requiring Seimens to obtain better visibility, consolidate security tools, and build a more unified cloud security strategy.
The solution helped Seimen also prioritize remediation and improve the system’s efficiency through the consolidation of tools in a single platform. The cloud visibility was improved by 400%, over 500 employees within Siemens actively use Wiz (80% of them are non-security teams) and it also optimized their cloud resources and reduced unnecessary cost expenditure.
Wiz’s solutions are deployed by 40% of Fortune 100 organizations, showing their rapid advancement in tackling cloud security through a secure, simple, and efficient unified solution.
About Wiz
Meet the organization that rejected Google’s $23 billion takeover deal – Wiz, a leading cybersecurity organization offering a comprehensive cloud security solution designed to secure organizations from a myriad of cyber threats. It came up with a comprehensive solution that presents a unified view of complete cloud environments.
It’s becoming one of the fastest-growing software companies. Its impressive growth trajectory and innovative approach to cloud security have solidified its position.
Wiz's comprehensive solution addresses multiple cloud security risks, while at the same time, eliminating the need for organizations to deploy separate software solutions, simplifying management and boosting overall security.







Comments ( 0 )