Safeguarding sensitive information and systems from cyber threats has become an urgent priority for organisations worldwide.
Threat intelligence is critical to cybersecurity strategies, offering key insights into potential risks and empowering proactive defence measures.
In this article, we’re deep-diving into the meaning of threat intelligence, exploring its components, benefits and challenges.

What is Threat Intelligence? Definition
Threat intelligence is the valuable knowledge derived from analysing data related to potential or existing cyber threats. This includes a broad spectrum of information, including indicators of compromise (IOCs), threat actor tactics, techniques, procedures (TTPs), vulnerabilities, and emerging trends in the cyber threat landscape.
The primary objective of threat intelligence is to equip organisations with actionable insights that enable them to identify, understand, and effectively mitigate potential threats.
Threat intelligence enhances proactive cybersecurity by providing organisations with timely and relevant information about potential risks and vulnerabilities. By monitoring and analysing various data sources such as network traffic, logs, and security events, threat intelligence enables organisations to stay ahead of cyber threats and prevent security incidents before they occur.
Threat intelligence is not limited to technical indicators and data alone. It also includes contextual information such as threat actors' motivations and intentions, targeting preferences, and the geopolitical landscape influencing cyber activities.
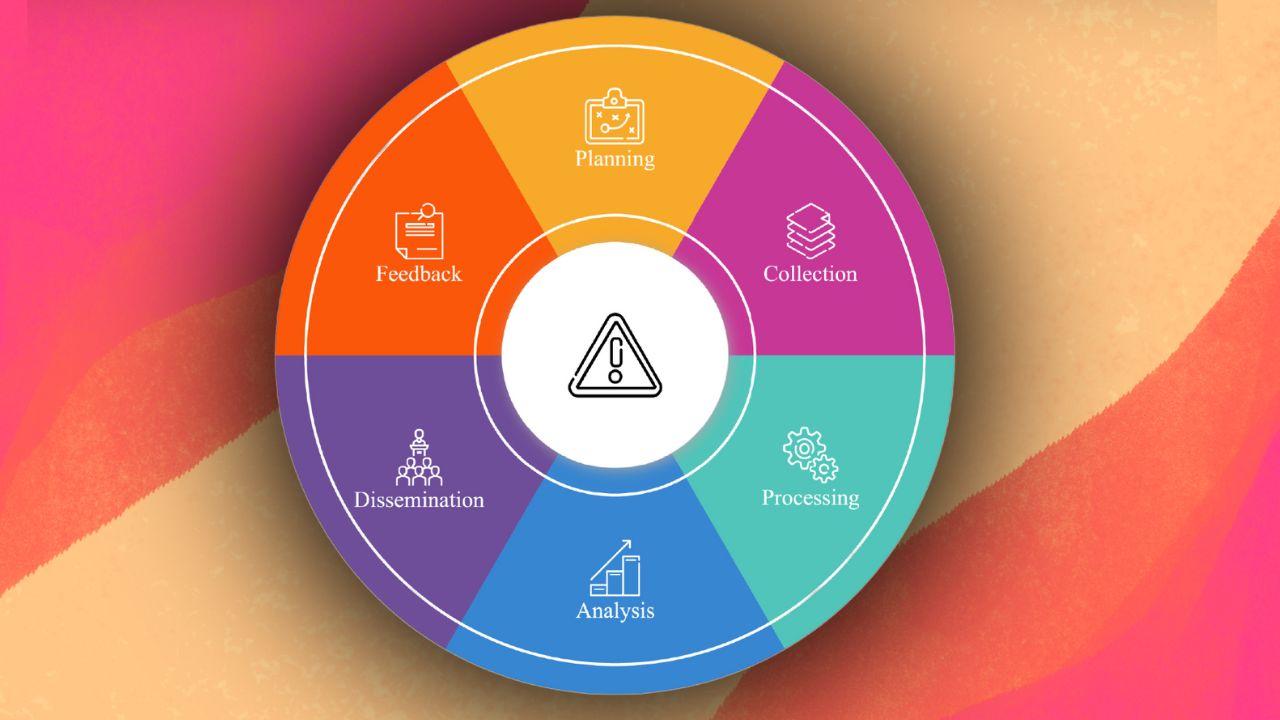
Components of Threat Intelligence
The process of threat intelligence begins with collecting relevant data from various sources. These sources range from internal data sources such as network logs and security alerts to external feeds, open-source intelligence (OSINT), and information-sharing platforms.
Once data is collected, the raw data undergoes thorough processing and analysis to extract meaningful insights. This involves sorting, correlating, and enriching data to identify patterns, trends, and anomalies indicative of potential threats.
Advanced analytical techniques, such as machine learning and natural language processing, are often employed to enhance the analysis process and uncover actionable intelligence hidden within the data.
Contextualisation plays a critical role in understanding the significance and relevance of the identified threats. Analysts can prioritise threats based on their potential impact and likelihood of occurrence by considering factors such as the organisation's industry sector, geographical location, and the tactics typically employed by threat actors targeting similar entities.
Moreover, threat intelligence analysis often involves attribution, which entails identifying the individuals, groups, or nation-states behind the observed cyber threats. While attribution can be challenging due to threat actors' anonymity and deception techniques, it provides valuable insights into their capabilities, motivations, and potential future activities.
Once the analysis is complete, the findings are disseminated to relevant organisational stakeholders through actionable reports, threat briefings, and intelligence alerts. These reports highlight the identified threats and provide recommendations and mitigation strategies to help organisations effectively reinforce their defences and mitigate potential risks.
This actionable intelligence comes in various forms, including IOCs such as IP addresses and malware hashes, TTPs employed by threat actors, or strategic insights into emerging threats and vulnerabilities.
The threat intelligence process includes feedback loops and continuous improvement mechanisms to refine and enhance the effectiveness of intelligence gathering and analysis.

Inside 2025 Blockchain Defences
Boards are shifting focus from protocol safety to tools that secure keys, wallets, contracts and users across decentralised operations.
By incorporating feedback from security incidents, threat-hunting exercises, and external intelligence sources, organisations can cyclically improve their capabilities and stay ahead of evolving cyber threats.
Benefits of Threat Intelligence in Today’s World
Threat intelligence offers several key benefits:
- Proactive Defence: By providing insights into potential threats, organisations can identify and stop attacks before they happen. This is achieved by understanding indicators of compromise (IOCs) and attackers' tactics, techniques, and procedures (TTPs).
- Faster Incident Response: When a security incident occurs, threat intelligence helps organisations respond quickly and efficiently. It provides essential details about the attack, including its nature, scope, and potential source, allowing for rapid damage mitigation.
- Informed Risk Management: Threat intelligence gives organisations a clear understanding of the ever-changing threat landscape. This knowledge empowers decision-makers to allocate resources effectively, prioritise security investments, and implement appropriate controls to protect critical assets.
- Compliance Support: Many industries face strict cybersecurity regulations. Threat intelligence helps meet these requirements by demonstrating proactive measures to safeguard sensitive data.
- Enhanced Security Operations: Threat intelligence empowers security teams to actively hunt for network threats. By analysing various data sources, teams can prioritise alerts and incidents based on their potential impact, leading to more efficient and effective security operations.
Inside Public DNS Performance
Breaks down how leading DNS networks route queries, cut latency and offload fragile ISP infrastructure at global scale.

Challenges of Implementing Threat Intelligence
Implementing threat intelligence comes with its own set of challenges:
- Information Overload: The absolute amount of data from multiple sources can be overwhelming, making it difficult to find actionable insights. Thus, advanced tools and techniques are needed to extract relevant information and prioritise threats effectively.
- Data Quality Concerns: Ensuring accurate and reliable data is key. Inconsistent sources, false positives, and misleading information can hamper the effectiveness of security measures and lead to wrong decisions. Careful verification and validation of data and sources are essential.
- Standardisation Issues: The need for standardised formats and terminology makes it difficult for organisations to share and collaborate. Incompatible data formats and vocabularies obstruct information exchange and joint efforts to combat cyber threats.
- Resource Limitations: Implementing an effective program requires significant resources, including skilled personnel, advanced technology, and ongoing training. Smaller organisations may need help allocating the necessary resources, limiting their effectiveness in threat intelligence operations.
- Evolving Threats: Cyber threats constantly evolve, pushing the boundaries of what threat intelligence can handle. Advanced techniques attackers use to evade detection require continuous adaptation and innovation to stay ahead of emerging threats.

Why Cyber Attacks Are So Costly
Explores how modern attacks convert data loss and downtime into escalating fines, customer churn, and strategic security spend.
Final Thoughts
In conclusion, threat intelligence is the cornerstone of proactive cybersecurity, empowering organisations to effectively anticipate and mitigate cyber threats. Organisations can fortify their security posture and preemptively thwart potential cyber-attacks by meticulously orchestrating data collection, analysis, and dissemination processes.
Mastering threat intelligence demands organisations' steadfast commitment to cultivating robust processes, harnessing cutting-edge technologies, and forging strategic partnerships.
Through such concerted efforts, organisations can unlock the full potential of threat intelligence, safeguarding digital assets and infrastructure against the ever-evolving landscape of cyber threats.







Comments ( 0 )