Ransomware impacts organizations of all sectors and sizes. Ransomware attacks have risen by 13% in the last five years, with an average cost of an incident costing a whopping $2.73 million – an increase of $1 million from 2023.
They’re also becoming increasingly sophisticated by the day. The rise of double-extortion and triple extortion, attacks, where attackers not only encrypt data but also steal and threaten to publish it, has made it more difficult to recover data when hackers strike.
Beyond the threat of publishing stolen data, attackers may now target a company’s customers or partners, or disrupt operations through DDoS attacks, adding more pressure to pay the ransom.

And this has all become easier than ever for threat actors thanks to Ransomware as a Service (RaaS), which allows cybercriminals around the world to launch sophisticated attacks with no technical know-how required.
This article tells you everything you need to know about Ransomware as a Service (RaaS), including what it is, how it works, and why it’s dangerous.
What is Ransomware as a Service (RaaS)?
Ransomware as a Service (RaaS) is a business model where ransomware developers create and offer their malicious software to cybercriminals, who then use it to conduct attacks.
RaaS allows individuals without technical expertise to launch sophisticated ransomware attacks by providing them with the necessary tools and support. This model operates similarly to legitimate Software-as-a-Service platforms, making ransomware widely accessible and significantly expanding the pool of potential attackers.
RaaS platforms often function through underground forums or dark web marketplaces, where developers offer their ransomware kits for a share of the profits or for a subscription fee.

These kits typically include the ransomware itself, user-friendly dashboards to manage infections, and even customer support to help affiliates deploy and customize their attacks. The developers benefit from this arrangement as it broadens their reach without directly participating in each attack, while affiliates gain access to powerful tools and infrastructure without needing to code or understand the technical details.
The rise of RaaS has contributed to the surge in ransomware attacks worldwide, as it lowers the entry barrier for cybercrime. It also enables rapid evolution and adaptation of ransomware strains, as developers continually update their software to bypass new security measures.
This proliferation of easily accessible ransomware tools has made it challenging for organizations to defend against attacks, as they face an increasing number of threat actors equipped with advanced, professionally developed malware.
How does the RaaS model work?
Ransomware-as-a-Service (RaaS) model works much like a legitimate business, where ransomware developers create and maintain malicious software and then lease it to affiliates who carry out the attacks.
The structure usually involves two primary entities:
- The developers: who build and update the ransomware.
- The affiliates: who use it to infect targets.
In return, the affiliates pay the developers a fee, often a percentage of the ransom payments they collect, or a flat subscription fee. The RaaS process typically begins with developers advertising their ransomware on underground forums or dark web marketplaces. They provide potential affiliates with a user-friendly dashboard, detailed instructions, and often a range of customization options.
Affiliates, who may not have technical expertise, can then use these tools to launch ransomware campaigns by distributing the malware through phishing emails, malicious websites, or exploiting network vulnerabilities. Some RaaS providers even offer additional services like stolen data hosting or automated payment portals to handle ransom transactions, streamlining the entire attack process.
This division of labour and profits makes the RaaS model attractive to both skilled developers, – who can focus on improving the malware – and cybercriminals – who can execute attacks with minimal technical knowledge. As a result, the RaaS model has democratized ransomware attacks, contributing to the global increase in cyber extortion incidents.
What happens in a RaaS attack?

When Cyber Risk Hits the P&L
Unpacks the ten priciest breaches to show how cyber incidents cascade into long-term financial, legal, and reputational liabilities.
RaaS attacks typically begin like any other ransomware attack, with the affiliate choosing a target and deploying the ransomware. Once the ransomware is deployed and a target is infected, the victim is then presented with a ransom note, which appears on their screen, instructing them on how to make the payment, typically in cryptocurrency like Bitcoin, to receive the decryption key
The ransom note may also include a timer, threatening to permanently delete the encrypted data or increase the ransom amount if payment is not made within a certain timeframe. In cases of double extortion, the note will also threaten to release the stolen data publicly, causing further damage to the victim’s reputation or operations.
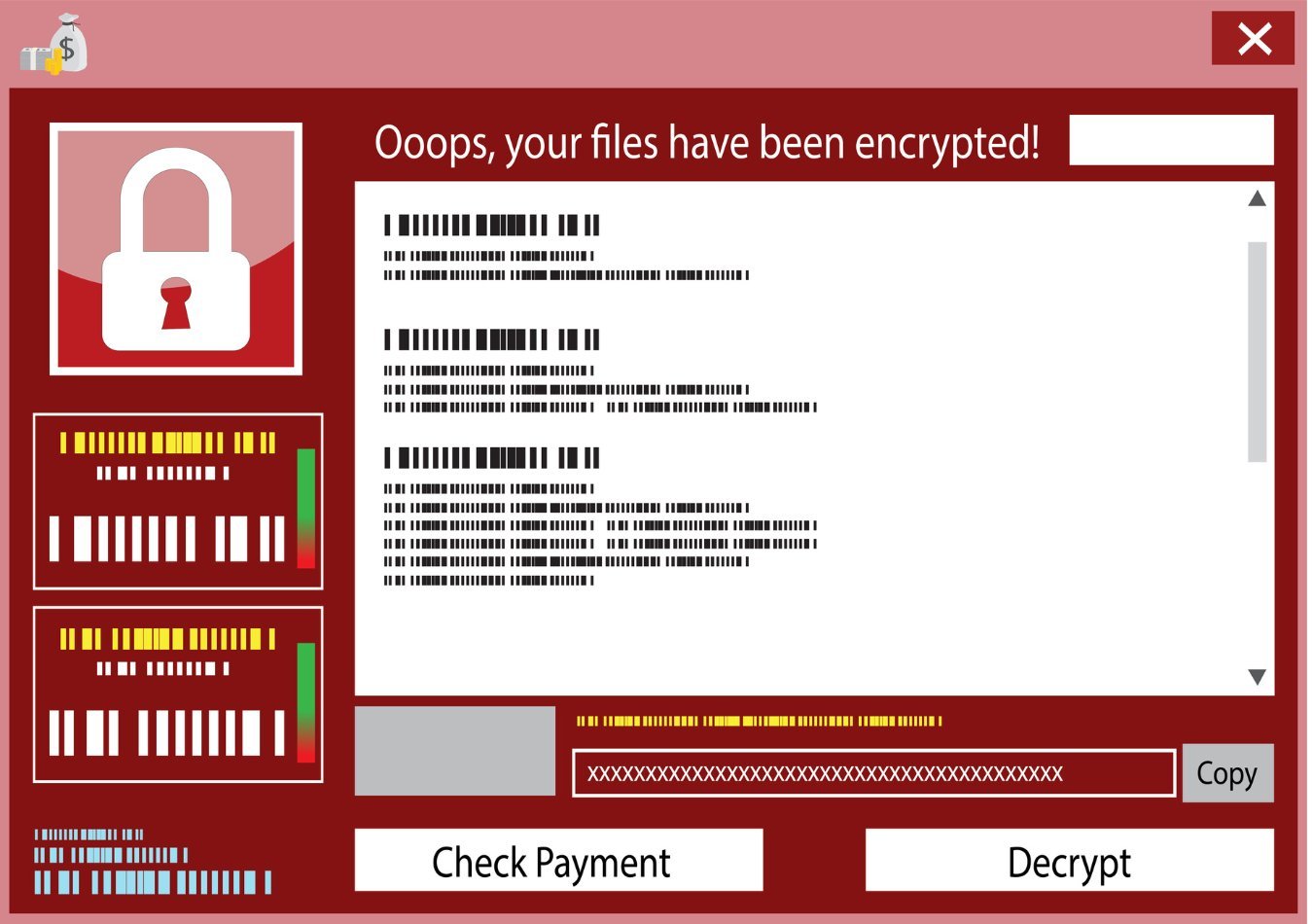
If the ransom is paid, the affiliate and the RaaS developer split the proceeds according to their agreement. If the ransom is not paid, the victim may lose access to their data permanently or face additional extortion demands.
But even if the ransom is paid, there’s no guarantee that the victim will receive the decryption key, or that the data will be restored without corruption.
In many cases, attackers may demand further payments or leave behind malware that can be used for future attacks after a demand is paid. This makes RaaS attacks particularly devastating, as they can disrupt operations, lead to financial losses, and damage reputations long after the initial incident.
Examples of RaaS
Several well-known Ransomware-as-a-Service RaaS groups have been responsible for some of the most disruptive and costly cyberattacks in recent years. These groups provide their ransomware tools to affiliates, who then carry out the attacks. Some notable examples include:
1. REvil (Sodinokibi
REvil, also known as Sodinokibi, emerged in 2019 as a RaaS group and quickly gained notoriety for its high-profile attacks. REvil’s attack strategy often includes double extortion, where they not only encrypt victims' data but also steal sensitive information, threatening to publish it on their dark web leak site, "Happy Blog," if the ransom isn’t paid.
Lazarus Tactics And Toolchain
Dissects Lazarus malware architecture, DDoS methods, SWIFT abuse and TLS masquerading to expose where enterprise controls are weakest.

Notable attacks attributed to REvil include the 2021 attack on JBS Foods, the world’s largest meat processor, which led to a temporary shutdown of its operations in North America and Australia, and a ransom payment of $11 million. It has also attacked Kaseya, an IT management software provider, which affected hundreds of companies globally. In late 2021, after international pressure and a series of arrests, REvil’s operations were disrupted, though there have been signs of some of its members resurfacing under new identities or in different groups.
2. DarkSide
DarkSide first appeared in August 2020, offering a RaaS platform with a focus on targeting large organizations. Their most infamous attack was on Colonial Pipeline in May 2021, which resulted in a temporary shutdown of the largest fuel pipeline in the United States and a ransom payment of $4.4 million (partially recovered by the FBI). This attack highlighted the vulnerability of critical infrastructure to ransomware and led to increased scrutiny and response from law enforcement agencies.
DarkSide’s business model included offering affiliates a highly customizable ransomware toolkit, along with detailed manuals and customer support. They positioned themselves as “ethical” cybercriminals, claiming they would not attack hospitals, non-profits, or educational institutions. However, their affiliates did not always adhere to these claims. Following the Colonial Pipeline attack, DarkSide announced its closure, citing pressure from law enforcement and disruption of its infrastructure. Despite this, variants of their ransomware have continued to surface under different names, indicating the group’s influence on subsequent RaaS operations.
3. Conti
Conti, active since 2020, is known for its aggressive and persistent attacks, primarily targeting large organizations and critical sectors like healthcare. Conti's ransomware is notable for its speed and efficiency, leveraging advanced encryption techniques to lock down systems rapidly. They are also known for their meticulous targeting, conducting extensive reconnaissance on their victims to maximize the impact of their attacks.
One of Conti’s most significant attacks was on the Irish Health Service Executive (HSE) in May 2021, which crippled the country’s healthcare system, disrupting patient care and access to medical records. Conti demanded a $20 million ransom, which was not paid, but the group later released the decryption key after negotiations. Conti has been linked to the Russian cybercrime ecosystem, and their tactics have evolved over time, with new versions of their ransomware appearing frequently.
4. LockBit

How Hacker Gangs Weaponize IT
Breaks down malware families, botnets, and DDoS tactics used by hacker crews to turn everyday infrastructure into a global attack surface.
LockBit is one of the most prolific RaaS groups today, developing one of the fastest encryption processes, making it difficult for victims to respond before their data is completely encrypted. They provide affiliates with a range of different attack tools, including automated scanners to identify and exploit vulnerabilities in potential targets.
LockBit has targeted a wide range of sectors, from manufacturing and construction to professional services and healthcare. Their attacks are notable for their precision and the rapid deployment of ransomware once a target is identified. In 2021, LockBit introduced a new variant, LockBit 2.0, which included enhancements to their encryption algorithm and increased anti-analysis features to evade detection. They also implemented a double extortion model, threatening to publish stolen data on their leak site if the ransom is not paid.
5. Maze
Maze was one of the first RaaS groups to introduce the double extortion tactic, where they not only encrypted data but also exfiltrated it and threatened to release it publicly. Maze first appeared in 2019 and quickly gained a reputation for targeting high-profile organizations, including Canon, Cognizant, and the City of Pensacola. They were known for publishing data of non-compliant victims on their website as a form of additional pressure.
Maze’s operations were sophisticated and well-coordinated, often involving extensive reconnaissance and exploiting unpatched vulnerabilities. Their success in extorting large ransoms and the visibility of their operations influenced many other ransomware groups to adopt similar tactics. In November 2020, Maze announced its retirement, stating that it would no longer engage in ransomware attacks. However, many of its members and affiliates likely transitioned to other RaaS groups like Egregor and SunCrypt, carrying forward Maze’s legacy of aggressive and highly publicized attacks.
Preventing RaaS attacks
Because RaaS attacks exploit human error, unpatched vulnerabilities, and weak security practices, organizations must adopt a multi-layered security approach to minimize the risk and impact of ransomware.
The foundation of ransomware prevention lies in maintaining a strong security posture. This includes deploying advanced endpoint protection, firewalls, and intrusion detection systems to monitor and block suspicious activities.

It also includes:
Rewriting Healthcare Cyber Risk
Boards are reframing patient data, clinical workflows and IoT estates as critical assets that demand coordinated, enterprise-grade protection.

- Regularly updating and patching software and systems is essential, as many RaaS attacks exploit known vulnerabilities in outdated software.
- Implementing multi-factor authentication (MFA) across all critical systems can further prevent unauthorized access, even if credentials are compromised.
- Ensuring that all critical data is backed up frequently and stored securely, ideally off-site or in a cloud environment. This allows organizations to recover their data from ransomware attacks without succumbing to ransom demands.
- Regularly testing backups to ensure they can be restored quickly and effectively.
- Conducting regular cybersecurity training sessions for employees to recognize phishing attempts and social engineering tactics.






Comments ( 0 )