The state-sponsored hacking group ‘Dark Pink’ has become a global threat after expanding its targets to government organisations across Asia and Europe.
That’s according to researchers from the cybersecurity firm Group-IB, who has discovered five new victims of the Asia-linked hacking group including government agencies in Brunei and Indonesia, a military body in Thailand, and an educational institution in Belgium.
Dark Pink has been active since mid-2021, previously targeting organisations in the Asia-Pacific region, but was only exposed in January 2023 following an investigation from Group IB.
Despite this exposure, Dark Pink has continued to expand its operations, targeting a range of organisations in 11 different countries in a bid to steal corporate data and high-value government secrets.
Researchers found it was responsible for at least seven successful attacks between June and December 2022, with victims including “high-profile targets” in Cambodia, Indonesia, Malaysia, Philippines, Vietnam and Bosnia and Herzegovina.
“The risk of highly damaging confidential data leaks remains alarmingly high,” said Group-IB malware analyst Andrey Polovinkin
“There is mounting evidence suggesting that Dark Pink is not a one-time campaign carried out by a known APT group, but rather a distinct and continuously evolving threat,” added Mr Polovinkin referring to advanced persistent threats or stealthy cyberattacks often sponsored by a government.
Group-IB has not attributed the campaign to any specific country, but in January the Chinese security firm Anheng Hunting Labs linked the group – which it calls the “Saaiwc Group” – to an unnamed southeast Asian country.
A March analysis by EclecticIQ also found metadata that pointed to China, but said there was a lack of conclusive proof and characterized it as a “low confidence” attribution.”

A modified kill chain
Along with expanding its operations, Dark Pink’s operators have also updated their tools and data exfiltration techniques as recently as this month – a sign experts say “that the group shows no signs of slowing down.”
In their most recent attacks, the group demonstrated a revamped attack chain, implementing different persistence mechanisms, and developing new data exfiltration tools to dodge detection.
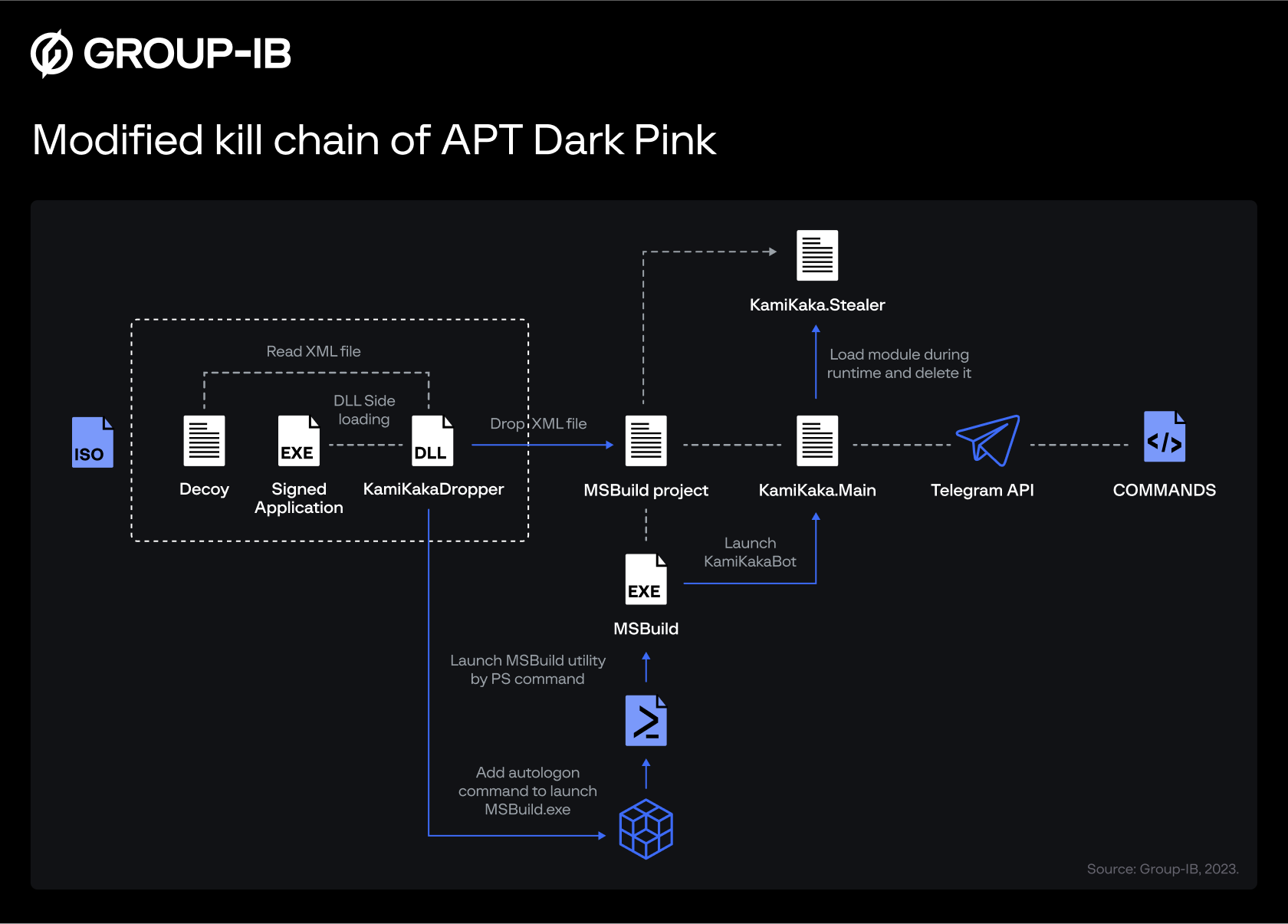
Attacks continue to depend on ISO archives sent via spear-phishing for initial infection. This employs DLL side-loading to launch its signature backdoors – 'TelePowerBot' and 'KamiKakaBot.'
A new element to this, however, is that the attackers have now split KamiKakaBot's functionalities into two parts, namely device control and data theft.
The implant is also now loaded from memory, never touching the disk, allowing the threat actors to evade detection as antivirus tools do not monitor processes that initiate in memory.
KamiKakaBot continues to target data stored in web browsers and sends it to the attackers via Telegram. This backdoor can download and execute arbitrary scripts on the target device.
Data exfiltration
Researchers discovered that Dark Pink uses a private GitHub repository to host additional modules downloaded by its malware to compromised devices.
The attacks performed only 12 commits on that repository throughout 2023, mainly to add or update malware droppers, PowerShell scripts, the ZMsg info-stealer, and the Netlua privilege escalation tool.
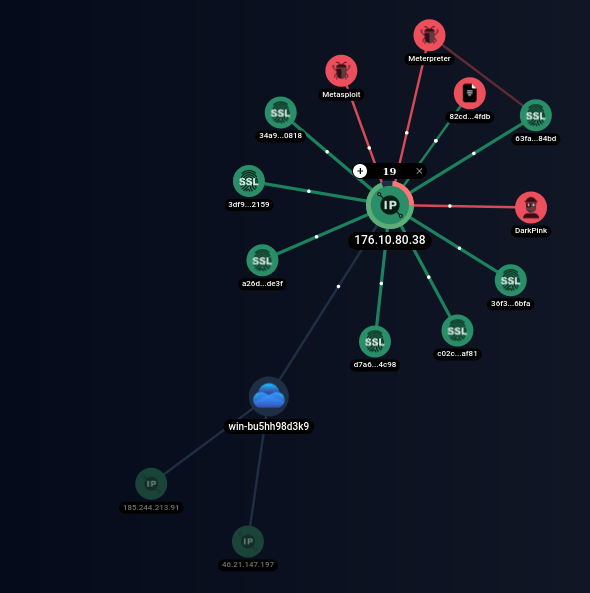
In some cases seen by the analysts, the attackers used DropBox uploads, while in others, they used HTTP exfiltration using a temporary endpoint created with the ‘Webhook site’ service or Windows servers.
The motive behind these choices remains unclear given that in the past Dark Pink has usually favoured public free-to-use services.
The scripts also feature the ability to exfiltrate data by creating new WebClient objects to upload files to an external address using the PUT method after defining the location of the target files on the breached computer.

Today’s business leaders must respond to more risks than ever before yet at the same time innovation is seen as an imperative and there can be no innovation without risk. The last few years have seen seismic shifts in remote work technology, privacy, security, ESG and consumer attitudes to diversity, inclusion, and trust.
Taking place on the 6th and 7th of June 2023, #RISK DIGITAL EU Focus will examine the changing risk landscape in a content-rich, knowledge-sharing environment. Attendees will be able to learn and better understand how to mitigate risks, reduce compliance breaches, and improve business performance.
Risk management can no longer be just compliance-driven and reactive and every organisation faces market, economic, technological, social, crime and security risks.
Stay ahead of the curve, REGISTER NOW.






Comments ( 0 )