Europe’s financial sector has reached a pivot point. The EU Digital Operational Resilience Act set a clear intent in 2025: strengthen operational resilience across banks, insurers and market infrastructure, including the technology supply chain that supports them. That intent now meets verification.
Supervisory authorities are moving from guidance to evidence, from plans on paper to proof of performance. For leaders, DORA enforcement is no longer a compliance milestone. It is a measure of trust, risk discipline and readiness that competitors and customers will notice.

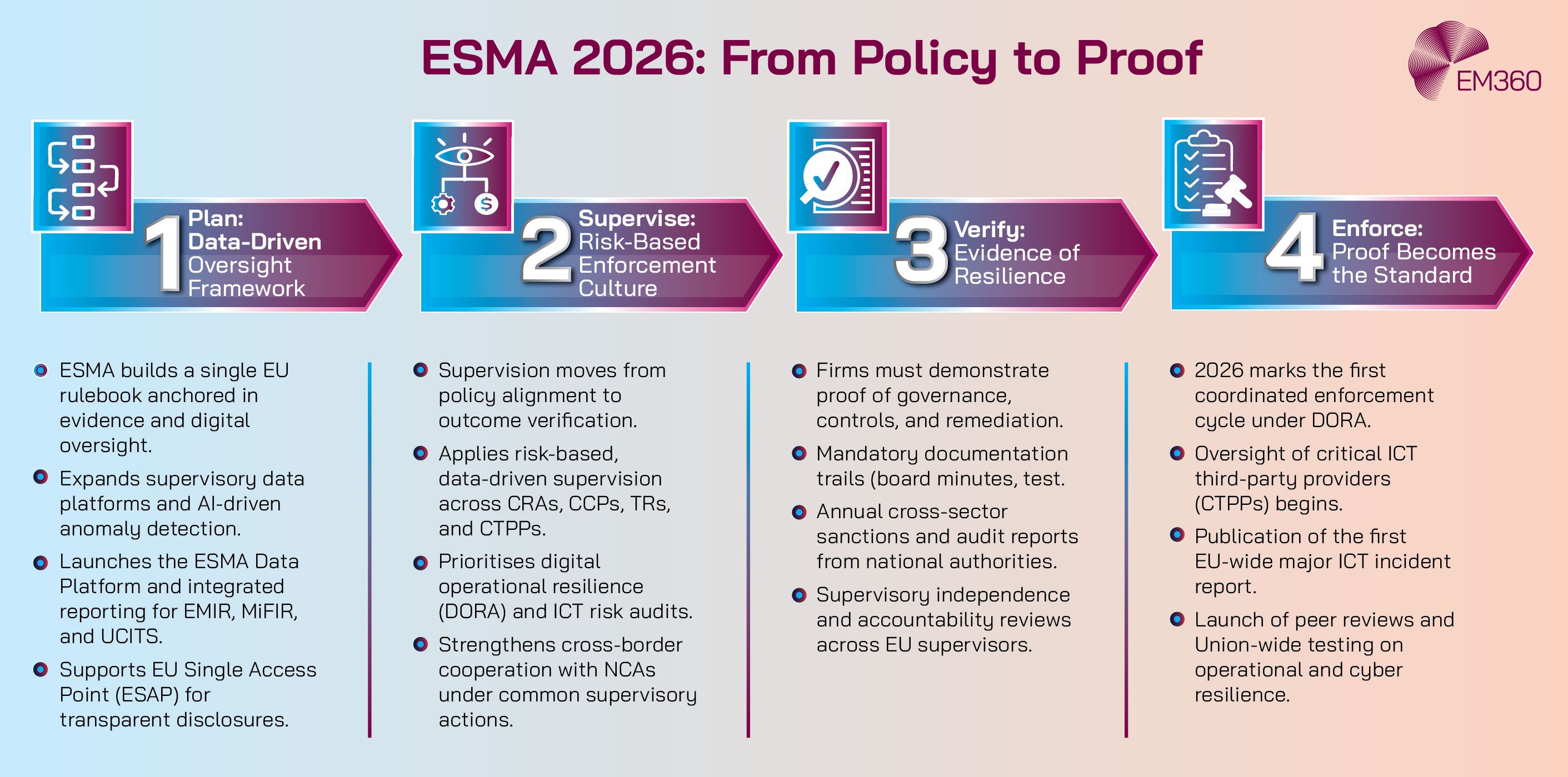
From Regulation to Enforcement — What’s Changing in 2026
2025 was about implementation. 2026 is about validation. Supervisors across ESMA, the EBA and EIOPA have signalled a sharper posture that puts audits, inspections and corrective actions on the table. The April 2025 outsourcing registers have given regulators a detailed view of who runs what, and where concentration risk lives.
The designation process for critical ICT third-party providers is advancing, which brings direct EU-level oversight for the technology firms that underpin core financial services. The result is a tangible shift. Firms should expect more requests for evidence, more questions about governance and more scrutiny of whether resilience actually works when systems fail.
The road to oversight and designation
The oversight pipeline is now defined. Firms submitted ICT outsourcing data, supervisors performed analysis, and preliminary classifications for critical ICT providers are under way. Engagement with designated providers follows, supported by an oversight guide that sets expectations for audits, thematic reviews and remediation.
The intent is simple: reduce systemic risk from concentrated technology vendors and ensure continuity for essential services if a major cloud, core banking platform or market utility suffers disruption.
The rise of accountability and evidence culture
DORA has raised the bar on proof. Regulators want to see the audit trail that sits behind your claims.
That includes board minutes showing how directors have challenged ICT risk, documented risk decisions, incident logs that meet EU templates, test plans with outcomes and tracked remediation, and updated contracts that cover subcontractors, audit rights and exit plans.
ESMA’s 2026 work plans point toward a simple expectation: show your work, and show that it holds up under pressure.

When Obsolescence Is a Strategy
How intentional product lifespans reshape revenue models, regulation pressure, and long-term technology planning for hardware ecosystems.
The Financial Services Impact — Who Feels It Most
The impact lands differently across the sector, but the direction is consistent. Risk, governance and technology priorities are being reset.
Budgets are shifting to evidence-driven resilience, resourcing is moving toward continuous testing and vendor oversight, and boards are asking sharper questions about dependency, concentration and recovery time for critical services.
Banks and insurers under the microscope
European surveys through 2025 tell a clear story. Many institutions still lag on third-party controls, incident preparedness and cross-functional testing. The pressure points are familiar. Board accountability is explicit under DORA, yet directors need regular, decision-ready reporting to discharge those duties.
Vendor dependency runs deep in payments, trading, customer channels and core processing, which makes subcontractor visibility and exit strategies more than a legal clause. Resilience testing is improving, but too many programmes measure plan completion rather than recovery outcomes.
Technology vendors and critical providers
The technology side of the ecosystem will now feel the regulator’s presence directly. Critical ICT providers face EU-level oversight, with lead overseers, annual oversight plans and the potential for on-site inspections. This shifts accountability upstream and makes service continuity a shared obligation between the financial entity and its providers.
It also raises the standard for transparency on architecture, failover, incident response and subcontracting chains across cloud regions and software supply.
When Query Volume Sets Quality
Microsoft’s CEO details how search distribution drives data, relevance and ad economics—and why Bing can’t break Google’s feedback loop.

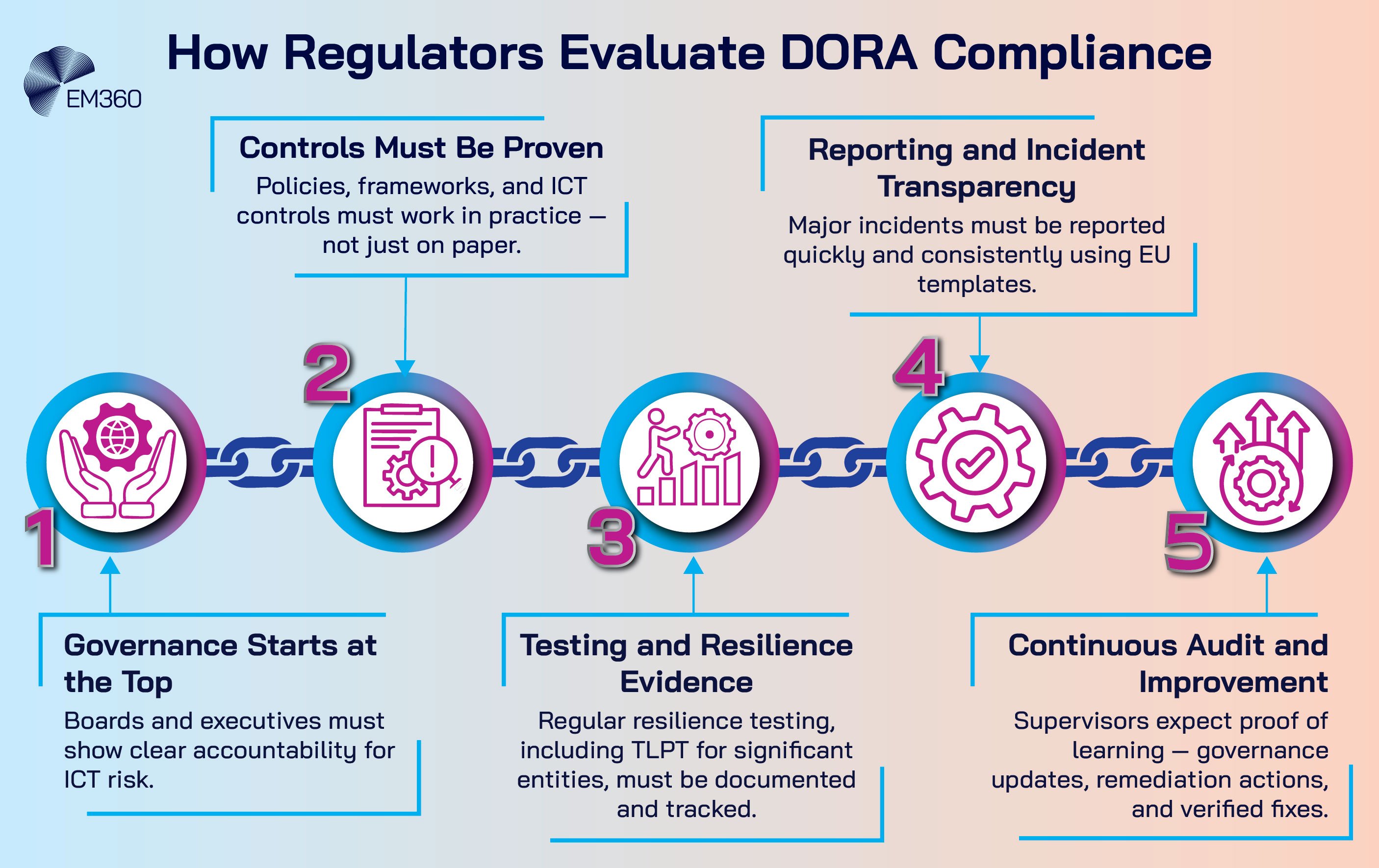
Inside the Enforcement Playbook — What Regulators Expect
DORA enforcement translates into a practical checklist for leadership. The measures below are how supervisors will test maturity, and how executives should prepare.
Prove it, do not just plan it
Evidence beats intent. Establish a rolling testing programme for critical services that blends vulnerability management, disaster recovery exercises and scenario drills. If you are likely to fall into scope for threat-led testing, begin scoping now with risk-based prioritisation and a multi-year budget.
Track remediation to closure with owner, date and residual risk. Report test results and trends to the board in business terms, not tool outputs.
Third-party oversight beyond contracts
Paper is not protection. Perform due diligence before onboarding, including data location, recovery objectives, incident history and security certifications. Update contracts for incident notification timelines, audit rights and subcontractor obligations. Maintain a current register of ICT providers and material services.
Move from annual reviews to continuous monitoring, including service reports, SLA performance and targeted resilience tests of interfaces and failover paths. Keep exit strategies executable, with playbooks that show how to switch or recover if a provider fails.

Reshaping Music’s AI Playbook
Artists, labels and AI firms clash over control, compensation and creative rights as synthetic tracks compete with human-made music.
Governance as a living system
Operational resilience is now a leadership discipline. Define accountabilities across the CIO, CISO and CRO, supported by an independent risk or audit function that can challenge plans and evidence. Make resilience part of your management rhythm.
That means boards receiving regular ICT risk updates, executives reviewing incident trends against thresholds, and teams collaborating across security, operations, risk and business continuity. Culture shows up in how quickly issues surface, how clearly decisions are recorded and how consistently learnings turn into improvements.
What Comes Next — Preparing for Audits and Penalties
Expect national audits, thematic reviews and requests for documented proof through 2026. Enforcement tools include remediation orders, public statements and fines if firms ignore material obligations. Significant entities should prepare for the first wave of TLPT scheduling, which typically runs on a three-year cycle and requires substantial planning.
Oversight of critical ICT providers will expand, bringing coordinated actions that can include on-site inspections and mandated improvements. Firms that treat this phase as a chance to demonstrate reliable service will strengthen customer trust and market credibility.
Inside Neuralink’s Human Trial
First-in-human brain implant shifts BCIs from lab concept to live deployment, raising new questions on regulation, access and clinical benefit.
Sector-wide testing and collaboration
Supervisors may convene sector-wide resilience drills that simulate incidents across payments, market infrastructure or shared service providers. Firms that can share threat intelligence quickly and respond in a coordinated way will reduce systemic risk and shorten recovery time.
Collaboration is not only good practice, it is aligned with DORA’s goal of raising resilience across the ecosystem rather than within isolated compliance programmes.
Final Thoughts: Resilience Is the New Currency of Trust
DORA enforcement turns operational resilience into a public signal of leadership, discipline and customer commitment. The shift from preparation to proof is already reshaping how boards govern ICT risk, how executives invest in testing and recovery, and how firms manage the suppliers that keep their services running.
Treat resilience as a continuous system, not a checklist that ends at year-end. Those who do will navigate audits with confidence, recover faster when incidents occur and convert regulatory readiness into competitive strength. For ongoing guidance on the practices that matter most, follow EM360Tech’s coverage of resilience, compliance and risk leadership.







Comments ( 0 )