The NIS2 Directive is the European Union’s upgraded cybersecurity regulation that replaces NIS1, extends obligations across 18 sectors, and puts leadership accountability at the forefront of compliance. It is not a narrow security uplift.
It is a structural shift that touches how organisations govern critical infrastructure, manage supply chain risk, and evidence competence to supervisory authorities under EU legislation. With the Commission’s Implementing Regulation (EU) 2024/2690 defining incident thresholds and technical expectations, and national transposition advancing across Member States, compliance has moved from theory to execution.
ENISA’s latest threat landscape confirms the pressure: thousands of cyber incidents analysed in the last cycle, with social engineering and DDoS prominent across public administration, transport, and digital services.

NIS2 responds by turning essential and important entities into stewards of sector resilience. The path forward is to treat compliance as a living risk management programme embedded in operations and supplier oversight. That starts with clarity on what has changed.
What NIS2 Changes — From Directives to Direct Accountability
At its core, NIS2 is about maturity. It replaces fragmented national efforts with a single, enforceable framework that connects regulation, governance, and execution. The directive does not simply expand coverage; it deepens responsibility, holding leadership directly answerable for the resilience of their operations and supply chains.
From fragmented national rules to unified EU oversight
NIS1 delivered a first framework, but uneven application across Member States left gaps. Definitions varied, supervisory expectations differed, and reporting thresholds were inconsistent.
NIS1 vs NIS2 reflects a maturity curve: NIS2 harmonises core obligations, clarifies scope, and strengthens cooperation among national supervisory authorities and CSIRTs. It is a single regulatory language designed to reduce ambiguity for organisations that operate across borders.
Board-level accountability becomes the norm
NIS2 sets clear expectations for governance. Senior management is directly responsible for cyber risk oversight, including approval of security policies, resourcing, and programme effectiveness.
Penalties are calibrated to entity type and scale, with essential entities facing maximum fines that can reach at least €10 million or 2 per cent of global turnover, and important entities subject to lower but still material ceilings. The signal is simple: leadership must be able to explain how cyber risk is managed, tested, and improved.
Tightened supervision and harmonised enforcement
The Commission’s Implementing Regulation (EU) 2024/2690 brings practical detail. It defines incident materiality and notification timelines, and specifies methodological requirements for areas such as vulnerability handling and service continuity.
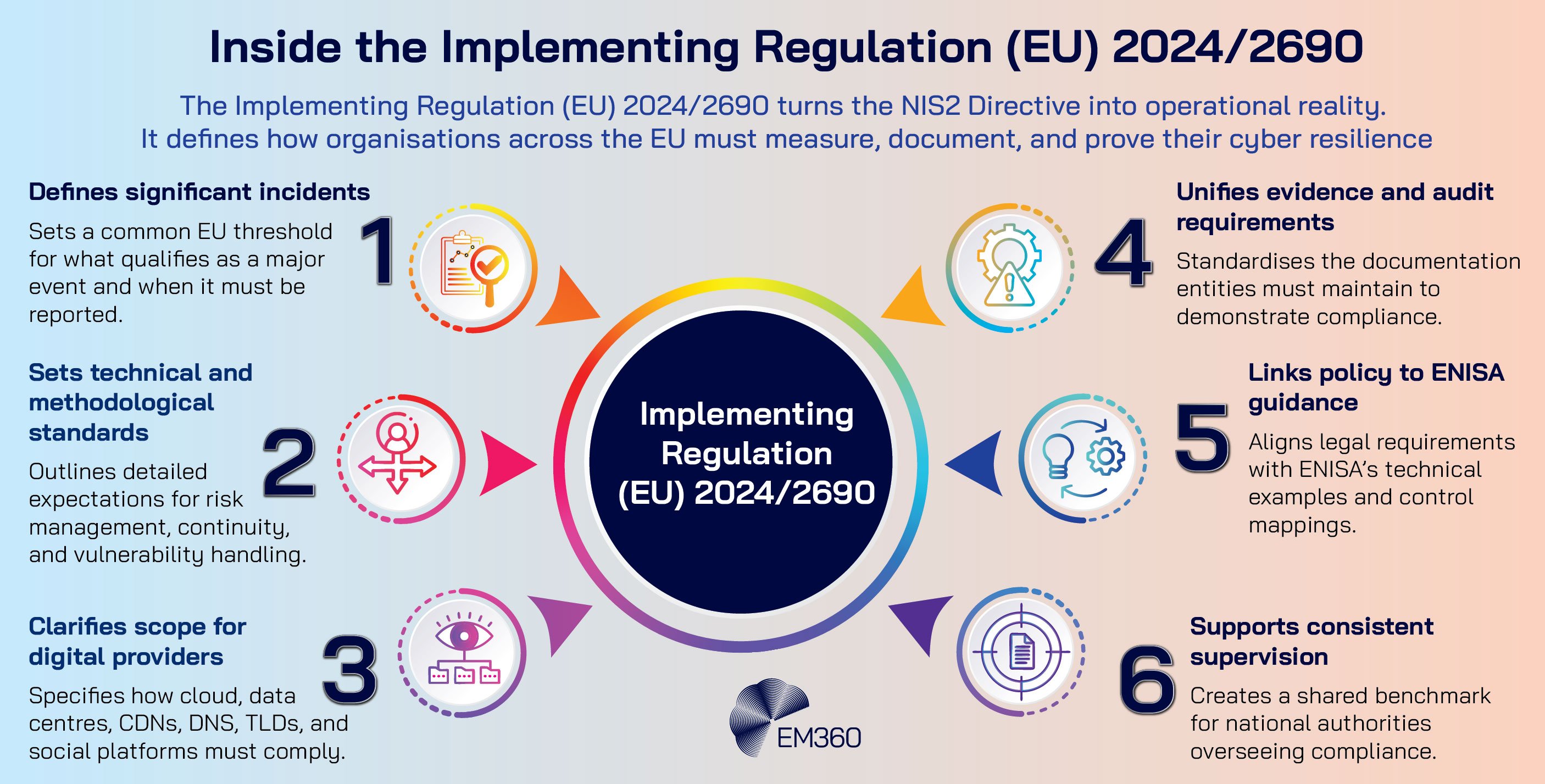
Digital infrastructure and providers receive particular focus, including cloud, data centres, content delivery networks, DNS and TLD services, online marketplaces, search engines, and social media platforms. This closes the loop between principle and practice, giving authorities a common baseline for oversight and giving entities a common blueprint for evidence.
Who’s Now In Scope — The Expanded EU Sectors
NIS2’s expansion is not a bureaucratic exercise. It reflects how digital dependency now underpins every critical service and supply chain in Europe. By broadening its reach, the directive acknowledges that resilience can no longer stop at traditional infrastructure—it must extend to every sector that keeps the economy and society running.
Eighteen sectors under the microscope
NIS2 widens the net across three broad groupings:
- Critical infrastructure and essential services: energy, transport, banking, financial market infrastructure, health, drinking water, wastewater, space.
- Digital infrastructure and platforms: DNS and TLD services, cloud computing services, data centre services, content delivery networks, trust services, providers of public electronic communications networks, online marketplaces, online search engines, and social media platforms.
- Essential economy and public services: manufacturing of critical products, food, postal and courier services, chemicals, and public administration at central and regional levels.

Rethinking Trust at the Edge
Why protocol-era VPN and IKEv2 assumptions undermine Zero Trust, and what boards should ask about hidden edge dependencies.
This expansion reflects systemic interdependence. Disruption in digital infrastructure can cascade into hospitals, transport networks, and supply chains, which is why NIS2 scope is explicit about digital service providers and their role in continuity.
Essential vs important entities
Classification determines the intensity of oversight. Essential entities are typically larger or more critical operators whose disruption would have significant societal or economic impact. Important entities are still in scope but generally subject to less intrusive supervision.
Both must implement appropriate technical and organisational measures, maintain incident response and business continuity capabilities, and report significant incidents. The proportionality principle applies to how measures are applied, not to whether they are applied.
The vendor chain challenge
NIS2 recognises that resilience fails at the weakest link. That places supply chain risk at the centre of compliance. Managed service providers and other ICT suppliers now carry explicit obligations, and contracting models must support audit rights, incident cooperation, and continuity expectations.
The practical outcome is a more rigorous approach to third-party assurance, from due diligence and onboarding through to continuous monitoring, testing, and exit planning.
Implementation in Practice — New Standards and Sector Readiness
With the directive now in force, the question has shifted from interpretation to execution. Member States are translating NIS2 into national law, and enterprises are moving from policy design to proof of compliance. The coming years will test how well ambition turns into measurable resilience.
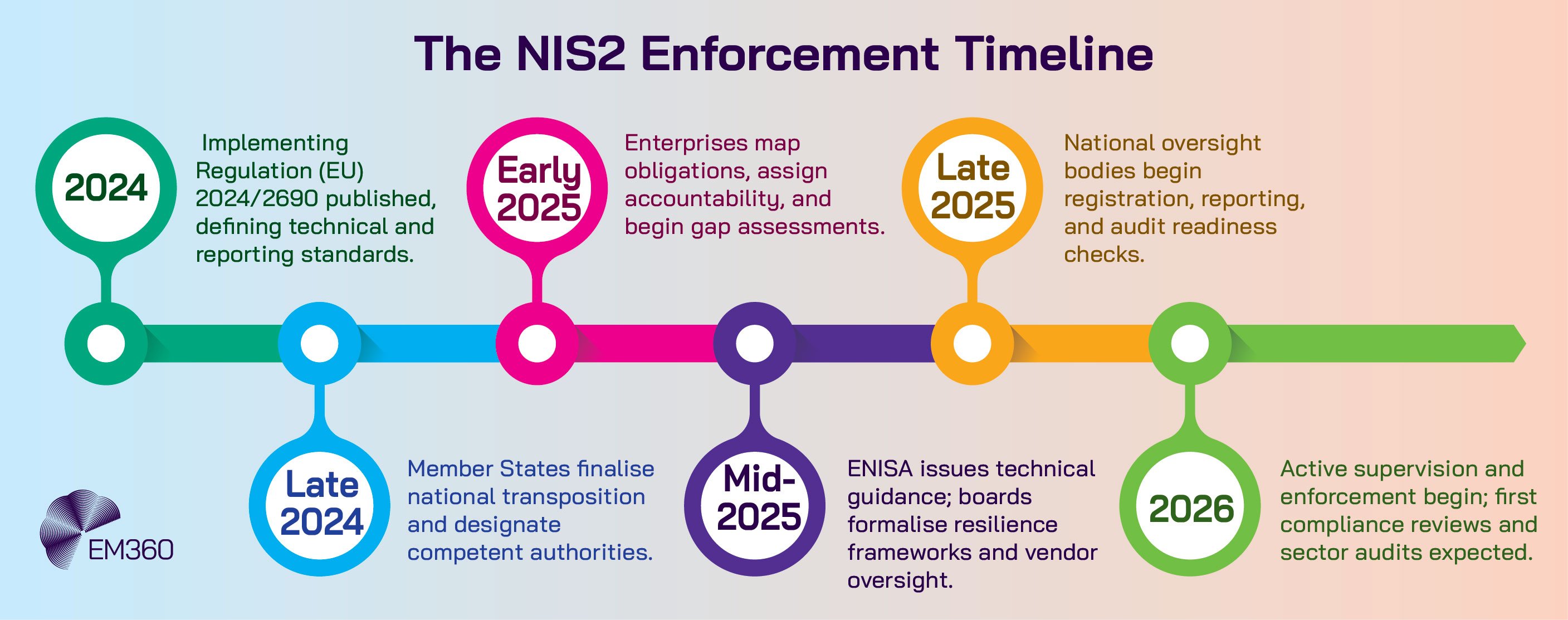
2025–2026: The enforcement phase begins
By late 2025, several Member States had completed or advanced their national transposition, while others were finalising bills or secondary legislation. Italy’s national authority formalised registration and oversight pathways. Germany progressed its implementation act alongside an updated KRITIS approach.
France advanced a resilience-focused bill that aligns NIS2 with related frameworks. For multinationals, this means staying aligned to the EU baseline while monitoring national deviations that affect reporting mechanics, supervisory processes, or sector nuances. Cross-border compliance depends on a common internal standard that can flex to local rules.
ENISA’s 2025 technical guidance
Inside Modern Pentest Stacks
How integrated scanners, WAFs, IDS and password tools now form a unified layer in security architectures to expose and close attack paths early.

ENISA’s mid-2025 guidance translates Implementing Regulation 2024/2690 into actionable measures and evidence examples for digital infrastructure and ICT service management. It maps governance roles and skills to the European Cybersecurity Skills Framework so that boards and technology leaders can staff programmes with the right competencies.
This is the practical handbook for proving that controls are in place and tested, and that responsibilities are owned by qualified people.
Shared accountability under the Cyber Solidarity Act
The EU Cyber Solidarity Act adds an EU-level detection and crisis support layer. It does not dilute NIS2 responsibilities. It creates a mechanism for cross-border assistance, large-scale incident response, and coordinated exercises.
For entities, this means preparing to interface with national teams and EU-level capacities while maintaining local accountability for prevention, detection, and recovery.
What the Data Reveals — The Sectoral Threat Landscape
The logic behind NIS2’s urgency is written in the data. Europe’s threat landscape has intensified, with attacks growing in both volume and sophistication. Understanding where and how these incidents occur is essential to seeing why regulators widened the net—and why every covered sector now faces closer scrutiny.
Rising incident volume and evolving attack vectors
ENISA’s latest threat landscape reports thousands of analysed incidents in the last cycle, with phishing and other social engineering techniques accounting for a large share of initial access. Vulnerability exploitation remains a significant driver of compromise.
DDoS activity continues to affect digital services at scale, stressing availability and customer trust. These patterns align with the expanded focus on digital infrastructure under NIS2.
Sector hotspots under NIS2 focus
Public administration, transport, digital services, and manufacturing feature prominently in recent incident data. That overlap matters. NIS2’s sector expansion is not arbitrary. It reflects where disruption can propagate quickly and where coordinated defence yields system-level benefits.
Data-driven prioritisation for enterprise leaders
Data points should dictate sequencing. If social engineering dominates initial access, accelerate targeted awareness and control of identity flows. If DDoS continues to degrade service quality, invest in layered mitigation, resilient architectures, and realistic failover exercises.

When Sanctions Don't Stop Hackers
US indictments and bounties have not slowed this group. See why traditional defenses and policy tools struggle against state-tolerated cybercrime.
If exploitation of known vulnerabilities is prevalent, prioritise patch pipelines and configuration baselines. Cyber threats are multi-vector. The response must be multi-disciplinary.
How Enterprises Can Operationalise Compliance
Compliance under NIS2 cannot be achieved through documentation alone. It demands structure, ownership, and clear lines of accountability that extend from the boardroom to operations. The first step is building a governance model capable of turning regulatory intent into everyday practice.
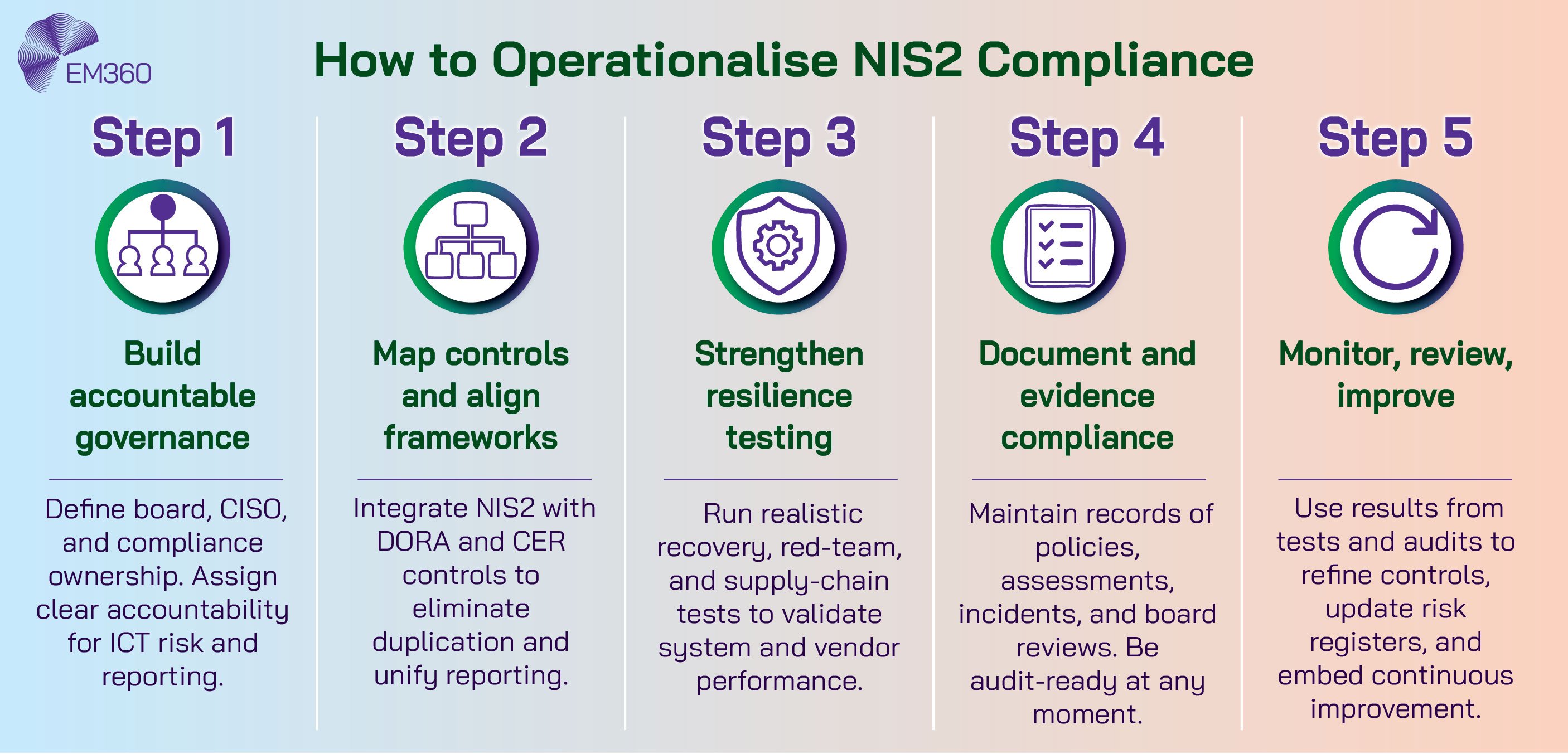
Build a governance structure that scales
Start by clarifying accountability. The board approves strategy and receives regular reports on risk posture. The CISO owns the security and resilience programme. The CIO aligns architecture and operations.
Compliance and legal provide regulatory interpretation and evidence standards. Use the ENISA and ECSF role mapping to define skills, responsibilities, and escalation paths. A clear governance framework stops gaps from forming between teams.
Integrate compliance with resilience
NIS2 sits alongside the Digital Operational Resilience Act (DORA) and the CER Directive. Duplicate projects add cost without reducing risk. Map controls once, then surface them through the appropriate reporting channels. Align incident categories and thresholds so that one incident generates the right notifications, evidence, and actions across frameworks.
Treat testing and exercising as a single resilience testing programme that covers business services, technology, and third parties.
Test, document, prove
NIS2 moves the burden from assertion to evidence. Maintain a documentation pack that includes policies, risk assessments, asset and service maps, supplier registers, incident playbooks, test plans, test results, remediation actions, and board minutes recording key decisions.
For incident response, rehearse classification criteria and notification workflows so that weekend or holiday events still meet timelines. For business continuity, demonstrate that recovery time and recovery point objectives are viable under realistic stress.
Cross-Border Challenges and Future Alignment
When OT Becomes a Cyber Target
How IT-OT convergence is forcing boards to rethink industrial risk, resilience, and which vendors can truly protect critical operations.

Achieving harmonisation across 27 jurisdictions is complex in theory and harder in practice. Each Member State interprets and enforces NIS2 through its own legal lens, creating subtle but significant variations. Navigating these differences has become a defining test of resilience for multinational enterprises.
National divergence and industry adaptation
The EU has set a harmonised floor, not a ceiling. National authorities can interpret and operationalise differently, particularly in sectors with existing local frameworks. For organisations spanning several jurisdictions, the answer is a common internal standard that is at least as strict as NIS2, plus a register of national deltas.
Keep contracts, reporting templates, and assurance activities flexible enough to satisfy local expectations without fragmenting the operating model.
The next wave of EU harmonisation
Direct oversight of critical third-party providers under other regimes, plus ongoing Commission reviews, points to continued alignment across EU security laws. Expect iterative guidance, more structured sector exercises, and closer scrutiny of cross-provider concentration risk.
Preparation is not a one-off. It is the maintenance of organisational fitness: monitoring draft texts, adjusting testing cadence, and investing in people who can join the regulatory dots.

Final Thoughts: Regulation Only Works When Resilience Becomes Routine
NIS2 is a watershed. It expands scope across sectors, hardens expectations on leadership, and demands proof that controls work when incidents strike. The expanded coverage reflects the reality of modern interdependence, where a disruption in one provider can ripple through healthcare, transport, finance, and public services. The lesson is consistent.
Treat operational resilience as a continual practice within cybersecurity governance, align controls across EU frameworks, and build evidence into the way teams operate every day. The organisations that will thrive under NIS2 are not those that chase checklists but those that make resilience habitual.
Have a look at EM360Tech’s latest analyses and expert insights to benchmark your programme and plan your next step with confidence.







Comments ( 0 )