Disaster recovery and business continuity are the backbone of enterprise resilience. Disaster recovery is about restoring systems and data after disruption. Business continuity ensures critical operations carry on through the disruption. Together, they define whether an organisation can withstand shocks and recover with confidence.
The need for both has never been sharper. Breaches cost millions, outages are triggered by increasingly complex IT environments, and climate-driven disasters continue to escalate. At the same time, regulators are raising expectations, demanding that enterprises prove their resilience instead of promising it.
Enterprises now face a simple reality: disaster recovery and business continuity are no longer technical exercises. They are strategic capabilities tied directly to data protection, compliance, and reputation.

Why Disaster Recovery and Business Continuity Matter More Than Ever
Enterprises today operate in an environment where disruption is constant. The cost of downtime continues to climb, with IBM reporting the average global data breach now exceeds $4 million. Uptime Institute data shows more than half of recent outages cost organisations over $100,000. NOAA’s figures confirm the financial scale of physical risks too, with billions lost each year to climate-related disasters.
The threat landscape is also shifting. Ransomware attacks remain relentless, but what is changing is speed. Attacker dwell times have dropped to only a few days, leaving organisations with less opportunity to detect and contain threats before they cascade into full disruption. In parallel, third-party breaches are rising, amplifying the risk exposure across supply chains.
On top of operational and security pressures, regulation is raising the bar for resilience. Europe’s Digital Operational Resilience Act (DORA), the US Securities and Exchange Commission’s disclosure rules, and NIS2 all require organisations to demonstrate robust continuity and recovery capabilities. NIST’s Cybersecurity Framework 2.0 further formalises governance expectations, embedding resilience into the way enterprises must manage risk.
For leaders, the conclusion is unavoidable. Disaster recovery and business continuity cut directly across cost, compliance, and cyber resilience. They are no longer support functions tucked in the background. They are frontline measures that determine how strong an enterprise really is.
Business Continuity vs Disaster Recovery vs Resilience
Business continuity planning is about keeping operations running. In other words, the whole purpose of it is to make sure that essential business functions can continue even while systems are down or facilities are disrupted.
Disaster recovery planning is more focused but no less critical. It deals with restoring IT systems, applications, and data after an incident. Recovery time objectives (RTOs) and recovery point objectives (RPOs) are central here, setting the benchmarks for how quickly and how much can be recovered.
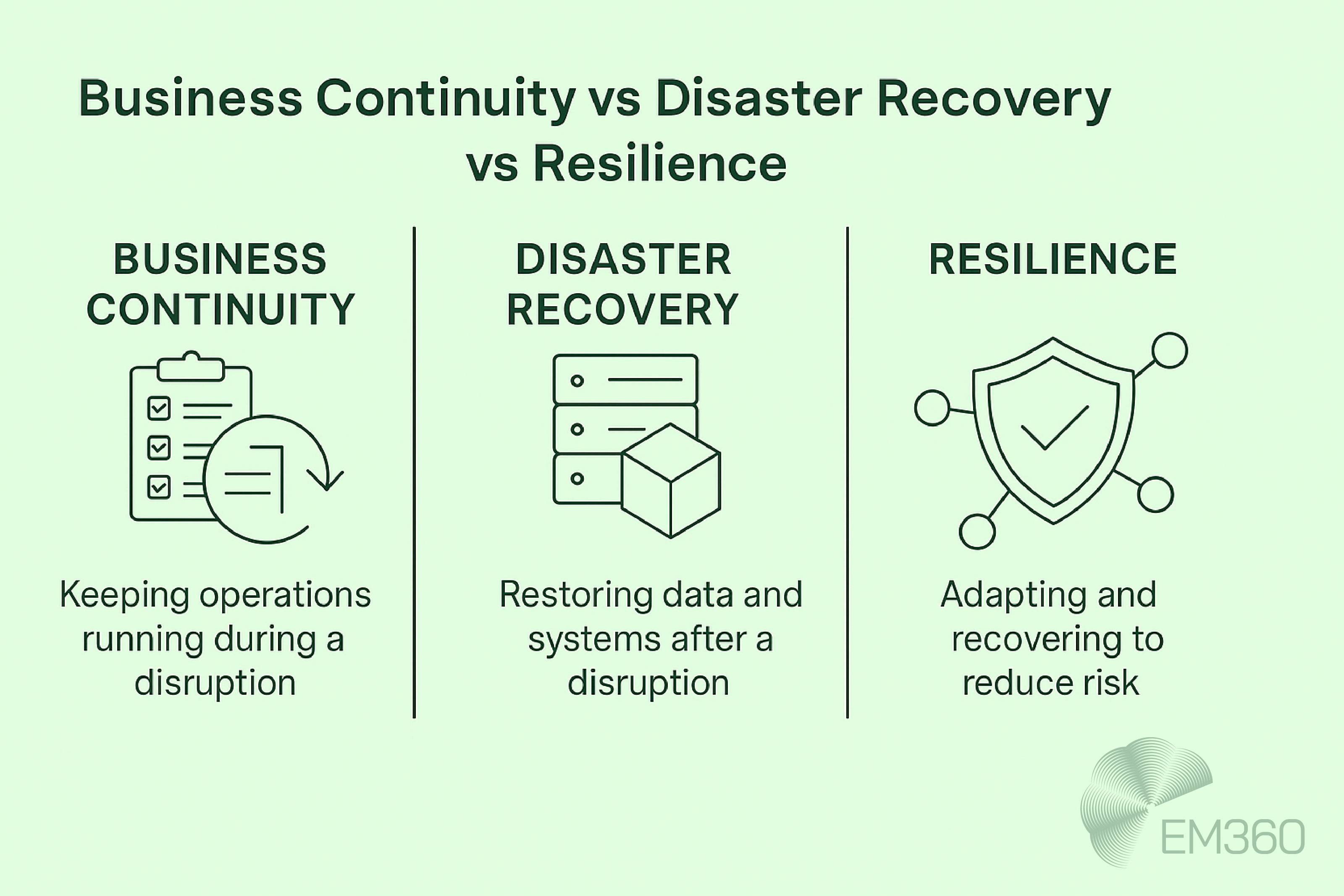
Organisational resilience goes further. It is the integration of both continuity and recovery into a proactive posture that allows an enterprise not just to survive disruption but to adapt through it. Resilience is the ability to anticipate risks, absorb impact, and return to normal operations without losing trust, compliance, or competitive standing.
A ransomware attack makes the distinction clear. Business continuity planning ensures that customer-facing services can still operate, perhaps by switching to manual processes or activating backup systems. Disaster recovery planning determines how quickly encrypted systems and data can be restored from clean backups.
Resilience is the point where both of these capabilities work together, supported by governance and testing, so the enterprise can contain the incident, continue operations, and recover without prolonged damage to reputation or compliance.
For enterprise leaders, the distinction matters. Business continuity and disaster recovery provide the mechanisms. Resilience is the outcome when they are combined, governed, and tested as part of a single strategy.
The Core Framework for Enterprise Continuity
Enterprise continuity depends on structure. ISO 22301, NIST CSF 2.0, and CISA’s Cybersecurity Performance Goals all emphasise the same principle: resilience must be built on a repeatable framework that can be tested, governed, and improved.
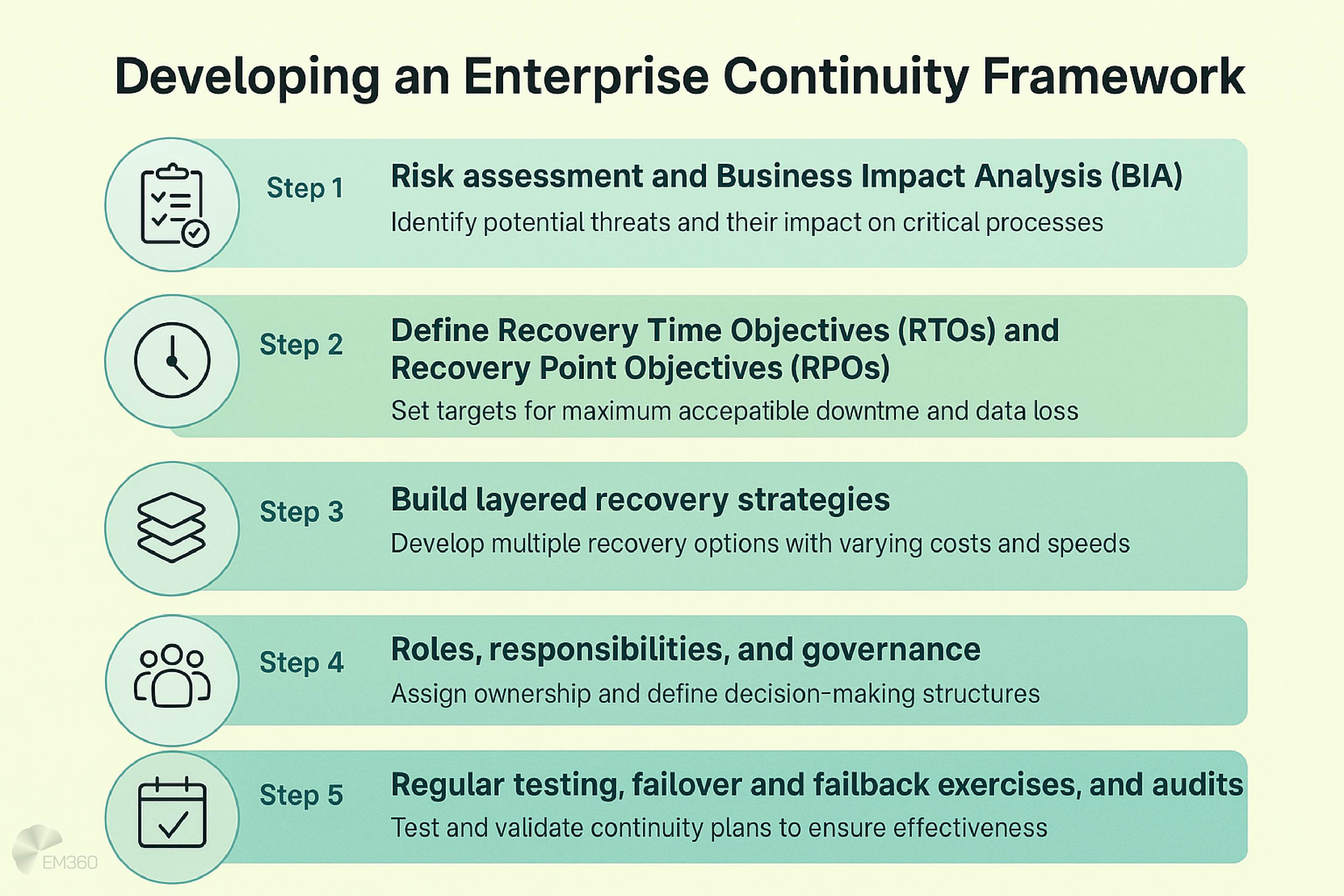
Step 1: Risk assessment and Business Impact Analysis (BIA)

BCM Software and the DORA Shift
Why boards are replacing static plans with platforms that prove resilience, meet 2025 regulatory tests, and turn BCM data into audit-ready evidence.
A risk assessment establishes the threats most likely to affect the organisation, from cyberattacks and system outages to natural disasters and supplier failures. A BIA looks at how those risks would hit critical processes, measuring the financial, operational, and reputational impact.
Step 2: Define Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs)
Every critical service needs recovery benchmarks. RTO sets the maximum downtime. RPO defines the acceptable level of data loss. These metrics turn continuity planning into measurable commitments that guide investment in technology and processes.
Step 3: Build layered recovery strategies
Organisations need options. Hot, warm, and cold recovery sites offer different balances of cost and speed. Cloud disaster recovery provides another layer, enabling rapid failover across regions or providers. A layered approach gives critical services more than one recovery path, so no single point of failure can bring everything down.
Step 4: Roles, responsibilities, and governance
Business continuity management has to be owned across the enterprise. Clear accountability ties it directly into integrated risk management and enterprise risk management. When roles are defined, decision-making is faster during disruption, and governance ensures that continuity strategies are aligned with wider risk priorities.
Step 5: Regular testing, failover and failback exercises, and audits
Plans only hold up if they are tested. Tabletop exercises, simulated outages, and full failover drills confirm whether recovery objectives can be met. Failback tests prove that systems can return to normal without adding new risks. Regular audits provide assurance that the framework is working and aligned with standards.
Enterprise continuity is not a checklist. It is a discipline of structured planning, measurable objectives, and constant validation. This is how business continuity management and disaster recovery combine into a single, resilient strategy.
Technology Shaping the Future of BC and DR
Technology is reshaping how enterprises approach continuity and recovery. Cloud, AI, and automation are no longer add-ons. They are central to strategies that reduce risk, strengthen recovery, and simplify operations.
Cloud-native disaster recovery
Designing Resilient Data Backup
Inside modern backup architectures that span cloud, NAS and cleanrooms to keep data recoverable across complex hybrid estates.

Cloud disaster recovery gives enterprises more agility, but it also introduces new dependencies. Multi-cloud strategies protect against a single provider outage, while SaaS applications often expose gaps in continuity planning. Critical services running in the cloud still need clear failover and failback processes.
Immutable storage and cyber vaulting
Immutable backups are becoming a cornerstone of cyber recovery. Features such as AWS S3 Object Lock and Azure Immutable Blob prevent backups from being altered or deleted, even by malicious actors. Combined with isolated “cyber vaults”, they give organisations a trusted recovery point after a ransomware attack.
AI in detection and response
Artificial intelligence is changing how threats are detected and contained. Machine learning models can flag anomalies faster than human teams, cutting down the window of disruption. At the same time, IBM and others warn that AI governance must be built in, or automation can create its own blind spots and risks.
Observability and automation
Outages often stem from complexity. Advanced observability tools and automated recovery processes reduce that risk by spotting failures in real time and executing predefined recovery steps. Automation removes human delay from failover and failback, giving enterprises faster and more predictable recovery.
Technology is not a replacement for continuity planning. It is the force multiplier that makes disaster recovery and business continuity faster, more reliable, and more resilient.
Preparing for Ransomware and Cyber-Driven Disruptions
Ransomware remains one of the most disruptive risks enterprises face. Attackers now move faster, target backups directly, and exploit supplier dependencies to widen their reach. Continuity planning has to assume a breach and prepare for recovery under hostile conditions.
Immutable and offline backups
The first line of ransomware recovery is having data that cannot be encrypted or deleted. Immutable backups and offline copies give enterprises a clean recovery point. Rapid restore paths then become the difference between prolonged downtime and a controlled return to operations.
Segmentation, privileged access, and supplier monitoring

When Downtime Threatens Survival
Stress-test your continuity plan, align risk scenarios to impact, and close gaps before cyberattacks or outages hit operations.
Technical controls play a critical role in continuity. Network segmentation limits lateral movement once an attacker is inside. Privileged access management reduces the chance of critical systems being taken over. Supplier monitoring closes off one of the fastest-growing attack vectors by ensuring that third-party disruptions do not cascade into core operations.
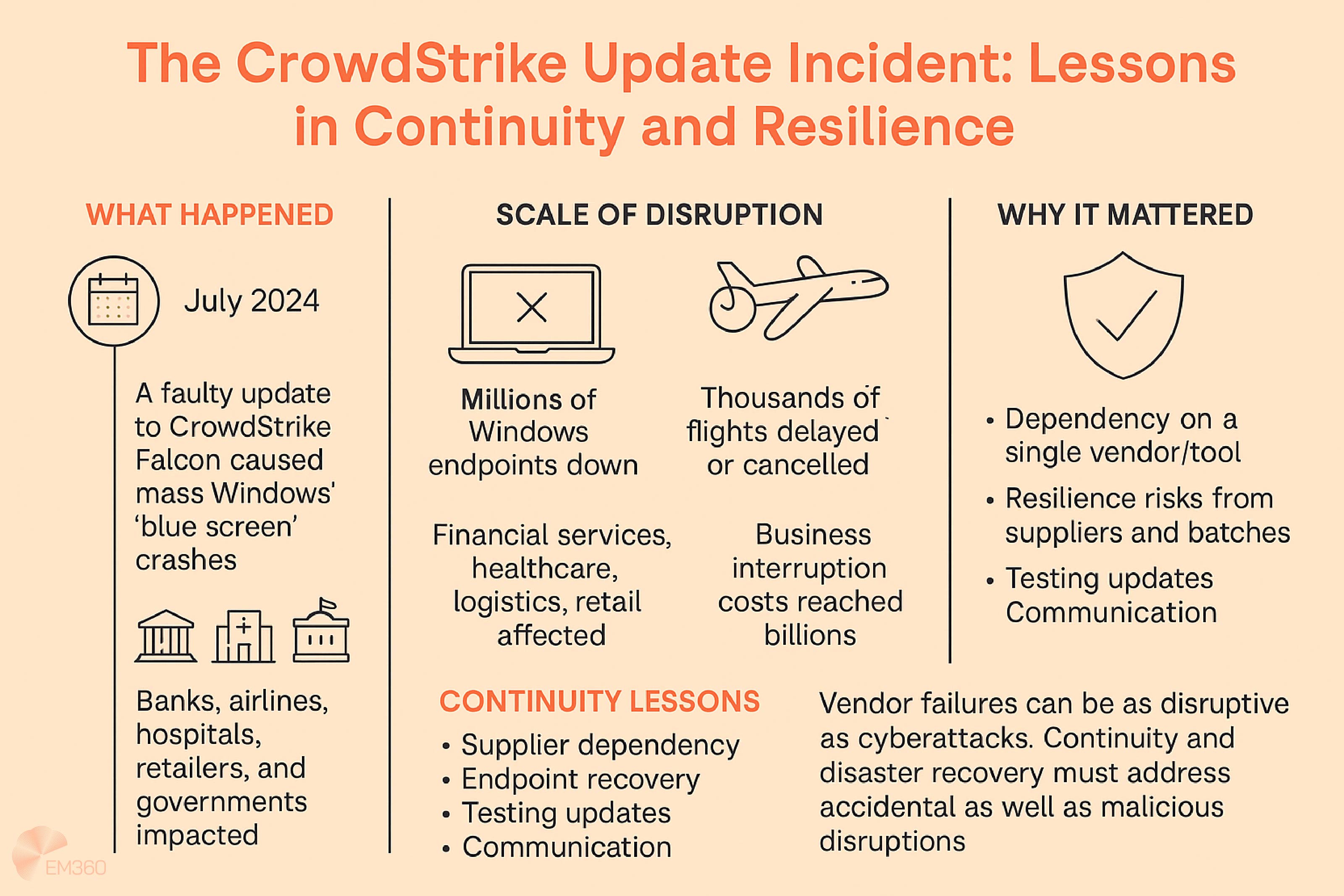
Lessons from the CrowdStrike incident
The recent global outage triggered by a faulty CrowdStrike update showed that continuity planning cannot stop at traditional cyberattacks. Endpoint failure at scale created downtime across industries, highlighting that reliance on a single security tool can itself become a continuity risk. Enterprises need to plan for both malicious and accidental disruptions in equal measure.
Testing under assume-breach conditions
Testing has to reflect reality. Simulated ransomware attacks and breach scenarios show whether backup data can be restored quickly, whether detection and response processes hold up, and whether business units can continue operating under stress. Preparing for the worst-case scenario makes recovery faster, cleaner, and more predictable when an actual incident occurs.
Cyber-driven disruption is not a remote possibility. It is a recurring threat that requires disaster recovery and business continuity to be designed, tested, and governed as part of the same strategy.
Addressing Physical and Climate Risks
Cyber risks dominate the headlines, but natural disasters and facility outages remain just as critical to business continuity. NOAA data shows a steady rise in billion-dollar climate events, each bringing the potential to knock out power, disrupt facilities, and fracture supply chains.
Facility redundancy and power resilience
Continuity depends on physical infrastructure as much as digital. Redundant facilities, backup power systems, and failover capacity at the data centre level ensure that operations can withstand outages linked to storms, floods, or grid instability.
Data-centre continuity
Enterprises with on-premises or hybrid infrastructure need to account for location-based risks. Geographic separation between primary and secondary sites is essential. So is testing how fast workloads can be shifted between them when disaster strikes.
Supply chain continuity
Ransomware and Backup Strategy
Why board-level cyber resilience now hinges on automated, diversified backups instead of ransom payments after a major breach.

Disruptions ripple outward. Continuity planning has to extend to transport routes, logistics partners, and critical suppliers. Mapping dependencies and creating alternatives reduce the risk of a single break causing prolonged interruption.
Building climate resilience is not only about responding to events. It is about planning for a world where physical risks are more frequent, more costly, and more complex. Enterprises that treat facility recovery and supply chain continuity as part of the same strategy will be better positioned to absorb shocks and maintain trust.
Regulatory and Compliance Readiness
Resilience is not only a business priority. It is now a regulatory requirement. Global frameworks are converging around the need for continuity and recovery to be documented, tested, and proven.
EU DORA and ICT third-party risk
The Digital Operational Resilience Act (DORA) requires financial institutions in the EU to manage operational resilience across their entire ICT landscape, including third-party providers. This makes supplier risk part of the compliance mandate, not just an internal concern.
US SEC disclosure rule
In the US, the Securities and Exchange Commission now mandates that material cyber incidents be disclosed within four business days. This rule puts direct pressure on continuity planning, since enterprises must detect, assess, and respond fast enough to meet disclosure timelines while containing disruption.
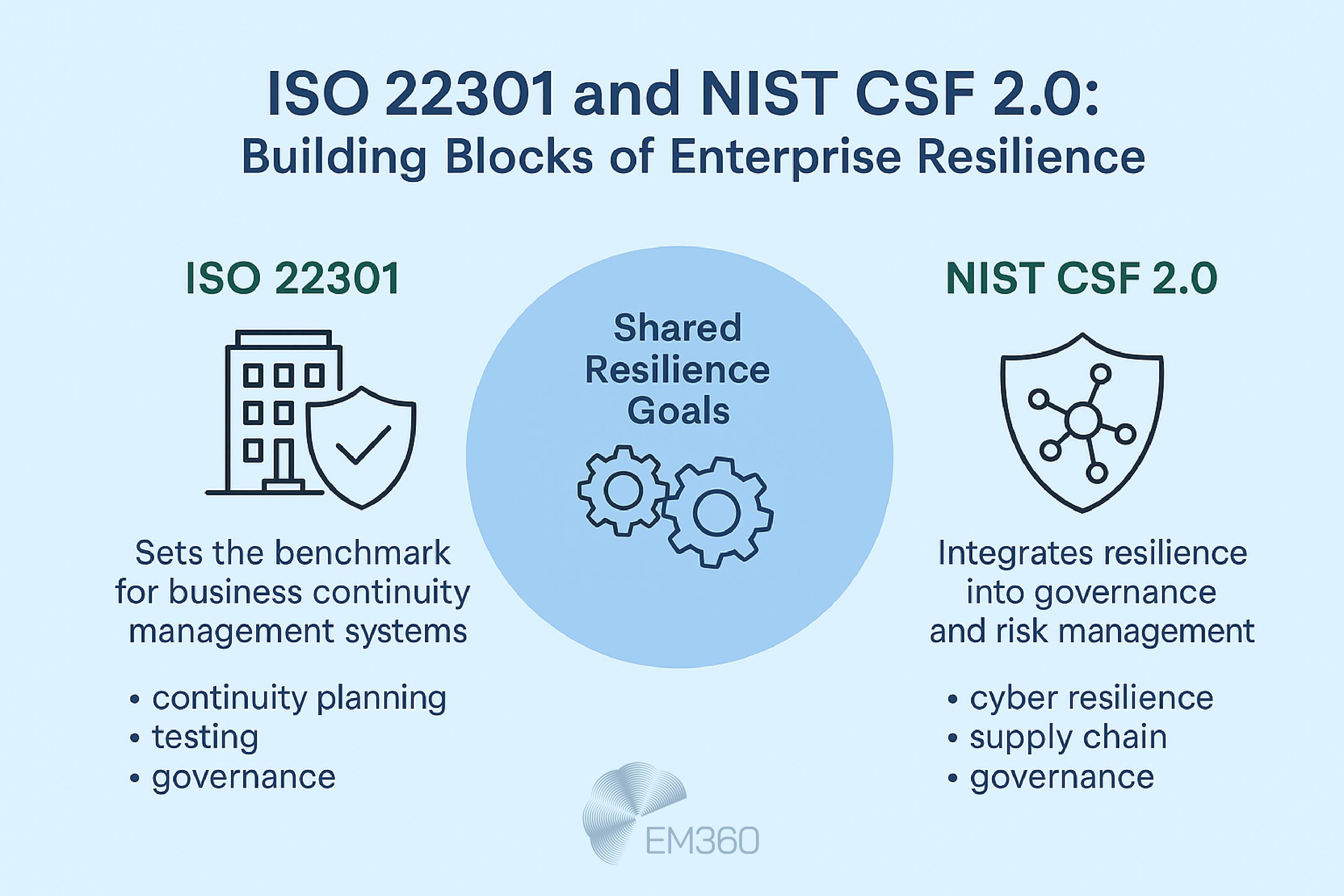
ISO 22301 and NIST CSF 2.0
Global standards provide the blueprint for compliance. ISO 22301 sets the benchmark for business continuity management systems, while NIST’s updated Cybersecurity Framework 2.0 integrates resilience into governance and risk management. Aligning with these frameworks allows enterprises to meet regulatory expectations while strengthening internal controls.
Proving resilience posture
Auditors, regulators, and boards are asking for evidence, not promises. Demonstrating a tested continuity and recovery posture is becoming central to enterprise governance. Regular reports, documented exercises, and measurable objectives are the means of showing that resilience is built in rather than assumed.
Compliance has become a forcing function for resilience. Enterprises that treat continuity and recovery as regulatory checkboxes will struggle. Those that embed them into strategy will be able to meet mandates and protect their reputation at the same time.
Testing, Governance, and Continuous Improvement
Continuity and recovery plans only work if they are tested, owned, and improved over time. Enterprises that treat them as static documents risk failure when disruption hits.
Types of testing
Different tests deliver different insights. Tabletop exercises validate decision-making and escalation paths. Simulations stress systems and people under realistic conditions. Full failover tests provide the ultimate proof that recovery time objectives and recovery point objectives can be met in practice, not just on paper.
Governance structures
A business continuity management system (BCMS) depends on clear ownership. Crisis management teams must know who leads, who escalates, and who makes decisions when time is short. Defined governance ensures BC and DR are embedded into enterprise risk management, not left to individual departments.
Feedback loops and lessons learned
Testing is only valuable if results are captured and applied. After-action reviews, incident debriefs, and lessons learnt from industry peers feed directly into stronger planning. Each cycle improves the organisation’s ability to respond, proving that resilience is a living capability rather than a one-time achievement.
Enterprises that combine structured testing with strong governance create continuity strategies that evolve with the threat landscape. This is what turns business continuity and disaster recovery into lasting resilience.
Practical Steps to Strengthen Your BC and DR Strategy Today
Resilience takes time to build, but there are actions enterprise leaders can take right now to strengthen their position.
Reassess your BIA and update RTO/RPO
A Business Impact Analysis should be kept current. Recovery time and recovery point objectives need to reflect today’s risks and critical services, not last year’s assumptions.
Invest in immutable and offline backups
Clean, untouchable recovery points are essential for ransomware recovery. Building both immutable and offline backup capabilities ensures you can restore operations even if attackers target live systems.
Map dependencies across third-party and SaaS platforms
Continuity risks often hide in suppliers and software-as-a-service providers. Mapping dependencies shows where single points of failure exist and creates a basis for stronger risk mitigation.
Run at least one enterprise-wide test every year
Small-scale tests validate processes, but only a full enterprise-wide exercise can show whether the organisation is truly prepared. Annual testing should include both continuity and recovery.
Integrate BC and DR into board-level reporting
Boards and regulators want visibility into resilience posture. Bringing business continuity and disaster recovery into risk reporting makes resilience a core part of governance, not an isolated function.
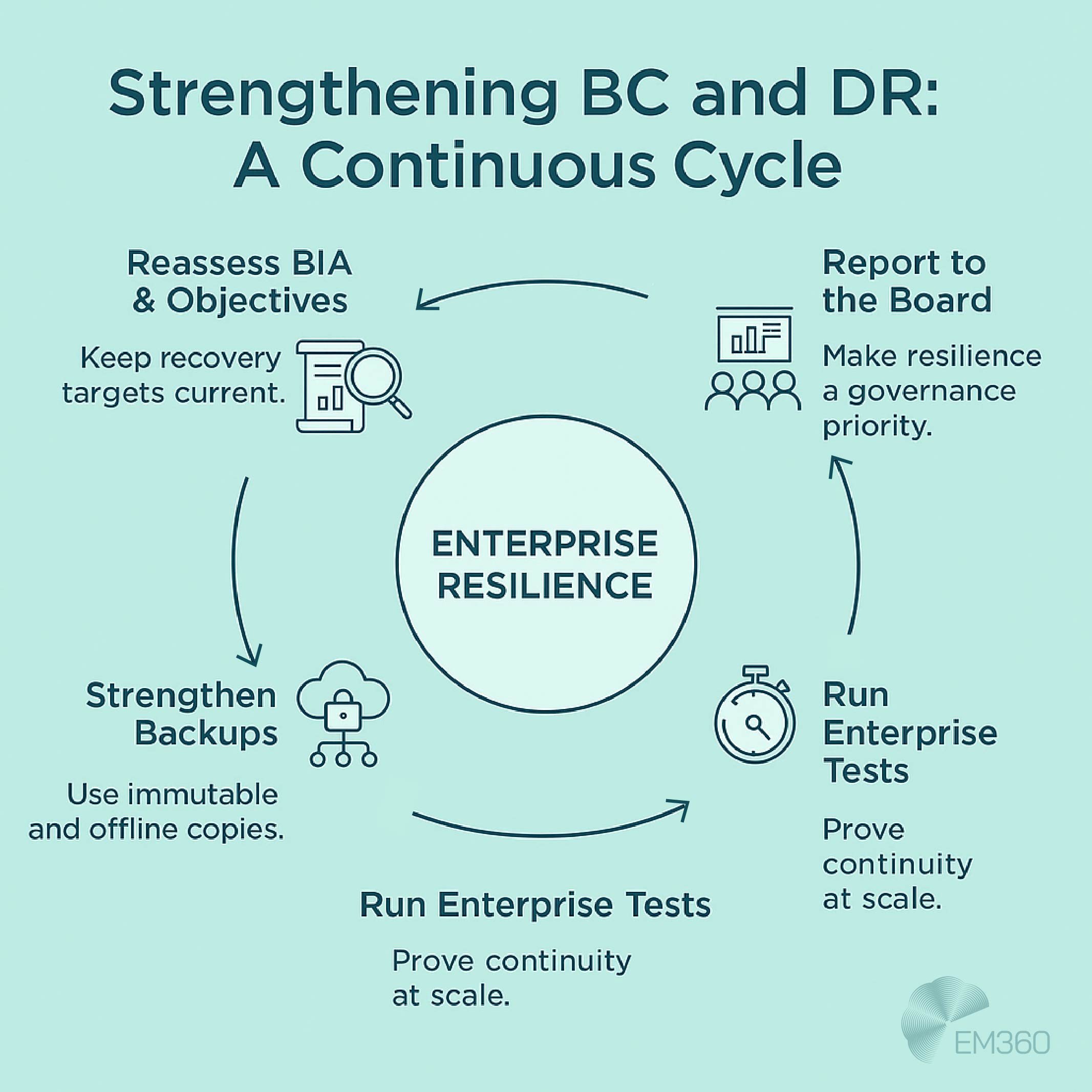
These steps do not replace a full strategy, but they create immediate impact. They raise confidence in continuity and recovery today while building the foundation for long-term enterprise resilience.
Final Thoughts: Resilience Is a Leadership Mandate
Business continuity planning and disaster recovery strategy are no longer IT checkboxes. They are board-level imperatives that define enterprise resilience. The ability to keep operations running, recover systems, and prove compliance now sits at the heart of trust and competitiveness.
Leaders cannot delegate resilience down the stack. They have to own it, govern it, and invest in it as a core business capability. Those that do will not only meet regulatory expectations but also protect their reputation and strengthen their position in the market.
Resilience is now a measure of leadership. Explore EM360Tech resources to stay ahead of how enterprises are building continuity and recovery strategies fit for today’s risks.





Comments ( 0 )