RansomHub, a ransomware-as-a-service (RaaS) platform, has quickly emerged as one of the largest and most dangerous ransomware groups in 2024. Likely an updated and rebranded version of Knight ransomware (previously known as Cyclops), RansomHub has significantly expanded its operations. Although it shares origins with Knight, it is unlikely that the original creators of Knight are behind RansomHub. The Knight ransomware source code was sold on underground forums in February 2024, signalling a possible shift in leadership.
Despite debuting only in early 2024, RansomHub has surged in activity and became the fourth most active ransomware group by the number of publicly claimed attacks within three months.
In this article, we explore the origins of RansomHub, some of their biggest attacks, how it rapidly grew into one of the most prolific ransomware groups and how to protect your organisation from a RansomHub attack.

What is RansomHub?
Since its launch in February 2024, RansomHub ransomware has rapidly gained notoriety by encrypting and exfiltrating data from over 210 victims. These victims include critical sectors such as water and wastewater systems, information technology, government services, healthcare, emergency services, and other vital infrastructure. RansomHub's ability to target high-profile industries has made it one of the most dangerous RaaS groups.
A critical factor in RansomHub's growth may be its recruitment of former affiliates from the now-defunct Noberus ransomware group (also known as BlackCat). Notably, one affiliate, known as Notchy, is reportedly working with RansomHub. Additionally, tools previously associated with another Noberus affiliate, Scattered Spider, were used in a recent RansomHub attack, further accelerating its impact.
Like many other RaaS models, RansomHub offers its malicious software to affiliates who carry out the attacks, creating a decentralised network of cybercriminals that can adapt quickly to new targets and vulnerabilities. The group's use of double extortion tactics—encrypting victims' data while threatening to release sensitive information publicly if the ransom is not paid—has proven highly effective in pressuring organisations to meet ransom demands. Moreover, RansomHub's ability to exploit zero-day vulnerabilities and leverage social engineering techniques has made it adept at bypassing traditional security measures, leaving even well-defended organisations at risk.
RansomHub's rapid establishment suggests that its operators are seasoned cybercriminals with deep connections in the cybercriminal underground. This expertise and network have helped the group become a significant player in the 2024 ransomware landscape.
Where is RansomHub from?
As with all these groups, its tricky to be definitive. However, there are some clues in statements the groups has made online.
As with many ransomware groups, pinpointing the exact location of RansomHub is challenging. However, certain clues can be found in statements made by the group online. On its official website, RansomHub reveals in its "About" section that it does not permit attacks on CIS (Commonwealth of Independent States) countries, Cuba, North Korea, or China. This suggests that RansomHub may be based in a country with favourable relations with Russia or perhaps even operates from Russia itself, given the group's decision to avoid targeting Russian allies.
While there is no concrete proof, these self-imposed restrictions on attack locations are common among ransomware groups with ties to Russian-speaking regions.
What are the Key Tactics used by RansomHub?
RansomHub employs several sophisticated tactics to extort victims, leveraging a double extortion model that encrypts systems and exfiltrates data. The stolen data is used as leverage to further pressure victims into paying the ransom. It’s important to note that data exfiltration methods vary depending on the affiliate responsible for the network compromise.
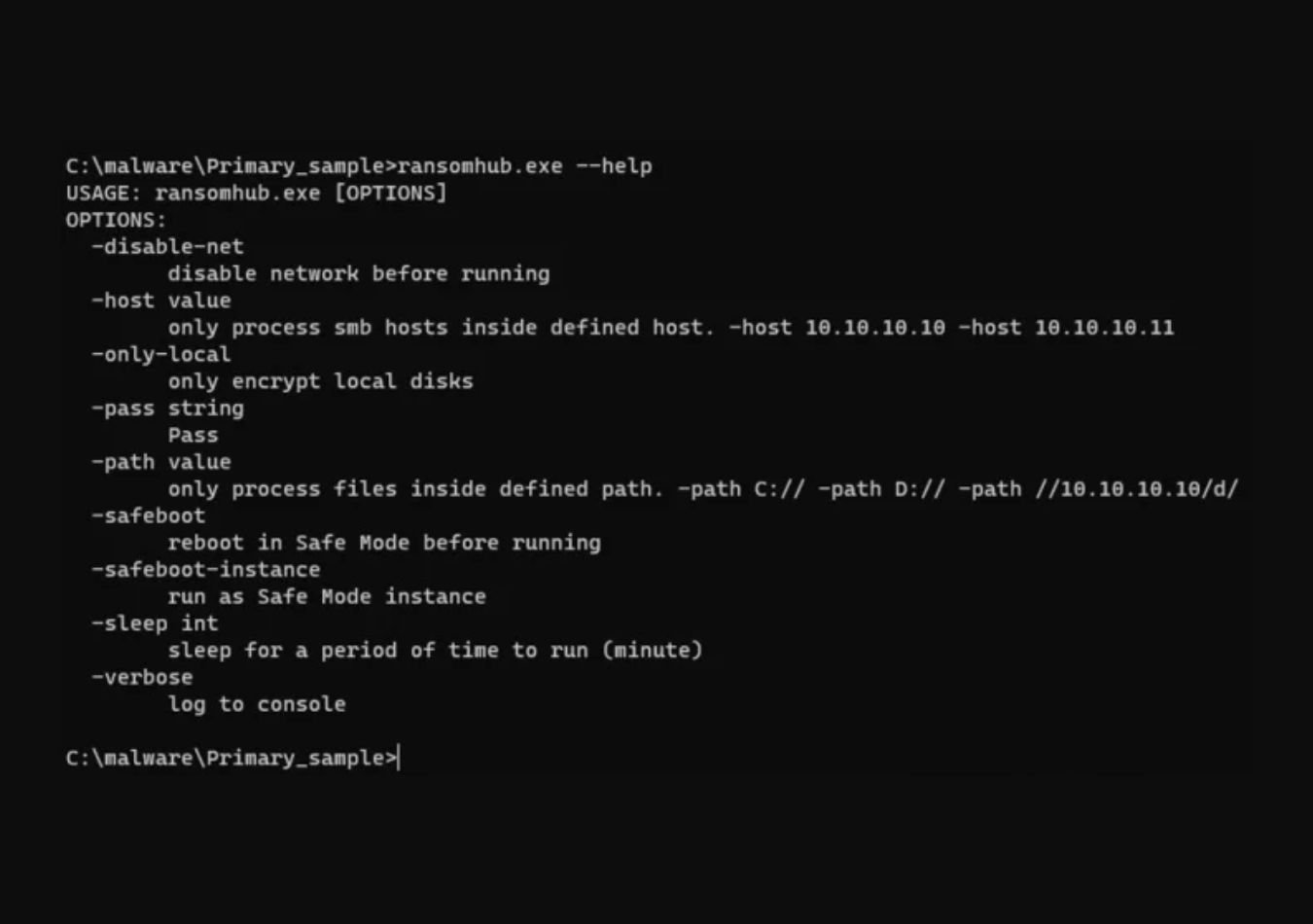
Unlike many ransomware groups, RansomHub does not provide an initial ransom demand or payment instructions in its ransom note. Instead, the note includes a client ID and directs victims to communicate via a unique Onion URL. Typically, the group allows between three to 90 days for payment before they publish the stolen data on the RansomHub Tor data leak site.
RansomHub uses several attack vectors to compromise systems, including phishing emails, exploitation of known vulnerabilities, and password spraying. Password spraying often targets accounts compromised in previous data breaches. The group also leverages proof-of-concept exploits from platforms like ExploitDB and GitHub to carry out these attacks.
Most Notable Attacks by RansomHub
In recent RansomHub ransomware attacks, attackers gained initial access by exploiting the Zerologon vulnerability. This critical flaw allows attackers to escalate privileges to domain administrator, giving them control over the entire domain.
Before deploying ransomware, the attackers utilized several dual-use tools. Atera and Splashtop were used for remote access, enabling them to maintain control over compromised systems. Additionally, NetScan was likely used to gather information about network devices, aiding in the reconnaissance phase of the attack. To disrupt operations, the RansomHub payload executed iisreset.exe and iisrstas.exe command-line tools to stop all IIS services, effectively crippling web-based applications.
Christie's
RansomHub took responsibility for a cyberattack on the prestigious British auction house Christie’s. The group is threatening to leak "sensitive personal information" from identification documents, including names, dates of birth, and nationalities, according to a screenshot from RansomHub’s dark web site.
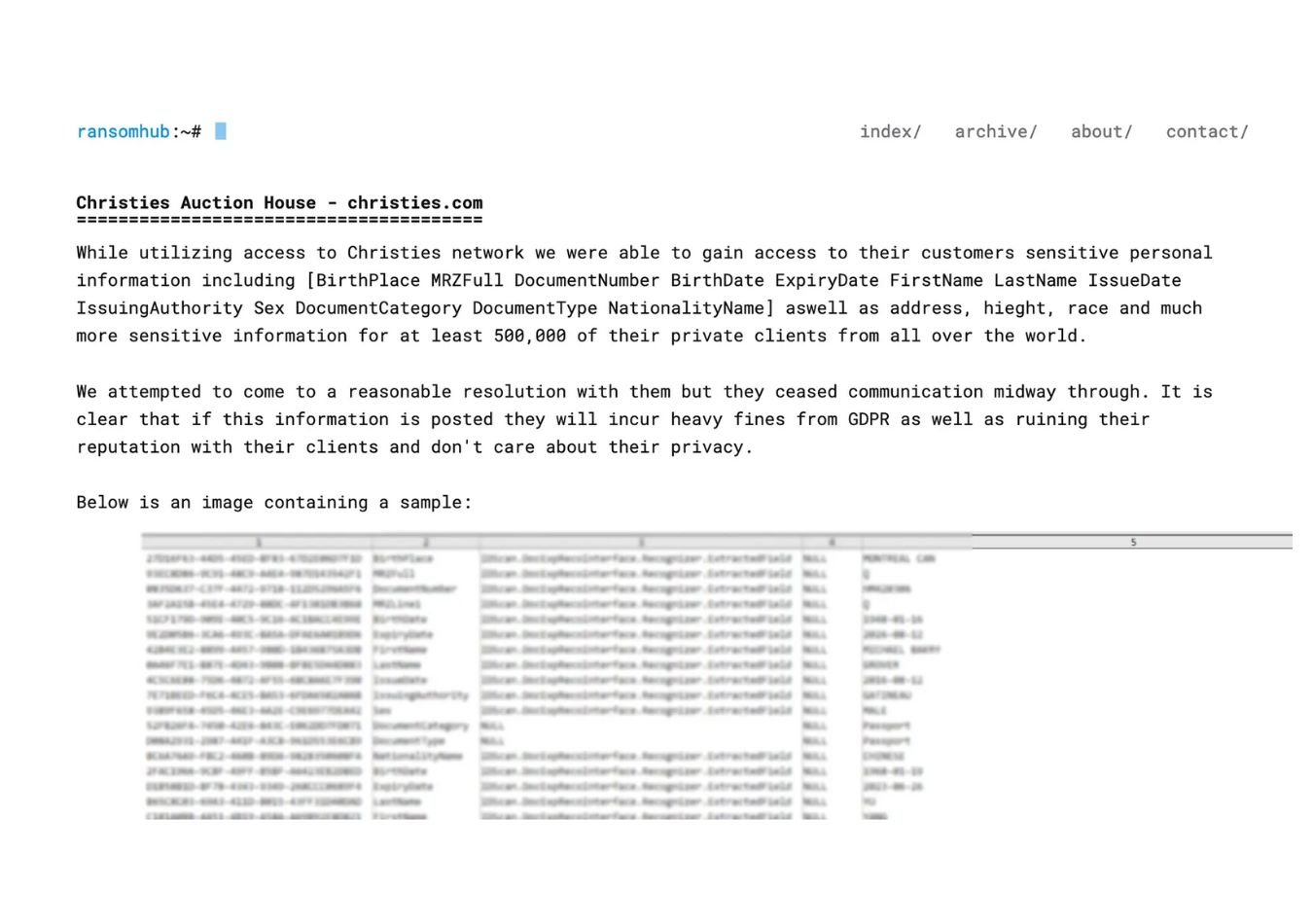
RansomHub claimed to have exfiltrated 2GB of data from Christie’s, impacting over 500,000 clients worldwide. The auction house, which handles billions of dollars worth of art and luxury goods each year, temporarily took down its main website on May 9 in response to the attack.
During the outage, Christie’s CEO Guillaume Cerutti shared a statement on LinkedIn, confirming that the company was addressing the incident with the help of cybersecurity experts. While one auction was briefly postponed, all other auctions continued as scheduled. Following RansomHub’s claims, Cerutti later updated that a limited amount of personal data was stolen after an unauthorized third party accessed Christie’s network.
Change Healthcare
On February 22, UnitedHealth, the parent company of Change Healthcare, disclosed a major cybersecurity incident. It was initially suspected to be a nation-state attack, but it was later confirmed that the BlackCat ransomware gang was responsible. The attack severely disrupted Change Healthcare's operations, taking down many systems and impacting the ability of pharmacies to fulfil orders for patients paying with insurance.
Although BlackCat initially took credit, Change Healthcare’s troubles didn’t stop there. In April, RansomHub, another ransomware group, began leaking sensitive medical and financial information from the company, threatening to publish the data unless ransoms were paid by insurance providers.
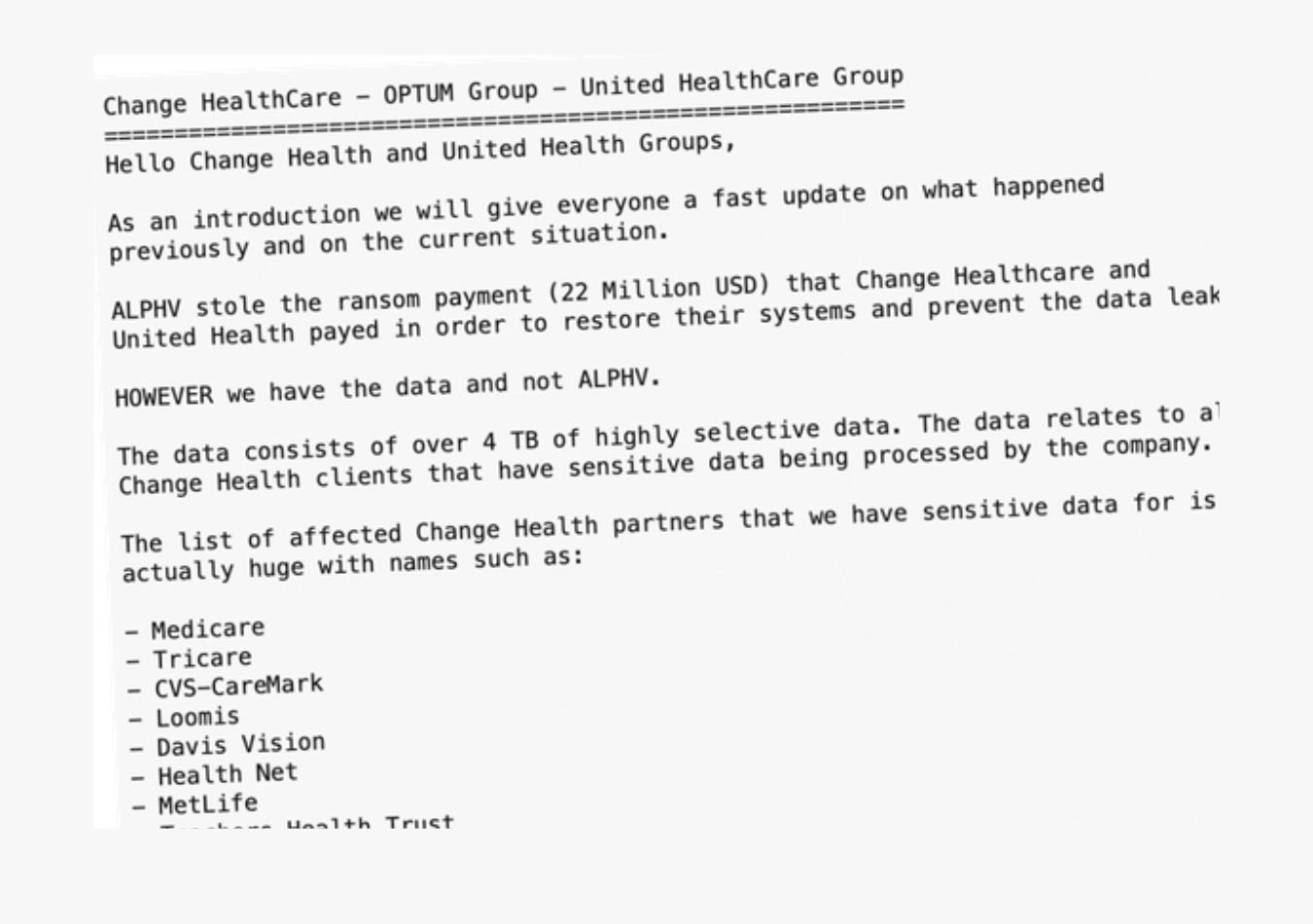
The attack on Change Healthcare is considered one of the most devastating cyberattacks in history. As one of the largest health payment processing companies globally, Change Healthcare processes over 15 billion medical claims annually, covering nearly 40% of all claims in the U.S. The attackers exploited compromised credentials on Citrix remote-access software that lacked multi-factor authentication. After gaining access, they moved laterally through the network, exfiltrating 6TB of sensitive data before deploying ransomware nine days later. The attack resulted in a $872 million financial impact, causing months of disruption and congressional testimonies.
Despite Change Healthcare paying $22 million in ransom to BlackCat, the payment was reportedly not shared with key affiliates, including Notchy. Notchy and several other former ALPHV affiliates then joined RansomHub, which has grown rapidly since. RansomHub began leaking Change Healthcare files on April 15, extorting the company a second time and claiming the initial payment went to the wrong recipients.
RansomHub’s Attacks on US Counties: Robeson and Jefferson County
In April 2024, RansomHub claimed responsibility for cyberattacks on several US county government offices, further extending its reach into local government organisations. One of the victims was Robeson County, a government entity in North Carolina. RansomHub successfully compromised systems, disrupting critical services in the county for days.
In another incident, Jefferson County Clerk’s Office in Kentucky experienced a nearly four-day-long system outage due to a RansomHub attack. The clerk’s office was forced to halt its operations, preventing the public from accessing essential services such as property deeds and marriage licenses. In response, the office posted a photo of the ransom note online, which contained explicit instructions from the RansomHub gang. The note urged the office to pay the ransom and warned against involving third-party specialists to recover their systems.
These attacks are a part of RansomHub's growing pattern of targeting local government offices, disrupting essential services, and demanding ransom payments. The attacks highlight the vulnerability of government agencies to ransomware threats, particularly in smaller counties with limited cybersecurity resources. Many local governments struggle to fend off sophisticated attacks due to outdated systems, insufficient budgets for cybersecurity defences, and a lack of comprehensive incident response plans.
How do you Defend Yourself against a RansomHub Attack?
RansomHub ransomware attacks are growing in sophistication, and defending against them requires a robust strategy. Cybersecurity experts have observed affiliates disguising the ransomware executable with innocuous filenames like "Windows.exe" on users' desktops or downloads to avoid detection. Attackers often clear Windows and Linux system logs to obstruct incident response and use Windows Management Instrumentation (WMI) to disable antivirus solutions. In some instances, RansomHub-specific tools are deployed to disable endpoint detection and response (EDR) systems, increasing the challenge of mitigating the attack.
Key Steps to Defend Against RansomHub:
- Isolate Compromised Systems: Quarantine or take potentially infected hosts offline immediately to prevent the spread of ransomware.
- Reimage and Rebuild: Reimage compromised hosts and provision new account credentials to ensure integrity.
- Collect and Analyse Evidence: Gather artefacts such as unusual services, processes, or network connections to understand the breach.
- Backup and Recovery Plans: Ensure multiple copies of sensitive data are kept in secure, segmented, and physically separate locations to ensure recovery.
Additional Preventive Measures:
- Implement National Institute for Standards and Technology (NIST) standards for password management and enforce phishing-resistant multi-factor authentication (MFA) for administrative accounts.
- Keep operating systems, software, and firmware up to date to close off vulnerabilities.
- Network Segmentation: Segment networks to limit ransomware movement and use network monitoring tools to detect suspicious activity early.
- Disable unnecessary command-line and scripting permissions to reduce exploitation risks.
- Maintain offline encrypted backups and test backup restoration processes regularly to minimise downtime during an attack.
Embedding security into product architecture, enforcing MFA for privileged users, and implementing strong endpoint detection measures are critical in reducing exposure to RansomHub and similar ransomware threats.




Comments ( 0 )