LockBit is a notorious Russia-based ransomware group first identified in 2019. The group operates under a Ransomware-as-a-Service (RaaS) model, licensing its sophisticated ransomware software to affiliated cybercriminals in exchange for a percentage of the ransom payments. This structure allows LockBit to quickly scale its attacks by leveraging affiliates around the world.
LockBit is widely known for using double extortion tactics. The group's cybercriminals exfiltrate vast amounts of sensitive data before encrypting the victim's systems. They then demand a ransom not only for the decryption key but also to prevent the leaked data from being published online. LockBit ransomware was the most widely deployed variant globally in 2023 and will continue to dominate the ransomware landscape in 2024.

In this article, we explore the evolution of LockBit, how it has become one of the most dangerous ransomware gangs, and the key defence strategies companies can implement to protect against its attacks. Additionally, we will cover LockBit’s tactics, its impact on global organisations, and the best practices for ransomware prevention.
Who is LockBit?
Since its inception, LockBit has continuously evolved its RaaS model, becoming a highly sophisticated and dangerous threat to organizations worldwide. The group is known for its double extortion tactics, where they not only encrypt victims' data but also threaten to leak it if the ransom is not paid.
The Evolution of LockBit:
- LockBit 1.0: The initial version was designed to target organizations with weak cybersecurity defences, spreading quickly through phishing emails and vulnerability exploitation.
- LockBit 2.0: Released in 2021, this version introduced new features such as automated system scanning, which allowed the ransomware to quickly identify and lock down critical systems. This upgrade made LockBit even more efficient in carrying out attacks.
- LockBit 3.0: Launched in June 2022, this is the current and most advanced version of the ransomware. LockBit 3.0 introduced a bug bounty programme, where the group offered rewards for vulnerabilities discovered in their software or attack strategies. This unique approach helped them refine their ransomware even further, making it harder for organizations to detect and defend against their attacks.
LockBit 3.0
Launched in late June 2022, LockBit 3.0 represents a significant advancement in ransomware technology, focusing on faster encryption speeds to bypass security detections. According to cybersecurity expert Arda Buyukkaya, who analysed an early sample of the malware, LockBit 3.0 incorporates a variety of advanced techniques, including anti-analysis mechanisms, password-only execution, and enhanced command-line augmentation. These features make it harder for traditional security tools to detect and prevent ransomware attacks.
A key innovation in LockBit 3.0 is the introduction of the first-ever ransomware bug bounty program. The LockBit group is actively soliciting cybersecurity researchers and users to report bugs and vulnerabilities in exchange for financial rewards. These bounties, starting at $1,000 USD, incentivise individuals to reveal potential weaknesses, not just in systems that LockBit could exploit but also within the LockBit malware itself. This tactic allows LockBit to continuously evolve and refine its operations, making it an even more formidable threat.
The categories of interest in LockBit’s bug bounty program include:
- Locker bugs: Issues related to the encryption process.
- Tor network vulnerabilities: Weaknesses in the Tor network, which LockBit uses for communication and extortion.
- Tox messenger vulnerabilities: Exploits within the Tox encrypted messaging system, which LockBit uses to communicate with victims.
- Website bugs: Flaws on LockBit’s own infrastructure, including their data leak site.
In addition to these features, LockBit 3.0 has improved payload delivery techniques, allowing it to spread more quickly across compromised networks. Its password-protected payloads make it difficult for security solutions to scan or block the ransomware effectively. The bug bounty programme is a unique and bold move that demonstrates how cybercriminal groups are increasingly adopting practices from the legitimate tech world to improve their malware and increase their operational success.
Key Features of LockBit Ransomware:

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
- Double Extortion: Victims face not only data encryption but also the threat of public data leaks if they refuse to pay.
- Fast Encryption: LockBit’s encryption algorithms are designed for speed, allowing it to lock up large networks in a short amount of time.
- Advanced Evasion Techniques: The ransomware uses techniques to avoid detection by security software, including disabling endpoint detection and response (EDR) systems.
- Customisable Ransom Demands: LockBit affiliates can customize the ransom note, demands, and tactics, making each attack unique.
LockBit’s Website
LockBit operates a dark web portal hosted on the Onion Router (TOR) network, which serves as a central hub for their operations. This TOR website is used to recruit skilled hackers and cybercriminals, and it’s also where the group publicly releases sensitive data stolen from victims who refuse to pay the ransom.
The LockBit website is a core part of the group’s double-extortion strategy. Victims who pay the ransom are promised the safe return of their data, while those who refuse are threatened with public exposure of sensitive information. LockBit assures that data will be "deleted" for those who comply, claiming to uphold this as part of their “business model.” However, paying the ransom does not guarantee the data won’t be sold or leaked later, as trust in cybercriminals is inherently risky.
LockBit’s dark web portal is continuously updated with new victims, often from sectors such as healthcare, finance, and manufacturing. The group has built a reputation for efficiency, offering RaaS to affiliates, which enables rapid dissemination of their attacks across a wide range of targets.
Where is LockBit From?
LockBit has positioned itself as the "Robin Hood" of ransomware groups, claiming to follow an ethical approach to their cyberattacks. While the FBI has not directly attributed LockBit to Russia, there are strong indications that the group has Russian origins. This conclusion comes from an analysis of LockBit’s public communications, which often express anti-Western political views. Additionally, LockBit operates with global affiliates, extending its reach worldwide.
When Case Systems Become Weapons
Examines how a case-management platform became alleged intelligence infrastructure, blurring lines between legal IT and covert operations.

LockBit claims to avoid targeting sectors like healthcare, education, charitable organisations, and service industries, promoting itself as a responsible player in the ransomware world. However, the reality of their attacks contradicts these claims, as the group has been linked to several high-profile ransomware incidents affecting various industries.
Key Figures Behind LockBit
One of the most prominent figures associated with LockBit is Ivan Gennadievich Kondratiev, a Russian national based in Novomoskovsk, Russia. Kondratiev, who is known in the cybercriminal underground as Bassterlord and Fisheye, is the leader of a LockBit affiliate group called the National Hazard Society.
His cybercriminal activities extend beyond LockBit, as he also has connections to other major ransomware groups like REvil, RansomEXX, and Avaddon. Kondratiev has been actively involved in orchestrating LockBit ransomware attacks and is considered a significant player in the group’s operations.
Another key affiliate is Artur Sungatov, also a Russian national, who has played a critical role in LockBit’s cyberattacks. Both Kondratiev and Sungatov have been designated by the U.S. Office of Foreign Assets Control (OFAC) under an Executive Order, highlighting their importance in LockBit’s global ransomware campaigns.
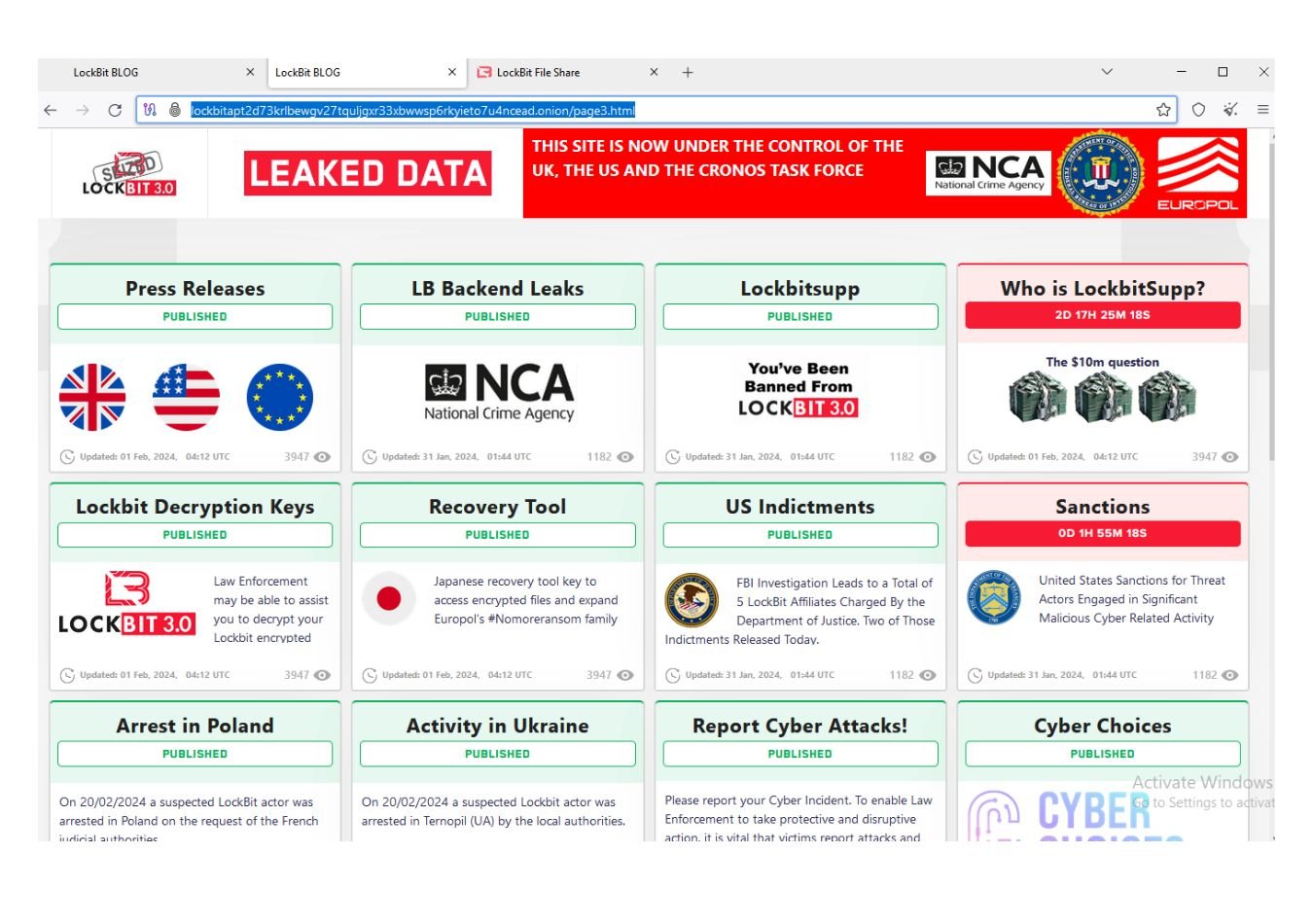
LockBit Leadership Unmasked: Dmitry Khoroshev Sanctioned by UK, US, and Australia
In an international effort led by the UK's National Crime Agency (NCA), the leader of LockBit has been unmasked and sanctioned. Dmitry Khoroshev, a Russian national and key figure behind the notorious LockBit ransomware gang, faces sanctions from the UK, US, and Australia in a coordinated disruption campaign.

Khoroshev, also known as LockBitSupp, served as the administrator and developer of LockBit, a ransomware group responsible for thousands of attacks globally. These attacks targeted sectors ranging from healthcare to critical infrastructure, demanding multimillion-dollar ransoms in exchange for decryption keys. Once considered the most harmful ransomware syndicate, LockBit's operations have been severely disrupted as authorities close in on its leadership.

Data Trust Erosion in Niche Apps
What a delayed breach disclosure, insecure password practices, and account removal reveal about security risk in smaller networks.
Today, the UK Foreign, Commonwealth & Development Office (FCDO), alongside the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and Australia’s Department of Foreign Affairs, announced a series of sanctions against Khoroshev. These measures include asset freezes and travel bans, effectively crippling his ability to operate internationally.
LockBit Attacks
With over 7,000 recorded attacks between June 2022 and February 2024, LockBit’s impact on global cybersecurity is staggering. The group targets organizations across various sectors, primarily in the United States, the United Kingdom, France, Germany, and China. While the average global ransomware payment is nearly $1 million, LockBit victims pay an average ransom of $85,000, indicating that the group tends to focus on small to medium-sized businesses.
With over 7,000 recorded attacks between June 2022 and February 2024, LockBit’s impact on global cybersecurity is staggering. The group targets organizations across various sectors, primarily in the United States, the United Kingdom, France, Germany, and China. While the average global ransomware payment is nearly $1 million, LockBit victims pay an average ransom of $85,000, indicating that the group tends to focus on small to medium-sized businesses.
How LockBit Operates
LockBit gains initial access to target networks using a combination of methods, including:
- Purchased access from criminal marketplaces
- Exploitation of unpatched vulnerabilities
- Insider access
- Zero-day exploits
Once inside a system, LockBit affiliates move into the second stage of their attack, collecting network information and achieving their primary goals, such as stealing and encrypting sensitive data. LockBit affiliates often use double extortion tactics: first, demanding payment for the return of encrypted files, and then threatening to leak the stolen data publicly if a second ransom isn’t paid.
Similarly, LockBit affiliates are known for using a range of legitimate freeware and open-source tools to carry out their attacks. These tools, which are intended for legal use, are repurposed for malicious activities, including:
- Network reconnaissance
- Credential dumping
- Remote access and tunnelling
- File exfiltration
Commonly observed tools and tactics include:
When Breach Containment Fails
What a 560m-record heist exposes about outdated perimeter defenses and why boards must pivot to an assume-breach, limit-and-contain security model.

- PowerShell scripts for system discovery and reconnaissance
- Batch scripts for credential hunting and privilege escalation
- Metasploit and Cobalt Strike, professional -testing tools repurposed for cybercrime
- Credential dumping and data extraction tools to steal sensitive information
LockBit's Alleged Breach of the Federal Reserve
In a shocking claim, the notorious LockBit announced they had successfully breached the U.S. Federal Reserve, the central banking system of the United States. On their dark web leak site, LockBit threatened to release over 30 terabytes of sensitive banking information, including personal data of millions of American citizens, if a ransom wasn't paid by June 25, 2024.
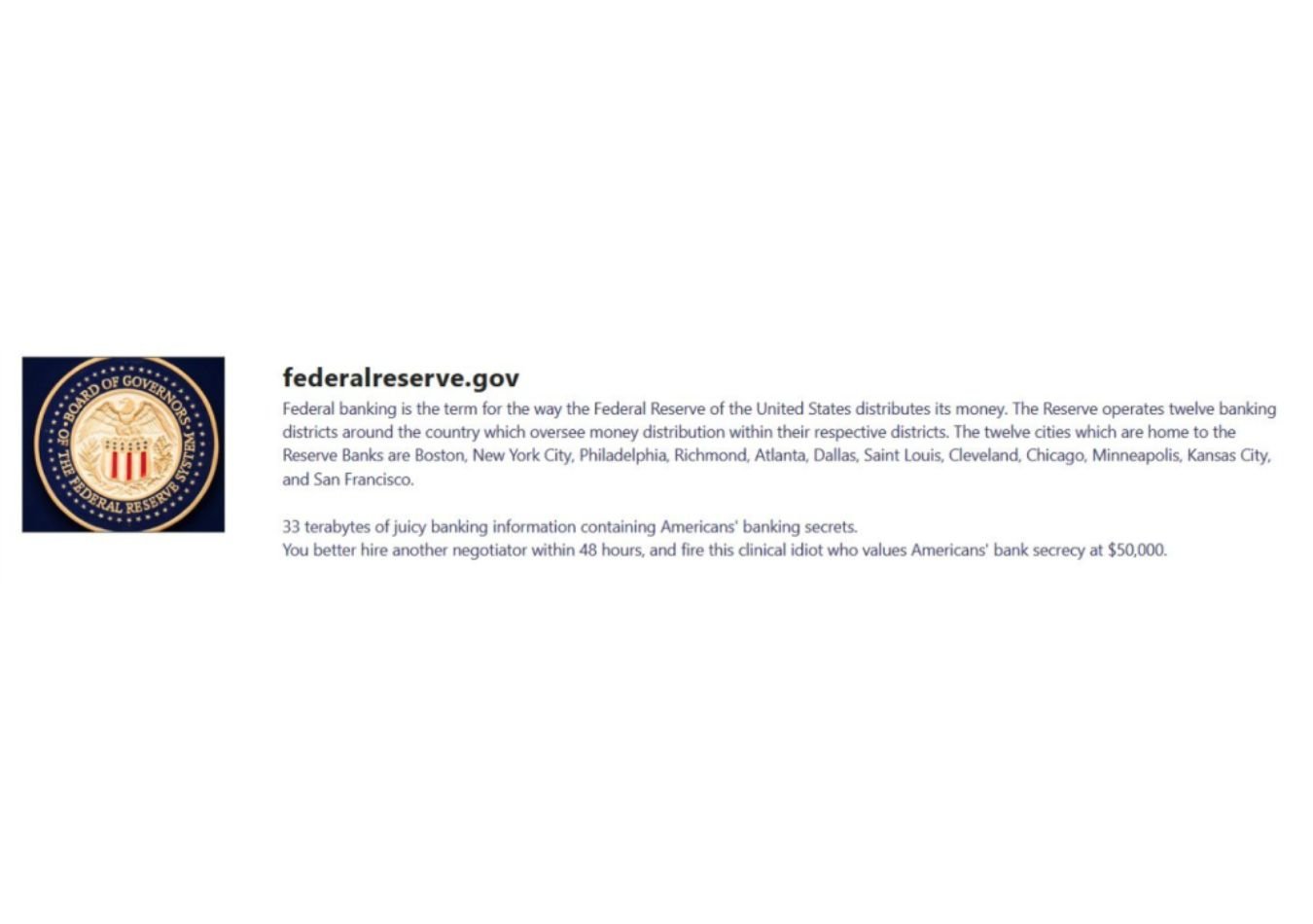
This announcement sent shockwaves through the financial world, raising concerns about the potential exposure of vast amounts of confidential data. Many feared the attack could destabilise financial markets, disrupt the banking system, and cause widespread panic.
However, when the deadline passed and the data was released, analysts discovered that the compromised information did not belong to the Federal Reserve. Instead, it was traced back to Evolve Bank & Trust, a financial organisation.
While still significant, this revelation provided some relief as the Federal Reserve’s critical infrastructure remained secure. Nonetheless, the breach of Evolve Bank & Trust exposed highly sensitive financial records, which could still have long-term consequences for its clients and the wider banking sector.
ICBC Attack: Another LockBit Victim
In another major incident, investigations revealed that LockBit was responsible for a ransomware attack on ICBC (Industrial and Commercial Bank of China)'s U.S. broker-dealer operations on November 9, 2023. This attack severely disrupted the settlement of over $9 billion worth of treasury-backed securities, a crucial component of the financial system.
The ransomware attack caused a complete blackout of ICBC’s computer systems, including email and communication services, making it impossible for the bank to process trades or access funds backing the securities. This led to major settlement failures, with securities delivered for settlement without any corresponding funds. The disruption sent shockwaves through the U.S. financial markets, highlighting the devastating impact ransomware can have on global banking systems.
How to Protect Against LockBit Ransomware?
Protecting your organisation against LockBit ransomware requires a comprehensive approach that aligns with the MITRE ATT&CK framework. This framework helps identify tactics, techniques, and procedures used by attackers, enabling organisations to implement effective mitigations. Below, we've outlined key strategies categorised by MITRE ATT&CK tactics, ensuring that organisations can address vulnerabilities across the incident lifecycle.
Initial Access Mitigations
- Implement Sandbox Browsers: Use sandboxed browsing environments to isolate web activity and reduce the risk of malicious software being executed on the network.
- Require Strong Password Policies: Enforce the use of complex passwords for all accounts, particularly those with administrative access, to minimize the risk of unauthorized access.
- Email Filtering: Install email gateway filters to detect and block emails containing known malicious indicators or suspicious attachments.
- Web Application Firewall: Deploy a web application firewall (WAF) at the email gateway to monitor and filter HTTP traffic between your web applications and the internet.
- Network Segmentation: Segment networks to limit lateral movement and contain potential breaches, making it harder for attackers to access critical systems.
- Adhere to the Least Privilege Principle: Ensure users have only the access necessary for their job functions, thereby reducing potential attack vectors.
- Audit Administrative Accounts: Regularly review and manage audit user accounts with administrative privileges to ensure proper access controls.
- Time-Based Access Controls: Implement time-based access for accounts with administrative privileges, allowing access only during specific periods when needed.
Execution Mitigations
- Develop Comprehensive Network Diagrams: Maintain updated network diagrams to visualise connections and identify vulnerable points within your infrastructure.
- Control Network Connections: Restrict and manage network connections to ensure that only trusted devices can communicate within your environment.
- Enhanced PowerShell Logging: Enable detailed logging for PowerShell to monitor script executions that may indicate malicious activity.
- User Account Control (UAC) Configuration: Configure the Windows registry to require UAC approval for any PsExec operations, adding an additional layer of security.
Privilege Escalation Mitigations
- Disable Unnecessary Command-Line and Scripting Activities: Limit the use of command-line tools and scripts to reduce the risk of privilege escalation.
- Enable Credential Guard: Utilize Windows Credential Guard to protect against credential theft and unauthorized access.
- Local Administration Password Solution (LAPS): Implement LAPS to manage local account passwords, ensuring they are unique and regularly changed.
Defence Evasion Mitigations
- Local Security Policies: Apply local security policies to control which applications can execute on your systems.
- Application Allowlisting: Establish an application allowlist to ensure only approved applications can run, minimising the risk of malware execution.
Credential Access Mitigations
- Restrict NTLM Usage: Limit the use of NTLM authentication to mitigate the risk of credential theft.
Discovery Mitigations
- Close Unused Ports: Disable any unnecessary open ports to reduce the attack surface and limit potential entry points for attackers.
Continuous Testing and Validation
In addition to implementing these mitigations, organisations should exercise, test, and validate their security programs against the threat behaviours outlined in the MITRE ATT&CK for Enterprise framework. This process involves evaluating existing security controls to determine how well they perform against specific ATT&CK techniques.
To get started, follow these steps:
- Select an ATT&CK Technique: Choose a technique described in this advisory to focus your testing.
- Align Security Technologies: Map your security technologies to the selected ATT&CK technique.
- Conduct Performance Testing: Evaluate how your technologies respond to the chosen technique in a controlled environment.
- Analyse Performance Data: Review the results to identify any gaps in detection or prevention capabilities.
- Repeat for All Technologies: Continue this process for all security technologies to build a comprehensive set of performance data.
- Tune Your Security Programme: Adjust your security program, including policies, processes, and technologies, based on the insights gained from testing.
Organisations are strongly encouraged to continually test their security measures at scale, in a production environment, to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory. Regular testing not only helps improve resilience against LockBit but also fortifies defences against a wide array of cyber threats.
By implementing these strategies, businesses can significantly enhance their security posture, making it harder for ransomware groups like LockBit to succeed in their attacks. Emphasising a proactive approach to cybersecurity will help organisations safeguard their assets, data, and reputation in an increasingly dangerous digital landscape.







Comments ( 0 )