The Industrial and Commercial Bank of China (ICBC) has become the latest large corporation to fall victim to a cyber attack this week following a string of cyber attacks by the ransomware gang LockBit.
The attack, which hit the bank’s US financial services arm yesterday, left brokers and traders scrambling to assess the extent of the impact and clients unable clients to reroute transactions throughout the evening.
China's foreign ministry said on Friday the lender is doing everything it can to minimise risk impact and losses after the attack.
“ICBC has been closely monitoring the matter and has done its best in emergency response and supervisory communication,” China's foreign ministry spokesperson Wang Wenbin said in a statement.

He added that ICBC had acted swiftly to respond to the breach and that businesses remained normal at ICBC's head office and other branches and subsidiaries across the globe.
‘Now we know it’s ransomware, it’s much worse’
The Security research group vx-underground was the first to share news of the disruption – posting on X that the hack was impacting “all of ICBC’s clearing customers.”
“It was speculated that it was ransomware, however, it was not confirmed, and it was just rumors,” vx-underground wrote in a subsequent X post. “If it was a technical issue, it is bad But now that we know it is ransomware, it is much worse.”
The big whoopsie has hit.
— vx-underground (@vxunderground) November 9, 2023
Earlier this morning nerds began informing us that equity traders were unable to place trades (or clear previous ones) through ICBC (Industrial and Commercial Bank of China).
An emergency notice was sent out stating:
"ICBC is currently unable to… https://t.co/m1HK0NueKR
ICBC is China’s largest commercial lender, with assets exceeding $6 trillion. The bank employs nearly 435,000 people globally, and its majority shareholder is the Chinese government.
Martin Mackay, CRO at Versa Networks, said large corporations are a big target for ransomware gangs like LockBit due to the impact they can have on financial institutions.
“The finance sector is an attractive target for ransomware attacks because of the sheer volume of critical services managed by financial institutions. Ransomware actors know that by hitting one part of the financial supply chain, they could plunge the whole financial system into chaos,” commented Mr Mackay.

When Hackers Defend Business
How elite attackers-turned-defenders expose systemic weaknesses before criminal gangs can, reshaping modern cybersecurity strategy.
“Whilst this particular attack hasn’t impaired the market’s overall functioning, some clients have been forced to reroute trades. The financial sector works 24/7 and is dependent on network connectivity, therefore downtime in services or operations can cause significant damage financially and reputationally for the bank.”
Raghu Nandakumara, Head of Industry Solutions at Illumio, agrees. He told EM360tech that the financial sector needs to do more to protect itself against the rising ransomware threat.
“The finance industry must prioritise both proactive and reactive measures to mitigate the impact of ever-increasing ransomware attacks. It's also why we are seeing legislation like DORA in Europe that is focused on strengthening cyber resilience," said Mr Nandakumara.
He added that the fact that ICBC was able to resume operations swiftly after the attack, it should bring no comfort to the financial institution as a whole.
“Although ICBC's swift response to isolate and contain the attack is commendable, the broader economic disruption is concerning – any attack that can disrupt trade and the wider economy gives attackers more leverage and increases the likelihood of ransomware being paid.
“Yes, cyber spending in the sector is high, but if attacks of this scale are still occurring, I would question whether the budget is being spent in the right places.”
Inside Breach Recovery Costs
Breaks down how outages, remediation, compliance work, and security uplift turn a single breach into a multi-year infrastructure expense.

LockBit strikes again
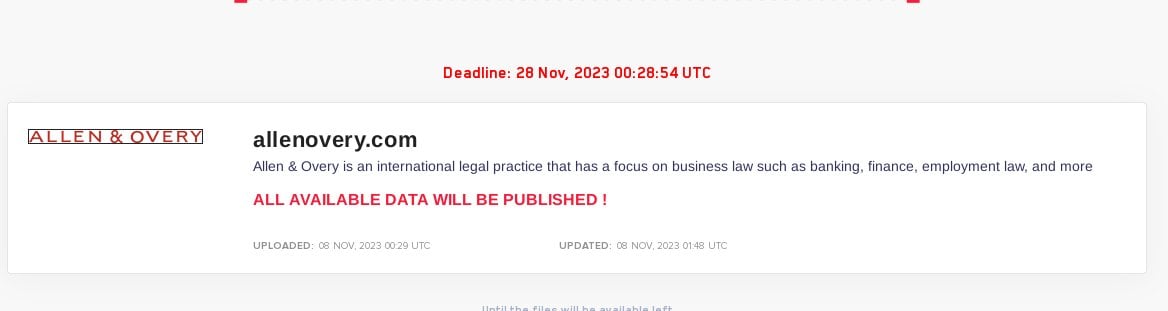
The attack on ICPC less than 24 hours following another LockBit ransomware attack on the London-headquartered legal Giant Allen & Overy.
In that attack, the Russia-linked cyber gang threatened to publish confidential A&O data if the ‘magic circle’ law firm failed to meet its ransom demands.
LockBit has been racking up victims in recent months, with large corporations from all industries falling victim to their cyber rampage. But Roger Grimes, Data-Driven Defense Evangelist at KnowBe4, said he was surprised the hacktivist group went through with their attack on ICPC.
“I'm surprised the ransomware gang went ahead with the exploitation. Perhaps they didn't realize what they had and what they would be interrupting,” Mr Grimes said.
"Incidents like this, where there's "real" money involved, often don't work out long-term for the ransomware gang involved. The authorities not only get involved but there's big pressure for people to be arrested and the gang shut down."
“But the Chinese certainly have their own great hackers they can use as an offensive resource and the US authorities are pretty good at identifying culprits and dishing out pain when the money involved is enough. This is one of those cases,” Mr Grimes added.
The Cyber Security & Cloud Expo is the leading event for Zero Trust, Threat Detection & Response, Training, Talent & Culture, Identity & Access Management, Application Security, and Data Security.
Taking place at the Olympia in London from 30th November - 1st December, the event brings together leading cybersecurity experts and discover key strategies for making your digital efforts a success. Explore the critical technologies and approaches needed to improve customer engagement and drive your organisation’s digital culture.
Join thousands of Cyber Security & Cloud industry experts to discover the latest cyber security & cloud solutions and connect with influential thought leaders during the two-day event.

Ransomware in the Classroom
The Blackpool attack underscores education’s status as a prime target and the need for state-backed investment to protect student data and services.







Comments ( 0 )