With the peak season of Black Friday looming, phishing attempts aimed at e-commerce shoppers are on the rise, especially in Europe and the USA.
A Chinese threat actor, going by the alias SilkSpecter, was allegedly found to be behind a phishing campaign targeting e-commerce markets in the West.
At the beginning of October this year, EclecticIQ analysts (a cybersecurity platform) discovered that SilkSpecter phishing leveraged the heightened online shopping activity in November, the peak season for Black Friday discounts.
The threat actor used fake discounted products as phishing lures to deceive victims into providing their sensitive information according to EclecticIQ’s official statement
The campaign aimed to steal sensitive information like Cardholder Data (CHD), Sensitive Authentication Data (SAD), and Personally Identifiable Information (PII).
Arda Buyukkaya, an EclecticIQ threat researcher who discovered the campaign, told BleepingComputer that, as of the publishing of their report, SilkSpecter operates 4,695 fraudulent domains.
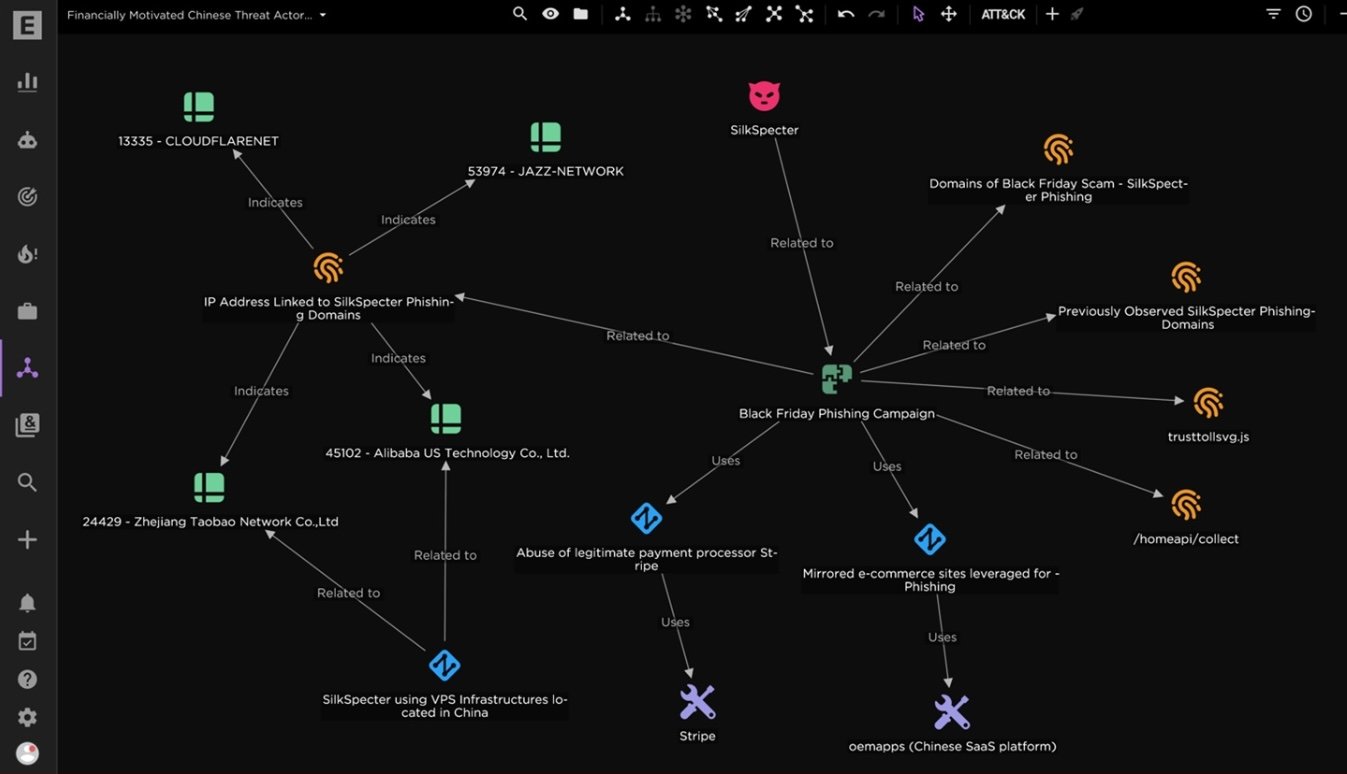
SilkSpecter essentially developed fake shopping websites mimicking legitimate online shopping brands.
North Face, Lidl, Bath & Body Works, L.L. Bean, Wayfair, Makita, IKEA, and Gardena among many others were some of the prominent brands targeted.

Luring Shoppers Via Black Friday Discounts
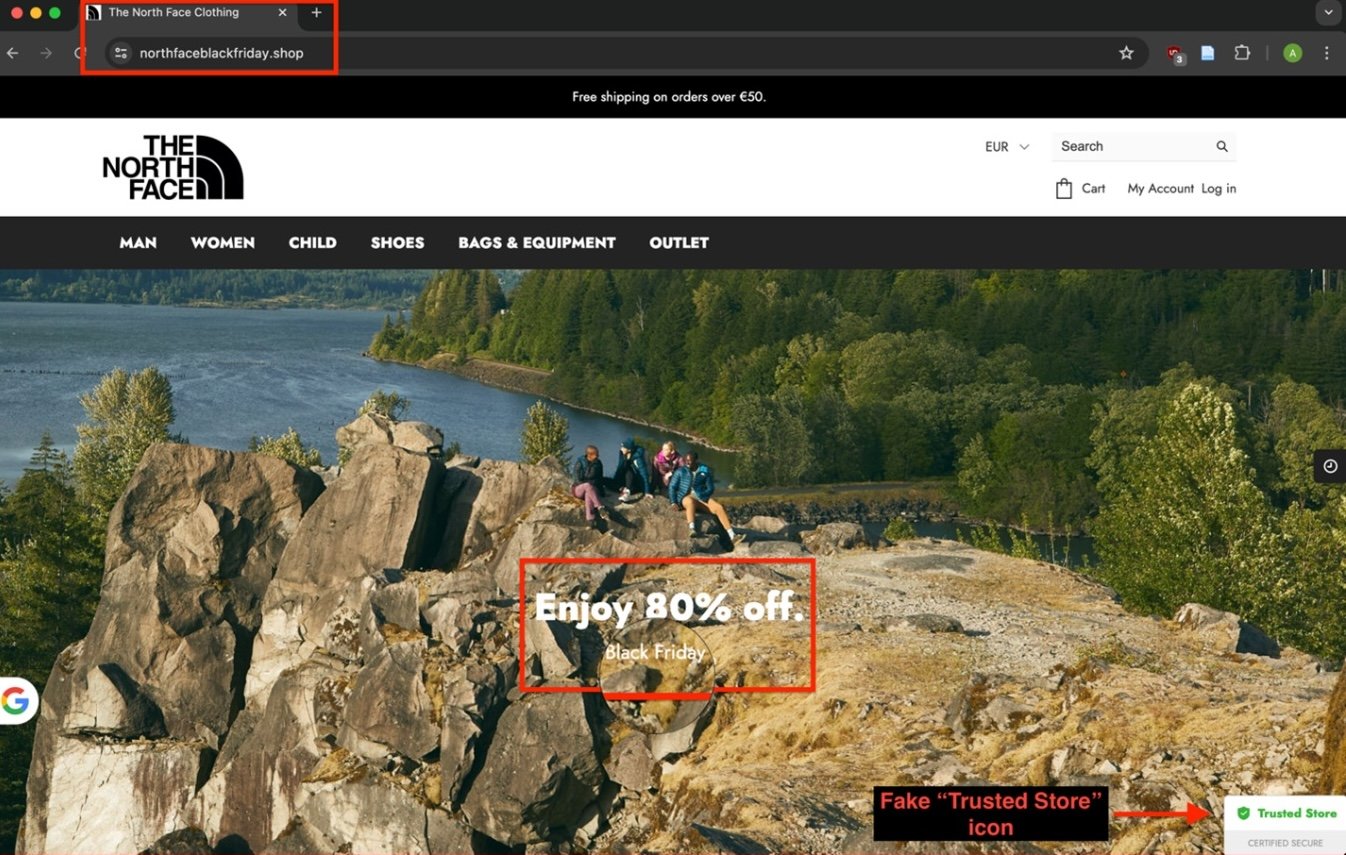
These fake websites were designed to lure unsuspecting shoppers into providing their personal and financial information, such as credit card numbers and addresses.
According to the report, the cybercriminal used super obvious domain names, like including "Black Friday" right in the URL, to trick people into thinking they were getting great deals.
SilkSpecter created a ‘Black Friday’ discount string to lure digital consumers to shop from these fake domains.
The EclecticIQ report emphasised that SkillSpecter targeted victims’ Cardholder Data (CHD) by leveraging the legitimate payment processor Stripe.
“This tactic allowed genuine transactions to be completed while covertly exfiltrating sensitive CHD to a server controlled by the attackers,” the statement added.
The threat actor used Google Translate to make the phishing site credible and sophisticated. This component adjusted the fake website’s language based on each victim’s IP location, to appear more convincing to an international audience.
Report Alleges Chinese Association to Phishing Campaign
This is not SkillSpecter’s first phishing campaign. The cyber security platform has spotted similar campaigns by the same threat actor before November 2024. They seemed to be associated with a Chinese Software as a Service (SaaS) platform called oemapps.
EclecticIQ analysts believe that the Chinese SaaS, oemapps very likely enable SilkSpecter to quickly create convincing fake e-commerce sites targeting unsuspecting users.
These phishing domains predominantly use the .top, .shop, .store, and .vip top-level domains (TLDs), often typosquatting legitimate e-commerce organisations' domain names to deceive victims.
During investigations, the cyber security platform observed a pattern in these phishing attempts. Each phishing page seems to have included "trusttollsvg," a deceptive icon designed to give the appearance of a trusted site. It also had a "/homeapi/collect" endpoint that informed attackers whenever a victim clicked or opened the URL - tracking the phishing campaign’s success in real-time.
The discovery helped EclecticIQ uncover many other discount-themed phishing domains linked to SilkSpecter’s activity network.
The discounts often advertised an “80% off” discount offer presenting as an exclusive deal to online shoppers.
When victims followed the links to such Black Friday discount strings, the hacker placed website trackers such as OpenReplay, TikTok Pixel and Meta Pixel.
These trackers gathered comprehensive information including each victim’s activity log details and observed the effectiveness of the attacks.
Phishing Captured Browser Metadata
The phishing kit also captured key browser metadata, such as IP addresses, geolocation, browser type, and OS details, reported EclecticIQ. Using this information, the page is dynamically translated into the victim's language through Google Translate APIs, further increasing its authenticity.
The threat actors tricked victims into entering their payment and personal information on fake online stores. These fake stores used a legitimate payment processor, Stripe, to make the transactions appear real.
Once the victims paid, their sensitive data was stolen and sent to the hackers. The hackers could then use this information to carry out more fraudulent activities such as identity theft or phone scams.
“By impersonating trusted entities, such as financial institutions or well-known e-commerce platforms, SilkSpecter could very likely circumvent security barriers, gain unauthorised access to victim's accounts, and initiate fraudulent transactions,” says EclecticIQ.
EclecticIQ’s experts believe that SilkSpecter likely distributed these phishing URLs through social media accounts and search engine optimisation (SEO) poisoning, leveraging a Black Friday discount theme as social engineering bait to deceive unsuspecting online shoppers.






Comments ( 0 )