A previously undiscovered cybercrime gang called Bigpanzi has been using a DDoS botnet to infect millions of Android TV boxes with 'pandoraspear' malware.
According to a report by the Beijing-based security firm Qianxin Xlabs, the gang is in control of a large-scale botnet of at least 170,000 bots globally, which have been running daily since at least 2015 after infecting TVs and other streaming hardware via pirated apps and firmware updates.
The researchers have seen 1.3 million unique IP addresses associated with the botnet since August, suggesting that millions of devices may now be infected by the malware.
Bigpanzi infects the devices by pushing users visiting unsafe streaming sites into downloading the associated malicious app to their Android-based smart TV.

A victim would then have their device backdoored and its resources made available for use in various cybercrimes, such as DDoS attacks, hijacking other streams, and replacing other channels' content with an attacker's.
"The potential for Bigpanzi-controlled TVs and STBs to broadcast violent, terroristic, or pornographic content, or to employ increasingly convincing AI-generated videos for political propaganda, poses a threat to social order and stability," said researchers at Chinese security biz Qianxin.
"In the face of such a large and intricate network, our findings represent just the tip of the iceberg in terms of what Bigpanzi encompasses," the researchers added. "There's a vast amount of tracing and investigative work still to be undertaken.
Pandoraspear Malware
Qianxin's investigation revealed that Bigpanzi’s malware, called pandoraspear, had added 11 different Mirai-related DDoS attack vectors to its list of commands after the first few versions had comparably weaker tools in this area.
The malware was first discovered by Dr. WEB, who on September 6 shared their discoveries with the cybersecurity community to help researchers pandoraspear's spread through pirated traffic APKs.
Bigpanzi and the pandoraspear malware have been active since at least 2015. Their efforts have been mainly concentrated in São Paolo, Brazil, the city where many of the active 170,000 bots were identified at the peak of the cybercriminal campaign.
The scale of the botnet was only uncovered when two of the nine domains used for the botnet's command and control (C2) infrastructure expired, allowing the researchers to register those domains for themselves and look into what Bigpanzi was up to.
"Upon realizing that we had secured their domains, the group countered aggressively," the researchers wrote. "They bombarded our domains with DDoS attacks to force them offline and manipulated the host’s files of the infected devices.”
"This strategy redirects certain domain names to specific IP addresses, bypassing the normal DNS resolution process used to find the IP addresses of command and control domains. This greatly limits our ability to observe and track them.
Read: Biggest Cyber Attacks in History
"We didn't engage much in this confrontation, voluntarily ceased resolving, and consequently lost this perspective."
Qianxin believes the group has recently shifted its DDoS operations to a separate botnet they control, using this for more lucrative crimes such as running it as a content delivery network.
"This strategic shift underscores the adaptability and evolving nature of cybercrime syndicates like Bigpanzi," the researchers added.

Inside North Korea's Cyber Arm
Profiles Lazarus Group as a state-backed asset, linking espionage, sabotage and theft into a coherent cyber strategy boards must plan for.
The new Mirai
The researchers didn't detail the history of the pandoraspear’s DDoS activity or blame it for any high-profile attacks, but its DDoS commands are inherited from the infamous Mirai botnet.
Mirai was responsible for some of the most high-profile and devastating DDoS attacks in recent years, including the attacks on Dyn, GitHub, Reddit, and Airbnb – all falling on a single day in October 2016. It's also malware cropping up and is under active development to this day.
Like Mirai, Pandoraspear acts as a backdoor trojan, hijacking DNS settings, establishing C2 communication, and executing commands received from the C2 server.
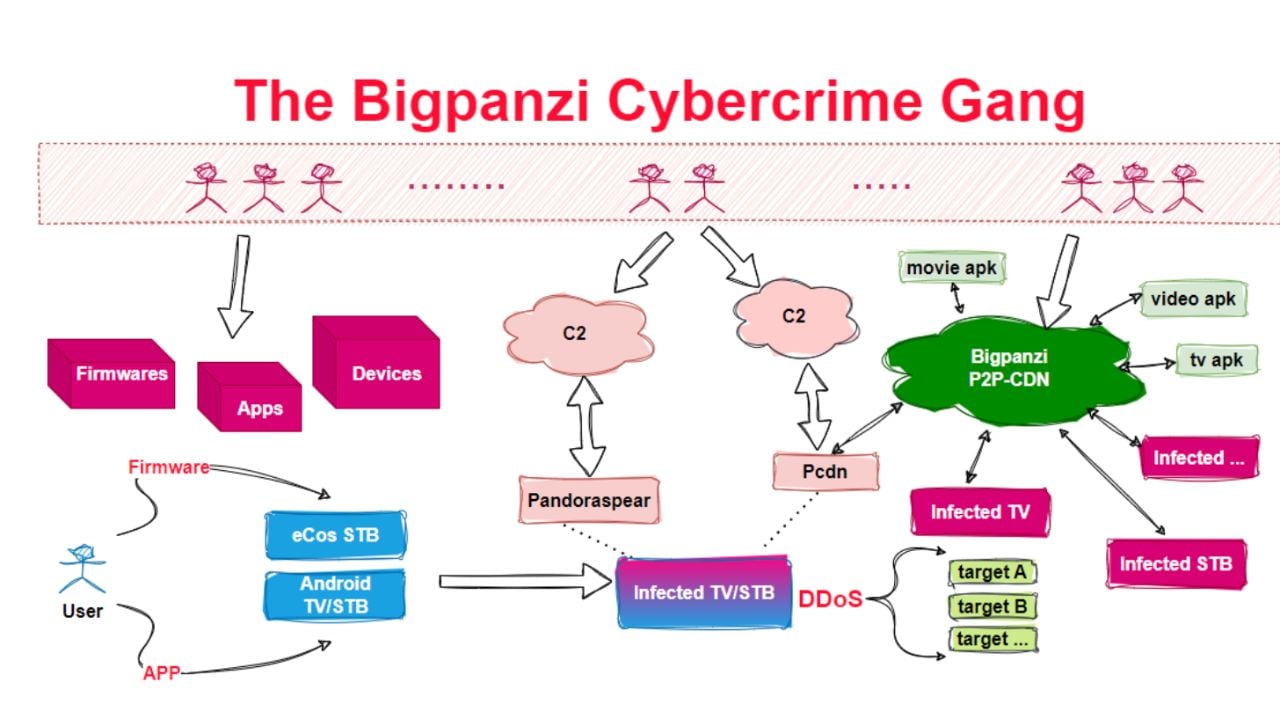
The malware also supports a variety of commands and can be used to manipulate DNS settings, initiate DDoS attacks, create reverse shells, manage its communication with the C2, and execute arbitrary OS commands.
Pandoraspear can use sophisticated techniques like modified UPX shell, dynamic linking, OLLVM compilation, and anti-debugging mechanisms to evade detection too, making it difficult to track for cybersecurity teams.
Taking place on February 6-7, CDAO UK brings some of the UK’s most senior positions within data and analytics from a cross-industry setting together under one roof for two days filled with of learning, networking and discussion around topics commonly faced by the community.
With a specific focus day included for Finance Services, as well as 50 speakers across Governance, Manufacturing, Healthcare, Transportation and much more, attendees can hear insights that will maximise the value of your data and innovate the strategies used within your organisation.
Speakers will share insights into data strategies, governance, quality and management whilst sharing real-world use cases, discussing common challenges and addressing ways to maximise business impact.
REGSITER TODAY and secure your place for the UK's most senior data and analytics event.







Comments ( 0 )