Qilin ransomware, also called Agenda ransomware, is a highly sophisticated and dangerous ransomware-as-a-service (RaaS) operation. This cybercrime group collaborates with affiliates to infiltrate organisations, encrypt critical data, and exfiltrate sensitive information. Once a system is compromised, the Qilin ransomware group demands a ransom payment to decrypt files and avoid the public release of stolen data.
The name "Qilin" comes from a mythical creature in Chinese folklore, often depicted as a hybrid of a dragon and a horned beast, similar to a unicorn. The group's use of this name reflects their elusive and powerful image in the world of cybercrime.
In this article, we’ll uncover the origins and tactics of the Qilin ransomware group, including its double extortion ransomware strategy, which combines data encryption with threats to publish stolen information. We’ll also explore notable victims and practical steps organisations can take to defend against these threats.

What is Qilin Ransomware?
Qilin ransomware first emerged on the darknet in October 2022, where it started listing its victims on its dedicated leak site. Since then, its ransomware attacks have steadily increased, targeting high-profile organisations worldwide. Some notable victims include The Big Issue, a prominent street newspaper; Yanfeng, a leading automotive parts manufacturer; and various Australian court services.
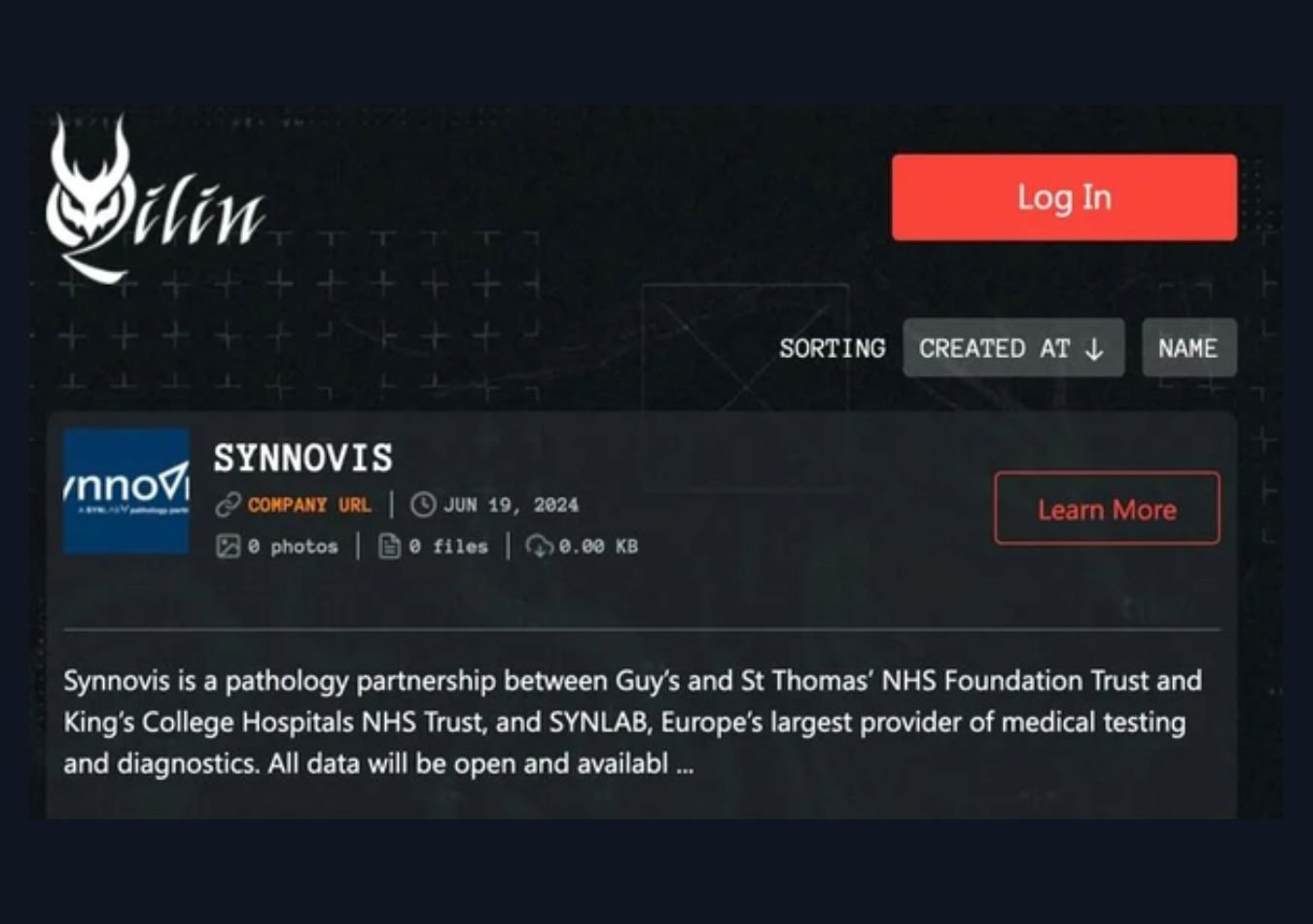
In June 2024, Qilin gained widespread attention for a ransomware attack on Synnovis, a key service provider for UK healthcare organisations and hospitals. This incident underscores Qilin’s growing threat. The group is notorious for employing double extortion tactics, where they steal sensitive data, encrypt systems, and then threaten to leak or sell the stolen information unless the ransom is paid.
How Does the Qilin Ransomware Group Attack?
The Qilin ransomware group initiates attacks by gaining initial access through compromised credentials. This cybersecurity vulnerability is a widely recognised method, making it a highly effective entry point for their ransomware operations. While this tactic isn't new, its consistent use by Qilin highlights its reliability in breaching networks.
The Qilin gang exhibits a significant dwell time of approximately 18 days between the initial access phase and further lateral movement. This prolonged delay indicates the likely involvement of an Initial Access Broker, enabling a seamless transition to the next stages of their attack. Once this waiting period ends, the group's actions intensify, targeting the domain controller through escalated privilege access.
Upon breaching the domain controller, the attackers modify the default domain policy, deploying a logon-based Group Policy Object (GPO). This carefully crafted policy executes two critical components across the network:
PowerShell Script - IPScanner.ps1
This 19-line script, stored temporarily in the SYSVOL folder, is designed to harvest saved credentials from Chrome browsers on compromised machines.
Batch Script - logon.bat
The batch file triggers the PowerShell script execution during user logins, automating the credential collection process across all devices connected to the network.
Qilin Ransomware Group Tactics
The Qilin ransomware group employs sophisticated methods to maintain anonymity and evade detection. Victims are directed to communicate exclusively via dark web portals or encrypted messaging apps like Telegram, making it exceedingly difficult for law enforcement to track their activities.
Ransom payments are demanded in cryptocurrencies, typically Bitcoin or Monero, ensuring transactions remain untraceable. Despite paying the ransom, victims often find that there is no guarantee of receiving the required decryption tools to recover their encrypted files.
Qilin Ransomware Notorious Attacks
Qilin Attack on Synnovis
In June, the Qilin group launched a devastating attack on Synnovis, a critical supplier of blood testing and transfusion services for NHS hospitals in London. The breach triggered a critical incident, causing widespread disruption across healthcare services.
The group claimed responsibility via its dark web leak site, threatening to release stolen data unless Synnovis paid an exorbitant ransom of $50 million. This attack underscores the escalating threat of ransomware to the UK’s healthcare sector. Despite the ransom demands, Qilin claimed in media statements that their actions were politically motivated—a protest against the British government’s alleged involvement in a conflict.
Such political claims are unusual for the group, which has historically focused on financial extortion. Their previous targets include hospitals, schools, and businesses across various industries. The staggering ransom demand reflects the immense impact on NHS hospitals, raising questions about the group’s true motives.
The Qilin ransomware attack has severely affected NHS trusts and GP surgeries dependent on Synnovis services. The disruption, detected on June 3rd, has led to:
- Blood stock shortages
- Delays in medical procedures
- Cancelled operations and appointments
The NHS, with its complex IT infrastructure and limited resources, remains a prime target for ransomware groups like Qilin. Unlike businesses, healthcare providers cannot afford downtime without risking lives, making them especially vulnerable to cyber extortion.
This attack highlights the urgent need for improved cybersecurity measures to protect critical healthcare infrastructure from threats posed by the group and similar cybercriminal organisations.
Google Chrome Credential Theft
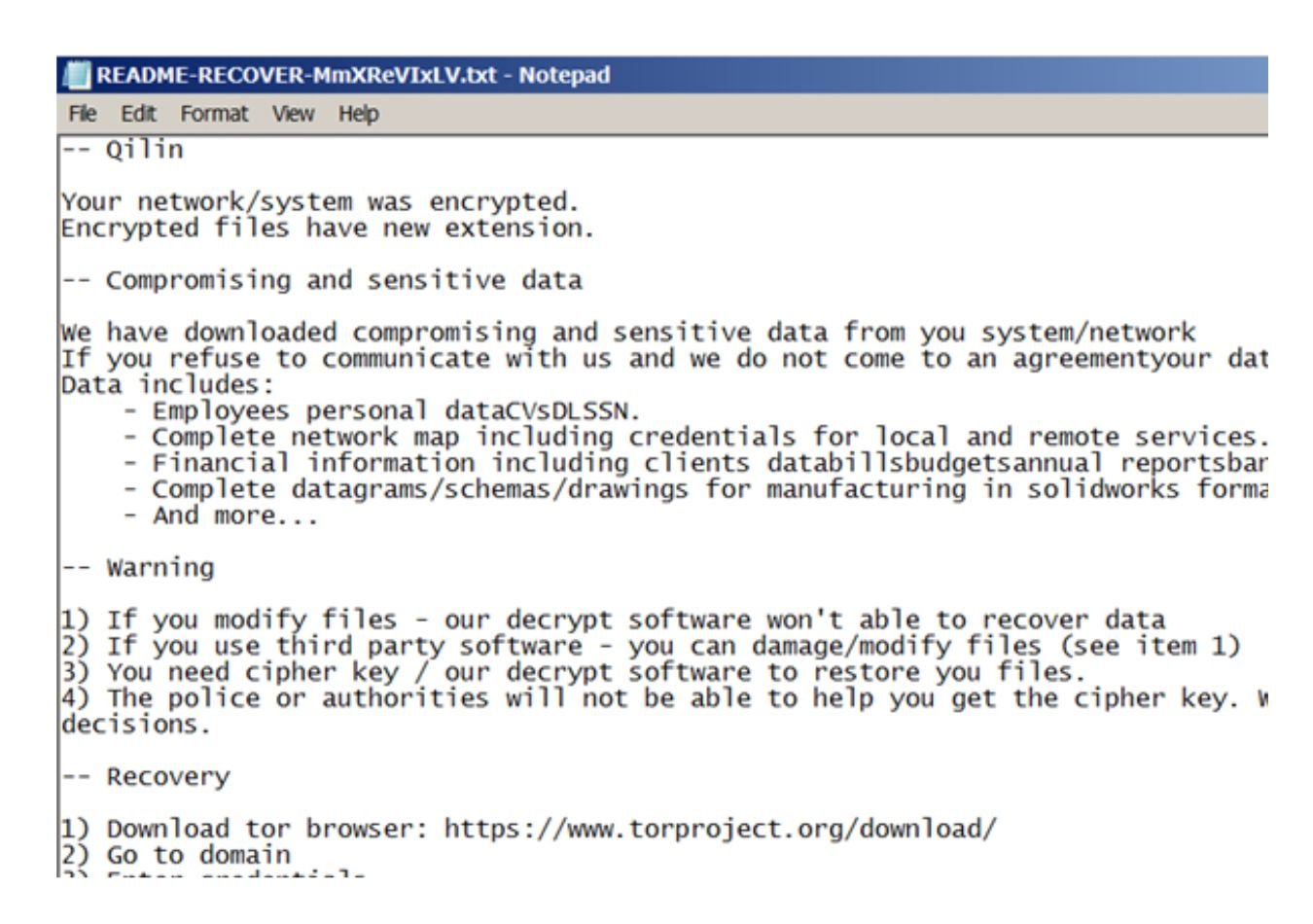
A recent Qilin attack has exploited vulnerabilities in Google Chrome, targeting credentials stored in the browser. This cybersecurity incident, reported by Sophos, highlights a significant evolution in ransomware tactics, where credential theft is combined with ransomware deployment to pose heightened security risks.
First detected in July 2024, the attack leveraged compromised VPN credentials from a portal without multi-factor authentication (MFA). This oversight allowed attackers to infiltrate the network and initiate post-exploitation activities after an 18-day delay. They eventually accessed the domain controller and modified the default domain policy to achieve persistence.
Using a logon-based group policy object (GPO), the attackers deployed two key scripts:
- IPScanner.ps1 – A PowerShell script designed to harvest sensitive credentials stored in Google Chrome.
- logon.bat – A batch script that triggered the credential harvesting process during user logins.
This GPO remained active for over three days, enabling continuous theft of Google Chrome credentials every time users logged in.
How to Protect Your Organization from Qilin Ransomware Attacks?
Qilin ransomware attacks pose a serious threat to businesses and organisations, especially in vulnerable sectors such as healthcare, education, and public administration.
These industries are often targeted due to their reliance on critical data and weaker cybersecurity measures compared to more fortified sectors like financial institutions or government entities. However, it’s crucial to understand that Qilin ransomware can target any industry, leaving no organisation entirely immune.
Best Practices to Safeguard your Organisation
To safeguard your organisation, it’s essential to follow best practices in cybersecurity:
- Offsite Backups: Regularly back up your critical data to offsite locations. In the event of a ransomware attack, secure backups will ensure that you can restore your systems without paying the ransom.
- Keep Security Solutions Updated: Ensure your antivirus software and all security solutions are up to date. Regularly install the latest security patches to close vulnerabilities that Qilin or other ransomware can exploit.
- Network Segmentation to Limit Lateral Movement: Restrict an attacker’s ability to move laterally across your network through proper network segmentation. This will isolate critical systems and limit the spread of ransomware.
- Use Strong Passwords and Multi-Factor Authentication: Protect sensitive data and accounts with strong, unique passwords. Enable MFA wherever possible to add an extra layer of security.
- Encrypt Sensitive Data: Implement data encryption to protect sensitive information, making it harder for attackers to access or exploit even if they breach your system.
- Reduce Your Attack Surface: Disable unnecessary services and features within your organisation to minimise the attack surface that cybercriminals can exploit.
- Educate Your Staff: Provide ongoing cybersecurity training for employees. Educating your staff about phishing, social engineering, and ransomware tactics will reduce the risk of human error leading to a breach.







Comments ( 0 )