As long as you’re using digital devices in your daily work, your company needs data security, and with it, data security management.
The increasing sophistication of cyber attacks, paired with the volume and complexity of the data you store, means that your data has never been more vulnerable to cybercrime.
All it takes is one malicious hacker to gain access to your IT systems and all of your data can be exposed. That’s why keeping your data secure through data security management has never been so important.
This article explores everything you need to know about data security management, including its meaning, benefits, and importance in today’s cyber threat landscape.
What is data security?
Data security is a security procedure that involves protecting digital information using a range of tools, policies and procedures. Its primary objective is to safeguard digital information throughout the entire data lifecycle – from creation to deletion.
This involves denying hackers access to your data, preventing data from getting lost by any means, collecting new data securely, and much more.
There are three main objectives of data security:
- Confidentiality: This ensures that only authorized people can access your data.
- Integrity: This means that your data is accurate and hasn't been tampered with.
- Availability: This makes sure that the people who need your data can access it when they need it.
These three core principles, often referred to as the CIA triad, form the bedrock of data security. If it keeps your data safe, it falls under data security.
Why is data security important?
A major factor in the importance of data security is the cost of doing it wrong. The damage from cybercrime that can take place thanks to poor security is staggering, leading to major financial losses, legal repercussions and even reputational damage.
Businesses hold a vast amount of sensitive data, including customer information, intellectual property, and financial records, and robust data security protects organizations from these threats.
Read: Top 10 Most Expensive Cyber Attacks
As if costing billions per day isn’t bad enough, overlooking the value of data security can also lead to your information being used by people with malicious intentions.
Data breaches can be incredibly dangerous for individuals as they can expose sensitive information like financial records, medical history, and social security numbers.
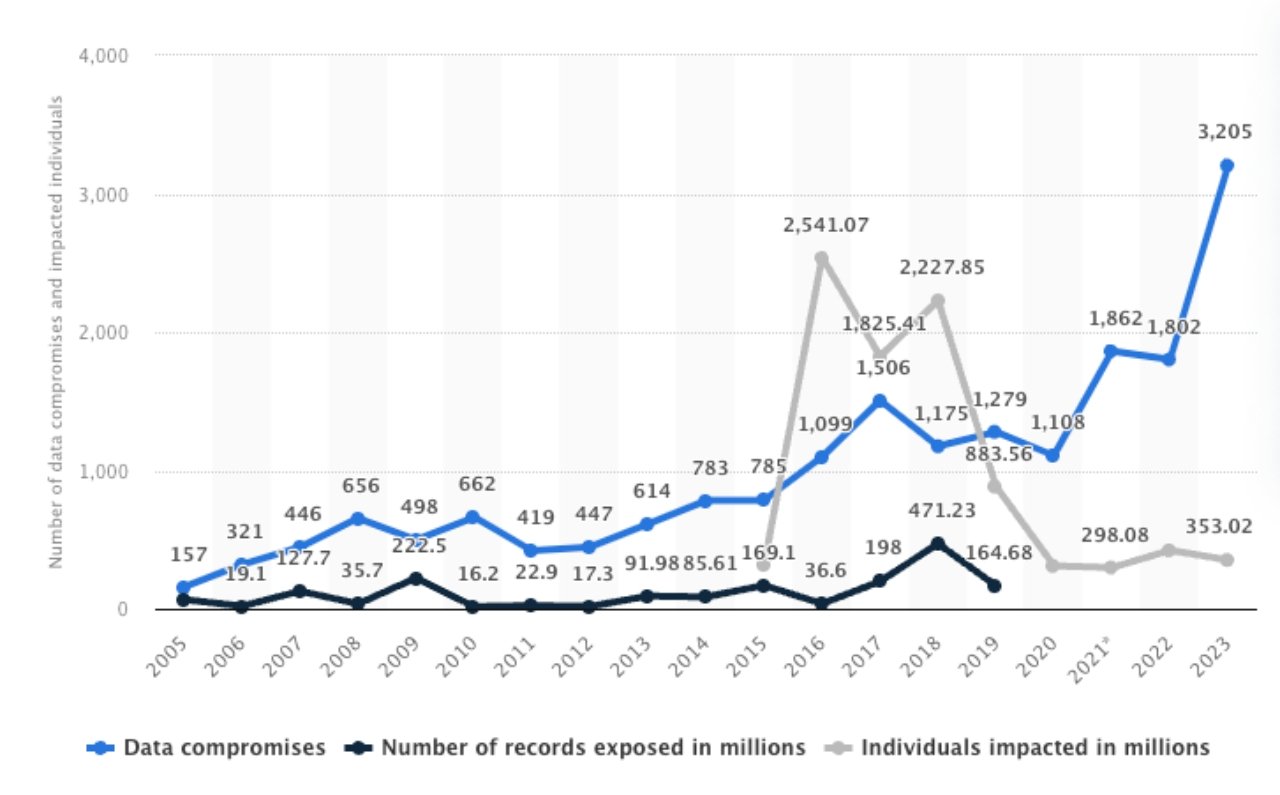
Every time you use your electronic devices at work, you’re generating data. For example, you create new data whenever you send an email, create a graph, set up a hyperlink, or do just about anything else that involves making some kind of change.
This also includes activities like looking up keywords in a search engine. Here, you’re not creating brand-new information, but you’re still generating data about your behaviour.
You’ll have spent time and energy following data quality best practices to make sure you eliminate errors and poor-quality data from your systems. You don’t want to throw away all that good work by not protecting your data.
For example, let’s say you’ve created a commercial proposal and saved it on a work laptop with poor security protocols. That proposal can then be stolen by fraudsters, who might charge you a ransom for your document or even release it, exposing the potentially sensitive information it contains.
Strong data security is crucial in protecting your organization and your users and customers from these threats
What is data security management?

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
Data security management is the process of implementing and overseeing the strategies that safeguard an organization's data. It establishes processes for identifying, containing, responding to, and recovering from security incidents to minimize damage and prevent future occurrences.
When you manage data security, you’re taking the theoretics of security and ensuring they’re applied properly in practice. This starts by developing a security policy that outlines your organization's data security objectives, acceptable use practices for data and systems, and incident response protocols.
You then need to implement risk management procedures to keep your data secure. This involves Identifying potential threats and vulnerabilities to data by conducting regular risk assessments to proactively address weaknesses and prioritize security measures.
Components of Data Security Management
1. Keeping data safe from outside sources
Many attempts on your data will come from outside of your company. That’s why it’s an absolutely crucial part of effective data security management to make sure you’re limiting who can access your data from outside your company.
Implementing company firewalls, for example, makes it much harder for outsiders to reach the data stored on any company devices. VPNs can help achieve the same effect for remote workers.
While these kinds of measures won’t protect against fraudsters within your company, they’re immensely helpful in cutting off outside threats.
2. Protecting data centers
At the moment, the US is the world leader in the number of data centers within a country. However, even at that, it has less than 3,000 data centers across the entire country:
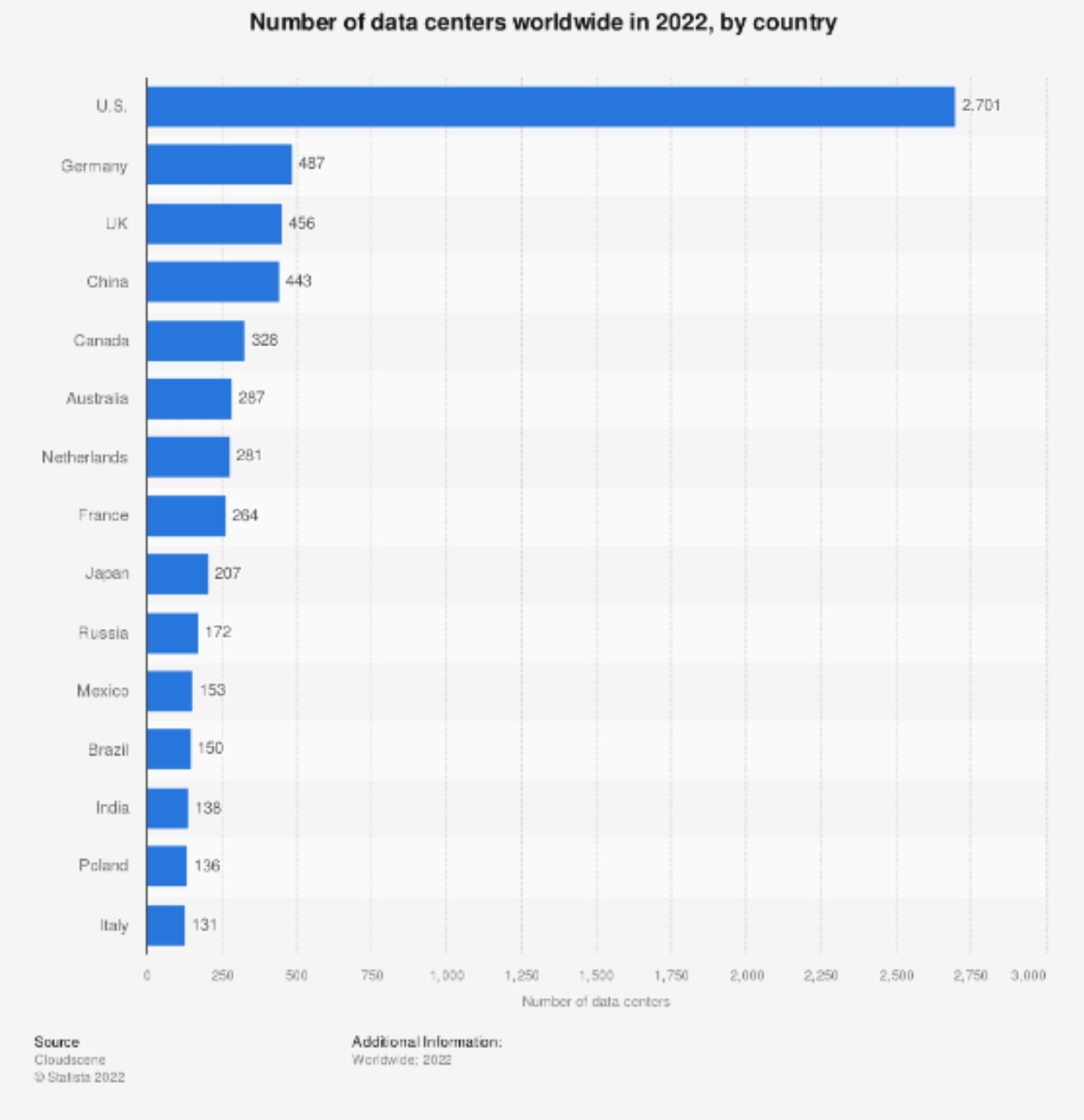
This tells us that any given data center has to contain a lot of information, knowing that billions of gigabytes of data are generated each day. It’s also why data security management needs to include practices for keeping those data centers as safe as possible.
If data is information, think of data centers as giant filing cabinets filled with all kinds of documents, each one containing huge quantities of information. In short, they’re storage houses for virtual information.
Inside a Social Graph Collapse
A case study in weak mobile-era adaptation, algorithm shifts, and feature deprecation eroding network effects in visual platforms.

This explains what they are as well as why they need to be protected. If the site where your data is being held is at risk, it becomes much harder to guarantee the safety of that data.
3. Establishing protocols and fail-safes for data breaches
Perhaps the most time-consuming part of data security management focuses on protocols.
Strong data security management protocols need to do more than just keep data safe in theory. They also have to do two other things: measure up in realistic settings, and provide instructions for what to do in the event of a security breach.
As it stands, less than one-quarter of companies that experienced a data breach actually made changes to their firewall security measures—with a further 14% doing nothing at all in the wake of the breach:
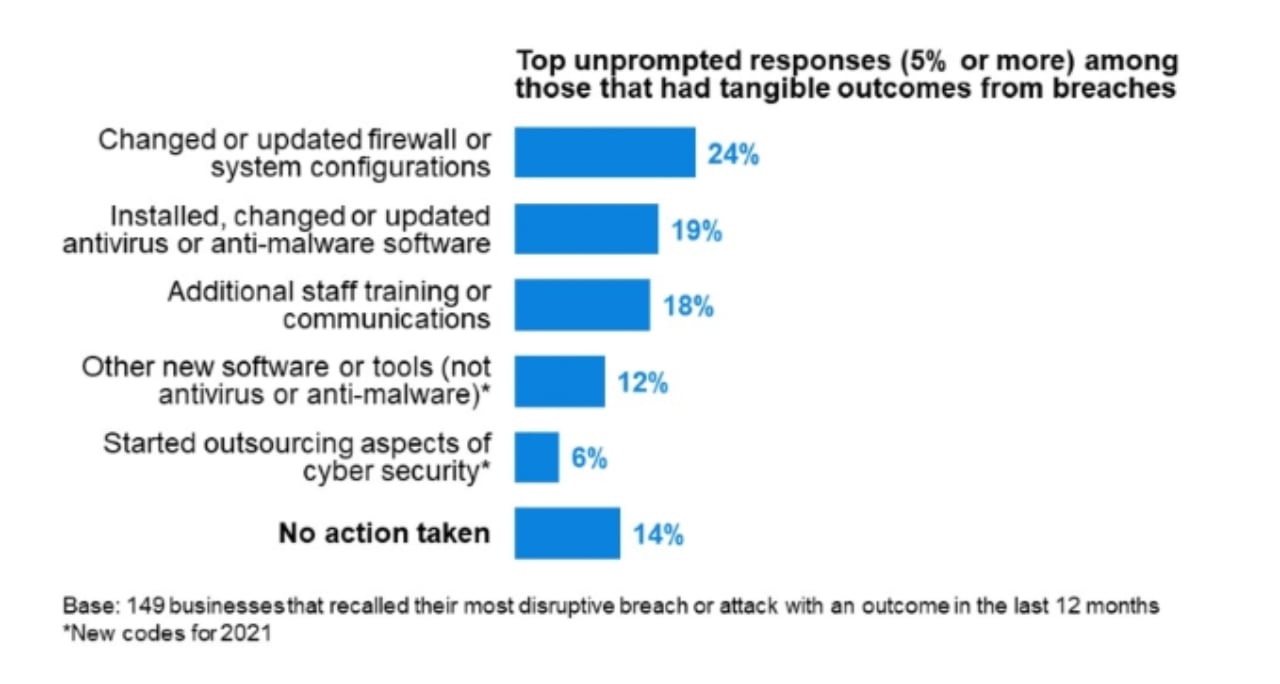
Striving for top-tier data security management means being part of the percentages that have strong protocols in place for all events. It means knowing just what to do if a breach happens, and exactly how to go about preventing that breach from happening.
Good protocols start from the basics. A data streaming platform can be a good jumping off point for exploring secure data sharing with other organizations.
Data security management best practices
Finally, let’s go through some of the best practices you can adopt to take your data security management to the next level.
1. Use multiple layers of security
Encrypting data is a good idea. Double-encrypting it, then putting it behind a strong firewall is a better plan. You can further protect that data by also installing anti-malware software, setting up breach protocols, requiring sign-ins to access the data, and so on. Data clean rooms allow you to collaborate with customers and partners in a private setting.
In other words, combining the measures you use to protect data keeps it safer.

When Info Overload Hits Risk
Fragmented AI and security signals now create governance blind spots. Explore a model that reduces decision risk through shared context.
There’s no such thing as overkill, provided the people who need it can still reach your data. It’s much better to be fully prepared for an attack that doesn’t happen, than to leave your security measures lacking and simply hope for the best.
2. Revise and update policies often
Unfortunately, hackers and fraudsters are only getting smarter with every year that passes. You’ve got to be ready for them—and measures from a few years ago aren’t going to cut it.
What you need to do to properly manage your data security is go over all your policies and protocols on a regular basis. This will allow you to ensure your plans keep up with those of the people you’re protecting your data from. It will also help you spot faults and weaknesses before anyone can exploit them.
Additionally, staying on top of your policies’ development is a great way to ensure you’re always prepared to catch data breaches as they happen, and to respond appropriately. This helps you prepare and protect the people whose data you’re looking after, and it ensures they’re more ready to forgive you:
3. Test extensively, and frequently
There’s no such thing as testing your security measures too much.
Any given tester is bound to think of a different way to assess the strength of your data security protocols. This helps ensure you’re not exclusively protected from people who think like your data security management team.
It’s a good idea to make sure you’re recruiting plenty of diverse testers for this reason. For example, you might bring freelance testers on board alongside company professionals.
4. Create dedicated teams
To fight security threats, you need experts, and those experts need the right kind of support to work at their best.
In other words, you need dedicated teams. Alongside your testers, you’ll also want security management teams. These might be split up depending on the functions you need to see performed on a regular basis.
Temu and the Data Trust Deficit
How ultra-low-cost marketplaces reshape data governance, consent, and transparency expectations across global digital commerce.

Just like your policies, your teams need to be kept fresh and updated regularly. When a new threat arises, you ideally want to have experts to hand already, which means constantly recruiting new talent with skills in detecting trends in security threats.
5. Always keep researching
Every year, the total number of cyber-attacks increases - and in fact, in recent years, it’s been rising on a weekly basis.
This worrying trend means that data security management needs to be an active practice rather than a passive one. There’s no use in assuming you know everything. You’ve got to put in the work to research all kinds of threats, continuously, so that no one catches you by surprise.
Even if a threat appears that you’re not fully prepared for, regular and extensive research will equip you with the tools you need to mitigate the risks it poses. At the very least, you can make yourself the least attractive target for an attack by demanding more work to breach your security, which is often enough to deter fraudsters and hackers.
Things to keep in mind
Data security is deceptively simple as a concept, though it’s often difficult to practice realistically.
With effective data security management, you can make sure you get as close as possible to perfectly safe data. This protects both your company and the information itself.
As our technology develops, so too does the world of data security management, meaning that the current state of things may become outdated very quickly. That’s why data security managers need to be proactive, and why they’ll always play a key role in protecting information.







Comments ( 0 )