If you run a financial service today, you’re running a technology service too. Payments, onboarding, trading, claims, credit decisions, customer support, fraud controls, reporting, and regulatory submissions all ride on systems that can fail in quiet ways or spectacular ones.
The EU’s Digital Operational Resilience Act wasn’t written because regulators suddenly developed a passion for acronyms. It exists because the financial sector’s dependence on complex, outsourced, always-on digital infrastructure has outpaced the rules that were meant to keep customers and markets safe.
What Is the Definition of the Digital Operational Resilience Act (DORA)?
The Digital Operational Resilience Act (DORA) is an EU regulation that sets consistent requirements for managing information and communication technology risk across the financial sector. In plain terms, it expects financial firms to keep delivering critical services even when systems are disrupted, whether that disruption comes from a cyber-attack, a software failure, a cloud outage, or a supplier problem.
DORA entered into force in January 2023 and has applied since 17 January 2025. That “applies” date is the one that matters operationally, because it marks when firms in scope are expected to meet the requirements under supervisory scrutiny.
One of DORA’s big shifts is that it pulls scattered ICT requirements into a single, more coherent framework, rather than leaving resilience split across different sector rules, guidance, and national interpretations.
Why was DORA introduced?
DORA was introduced because financial services had become deeply dependent on digital infrastructure without a consistent, enforceable standard for resilience across the EU. As firms expanded their use of cloud platforms, managed service providers, and complex software supply chains, the gap between regulatory expectations and operational reality widened.
That risk became impossible to ignore after the 2020 SolarWinds attack. A compromised software update from SolarWinds gave attackers long-term access to thousands of organisations worldwide, including government bodies and major enterprises. The incident wasn’t just a security failure. It exposed how a single trusted supplier could become a systemic risk across entire sectors.
For regulators, SolarWinds highlighted a critical weakness. Financial institutions could meet existing security requirements and still be vulnerable to failures buried deep inside their third-party technology stack. Oversight was fragmented, supplier accountability was uneven, and resilience expectations varied widely between EU member states.
DORA was designed to close that gap. Rather than focusing narrowly on cyber controls, it establishes a unified framework that treats digital resilience as an operational requirement. One that covers governance, incident response, testing, and third-party risk in a way that reflects how modern financial services actually run.
Is DORA Just for the Financial Sector?
Mostly, yes, but not only.
DORA is aimed at EU “financial entities” and the resilience of the services they provide. That includes banks, insurers, investment firms, and other regulated financial organisations operating in the EU.
Where it expands the blast radius is third-party technology dependency. DORA creates an oversight framework for certain ICT providers that are designated as critical because so many financial firms rely on them. That’s how you get from “financial regulation” to direct pressure on major tech suppliers.
So if you’re a non-EU provider selling into EU regulated firms, DORA can still change your world. Not because you magically become a bank, but because your customers’ compliance obligations will force contract changes, audit rights, reporting expectations, and exit planning.
How Does the Digital Operational Resilience Act (DORA) Help Mitigate Cyber-Attacks?
Cyber-attacks don’t just succeed because controls are weak. They succeed because organisations are slow to detect, hesitant to escalate, unclear on responsibilities, and overconfident about third parties. DORA tackles those failure patterns by forcing repeatable operational habits.

BCM Software and the DORA Shift
Why boards are replacing static plans with platforms that prove resilience, meet 2025 regulatory tests, and turn BCM data into audit-ready evidence.
First, it pushes a stronger, documented approach to ICT risk management. That means security isn’t treated as a set of tools, it’s treated as a managed system with governance, policies, controls, and oversight that can be examined and challenged.
Second, it tightens incident discipline. DORA requires major ICT-related incidents to be reported to competent authorities, using harmonised approaches and templates. This matters because messy incident reporting is usually a symptom of messy incident response. Reporting pressure has a way of exposing what isn’t clear internally.
Third, it makes resilience testable. It’s easy to say “we’re prepared”. It’s harder to prove it under realistic conditions. DORA’s testing expectations, including advanced testing for the most significant entities, are designed to turn confidence into evidence.
Finally, it addresses the supplier problem directly. A huge amount of financial sector risk now sits inside outsourcing chains. DORA strengthens requirements around third-party risk and creates mechanisms for oversight of critical ICT providers, which is a direct response to systemic concentration risk.
What Are the Five Pillars of the Digital Operational Resilience Act (DORA) Regulation?
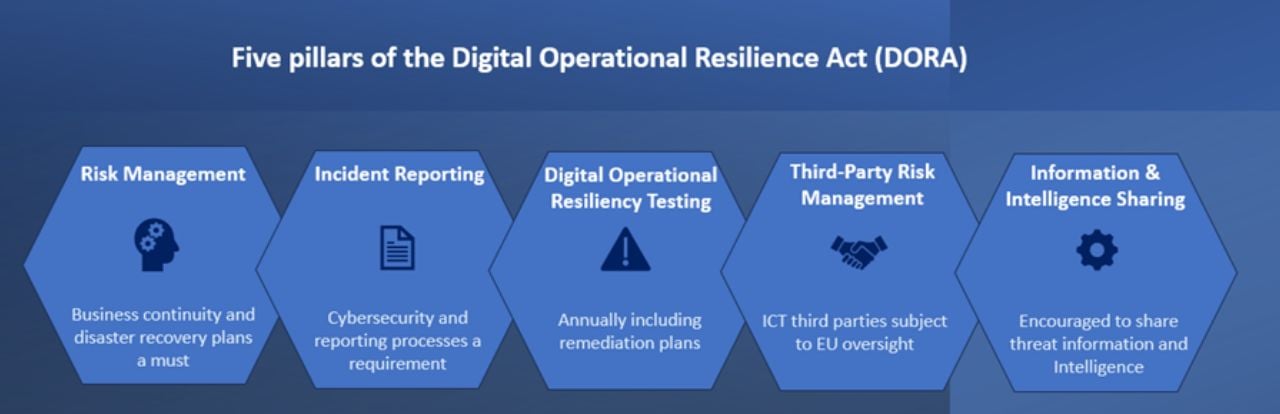
DORA is typically explained through five practical pillars. The names vary slightly depending on who’s summarising, but the structure is consistent:
Risk management
This is the foundation: governance, policies, protection, detection, response, recovery, and learning loops that can be evidenced and audited, not just “owned” by security teams.
Incident reporting
DORA formalises what gets reported, to whom, and how. That improves consistency across jurisdictions and reduces the chance that serious incidents get downplayed, delayed, or mishandled because teams can’t agree on severity.
Digital operational resilience testing
This is where resilience stops being a slide deck. DORA expects regular testing, and for some firms, more advanced threat-led exercises aligned to EU frameworks like TIBER-EU. The point isn’t to “win” a test. The point is to reveal how the organisation behaves under pressure.
ICT third-party risk management
Inside Modern DCIM Platforms
Telemetry, asset intelligence and integrated workflows turn sprawling server halls into measurable, optimizable infrastructure.

DORA strengthens expectations around supplier oversight, including contractual safeguards and the ability to understand and manage dependencies, especially where suppliers support critical or important functions.
Information sharing
DORA encourages structured sharing of cyber threat information and intelligence. Done well, it improves sector learning and reduces duplicated mistakes. Done badly, it becomes performative. The regulation’s intent is the former.
DORA’s Impact on Financial Institutions
DORA changes how financial institutions run technology risk as a business issue, not a specialist concern. That shows up in a few very practical places.
Governance gets sharper
DORA raises the standard for oversight. Senior leadership can’t treat resilience as “handled” because the evidence trail will reveal whether responsibilities, approvals, and risk decisions are real or ceremonial.
Reporting becomes an operational capability
Many firms discover, too late, that they can’t report cleanly because they can’t classify cleanly. If you can’t decide what’s major, you can’t decide who owns response, customer comms, regulatory comms, and internal escalation. DORA’s reporting requirements push organisations to build that muscle.
Third-party management stops being procurement-led theatre
DORA puts pressure on contract terms, audit rights, monitoring, exit strategies, and concentration risk, especially where critical functions rely on third parties. This is also where a lot of the “real work” sits, because suppliers won’t all be equally willing or equally mature.
Testing becomes a leadership issue, not a security exercise
Threat-led testing, when required, forces coordination across IT, security, risk, legal, comms, and business owners. It also forces the organisation to confront inconvenient truths, like the gap between “documented” recovery and actual recovery.
What Are Consequences of Non-Compliance to the Digital Operational Resilience Act (DORA)?
Managing AI Costs and Outcomes
Examines the gap between AI promises and operational reality, highlighting cost inflation, tech debt, and reliability pressures on I&O teams.

DORA doesn’t give you a single universal fine table because enforcement is carried out through national competent authorities, and Member States set rules for penalties and remedial measures in their legal frameworks. But the direction is clear: penalties and measures must be “effective, proportionate and dissuasive”.
The regulation also spells out the types of supervisory actions competent authorities must have the power to apply. Those include orders to stop non-compliant conduct, requiring cessation of practices, measures of pecuniary nature to ensure ongoing compliance, and public notices that name the entity and the breach. Depending on national law, criminal penalties may also apply for certain breaches.
For critical ICT third-party providers under the oversight framework, DORA goes further and includes periodic penalty payments to compel compliance. The regulation describes a mechanism where a daily penalty payment can be imposed until compliance is achieved, with the amount up to 1% of the provider’s average daily worldwide turnover in the preceding business year.
There’s also a practical consequence that matters just as much as formal penalties: if a key supplier becomes a regulatory problem, firms may be forced to suspend or terminate use of that service as a last resort, which turns compliance into an availability and continuity issue very quickly.
Read: Top 10 Biggest GDPR Fines in History (So Far)
Who Are Examples of Early Adopters and Industry Leaders?

Because DORA is a regulation, early adoption rarely looks like public celebration. It looks like organisations doing the unglamorous groundwork before deadlines force reactive fixes.
One clear signal of early adoption has been engagement with supervisory preparation efforts. In 2024, EU supervisors ran dry run exercises to help financial entities prepare for structured reporting requirements, including the registers of information used for third-party oversight. Firms that took these exercises seriously were typically aiming to industrialise compliance early, rather than patching processes under time pressure later.
When Security Tools Break Ops
A flawed CrowdStrike update halted critical services worldwide, forcing leaders to reassess cyber tooling, dependencies, and business continuity.

Industry leadership also shows up in how large institutions approach operational resilience more broadly. Global banks such as HSBC have spent years investing in resilience frameworks, third-party risk visibility, and large-scale operational testing across regions. While not positioned as “DORA programmes”, these efforts align closely with the regulation’s intent and put organisations in a stronger position as requirements take effect.
On the technology side, DORA is reshaping expectations for suppliers as well as financial institutions. In November 2025, EU regulators designated a group of technology companies as critical third-party providers to the financial sector, bringing them under direct oversight tied to financial stability. Firms such as IBM, which already work extensively with regulated industries on resilience, risk management, and governance, sit squarely in this evolving ecosystem where operational discipline and regulatory awareness increasingly intersect.
There’s also a growing layer of specialist providers responding directly to DORA-driven demand. For example, Fireblocks announced a DORA-focused compliance offering after the regulation began applying in January 2025. That kind of productisation is another market signal. Vendors don’t invest here unless customers are actively looking for ways to operationalise resilience, not just document it.
Final Thoughts: DORA Forces a Rethink of Digital Resilience
The Digital Operational Resilience Act isn’t just another regulatory requirement. It’s a clear signal that digital resilience now sits at the centre of financial stability, governance, and leadership accountability.
By bringing risk management, incident response, resilience testing, and third-party oversight into one framework, DORA exposes where assumptions have replaced evidence. For financial institutions, the real work starts beyond compliance, in understanding how technology dependencies and operational decisions hold up under pressure.
As DORA takes effect, the organisations best positioned to respond will be those that treat resilience as an ongoing operational discipline, not a one-off regulatory exercise. That’s the lens EM360Tech brings to emerging regulation and cyber risk, helping enterprise leaders understand not just what’s changing, but why it matters and what it means in practice.







Comments ( 0 )