The cloud is now the backbone of the modern enterprise. It runs revenue systems, customer experiences, identity, analytics, software delivery, and the connective tissue between business units that used to live in separate data centres.
It’s also one of the most hostile and least understood operational environments in IT, and one where companies like Aviatrix see the sharpest gaps between how cloud security is designed and how it actually operates. That’s not because security leaders don’t care, or because organisations lack tools.
It's because cloud environments change faster than most security operating models were built to handle. Workloads appear and disappear. Connectivity patterns evolve with every release. Access is granted through identities and APIs that rarely fit neat perimeter assumptions. When something goes wrong, attackers don't politely wait for teams to agree on who owns the response.

The Cloud Has Become the New Operational Battlefield
Enterprise cloud estates don't sit still. They stretch across regions, accounts, subscriptions, projects, and providers. They run on managed services that abstract away infrastructure, which is great for speed and resilience, and hard for consistent governance. They are also increasingly multicloud by design, whether that is deliberate strategy or the result of acquisitions, regional requirements, and product teams choosing what ships fastest.
Multicloud environments expand the attack surface in a specific way. This means an increasing amount of network facets that need to be secured, including control planes, identity boundaries, network constructs, and default settings, not to mention differences in how each cloud expresses the same idea.A security pattern that works cleanly in one provider can become a mess of exceptions in another.
Attackers benefit from that asymmetry. They only need one pathway that nobody fully mapped, one permission chain that was never meant to persist, one workload communication route that bypasses the controls people assume are in place. The cloud does not make defenders weaker. It makes the penalty for partial understanding much higher.
Why Traditional Security Models Break Down in the Cloud
Perimeter-based security made sense when you could draw a relatively stable line around “inside” and “outside”. In cloud-native environments, that line is either blurry or irrelevant.
Most meaningful movement happens inside. Workloads talk to workloads. Services call other services. Data moves across layers that don't look like classic network segments. Identity and access decisions often happen far away from where the traffic actually flows. That is why east-west traffic matters so much. It's where the business lives, and where attackers try to blend in once they have a foothold.
Static controls struggle here for a simple reason. They assume you have time to understand the environment before it changes. Cloud delivery pipelines do not. When teams rely on slow, manual mapping of connectivity or on a patchwork of tools that each see a narrow slice, they end up protecting an older version of reality.
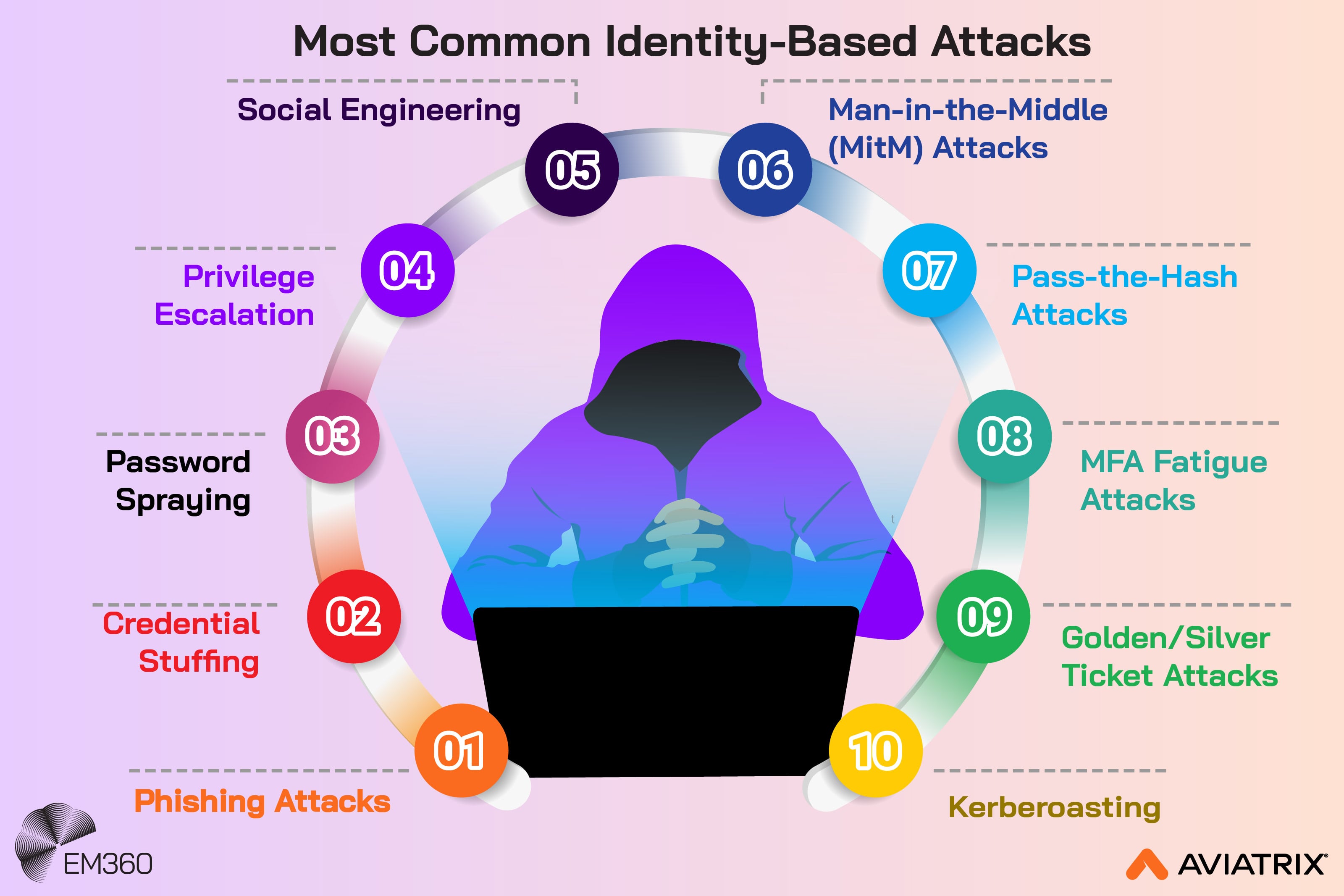
This is also where identity-driven attacks change the game. If access is granted through identities, tokens, and API permissions, then “network security” and “identity security” are no longer separate disciplines. They are two views of the same problem, and that problem is operational.
The Real Vulnerability Is the Fog of War
The biggest risk in cloud defence is not that the organisation lacks technology. It's that nobody has a complete, trustworthy view of what is happening right now.
Cloud estates generate enormous volumes of signals. Logs, events, flow data, alerts, configuration changes, identity actions, and deployment artefacts. But signal volume is not the same as understanding. When visibility is fragmented, teams end up with dashboards that confirm what they already suspect and miss what they cannot see.
That is the cloud version of fog of war. Situational awareness breaks down when:
Cloud Simplicity in a Multi Cloud Conundrum
Time and time again, users have struggled to achieve cloud simplicity for a number of reasons. While multi cloud is more or less essential in the mode

- networking teams see connectivity but not workload intent
- security teams see detections but not the normal communication graph
- platform and DevOps teams see deployments but not downstream exposure
- incident responders inherit a pile of alerts without a shared map of pathways
In that state, decisions slow down. Escalations multiply. Containment becomes risky because nobody wants to cut the wrong connection and take production down. Attackers don't need to be brilliant. They just need defenders to hesitate.
Why Cloud Defense Cannot Be a Solo Mission
Cloud defence is often treated like a security team deliverable. That framing sets everyone up to fail.
Cloud environments are built and run by multiple groups, each with legitimate priorities. Platform teams optimise for reliability and velocity. Networking teams fight for connectivity and performance. Security teams push for control and risk reduction. DevOps teams keep releases moving. In many enterprises, these groups operate with different toolchains, different success metrics, and different definitions of “done”.
This is not a people problem. It's a structure problem. When security responsibility is spread across teams but operational authority is unclear, the organisation ends up with security ownership that is shared in theory and fragmented in practice.
The result is predictable. Policies exist but are inconsistently enforced. Controls are deployed but not integrated into daily operations. Alerts are generated but not actionable at speed. The organisation becomes very good at talking about zero trust and much less consistent at executing it.
What “Special Forces” Means in a Cloud Security Context
The special forces metaphor is useful because it forces clarity, though not in the sense of secrecy or heroics. The key, rather, is operating with three characteristics that cloud defence demands.
First, it's embedded security. Defensive capability lives inside the environment, close to the workloads and communication paths that matter. This creates a continuous presence much more effective than a simple perimeter gate you pass once.

Aviatrix: The Security Architect's Guide to Multi-Cloud Networking
As enterprise cloud computing scales, it is expected to be 10x larger in size and complexity and will be deployed 1,000x faster than data center compu
Second, it's real-time security that is grounded in what workloads are actually doing. Not what they are supposed to do on paper. Not what a diagram said six months ago. Defence has to follow reality, and reality is behavioural.
Third, it's operational authority. When something is wrong, defenders need the ability to act quickly and precisely, without waiting for a chain of approvals that was designed for slower systems.
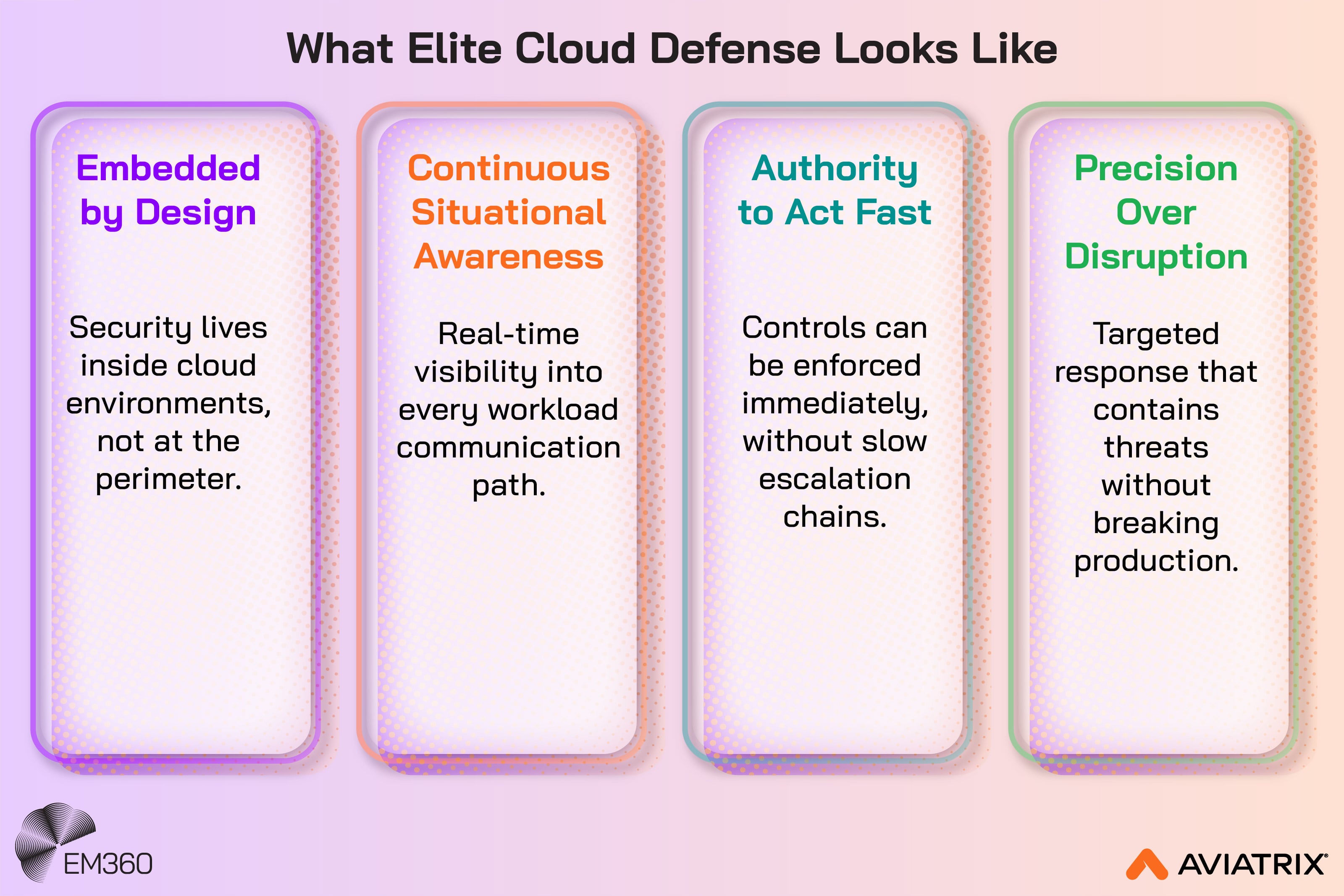
Precision matters here. Cloud environments are shared systems. Heavy-handed responses can cause outages, revenue loss, and customer harm. Elite cloud defence focuses on controlled, targeted actions that stop spread while keeping the business running.
From Tools to Tactics: Building a Cloud Security Operating Model
Technology is necessary. It's not sufficient. Cloud defence becomes mission-critical when the organisation treats it as an operating model, not a project.
A strong security operating model for cloud starts with shared intelligence. Everyone who is responsible for keeping cloud services safe should be working from a common picture of workload communication, identity access, and exposure. That does not mean one tool for everything. It means one truth layer that reduces argument and speeds decisions.
It also requires policy enforcement that travels with workloads. When guardrails depend on where something sits in a network diagram, they break the moment the environment evolves. Cloud security policies need to be expressed in ways that remain valid as infrastructure changes, and they need to be enforced consistently across accounts and clouds.
Automation helps, but only when it's aimed at decision-making. Cloud security automation should reduce time-to-understand and time-to-contain. If automation only increases the speed of alert generation, it simply moves the bottleneck downstream.
Finally, you need clear command paths during incidents. Who has authority to isolate a workload? Who can block a communication pathway? Who can revoke access, rotate credentials, or disable a risky integration? If those answers are fuzzy, response will always be slower than the attacker.
Operational Control Is the Difference Between Containment and Chaos
Aviatrix: Forrester's Total Economic Impact™ Study of The Aviatrix Cloud Network Platform
Forrester reveals customer ROI of 222% and total benefits of more than $4 million in three years for Aviatrix’s cloud network platform. Read this stud

When attackers gain a foothold in cloud environments, most organizations ask “can we detect them?” However, the real question should be “can we contain them before they move?” Operational control is what turns detection into action. It's the ability to map the blast radius, identify the pathways that matter, and apply targeted restrictions that stop spread. Without it, teams either respond timidly or respond destructively.
This is where lateral movement becomes a business issue, not just a security one. Attackers move towards what pays. Data stores, identity systems, deployment pipelines, and management planes. When defenders cannot see workload communication patterns clearly, or cannot enforce policy changes quickly, a small foothold becomes a broad incident.
Containment also has a human side. Teams under pressure need confidence that the action they take will help, not harm. Real-time visibility and clear controls reduce panic. They support calm, measured response that protects the business while shutting doors in the right order.
Why the Future of Cloud Security Will Favour Coordinated Defense
Cloud estates are not becoming simpler. Delivery velocity is not slowing down. The use of managed services and API-driven integration is accelerating. Attackers are adapting to that reality by leaning on identities, living-off-the-land techniques, and low-noise movement that hides in normal traffic.
That is why the organisations that win will not be the ones with the longest tool list. They will be the ones that align visibility, authority, and execution across teams.
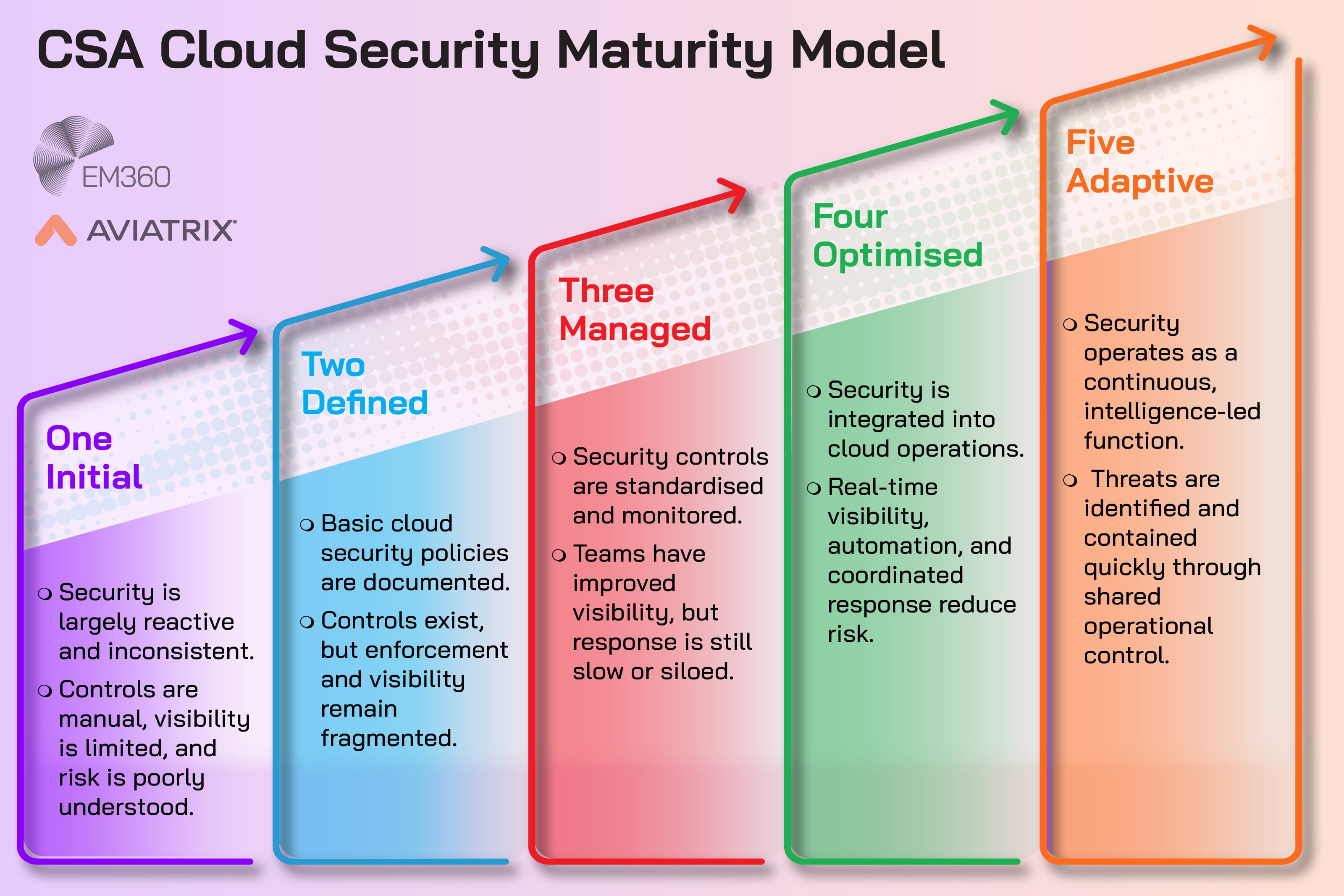
Over time, security maturity in the cloud will be judged less by policy statements and more by operational readiness. Can the organisation answer basic questions quickly? Do teams share a trusted picture of communication and access? Can they isolate risk without taking production down? Do they have a repeatable playbook that works on a normal Tuesday, not just during an annual audit?
This is also where cloud risk management becomes leadership work. Security cannot be treated as background function when the cloud is the operating environment for the entire business. Mission-critical systems need mission-grade defence.
Final Thoughts: Cloud Defense Fails Without Operational Command

Aviatrix: The Network Architect's Guide to Multi-Cloud Networking
Network architecture, network engineering, and network operations serve as the lifeblood of any application. This has always been true in the data cen
Cloud defence becomes mission-critical when you accept a hard truth. The cloud is not a static place you secure once. It's a living environment that changes by default, and it rewards attackers when defenders lack visibility, authority, and coordination.
The special forces mindset is simply a way to name what effective cloud security looks like at enterprise scale. Embedded defensive capability. Shared intelligence. Precision response. Operational control that lets teams contain threats quickly, without breaking the business in the process.
If the cloud is now your operational battlefield, the next question is uncomfortable but useful. Do your teams have a shared map, a shared mission, and the ability to act when the terrain shifts?
For security leaders looking to make that shift real, EM360Tech regularly publishes practitioner-led guidance on how enterprise teams operationalise cloud security. Aviatrix’s perspective on cloud security fabric principles also adds a practical lens for organisations that want to see communication pathways clearly and respond with speed and control, not guesswork.







Comments ( 0 )