In April 2023, the American Bar Association (ABA) was hacked affecting 1.5 million lawyers and others with accounts on the ABA platform whose login credentials, including encrypted password data, were compromised.
In fact, some of today’s current strong algorithms can also be hacked within hours or even minutes if using a quantum computing platform.
With rapidly advancing technologies, organizations, and their adversaries are beginning to leverage quantum mechanics for security interfaces.
But quantum computing can also be optimized to strengthen security systems against both present and future cyber threats.
One such organization, Quantinuum, provides a solution called Quantum Origin, the world's only source of verified quantum entropy to generate high-quality keys for digital certificates.

This article tells you everything you need to know about Quantum Origin developed by Quantinuum including what it is, some of its key features, benefits, and use cases.
What is Quantum Origin?
Quantum Origin by Quantinuum is a quantum random number generator (QRNG) platform that optimizes the power of quantum mechanics to yield cryptographic keys for stronger security against hacking attacks.
The solution is the world’s only provable and software-deployed quantum random number generator which can be integrated into an organization’s infrastructure. These cryptographic keys are provably unpredictable and can be strengthened to protect an organization’s most vital data and systems owing to their heightened resistance to hacking attacks when compared to traditional random number generators.
Quantum Origin can be easily deployed into an organization’s existing systems as a result of Quantinumm’s pre-built integrations. It’s also a unique software-based deployment that eliminates the need for extra hardware or a cloud connection.
Integrating Quantum Origin into an organization’s products can enhance the security foundation supporting the integrity and longevity of their systems which could ultimately provide greater value. The solution represents the next generation of quantum cybersecurity, built on stronger foundations than anything possible in the classical era.
How does Quantum Origin work?
Quantum Origin optimizes a powerful quantum computer to generate a quantum cryptographic key encryption. The inherent randomness of quantum mechanics ensures that these keys are virtually unpredictable, offering a significant security advantage over traditional cryptographic methods.
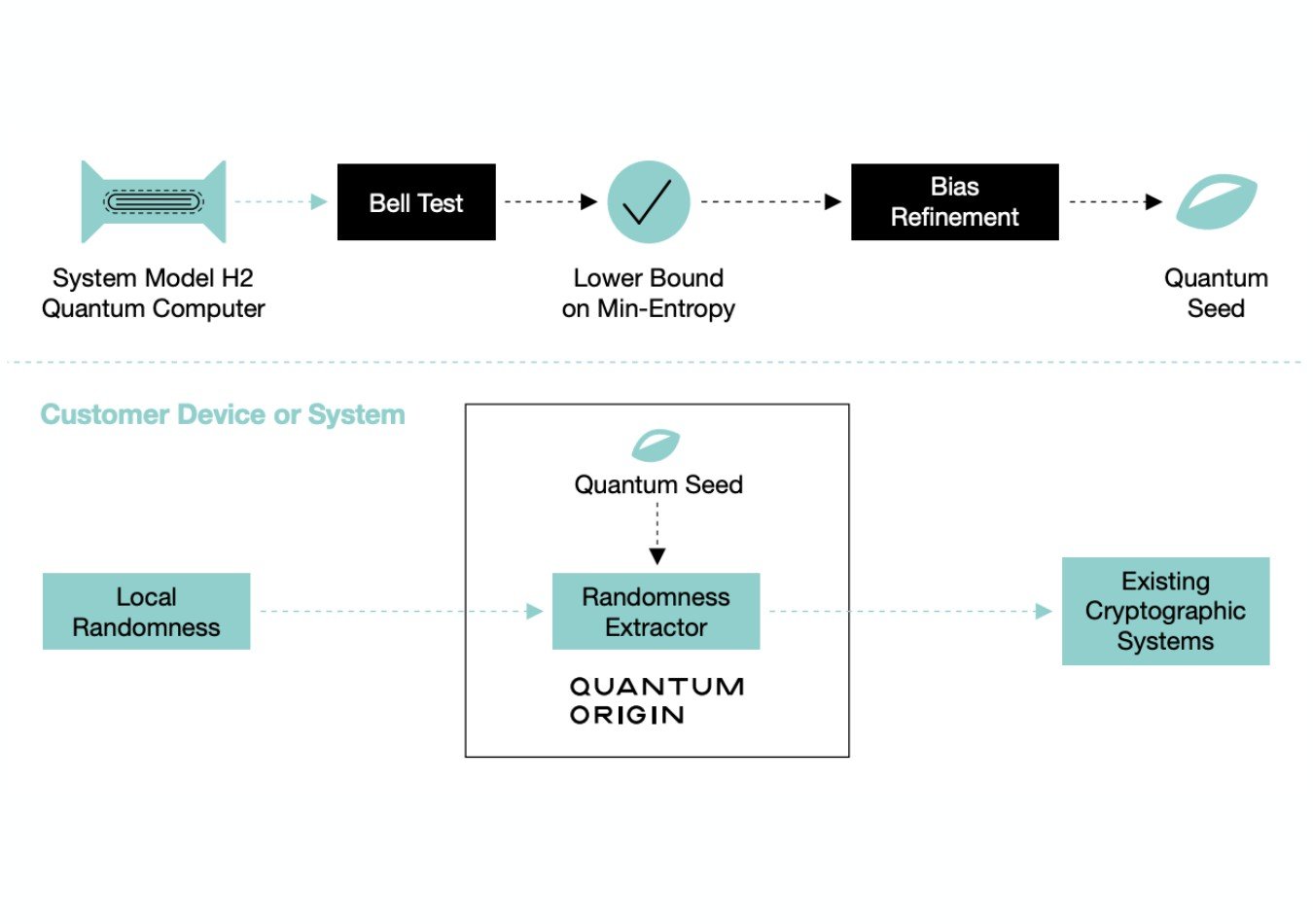
The process begins with a quantum computer, which is used to create a series of quantum bits (qubits) in a superposition state. This means that each qubit exists in multiple states simultaneously until it is measured. When a qubit is measured, its state collapses to a random value, either 0 or 1. This randomness is due to the fundamental unpredictability of quantum measurements.
After which, the quantum computer’s output is processed using classical algorithms to extract a sequence of random bits resulting in a cryptographic key generator. This key is secure and cannot be easily manipulated by classical computers. The seed quality is proven using a Bell test – a quantum technique that was awarded the 2022 Nobel Prize in Physics.
The Quantum Origin software deploys the embedded seed to enhance existing randomness in the target system, generating near-perfect randomness. No hardware or a cloud connection is required. This helps provide a major advantage over conventional random number generators, which can be compromised by hackers who have access to the underlying hardware or software.
Key features
1. Quantum cryptographic key
Quantum Origin uses properties of quantum mechanics to generate cryptographic keys with impeccable security. These keys are extremely hard to manipulate or predict because of the inherent randomness of quantum technology, unlike traditional security random number generators. Quantum Origin utilizes a quantum computer to generate keys that are truly unpredictable.

Inside Enterprise Quantum Bets
How IBM, AWS, Google and challengers are turning quantum pilots into enterprise advantage, and which bets CIOs should back through 2030.
The solution ensures the keys generated are truly derived from quantum technology through verifiable quantum randomness, providing an extra layer of assurance to users. Unlike classical cryptographic keys, which could be vulnerable to future quantum computers, Quantum Origin's keys are designed to be resistant to quantum attacks.
These generated cryptographic keys are nearly impossible to , ensuring strong security against classical and quantum attacks.
2. Cloud-based platform
Quantum Origin offers a convenient and accessible approach to organizations, helping them, leverage the power of quantum cryptography without the need for an upfront use of quantum hardware. Quantum Origin is a cloud-hosted service that can be accessed from anywhere with an internet connection, providing flexibility and ease of use.
This cloud-based approach eradicated the complexities of managing and maintaining quantum hardware, allowing organizations to focus on their core business while benefiting from the improved security provided by quantum-generated keys. The cloud-based platform enables Quantum Origin to be easily scaled to meet the changing needs of organizations. This ensures access to the latest security advancements.
3. Supporting traditional and post-quantum cryptography
Quantum Origin is versatile with future-proofing capabilities as it supports both current cryptographic algorithms including RSA and AES and emerging post-quantum algorithms to resist attacks from future quantum computers. The dual feature of the solution can also be easily integrated into already established security infrastructures while simultaneously preparing organizations for the future of quantum computing.

Quantum Origin provides a comprehensive solution that can help organizations protect their sensitive data against a wide range of threats, both present and future.
4. Integration with existing cyber systems
Quantum Origin is equipped with the capability to seamlessly integrate into existing cybersecurity systems, making it a practical and accessible solution for organizations of all sizes. Integration can take place across large cloud systems to small IoT devices.
Designing Quantum-Ready Defenses
How to build crypto-agile security architectures and access controls that can withstand AI-driven attacks and future quantum decryption.

In many cases, embedding Quantum Origin is seamless due to Quantinuum’s collection of out-of-the-box integrations with common operating systems, cryptographic libraries, and APIs (such as PKCS #11). The company aims to incorporate Quantum Origin into the core security framework of a device or system, which means that applications benefit from stronger randomness without any code changes.
Key benefits
1. Randomness extractors
Quantum Origin eradicates the need for client-side hardware because of randomness extractors. These extractors are a strong tool for distilling near-perfect randomness extracted from a number of weaker randomness.
The tool incorporates two inputs that help extract the near-perfect private randomness for encryption keys. The inputs include a private stream of data generated from a classical local source of randomness. The other is Quantum Seed which is a non-private piece of near-perfect randomness.
Powerful cryptographic keys are generated when an organization optimizes the quantum-backed randomness tool due to its mathematically verified quality level. In fact, mathematical guarantees are assured as a result of Quantum Origin’s unique ability to prove the quality of its output.
2. Quantum Seed generation
Quantum Origin leverages quantum computers to extract quantum seed which serves as the foundation for cryptographic key generation. Quantum Origin uses an innovative and patented approach using entangled qubits in quantum computers to generate these highly secure keys.
This quantum seed is generated by manipulating qubits, the fundamental units of quantum information, into a superposition state. In such conditions, every qubit exists in multiple states simultaneously until measured. When measured, a qubit's state collapses to a random value, either 0 or 1 – the randomness is unpredictable and cannot be controlled which ultimately boosts the encryption key.
3. Distribution and re-use of the Quantum Seed

When Cyber Risk Outruns Humans
Why governance, disclosure, and machine-speed containment now define resilience as AI-driven attacks and regulation close in.
Quantum Origin’s software, which is comprised of Quantum Seed, is designed for single use to maintain security and, therefore, doesn’t need to be delivered in encrypted format. Once the cryptographic key is generated, it is distributed securely to the intended recipient via a trusted channel such as a hardware security model (HSM). This ensures the seed’s confidentiality which is not compromised during transmission. Also, the Quantum Seed never needs to be replaced as the randomness extractor allows for 2300 uses of each Quantum Seed.
The same Quantum Seed can be used in multiple systems, provided they have their own independent local sources of randomness. After the seed is used to generate cryptographic keys, it is discarded or destroyed to prevent its reuse. Reusing a quantum seed would weaken the security of the generated keys, as a hacker could potentially exploit known information about the seed to compromise the keys.
Use Cases
1. Cybertrust Japan
Cybertrust Japan, a leading certificate authority in Japan integrated Quantinuum's Quantum Origin quantum-computing-hardened private keys into a new certificate issuance and distribution platform for IoT devices in early 2023. The integration helped the organization strengthen security for IoT devices against both current and future threats especially those posed by quantum computing.
Cybertrust Japan's new authentication infrastructure for high-speed, high-volume certificate issuance and distribution for IoT devices incorporates NIST-selected post-quantum cryptography (PQC) algorithms and Quantum Origin's quantum-computing-hardened keys. This provides a more secure and robust solution for authenticating IoT devices.
2. Keyfactor
Keyfactor, an identity-first security solution provider partnered with Quantinuum to deploy Quantum Origin for a verified quantum entropy source and integrate it into Keyfactor’s PKI platform. This partnership announced on February 6, 2024, was followed by the integration of Quantum Origin.
The deployment of Quantinuum’s quantum-backed solution not only aimed to bolster trust in public key infrastructures (PKIs) but also strengthen confidentiality in code signing, providing organizations with a more secure and resilient security solution in the face of growing cybersecurity threats, including those posed by quantum computing.
Keyfactor's PKI platform can now leverage the world's only source of verified quantum entropy to generate high-quality keys for digital certificates – Quantum Origin. This ensures that the keys are resistant to both classical and potential quantum attacks, providing a stronger foundation for secure digital communications.

About Quantinuum
When Quantum Chips Beat HPC
Willow’s below-threshold error rates hint at useful quantum workloads arriving sooner, resetting expectations for post-classical computation.

Quantinuum is a science-led and enterprise-driven company uniting Cambridge Quantum’s best-in-class software with Honeywell Quantum Solutions’ high-performing trapped-ion hardware. The firm is scaling quantum computing and developing applications today to solve the world’s most pressing challenges.
As the world’s largest integrated quantum company, Quantinuum is leading the development of the most powerful quantum computers and the most advanced quantum software solutions. With full-stack technology and world-class scientists, the company is rapidly scaling quantum computing to solve tomorrow’s biggest challenges.







Comments ( 0 )