While cloud adoption offers many benefits such as greater flexibility, cost savings, and improved continuity, it’s not without its challenges.
According to Foundry, 96% of organizations have encountered major challenges when implementing their cloud strategy.
Cost control, security management, and the cloud skills gap are among the most pressing concerns. In fact, 34% of IT decision-makers in security report challenges around the lack of cloud security skills and expertise.
To address these issues, organizations need a comprehensive security solution to manage them effectively. One such company addressing security vulnerabilities is Prowler, a comprehensive open-source platform for cloud security.
This article tells you everything you need to know about Prowler’s security solution, from how it works to key features and use cases.

What is Prowler?
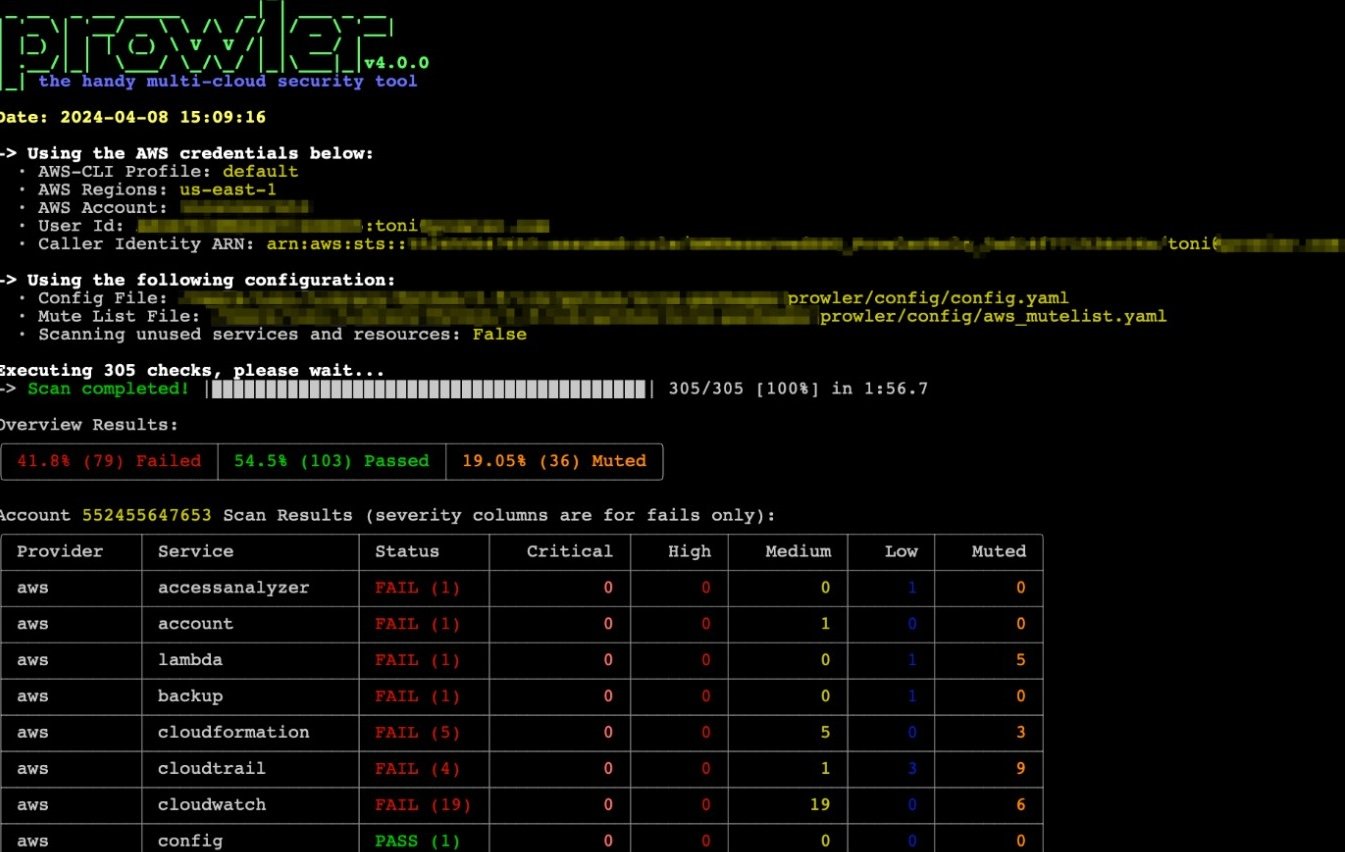
Prowler is a comprehensive open-source platform that scans cloud infrastructure for vulnerabilities and misconfigurations. It does this by running checks against various security standards and best practices, such as CIS, NIST, and PCI-DSS.
The platform delivers cloud security with open-source flexibility, enabling organizations to secure cloud environments in a way that’s best for the business or service.
Organizations can sign up, download, and trial it for free. The Prowler platform provides dashboards with actionable, direct insights for every level of detail of the organization’s security posture. It also presents a holistic view of the organization’s cloud infrastructure and yields results in seconds.
How does Prowler work?
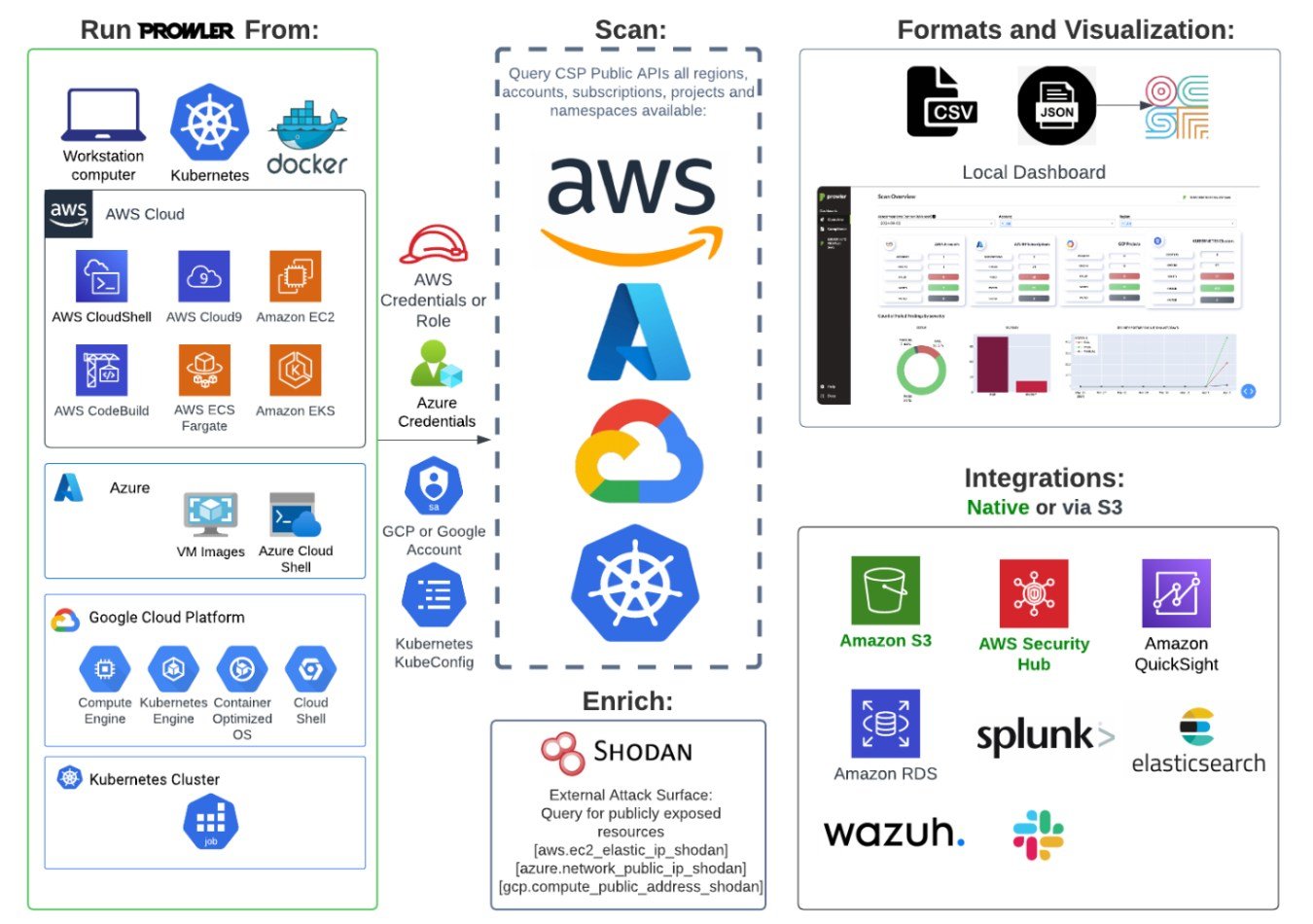
Prowler is designed for AWS, Azure, GCP, and Kubernetes. It can conduct security assessments, audits, incident response, compliance, continuous monitoring, hardening, and forensics readiness. It’s multi-region by default and runs on any AWS partition (Commercial, GovCloud, China, Top Secret).
The technique involves firstly seamlessly integrating the platform with major cloud providers such as AWS, Azure, and Google Cloud. The platform allows users to customize the tools provided by Prowler as per their specific needs – these are defined by custom checks, thresholds, and reporting formats. With such built-in checks, the platform scans for things like CIS benchmarks, GDPR, HIPPA compliance, SOC2 readiness, and many more.
It also offers Internet-exposed resources, unauthenticated services, open S3 buckets, misconfigurations, secrets in code, and more, and users can write their own custom checks for whatever additional or unique AWS security needs an organization may have.
Key Features of Prowler
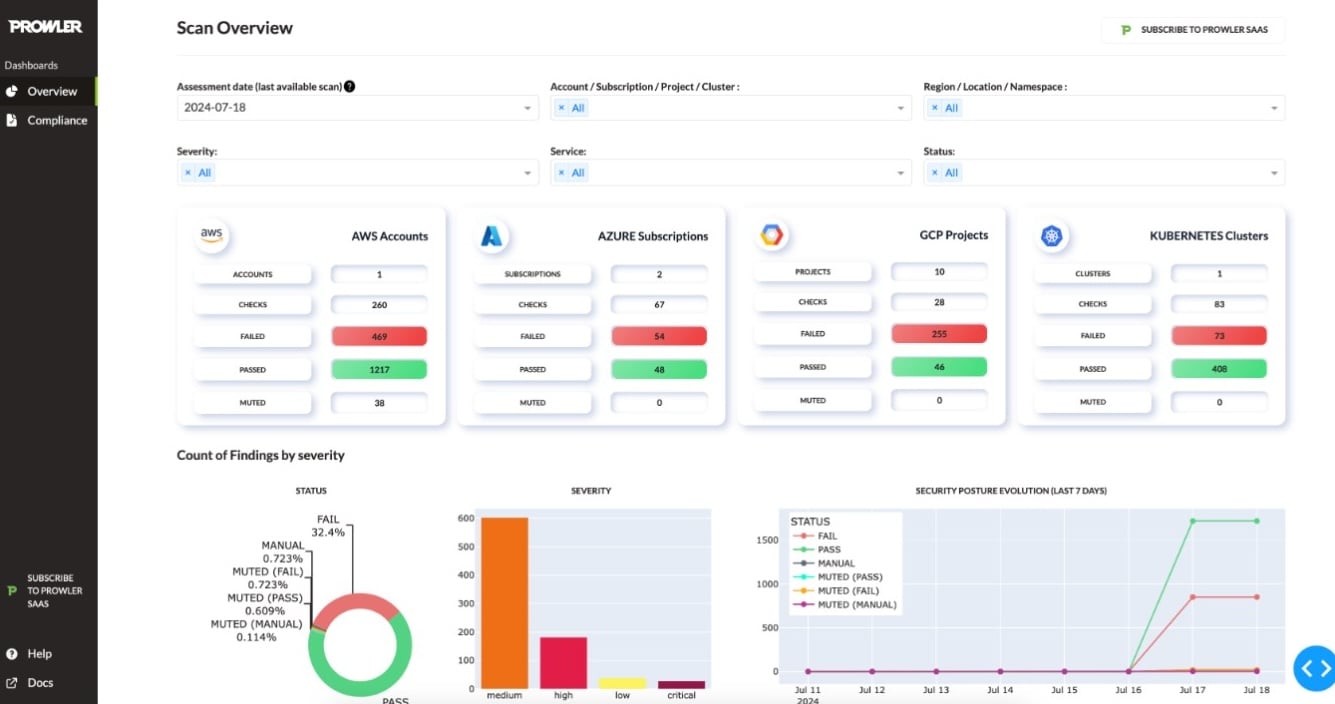
1. Data collection and analysis
Prowler can leverage the cloud provider’s APIs (Application Programming Interface) to collect comprehensive information about an organization’s cloud infrastructure, configurations, and access controls. It also analyzes raw data to yield relevant information and detect potential security risks.
For example, it can check if IAM roles have excessive permissions, if data is encrypted at rest and in transit, and if network security settings are configured correctly. This allows Prowler to provide comprehensive security assessments and identify areas for improvement.
2. Predefined security rules
To detect a variety of vulnerabilities and misconfigurations, the platform is also equipped with a huge library of predefined security rules. These rules are based on industry standards, security best practices, and compliance frameworks like CIS, NIST, and PCI-DSS. Essentially, the rules are related to different security facets such as IAM configurations, network security, encryption, and data protection.
Applying these rules to an organization’s cloud environment, the platform can detect possible security breaches or risks and present suggestions for remediation. Users can also customize checks, and create them to target unique concerns within the organization.
3. Vulnerability detection
Prowler identifies vulnerabilities by conducting a comprehensive analysis of an organization’s cloud environment. It leverages its massive library of security rules to spot multiple weaknesses such as misconfigured IAM roles, exposed ports, weak passwords, and other security weaknesses.

When SOAR Redefines Defense
Boards are backing SOAR to turn fragmented tools into coordinated, automated response and shrink breach impact windows across the enterprise.
Prowler compares the gathered data against its ruleset to identify instances where configurations deviate from security best practices. It basically conducts a risk assessment which is presented according to priority based on severity and potential consequences on the organization’s cloud infrastructure.
This allows Prowler to pinpoint potential vulnerabilities that could be exploited by malicious actors, allowing organizations to take preventative measures to mitigate risks and protect their cloud infrastructure.
4. Remediation steps
Prowler generates reports that spotlight vulnerabilities based on their level of severity, helping the platform generate reports with recommended remediation steps. These reports suggest actionable insights that address security issues promptly. Users can adopt the measures suggested in the reports and carry out remediation actions based on the priority risk factors and their impact on the identified vulnerabilities.
Prowler's recommendations often include specific steps or configuration changes that can be implemented to mitigate the risks associated with the vulnerabilities. The reports also provide references to relevant documentation or resources for further guidance.
5. Configurations
Prowler conducts regular scans to ensure that an organization’s cloud infrastructure is constantly monitored for emerging threats and vulnerabilities. The feature enables the user to configure scheduled scans of their cloud environment, ensuring that the security posture is constantly monitored to detect any emerging vulnerabilities.
The frequency of scans can be easily customized depending on the unique security needs of an organization. Whether they require daily, weekly, or monthly checks, Prowler can be configured to run scans at your desired intervals. This proactive approach helps stay ahead of potential security threats and maintain a high level of security for your cloud environment.
The tool can be set up to send alerts or notifications when new weaknesses are detected, allowing timely response. Prowler's scheduled scans can be integrated with other security tools and workflows. The scan results can also be integrated with incident response systems or security dashboards for further analysis and reporting.
An organization can establish a proactive security posture for its cloud infrastructure by leveraging Prowler’s configuration management features.
Key benefits of Prowler
Inside 2024 Smart BAS Stacks
Break down how leading BAS vendors are unifying sensors, EMS and control to cut energy use, simplify maintenance and standardize sites.

1. Enhanced Compliance Management
Prowler provides comprehensive evaluations against industry standards and regulations, helping organizations adhere to security best practices in alignment with compliance requirements. The platform detects and addresses security weaknesses and misconfigurations to help organizations ensure they are aligned with security frameworks such as CIS, NIST, PCI-DSS, GDPR, HIPAA, and more. It helps minimize the risk of data breaches and fines, demonstrating a commitment to security best practices to stakeholders, customers, and regulators.
The platform is equipped with the capabilities to generate detailed reports outlining compliance status followed by recommendations for remediations, helping organizations meet their compliance obligations and maintaining a strong security posture.
2. Industry-leading cloud security features
Prowler offers several pros especially when compared to conventional cloud security solutions. It provides comprehensive coverage by scanning an organization’s entire cloud infrastructure and detecting vulnerabilities across a variety of resources and services. It continuously monitors the cloud systems to spot emerging threats and automatically conducts tasks involving security assessments efficiently. Prowler integrates seamlessly with other security tools and workflows, providing a holistic view of your security posture. It can also customize the platform’s checks to match an organization’s specific security and compliance requirements.
3. Seamless integrations
To use the free platform, users or organizations can simply install Prowler on their computers or run it directly within their cloud environment. The instructions to install and integrate vary depending on the cloud environment, for example, they’ll be different for AWS, Azure, or GCP.
Users need to set up credentials and allow Prowler to access their cloud account, this allows the security solution to scan cloud resources for vulnerabilities. After setting up, users can run a scan using Prowler’s command-line interface.

Closing the SOAR Automation Gap
Why relying on manual triage leaves gaps in detection and response, and how AI-enabled SOAR can reduce exposure windows and analyst fatigue.
The scan results uncover the organization’s cloud environment to check if the system has been configured securely and generate a report. This report spotlights potential security risks and issues plus provides recommendations to fix them.
Prowler can be integrated with other security tools and workflows to enhance your overall security posture.
Use cases
1. Strengthening AWS security through collaboration
Prowler with Terraform boosts AWS security posture wherein the latter automates Prowler monitoring via infrastructure as code (IaC). The user achieves this in the dwp/prowler-monitoring/aws Terraform module. This module automates the creation of important components for Prowler monitoring within an organization’s AWS environment.
In case a user wants to monitor for unauthorized API calls within their AWS infrastructure, Prowler has a specific check for this. The Terraform module helps with creating a CloudWatch group that stores logs generated by Prowler’s scans. It sets up an SNS topic to receive alerts if any Prowler checks are assessed as vulnerable or carry a potential threat. The module sets up alarms based on Prowler logs, triggering notifications if unauthorized API calls are detected.
The capabilities of Prowler and Terraform combined help establish continuous and automated security monitoring for an organization’s AWS environment. They detect and respond to potential threats promptly.
2. Automated Security Assessment with AWS CloudFormation
Prowler and AWS CloudFormation automate security assessments within an AWS environment beginning with deployment. This happened by creating an AWS CodeBuild project to run Prowler scans, an S3 bucket to store generated reports, and an AWS Lambda function to trigger the CodeBuild project.
Users customize the scan type basic, intermediate, and full) and target accounts (single or multiple). The platform presents optional parameters to enable email notifications and a consolidated reporting summary for multi-account scans. The platform then provides instructions to deploy scans for both single and multi-account scenarios via AWS CloudShell or the AWS console.

From GRC Silos to IRM Scale
Why boards are backing integrated risk programmes to align resilience, performance and compliance across the enterprise.
Post completion, reports generated from the scan are uploaded to the S3 bucket, accessible to use through the S3 console, or users can select among various formats (HTML, CSV, JSON). Prowler dashboards can alternatively be employed for further analysis which requires local installation.
This method makes automation and customizability easy and efficient in Prowler, helping yield security assessments faster. It caters to both single and multi-account scenarios within an AWS Organization, providing comprehensive reports with findings categorized by severity including potential remediation actions.
About Prowler
Prowler is a comprehensive Open Source platform for cloud security, trusted by organizations of all sizes, and used every day so teams can be confident in ensuring cloud security. It recently achieved SOC 2 Type 2 compliance – a set of standards developed by the American Institute of Certified Public Accountants (AICPA). This award validates that service providers like Prowler manage users' data securely.







Comments ( 0 )