
What is Cl0p Ransomware?
Cl0p is one of the variants of CryptoMix ransomware that first appeared in February 2019. Cl0p is a Ransomware-as-a-Service (RaaS) used in several highly effective large-scale spear phishing campaigns using different evasion techniques. Notably, it uses a digitally signed and verified binary system, hence becoming a critical threat to any organisation.
One of the most salient features of Cl0p is its use of the double extortion tactic, which includes encrypting the victim's data and stealing it. After that, the ransomware operators promise to restore access only upon receiving the ransom. Another threat is that Cl0p operators will publish the exfiltrated data on the Cl0p LEAKS website on the Tor network to further coerce victims into compliance.
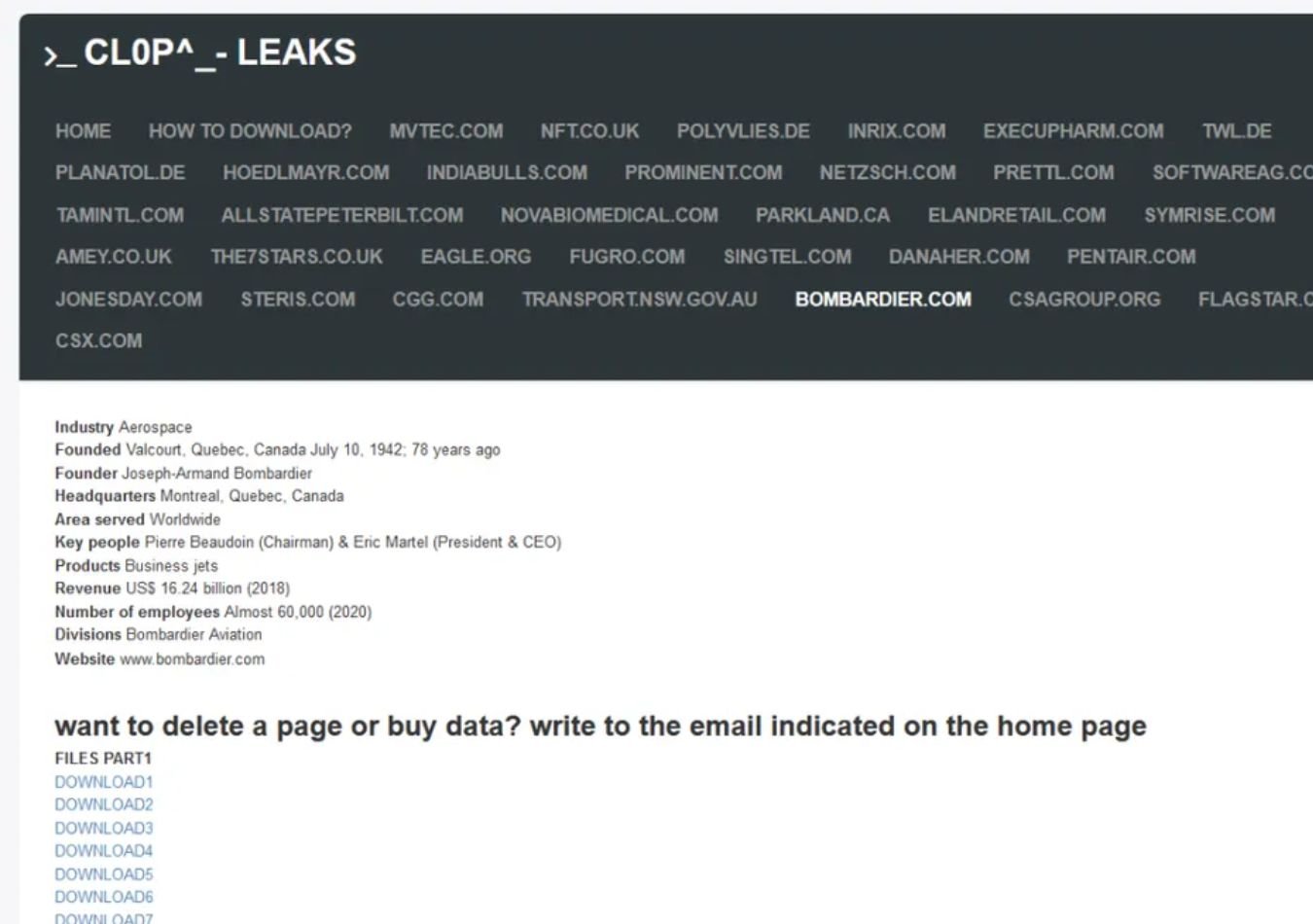
In 2019, actors associated with TA505 used Cl0p ransomware as the final payload in a phishing campaign. That campaign contained a macro-enabled document, which leveraged the Get2 malware dropper to download SDBot and FlawedGrace malware. However, in the newest campaigns since 2021, Cl0p has turned another corner, with a new concentration on data exfiltration rather than encryption. This development in the trend indeed marks a tactical shift for Cl0p, making him arguably far more formidable in this dynamic world of cyber threats.
This article will look at the history, tactics, and constantly changing face of the Cl0p ransomware group to provide insight that could help organisations prepare their defences against this emerging threat.
How Does Cl0p Ransomware Work?
Cl0p ransomware attacks sensitive data on infected devices through a multi-step attack process. Understanding the process is essential, as it will help individuals and organisations safeguard against cyber threats. Here's how Cl0p ransomware works in a simplified explanation:
Cl0p attackers typically infect targeted devices through phishing emails, malicious downloads, and software vulnerabilities. Such initial infection helps them gain success in infiltrating networks and systems.
Reconnaissance and Data Theft
After compromising the device, attackers conduct manual reconnaissance to find valuable data. Sensitive information is systematically stolen, including everything from personal data and financial records to business-sensitive proprietary information.
File Encryption
Then, Cl0p ransomware serves as the dropped encryptor. In such malware, files are locked through the reorganisation of their extension. In some recent attacks, such as the 2023 MOVEit attacks, cyber attackers not only block the files but often also steal data without encryption, hence raising the threat bar even higher.
Ransom Note Delivery
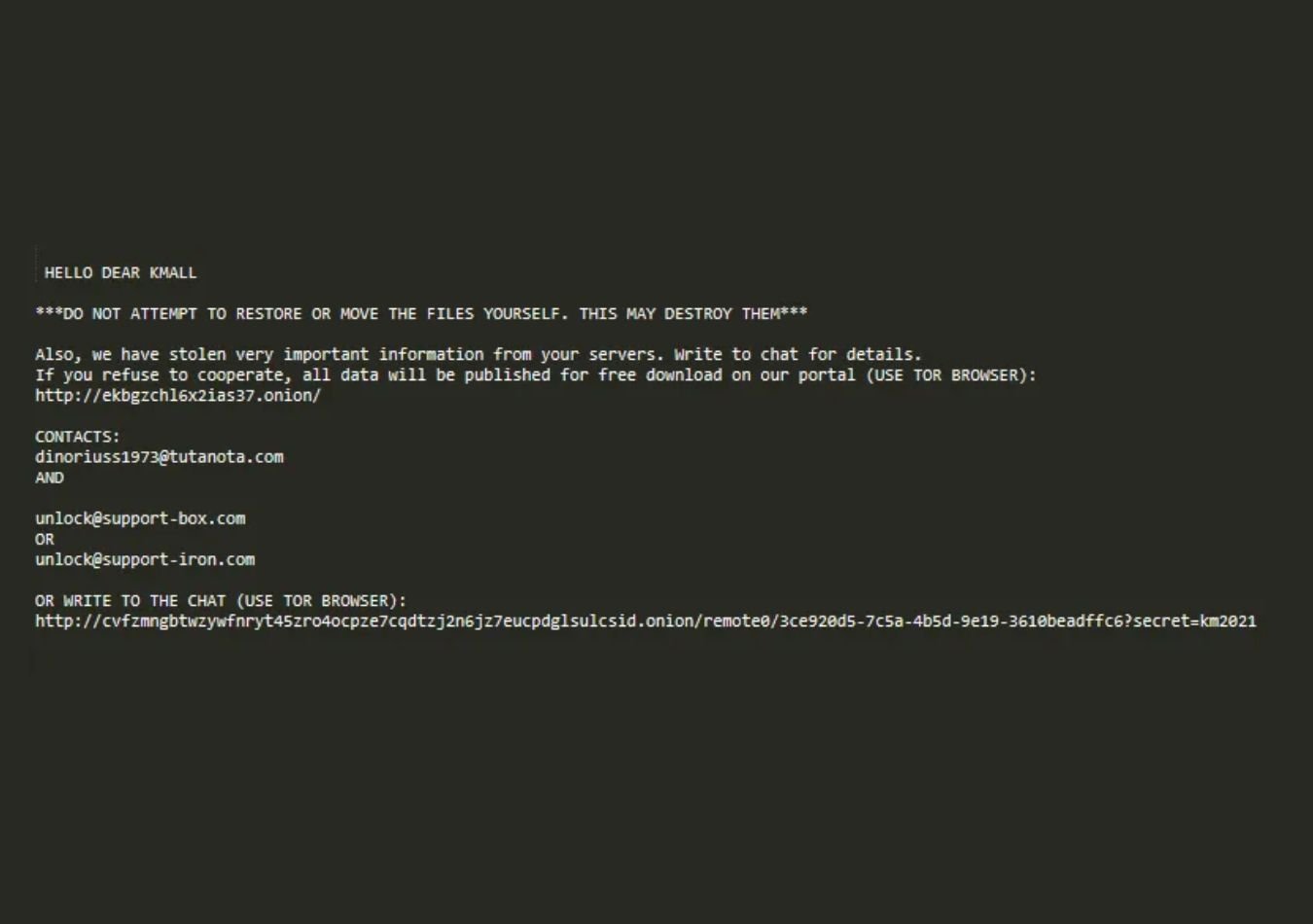
When the victims try to access their encrypted files, a ransom note pops up with instructions on making such payments. These typically involve demands for cryptocurrency payments and threats regarding the information stolen.
Double Extortion Tactics
Cl0p ransomware involves double extortion-one where, besides demanding a ransom for file decryption, the attackers also threaten to leak stolen data if their demands are unmet. A tactic that significantly raises pressure on victims to comply.
Payment for Decryption
Only then are the victims provided with the decryption key that allows them to access their files. Suppose the attackers' promise is to be taken literally. Therefore, attackers will only provide a decryption key upon receiving the ransom amount. However, there's no guarantee that attackers will keep their promise, so organisations need to have very efficient backup and recovery plans.
History of the Cl0p Ransomware
The Cl0p ransomware was first discovered by cybersecurity researchers back in February 2019 while investigating a wide-ranging spear-phishing attack. In such attacks, highly targeted emails are generally cleverly devised to trick targeted individuals into inadvertently disclosing sensitive information or installing malware.

When Tech Giants Lose Focus
How leadership churn, portal-era bets and misjudged deals eroded Yahoo’s position in search, media and digital advertising.
Upon its discovery, security experts immediately labelled Cl0p as a serious cybersecurity threat because the malware had capabilities for file encryption on the devices of targeted victims. This ransomware makes essential files unattainable by using highly efficient algorithms until paid in ransom, normally in virtual currencies.
See more: What is Clop? Understanding the MOVEit Ransomware Gang
The group behind the Cl0p ransomware has successfully attacked several entities, including global energy conglomerates, major universities, and renowned companies such as the BBC and British Airways.
Since its appearance, Cl0p has continuously improved due to new techniques and methods being included in its inventory. According to cybersecurity specialists, Cl0p is still continuously updated, with its creators introducing improvements with the purpose of better exploiting system vulnerabilities. This evolution shows that between cybercriminals and security experts, there is an arms race going on, where each develops new strategies and ways to counteract each other.
With Cl0p ransomware continuing to pose a serious threat to organisations of all sizes, understanding its background, operational methods, and tactics has become an essential ingredient of any practical cybersecurity approach.
The history of Cl0p ransomware underlines the dynamic nature of the cyber menace and shows an increasing need for businesses to be watchful. Understanding the tactics used by Cl0p and other variants of ransomware, companies will be better positioned against future attacks and secure their digital assets.
Cl0p MOVEit Zero-Day Vulnerability (CVE-2023-34362)
One such one is MOVEit Transfer, a web application used by many organizations to transfer files securely. However, the web application, which is powered by MySQL, Microsoft SQL Server, and Azure SQL database engines, was targeted in May 2023 by the Cl0p ransomware group using a critical SQL injection zero-day vulnerability, tracked as CVE-2023-34362.
When Case Systems Become Weapons
Examines how a case-management platform became alleged intelligence infrastructure, blurring lines between legal IT and covert operations.

LEMURLOOT is a web shell that provides Cl0p with persistence, information gathering, and data theft capabilities within the security context of MOVEit Transfer. To begin with, LEMURLOOT imports several essential libraries, including but not limited to MOVEit.DMZ.ClassLib and Application Files, which allow the web shell to interface directly with MOVEit's managed file transfer capabilities.
For the sake of evasion, the web shell was named human2.aspx, similar to MOVEit's legitimate file, human.aspx. After being installed, the web shell created a unique 36-character password for use in authentication, securing Cl0p’s access to the operations of MOVEit Transfer.
The vulnerability in MOVEit, specifically CVE-2023-34362, opened the door to several ransomware attacks, after which Cl0p gained access to the data of hundreds of organisations. As a result of this security breach, sensitive information was mass-exfiltrated, and Cl0p issued a ransom demand that had to be met before June 14. Consequently, U.S. law enforcement offered a reward of $10 million for any information related to Cl0p's operations.
Who is Behind Cl0p Ransomware?
The Cl0p ransomware seems to originate from a Russian-speaking cybercrime group that has established a foothold in most of the RaaS market. The organisation is best known as TA505 but sometimes as FIN11--a group largely perceived to operate out of Russia or other countries in Eastern Europe. Russian-speaking cybercriminal entities have been connected to a large portion of ransomware attacks worldwide, and TA505 is among the most notorious.
While the connection between TA505 and FIN11 is considered by some to be a subset, or even merely an affiliate, of TA505, it may also be another group operating from similar regions with similar methods.
Operating from Eastern Europe in the main, TA505 and FIN11 have capitalised on regional know-how and resources to produce super-sophisticated ransomware targeting companies, official agencies, and other organisations that yield higher value.

Data Trust Erosion in Niche Apps
What a delayed breach disclosure, insecure password practices, and account removal reveal about security risk in smaller networks.
This is where their origins offer some level of protection due to the reluctance or lack of interest shown by regional law enforcement agencies in pursuing cybercrime perpetrators whose targets are foreign-based, and so allowing Cl0p ransomware attacks to persist and shift into new modes of operation.
Cl0p Ransomware Group Attacks and Impact
In 2020, Cl0p leveraged vulnerabilities in the Kiteworks Private Content Network to attack its customers by gaining access to vital systems. At this point, however, the Cl0p malware had not been introduced. It was also behind the double extortion campaign wherein they leaked stolen data belonging to a pharmaceutical giant.
In 2021, Cl0p waged attacks on high-profile companies such as SolarWinds, one of the leading software providers, and Swire Pacific Offshore, a Singapore-based marine services firm. These attacks continued to leverage zero-day exploits and double extortion techniques.
It is a case of a big cyber attack organised at the end of January 2023 by the Cl0p ransomware group with the use of a zero-day vulnerability (CVE-2023-0669), which attacked the GoAnywhere MFT platform. This breach has affected an estimated 130 organisations; Cl0p claimed to have exfiltrated sensitive data from GoAnywhere MFT within a record period of only 10 days.
However, there was no evidence of lateral movement into other network areas, meaning that an attack by Cl0p was confined to the GoAnywhere platform itself. Operators of Cl0p ransomware have been reaching out to upper-level executives directly with ransom notes after a data breach, stating that their stolen data would be published on the data leak site if they are not paid an amount.
Cl0p was much more active in 2023, with a significant increase in attacks throughout the period of January-June. The Cl0p ransomware gang conducted such operations against businesses, software, and financial organisations, mainly in North America and Europe, most of which have been directed to the United States. This year alone, it hit over 2,000 organisations and breached the sensitive information of more than 62 million individuals, most of whom were from the United States.
When Ransomware Targets Care
Qilin’s attack on UK healthcare exposes how operational dependencies and weak controls turn clinical services into high-value extortion leverage.

Cl0p Ransomware Attacks: How to Mitigate Them
When mitigating against Cl0p ransomware attacks, one must adopt a multi-layer cybersecurity approach. Minimising the threat of Cl0p and other ransomware includes auditing remote access tools and reviewing logs for unauthorised execution of remote access software.
Advanced security software with stringent policies on who can access systems remotely must be installed. Robust application controls must be implemented to block and monitor RDP and other remote desktop services. Software listing can also control application execution, especially for remote access applications.
What makes this strain of ransomware particularly dangerous is the deliberate and calculated targeting of businesses and organisations; thus, it could cause really serious financial and reputational damage.
While such tactics are used by this ransomware, proper security best practices and implemented protective measures can be taken to guard against Cl0p ransomware attacks effectively and reduce the consequences if a breach does happen.






Comments ( 0 )