Leadership powerhouse Claire Williams OBE reveals how to navigate change and develop a strong team culture at Infosecurity Europe 2024
Dozens Arrested Following UK Police LabHost Takedown
Dozens of cybercriminals linked to the phishing website LabHost have been arrested following the site’s takedown by the Metropolitan Police.
The UK-founded website, which helped criminals send fraudulent text messages and create fake websites to steal from victims, has been linked to over 70,000 scams targetting UK nationals since 2021.
It was created by a criminal gang and enabled more than 2,000 users to set up phishing websites designed to steal personal information such as email addresses, passwords and bank details.
After LabHost was seized by police and disrupted, its 800 criminal customers got a message telling them that police knew who they were and what they were doing, and 37 people were arrested, including some at Manchester and Luton airports, as well as in Essex and London.
Detectives have also contacted up to 25,000 UK-based victims to tell them their data has been compromised by the scam.
"You are more likely to be a victim of fraud than any other crime,” Metropolitan Police Deputy Commissioner Dame Lynne Owens said in a statement.
“Online fraudsters think they can act with impunity. They believe they can hide behind digital identities and platforms such as LabHost and have absolute confidence these sites are impenetrable by policing.
“But this operation and others over the last year show how law enforcement worldwide can, and will, come together with one another and private sector partners to dismantle international fraud networks at source," Dame Owens added."
What is LabHost?
‘LabHost’ is a phishing service set up in 2021 by a criminal cyber network. It allowed scammers without technical skills to bombard victims with messages designed to trick them into making payments online.
This helped criminals to steal identity information, including 480,000 card numbers and 64,000 PIN codes, known in criminal slang as "fullz data".
Criminal subscribers could log on and choose from existing sites or request bespoke pages replicating those of trusted brands such as banks, healthcare agencies and postal services.
The website even provided a tutorial to cater for criminals with limited IT know-how, including a robotic voice saying at the end: "Stay safe and good spamming."
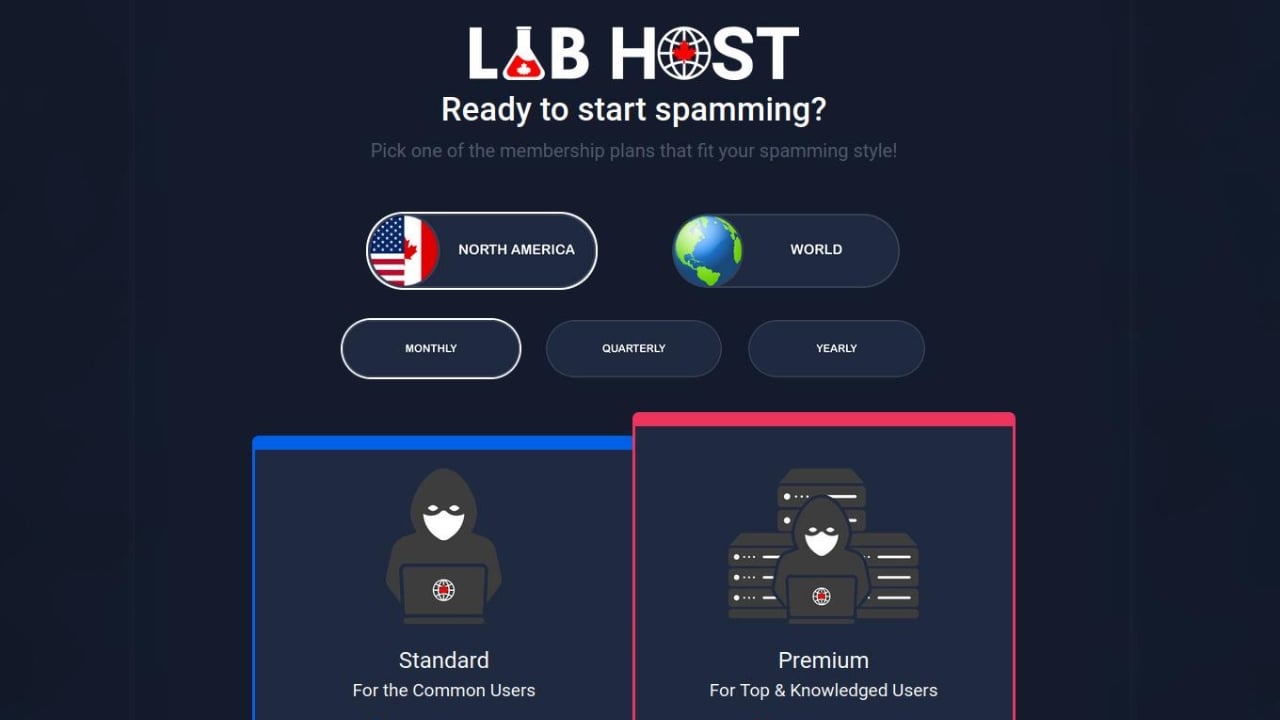
Those subscribing to Labhost’s worldwide membership, meaning they could target victims all around the world - paid between £200 and £300 a month. Since it began, the site has received just under £1m in payments from criminal users, according to UK Police.
“LabHost provided a real-life threat in action, acting as a platform which could enable almost anyone to conduct specialised phishing attacks,” Andrew Rose, Chief Security Officer at SoSafe, told EM360Tech.
“[It] is also a reminder that cybercriminals are not only in Russia and North Korea but are operating everywhere and businesses must be vigilant.
Impact of LabHost takedown
Police took down the gang's site, LabHost, to stop these smishing scams, and have since arrested 37 people worldwide and are contacting victims.
“The shutdown of LabHost is a great example of cutting cybercrime at its root source. “The arrests of some of the main perpetrators go to show that cybercrime is not unpunishable, and we are now seeing more and more people being held to account," said Christiaan Beek, Senior Director, Threat Analytics at Rapid7.
“As we see the growth of ransomware as a service, it is a positive sign to see that a key distributor has been taken down to reduce the increasingly easy access to fraudulent methods,”
“The collaborative efforts of the Cyber Defence Alliance and other agencies resulting in such a vast number of international arrests are a testament to this and will act as a deterrent for anyone thinking these activities don’t have consequences.”
A spokesperson for the Cyber Defence Alliance said: “The partnership with the Cyber Defence Alliance and law enforcement continues to develop.
“We have together, once again, been able to disrupt a major international criminal platform and prevented more people falling victim to these scams.”
The UK’s fight against Phishing
According to the UK’s 2024 cyber breaches survey, phishing is still the most common cyber attack in the UK, with an estimated 84% of British organizations falling victim to it in the last 12 months.
These attacks are a form of social engineering, where attackers exploit human psychology to trick victims into revealing confidential information, using spoofed websites and email addresses to seem more convincing.
“Phishing is still one of the most successful hacking tactics, targeting the human factor to enter technical systems and wreak havoc,” added Rose.
“Attacks of this kind psychologically trick users into clicking suspicious links, and attachments or lead them to fake landing pages to steal data and 83 per cent of security leaders in the UK rate phishing and the emotional manipulation of employees as a major security risk for their organisation.”
Adrian Searle, Director of the National Economic Crime Centre (NECC) in the NCA, said: “Fraud is a terrible crime that impacts victims both financially and psychologically, undermining our collective trust in others and the online services on which we all rely,”
“This operation again demonstrates that UK law enforcement has the capability and intent to identify, disrupt and completely compromise criminal services that are targeting the UK on an industrial scale.”
Collaboration to Prevent Fraud
Temporary Commander Oliver Shaw from the City of London Police said that collaborative operations like the LabHost takedown are “vitally important” in the global fight against fraud and cybercrime.”
“As the national lead force for fraud, we were able to support the operation by providing intelligence derived from reports made to Action Fraud. “We continue to support the Metropolitan Police Service, Regional Organised Crime Units (ROCUs) and forces across the UK, to put cyber-criminal fraudsters on the back foot.
Amy Hogan-Burney, General Manager, Cybersecurity Policy & Protection at Microsoft agreed, stating: “Today’s action led by the United Kingdom’s Metropolitan Police Service shows the impact we can have in the fight against cybercrime when we work together.
If you think you have been a victim of fraud, contact your bank immediately and report to Action Fraud at actionfraud.police.uk or call 0300 123 2040.