Darktrace Acquired by Private Equity Firm Thoma Bravo in $5 Billion Deal
What is SIEM? Definition, Benefits, Best Practices

Managing risks and mitigating threats has never been more important in today’s cyber threat landscape. Cybercriminals are launching more sophisticated attacks than ever before, and new technologies such as large language models (LLMs) and machine learning technologies are lowering the entry-level to sophisticated cyber-attacks and identity theft.
As attacks become more common, they’re also becoming more expensive. Cybercrime is expected to cost the world a whopping $9.5 billion this year, with that number expected to increase to $10.5 billion by 2025.
With the risk higher than ever before, organizations need to be able to identify attacks before they happen and respond quickly when their systems are breached.
Security Information and Event Management (SIEM) is becoming increasingly important in the detection, analysis and response to security threats. This article explores what SIEM is, its components, and why you need it in 2024.
What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) is a software solution that helps organizations detect, analyze, and respond to security threats before they can disrupt business operations.
It acts as a central hub that collects and analyzes security-related data (events) from various sources across your IT infrastructure, such as firewalls, servers, and applications. This gives security teams a central location to view and analyze all security-related data from their network.
SIEM gathers log data from various devices and systems within an organisation, providing a centralized view of security events. It analyzes the collected data to identify patterns and potential threats, correlating seemingly unrelated events that might indicate an attack.
Many of the best SIEM tools also use pre-defined rules and machine learning algorithms to identify activities that deviate from normal behaviour, potentially indicating a security breach. It helps organizations meet security compliance requirements by generating reports on security events and activities.
How does SIEM Work?
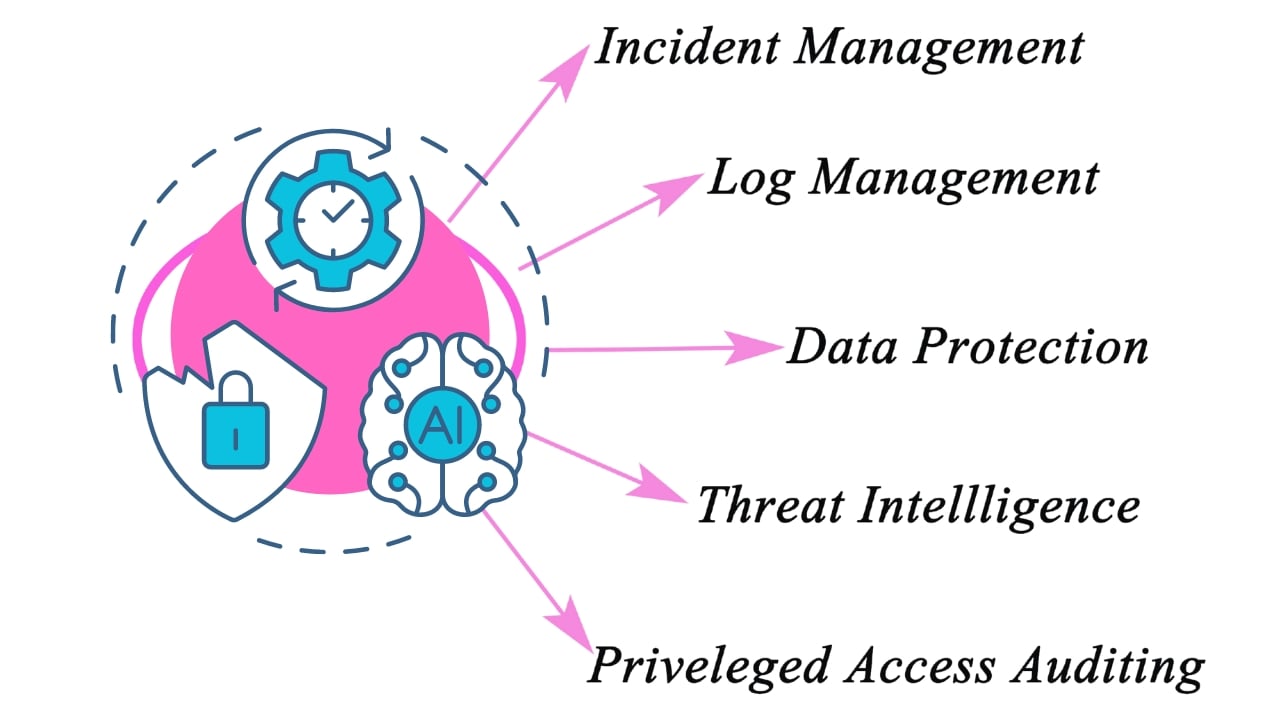
SIEM works in stages to collect, analyze, and respond to security threats across an organization's IT infrastructure. Here's a deeper dive into how it works:
Log Collection and Aggregation
SIEM consolidates its findings into a single, central dashboard where security teams monitor activity, triage alerts, identify threats and initiate response or remediation.
Most dashboards also include real-time data visualizations that help security analysts spot spikes or trends in suspicious activity. This means administrators are alerted immediately and take appropriate actions to mitigate threats before they materialize into more significant security issues. This includes devices like servers, applications, firewalls, and even user activity.
Log Parsing and Enrichment
Raw log data is messy and hard to understand. SIEM parses this data, making sense of it by identifying relevant fields and categorizing them. It might also enrich the data by adding context, such as user information or threat intelligence.
Log Storage and Retention
SIEM stores the collected data in a central repository for long periods. This is crucial for forensic investigations, where security analysts need to analyze historical data to understand an attack. It also helps with compliance requirements that mandate data retention for certain periods.
Event Correlation and Security Analytics
Event correlation is a crucial part of any SIEM solution. SIEM analyzes the data in real time using correlation rules and statistical models. These rules are predefined by security professionals and can identify suspicious activity, like a surge in failed login attempts from an unusual location.
SIEM can also leverage advanced analytics to detect more sophisticated threats. This improves the mean time to detect (MTTD) and mean time to respond (MTTR) for IT security teams, offloading the manual workflows associated with the in-depth analysis of security events.
Compliance Management
SIEM solutions are a crucial aspect of any regulatory compliance system. Due to the automated data collection and analysis that it provides, they’re a valuable tool for gathering and verifying compliance data across the entire business infrastructure.
SIEM can also generate real-time compliance reports for PCI-DSS, GDPR, HIPPA, SOX and other compliance standards, reducing the burden of security management and detecting potential violations early so they can be addressed. Many of the leading solutions come with pre-built add-ons that can generate automated reports designed to meet compliance requirements.
SIEM vs SOC: What’s the difference?
SIEM and Security Operation Centre (SOC), though both crucial for cybersecurity, serve different purposes:
SIEM is a tool – a software solution. It collects data from various security sources across your network, analyzes it to identify potential threats, and generates alerts for security teams Whether it’s firewalls, servers, or intrusion detection systems - SIEM pulls information from all of them and centralises it for analysis. It then sifts through this data, searching for suspicious activity based on predefined rules.
SOC, on the other end, is the team that utilizes SIEM and other tools to monitor your network's security posture. They're the ones who receive SIEM alerts, investigate them, and take action in response to security incidents.
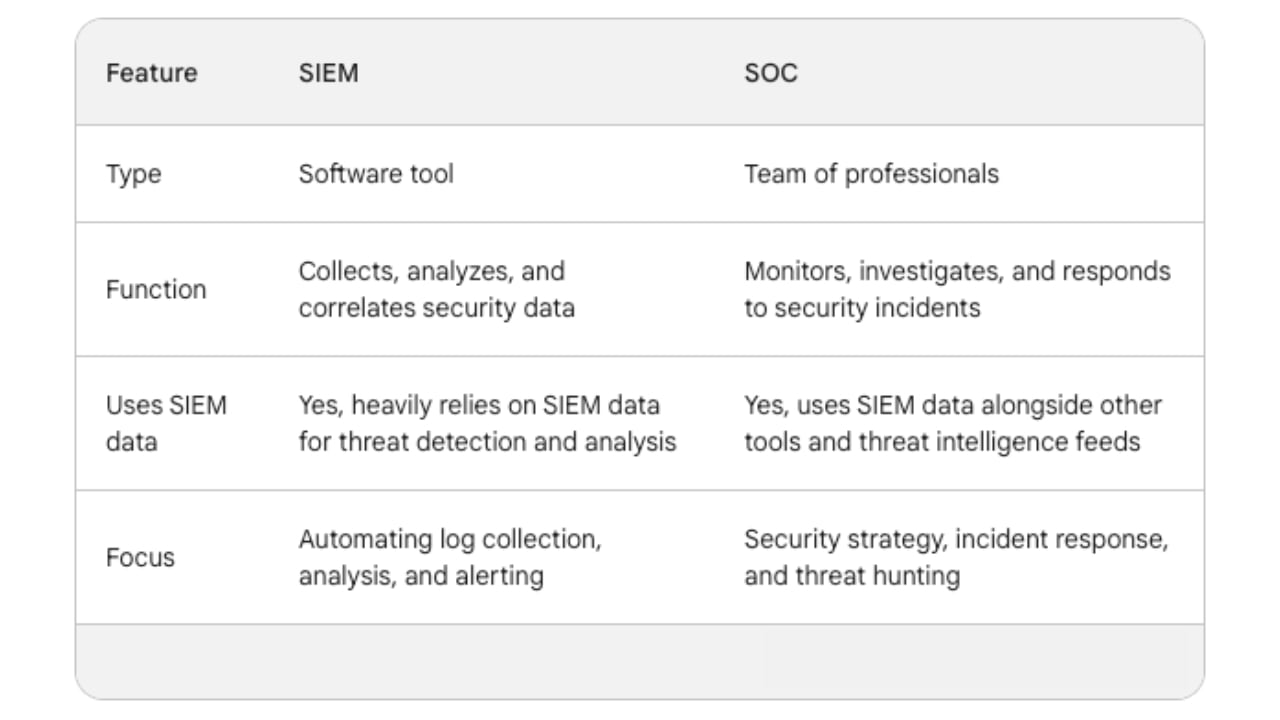
SIEM and SOC work together. SIEM provides the data and insights, while the SOC team uses them to take informed actions. Many organizations might choose to outsource their SOC function to a Managed Security Service Provider (MSSP) that would leverage SIEM technology.
Benefits of SIEM
Security Information and Event Management offers a range of advantages and use cases that strengthen an organization's overall security posture.
Here are some key benefits of SIEM:
1. Improved Threat Detection:
By centralizing and analyzing log data from numerous sources, SIEM can identify threats that individual security tools might miss. It can uncover patterns indicative of malicious activity, such as unusual login attempts, unauthorized file access, or suspicious data exfiltration.
2. Faster Incident Response:
SIEM helps security teams react quickly to security incidents. Real-time analysis and alerts enable them to pinpoint potential threats rapidly and initiate an incident response plan to minimize damage.
3. Enhanced Compliance Management
Many regulations mandate organizations to retain security logs for a certain period. SIEM facilitates centralized log storage and simplifies compliance reporting by generating audit trails and reports.
4. Centralized Security Data Management
SIEM acts as a central hub for all security-related data, offering a holistic view of security events across the network. This consolidated view streamlines security operations and simplifies threat-hunting efforts.
5. Reduced Security Management Costs
SIEM can automate manual tasks like log collection and analysis, freeing up security personnel's time to focus on higher-level tasks like threat hunting and investigation. Additionally, by enabling earlier detection and response to security incidents, SIEM can help reduce the financial impact of breaches.
6. Improved Security Posture
By providing insights into security threats and vulnerabilities, SIEM empowers organizations to proactively strengthen their security posture. Security teams can leverage SIEM data to identify areas for improvement and implement more effective security controls.
Best practies for implementing SIEM
1. Planning and Definition
- Define clear goals. Before diving in, clearly outline what you want to achieve with SIEM. What threats are you most concerned about? What kind of data do you need to collect? A well-defined roadmap ensures your solution is aligned with your organization's security needs.
- Identify data sources. SIEM works best when it has a comprehensive view of your network. Carefully identify all potential log sources including firewalls, servers, applications, security tools, and cloud environments.
2. Implementation
- Don't try to ingest and analyze everything at once. Begin with key log sources and prioritize critical use cases like detecting suspicious login attempts or unauthorized access. As you gain experience and confidence, you can gradually expand your SIEM's reach.
- Optimize data collection. Not all data is equally valuable. Focus on collecting relevant security logs while filtering out extraneous information. This will streamline SIEM's operation and minimize false positives.
3. Configuration and Tuning
- Standardize log formats. Ensure consistency in log formats across different devices and systems. This simplifies log parsing and analysis within SIEM.
- Refine correlation rules. Like any security solution, SIEM relies on pre-configured rules to identify threats. Regularly test and update these rules to ensure they accurately detect suspicious activity. Consider threat intelligence feeds to stay updated on the latest attack methods.
4. Management and Optimization
-
Invest in training. Security personnel need proper training to operate and interpret SIEM data effectively. Understanding the solution and its capabilities is crucial for maximizing its potential.
-
Continuously monitor and improve your system. Regularly monitor your system's performance, fine-tune configurations, and update rules as your security needs evolve. You may also have to replace your SIEM if it is not performing to suite your needs.
- Create an incident Response Plan. Establish a clear plan for how your team will respond to security incidents identified by SIEM. This ensures a swift and coordinated response to mitigate potential damage.
By following these best practices, you can implement an SIEM solution that effectively strengthens your organization's security posture and helps you proactively combat cyber threats.